- Cisco Community
- Technology and Support
- Security
- VPN
- Re: AnyConnect new feature - DTLSv1.2
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2018 02:02 PM - edited 02-21-2020 09:31 PM
With the release of v9.10.1, has anyone been able to get DTLSv1.2 working with AnyConnect sessions? (Our clients are v4.6.02074)
-If I don't specify dtlsv1.2, it will always establish the DTLS tunnel using dtlsv1.0.
-If I do specify dtlsv1.2 with the following config, the DTLS tunnel fails to establish with the message "%ASA-5-722043: Group <groupid> User <userid> IP <ipaddress> DTLS disabled: unable to negotiate cipher". Removing the "ssl cipher dtlsv1" line makes no difference.
ssl server-version tlsv1.2 dtlsv1.2
ssl cipher default custom "ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-GCM-SHA384"
ssl cipher dtlsv1 custom "AES256-SHA"
ssl cipher tlsv1.2 custom "ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-GCM-SHA384"
ssl cipher dtlsv1.2 custom "ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-GCM-SHA384"
ssl ecdh-group group20
ssl dh-group group24
Solved! Go to Solution.
- Labels:
-
AnyConnect
-
Other VPN Topics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2019 06:20 AM
Thanks, Marvin:
I have just upgrade my ASA to the latest interim release 9.10.1.7 and AnyConnect client 4.7.00136. It comes up with DTLSv1.2 and it can be seen in both ASA and Client GUI interface:
DTLS-Tunnel:
Tunnel ID : 8.3
Assigned IP : 192.168.68.27 Public IP : 10.5.160.27
Encryption : AES-GCM-256 Hashing : SHA384
Ciphersuite : AES256-GCM-SHA384
Encapsulation: DTLSv1.2 UDP Src Port : 56925
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-03-2019 12:40 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2021 05:20 AM
Hi,
I updated my just now:
ASA 9.12(4)
ASDM 7.13(1.101)
AnyConnectClient (4.903049)
but I still see only DTLDv1.0? Could you please tell me, what you configured on your asa?
Many thx in advance
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2021 06:56 AM
s.schuler@sys-tec.info please share the output of "show run ssl" from your ASA. It should match what the original poster has mentioned above.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2021 04:53 AM
Hi Marvin,
thx, do am I right, I have to configure these on CLI and not with the ASDM. I only find a box to tag or untag DTLD support?
Thx
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2021 10:39 AM
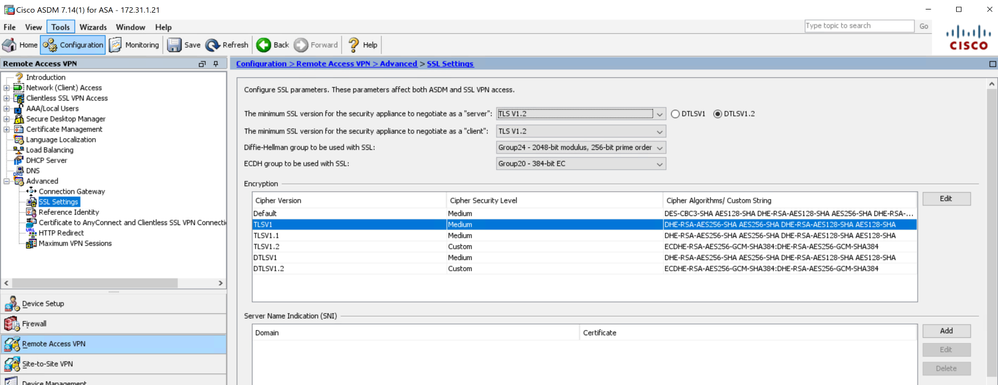
You can make the changes in ASDM. See the following example:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2021 04:41 AM
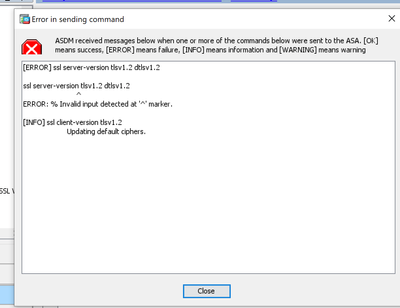
Hi
after doing it in ASDM I've got this message:
ciscoasa# sh run ssl
ssl client-version tlsv1.2
ssl dh-group group24
ssl ecdh-group group20
ssl trust-point ASDM_Launcher_Access_TrustPoint_0 outside
ssl trust-point ASDM_Launcher_Access_TrustPoint_0 inside3
ssl trust-point ASDM_Launcher_Access_TrustPoint_0 backup
ssl trust-point ASDM_Launcher_Access_TrustPoint_0 inside3 vpnlb-ip
Any ideas? Thx in advancd
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2021 08:35 AM
s.schuler@sys-tec.info please share the output of "show version" so we can confirm the necessary 3DES-AES licenses.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2021 10:37 AM
Hi
ciscoasa# sh version
Cisco Adaptive Security Appliance Software Version 9.12(4)
SSP Operating System Version 2.6(1.198)
Device Manager Version 7.13(1)
Compiled on Thu 21-May-20 11:17 PDT by builders
System image file is "disk0:/asa9-12-4-lfbff-k8.SPA"
Config file at boot was "startup-config"
ciscoasa up 1 min 19 secs
Hardware: ASA5506, 4096 MB RAM, CPU Atom C2000 series 1250 MHz, 1 CPU (4 cores)
Internal ATA Compact Flash, 8000MB
BIOS Flash M25P64 @ 0xfed01000, 16384KB
Encryption hardware device : Cisco ASA Crypto on-board accelerator (revision 0x1)
Number of accelerators: 1
1: Ext: GigabitEthernet1/1 : address is 7488.bb56.3244, irq 255
2: Ext: GigabitEthernet1/2 : address is 7488.bb56.3245, irq 255
3: Ext: GigabitEthernet1/3 : address is 7488.bb56.3246, irq 255
.....
14: Int: Internal-Data1/4 : address is 0000.0100.0001, irq 0
The Running Activation Key feature: 2 security contexts exceed the limit on the platform, reduced to 0 security contexts.
Licensed features for this platform:
Maximum Physical Interfaces : Unlimited perpetual
Maximum VLANs : 5 perpetual
Inside Hosts : Unlimited perpetual
Failover : Disabled perpetual
Encryption-DES : Enabled perpetual
Encryption-3DES-AES : Enabled perpetual
Carrier : Disabled perpetual
AnyConnect Premium Peers : 2 perpetual
AnyConnect Essentials : Disabled perpetual
Other VPN Peers : 10 perpetual
Total VPN Peers : 12 perpetual
AnyConnect for Mobile : Disabled perpetual
AnyConnect for Cisco VPN Phone : Disabled perpetual
Advanced Endpoint Assessment : Disabled perpetual
Shared License : Disabled perpetual
Total TLS Proxy Sessions : 2 perpetual
Botnet Traffic Filter : Disabled perpetual
Cluster : Disabled perpetual
This platform has a Base license.
Serial Number: xxxxxxxxxxxxxxxxxx
Running Permanent Activation Key: xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
Configuration register is 0x1
FPGA UPGRADE Version : 3.0
FPGA GOLDEN Version : 3.0
ROMMON Version : 1.1.15
Image type : Release
Key Version : A
Configuration has not been modified since last system restart.
ciscoasa#
I think this should not the problem ....
After using more and more ASDM I had to another problem. After configuring v1.2 I couldn't dial in, so I tried to do a full restore. The restore works til 55% showing loading *.pkg file than nothing happens. After I interrupted it, it seems to work, but my AbyConnect client show a profile cisco asa (IPSEC) IPv4 and shows the message cryptographic algorythmen fails ..... If I interrupt this using my outside ip it works.
I never configured a profile asa (IPSEC) IPv4. I don't see this in the xml.files I found. Where I can delete it?
Is there a asa /asdm version combi you works well. I re, that sometimes ASDM do strange things depending on the version?
My thx in advance
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2021 04:54 AM
The recommended releases for an ASA 5506 are currently 9.14(2)8, 9.12(4)10 or 9.8(4)32. All with ASDM 7.15(1).
However none of those should affect your ability to run TLS 1.2 and DTLS 1.2 with customer ciphers. I have it setup fine on my ASA 5506 running 9.10.
You don't have a Firepower service module do you? ASA 5506-X doesn't support those from ASA 9.10 or later.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2021 03:42 AM
Hi Marvin,
I updated all on the recommend SW. My 5506-x doesn't have a sfr modules:
ciscoasa# sh module
Mod Card Type Model Serial No.
---- -------------------------------------------- ------------------ -----------
1 ASA 5506-X with SW, 8GE Data, 1GE Mgmt, AC ASA5506 xxxxxxxxxxxxx
sfr Unsupported Unsupported
Mod MAC Address Range Hw Version Fw Version Sw Version
---- --------------------------------- ------------ ------------ ---------------
1 7488.bb56.3243 to 7488.bb56.324c 2.3 1.1.15 9.12(4)10
Mod SSM Application Name Status SSM Application Version
---- ------------------------------ ---------------- --------------------------
Mod Status Data Plane Status Compatibility
---- ------------------ --------------------- -------------
1 Up Sys Not Applicable
ciscoasa#
So would it be possible to show me your running config, so I can compared with my config?
Thx in advance
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2020 02:44 PM
how did you get this working? i currently have 4.7 anyconnect that the clients connect to an ASA with 9.8 and I don't even the options to configure dtlvs1.2.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2020 02:49 PM
@Amafsha1DTLS v1.2 was introduced in ASA v9.10, you will need to upgrade.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2020 03:24 PM
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2020 10:54 AM
is it possible to go from 9.8 directly to 9.12 in 1 upgrade?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide