- Cisco Community
- Technology and Support
- Security
- VPN
- AnyConnect new feature - DTLSv1.2
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2018 02:02 PM - edited 02-21-2020 09:31 PM
With the release of v9.10.1, has anyone been able to get DTLSv1.2 working with AnyConnect sessions? (Our clients are v4.6.02074)
-If I don't specify dtlsv1.2, it will always establish the DTLS tunnel using dtlsv1.0.
-If I do specify dtlsv1.2 with the following config, the DTLS tunnel fails to establish with the message "%ASA-5-722043: Group <groupid> User <userid> IP <ipaddress> DTLS disabled: unable to negotiate cipher". Removing the "ssl cipher dtlsv1" line makes no difference.
ssl server-version tlsv1.2 dtlsv1.2
ssl cipher default custom "ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-GCM-SHA384"
ssl cipher dtlsv1 custom "AES256-SHA"
ssl cipher tlsv1.2 custom "ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-GCM-SHA384"
ssl cipher dtlsv1.2 custom "ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-GCM-SHA384"
ssl ecdh-group group20
ssl dh-group group24
Solved! Go to Solution.
- Labels:
-
AnyConnect
-
Other VPN Topics
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2018 06:09 PM
AnyConnect must also be upgraded to Release 4.7 for DTLS 1.2 support.
Reference:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2018 06:09 PM
AnyConnect must also be upgraded to Release 4.7 for DTLS 1.2 support.
Reference:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2018 10:40 PM
Thank you Marvin! I've been struggling with this for awhile and of course today the client update is released...
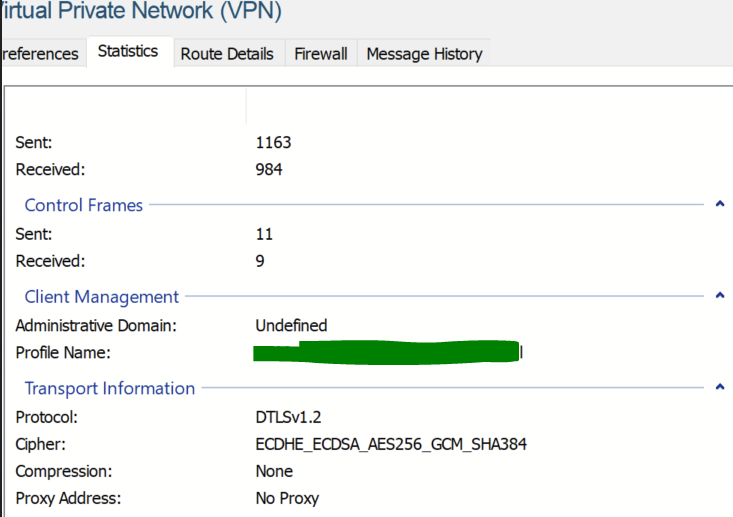
Confirmation session output is shown below.
DTLS-Tunnel:
Tunnel ID : 10156.3
Assigned IP : y.y.y.y Public IP : x.x.x.x
Encryption : AES-GCM-256 Hashing : SHA384
Ciphersuite : ECDHE-RSA-AES256-GCM-SHA384
Encapsulation: DTLSv1.2 UDP Src Port : 53241
UDP Dst Port : 443 Auth Mode : Certificate and userPassword
Idle Time Out: 30 Minutes Idle TO Left : 30 Minutes
Conn Time Out: 1440 Minutes Conn TO Left : 1437 Minutes
Client OS : Windows
Client Type : DTLS VPN Client
Client Ver : Cisco AnyConnect VPN Agent for Windows 4.7.00136
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2024 09:00 AM
I'm currently running asa version 9.16(4)18 with anyconnect 4.10 configured, and I can't get the following command to work:
ssl server-version tlsv1.2 dtlsv1.2
ssl cipher dtlsv1.2 custom "ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-GCM-SHA384"
It appears that dtlsv1.2 isn't an option anywhere.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2024 09:08 AM
@RANT what hardware are you using? DTLS 1.2 is not supported on 5506-X, 5508-X, and 5516-X
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvn63389
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2024 09:11 AM
yeah, just found out that limitation on another site. Grrrrrrr.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2018 08:01 PM - edited 12-05-2018 08:06 PM
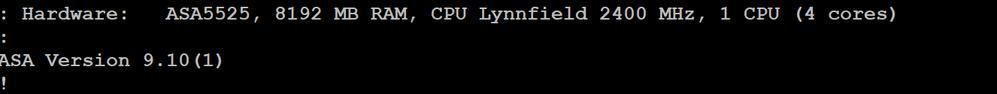
I just upgraded my lab - FTD 6.3 (includes LINA / ASA release 9.10(1)3) and pushing AnyConnect 4.7.00136. Note the TLS 1.2 connection:
> show vpn-sessiondb detail anyconnect Session Type: AnyConnect Detailed Username : user1 Index : 5 Assigned IP : 172.31.1.211 Public IP : 192.168.0.107 Protocol : AnyConnect-Parent SSL-Tunnel DTLS-Tunnel License : AnyConnect Premium Encryption : AnyConnect-Parent: (1)none SSL-Tunnel: (1)AES-GCM-256 DTLS-Tunnel: (1)AES256 Hashing : AnyConnect-Parent: (1)none SSL-Tunnel: (1)SHA384 DTLS-Tunnel: (1)SHA1 Bytes Tx : 32022 Bytes Rx : 34713 Pkts Tx : 129 Pkts Rx : 278 Pkts Tx Drop : 0 Pkts Rx Drop : 0 Group Policy : CCIELab_GP Tunnel Group : CCIELab_VPN Login Time : 03:52:57 UTC Thu Dec 6 2018 Duration : 0h:02m:21s Inactivity : 0h:00m:00s VLAN Mapping : N/A VLAN : none Audt Sess ID : ac1f0101000050005c089d19 Security Grp : none Tunnel Zone : 0 AnyConnect-Parent Tunnels: 1 SSL-Tunnel Tunnels: 1 DTLS-Tunnel Tunnels: 1 AnyConnect-Parent: Tunnel ID : 5.1 Public IP : 192.168.0.107 Encryption : none Hashing : none TCP Src Port : 23728 TCP Dst Port : 443 Auth Mode : userPassword Idle Time Out: 30 Minutes Idle TO Left : 27 Minutes Client OS : win Client OS Ver: 10.0.17134 Client Type : AnyConnect Client Ver : Cisco AnyConnect VPN Agent for Windows 4.7.00136 Bytes Tx : 8454 Bytes Rx : 0 Pkts Tx : 6 Pkts Rx : 0 Pkts Tx Drop : 0 Pkts Rx Drop : 0 SSL-Tunnel: Tunnel ID : 5.2 Assigned IP : 172.31.1.211 Public IP : 192.168.0.107 Encryption : AES-GCM-256 Hashing : SHA384 Ciphersuite : ECDHE-RSA-AES256-GCM-SHA384 Encapsulation: TLSv1.2 TCP Src Port : 23732 TCP Dst Port : 443 Auth Mode : userPassword Idle Time Out: 30 Minutes Idle TO Left : 27 Minutes Client OS : Windows Client Type : SSL VPN Client Client Ver : Cisco AnyConnect VPN Agent for Windows 4.7.00136 Bytes Tx : 8454 Bytes Rx : 496 Pkts Tx : 6 Pkts Rx : 5 Pkts Tx Drop : 0 Pkts Rx Drop : 0 DTLS-Tunnel: Tunnel ID : 5.3 Assigned IP : 172.31.1.211 Public IP : 192.168.0.107 Encryption : AES256 Hashing : SHA1 Ciphersuite : DHE-RSA-AES256-SHA Encapsulation: DTLSv1.0 UDP Src Port : 51520 UDP Dst Port : 443 Auth Mode : userPassword Idle Time Out: 30 Minutes Idle TO Left : 29 Minutes Client OS : Windows Client Type : DTLS VPN Client Client Ver : Cisco AnyConnect VPN Agent for Windows 4.7.00136 Bytes Tx : 15114 Bytes Rx : 34217 Pkts Tx : 117 Pkts Rx : 273 Pkts Tx Drop : 0 Pkts Rx Drop : 0 > show running-config ssl ssl server-version tlsv1.2 ssl cipher tlsv1.2 high ssl dh-group group1 ssl trust-point VPN_Cert_Enrollment ssl trust-point VPN_Cert_Enrollment Outside-Home >
> show version
---------[ vftd-new.ccielab.mrneteng.com ]----------
Model : Cisco Firepower Threat Defense for VMWare (75) Version 6.3.0 (Build 83)
UUID : 69c94e8a-92d2-11e7-b4ad-db36033706e7
Rules update version : 2018-12-03-001-vrt
VDB version : 307
----------------------------------------------------
> system support diagnostic-cli
Attaching to Diagnostic CLI ... Press 'Ctrl+a then d' to detach.
Type help or '?' for a list of available commands.
vftd-new> show ver
vftd-new> show version
---------[ vftd-new.ccielab.mrneteng.com ]----------
Model : Cisco Firepower Threat Defense for VMWare (75) Version 6.3.0 (Build 83)
UUID : 69c94e8a-92d2-11e7-b4ad-db36033706e7
Rules update version : 2018-12-03-001-vrt
VDB version : 307
----------------------------------------------------
Cisco Adaptive Security Appliance Software Version 9.10(1)3
Firepower Extensible Operating System Version 2.4(1.216)
Compiled on Tue 27-Nov-18 12:00 PST by builders
System image file is "boot:/asa9101-3-smp-k8.bin"
Config file at boot was "startup-config"
vftd-new up 1 hour 0 mins
Hardware: ASAv, 8192 MB RAM, CPU Pentium II 2100 MHz, 1 CPU (4 cores)
Model Id: ASAv30
Internal ATA Compact Flash, 50176MB
Slot 1: ATA Compact Flash, 50176MB
BIOS Flash Firmware Hub @ 0x0, 0KB
0: Int: Internal-Data0/0 : address is 000c.2924.8e3e, irq 10
1: Ext: GigabitEthernet0/0 : address is 000c.2924.8e48, irq 5
2: Ext: GigabitEthernet0/1 : address is 000c.2924.8e52, irq 9
3: Ext: GigabitEthernet0/2 : address is 000c.2924.8e5c, irq 11
4: Int: Internal-Control0/0 : address is 0000.0001.0001, irq 0
5: Int: Internal-Data0/0 : address is 0000.0000.0000, irq 0
6: Ext: Management0/0 : address is 000c.2924.8e3e, irq 0
7: Int: Internal-Data0/1 : address is 0000.0000.0000, irq 0
8: Int: Internal-Data0/2 : address is 0000.0000.0000, irq 0
Serial Number: 9ADK32SQAT2
Image type : Release
Key version : A
Configuration last modified by enable_1 at 03:41:24.871 UTC Thu Dec 6 2018
vftd-new>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2018 07:35 AM
Marvin, the config print out from your lab lists the the DTLS tunnel as using TLS 1.1 and SHA1. Was this an oversite in the thread?
Solved: Re: AnyConnect new feature - DTLSv1.2 - Cisco Community
DTLS-Tunnel: Tunnel ID : 5.3 Assigned IP : 172.31.1.211 Public IP : 192.168.0.107 Encryption : AES256 Hashing : SHA1 Ciphersuite : DHE-RSA-AES256-SHA Encapsulation: DTLSv1.0 UDP Src Port : 51520 UDP Dst Port : 443 Auth Mode : userPassword Idle Time Out: 30 Minutes Idle TO Left : 29 Minutes Client OS : Windows Client Type : DTLS VPN Client Client Ver : Cisco AnyConnect VPN Agent for Windows 4.7.00136 Bytes Tx : 15114 Bytes Rx : 34217 Pkts Tx : 117 Pkts Rx : 273 Pkts Tx Drop : 0 Pkts Rx Drop : 0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2018 07:37 AM
I noticed that. TLS is 1.2, DTLS is not.
I'm wondering if it's FTD vs. ASA thing. I need to upgrade my ASAv to 9.10(1) and compare.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2018 08:43 AM
I have scanned the requirements. Anyconnect 4.7 is required to enable TLS1.2. Do you also have to have a ECDHE Public Certificate? I am a little confused. There is a requirement for cipher strength in the documentation that I saw. Is this the case? 'ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-GCM-SHA384'
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2018 09:21 AM
From what I've seen, ciphers that start with ECDHE-RSA do not require an EC certificate. Ciphers that start with ECDHE-ECDSA do.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2018 10:30 AM
We are using Machine Certs and RSA SDI prox-ied thru ISE. In essence just username and password (RSA) with Machine Certificate Authentication. Our AC client is v4.4.03034. This should work just fine? Is this also the case? (I am little hesitant about it)
If v4.6.02074 works I don't see why not? ?
-> 'With the release of v9.10.1, has anyone been able to get DTLSv1.2 working with AnyConnect sessions? (Our clients are v4.6.02074)'
Thanks for the Help to all!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2018 11:00 AM
We were using v4.2 clients with v9.9 ASA code. I don't see 9.10.1 code as having a problem with older client versions. It's more like older client versions don't support more recently implemented features. If you are doing the same things, it shouldn't be a problem...but always test.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2018 10:45 AM - edited 12-14-2018 10:46 AM
I have tested ASA 9.10.1 with AnyConnect 4.7 and TLS 1.2. Connection comes up and shows correct DTLS version. as noted by others 4.7 is required for DTLS 1.2. Previous version of AnyConnect will work with this version of ASA, but will not connect with DTLS 1.2.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2018 10:51 AM
https://community.cisco.com/t5/vpn-and-anyconnect/anyconnect-4-7-00136-significant-mtu-bug/m-p/3764323
javentre Beginner
Beginner
12-15-2018 06:34 AM
AnyConnect 4.7.00136 - Significant MTU bug
There is a fairly major bug in AnyConnect 4.7.00136 regarding the tunnel MTU. If DTLS is enabled, it will send packets that are too big and many applications break. Ignoring the df-bit and/or specifying a low MTU doesn't workaround the issue. Disabling DTLS is the only workaround.
Syslog may show a flood of errors like this, where the packet is most often 16 bytes larger than the threshold.:
14 Dec 08 2018 20:06:33 722035 Group <ar-6> User <IC005654> IP <198.18.3.45> Received large packet 1276 (threshold 1260).
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide