- Cisco Community
- Technology and Support
- Security
- VPN
- ASA IOS 8.3 policy order-- 1. NAT, then...2. ACL, then... 3. ?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2023 02:11 PM
Hello.
Within an ASA-5525, the IOS 8.3 or later order of execution of policy-- Is it...
1. NAT, then...2. ACL, then... 3. (I forget the term-- it refers to when the NAT policy is executed lower in the order.)?
May you clarify, and answer my question?
Thank you.
Solved! Go to Solution.
- Labels:
-
AnyConnect
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2023 02:44 PM
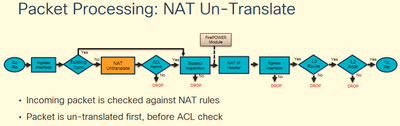
here is the packet flow from cisco live :
you can find the reference here :
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2023 02:44 PM
here is the packet flow from cisco live :
you can find the reference here :
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2023 02:59 PM
This is EXACTLY what I was looking for, though some questions remain...
May you please also explain the "third policy rule"-- It has to do with "nested" "or "conditional" (or something like that). It has to do with NAT or PAT translations. What is the name of this 3rd rule? What is the priority order of this 3rd rule? (It might be in the link from the text Cisco ASA Software Version 8.3 and later, but the link refers to many hundreds of pages of text.)
From your link-- "Cisco ASA has a built-in inspection engine that inspects each connection as per its pre-defined set of application-level functionality."-- What is the command to remove this "inspection engine"?
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2023 03:13 PM
why you want to remove inspection engine ??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2023 03:45 PM
troubleshooting.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2023 03:56 PM
you cant disable inspection but you can bypass it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2023 03:10 AM
Not sure you can to packet tracer see what is happening if you have ASA 8.3 code, I stopped using that code more than 10 years now.
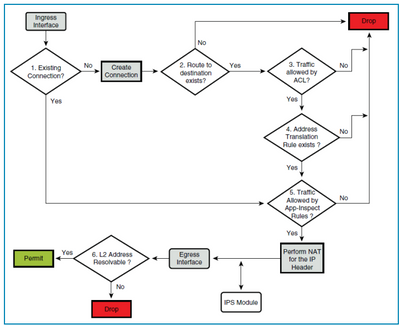
check this another view :
What is the command to remove this "inspection engine"? - the mode you mentioned does not have IPS module like SFR, are you looking to policy inspect ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2023 05:50 AM - edited 02-14-2023 06:24 AM
The data on this thread is invaluable. Thank you all.
This ASA has a long config. What is the best way to policy inspect?
Also, please see image attached. If the packet is dropped because of IPS module fail, then what command will show that packet was dropped? (#show asp drop , #{other command} ?)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2023 08:04 AM
Not like re-invent the wheel you can find many documents around for the best practice is based on the organisation's requirement.
https://community.cisco.com/t5/network-security/traffic-inspection-best-practices/td-p/1932294
the best practice is you need to be up to the level of security patches to meet first, so start from ASA 8.3 decade back end of life, so there are lot more security holes in that, before we consider best practice, make sure we are up to date.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2023 08:52 AM
show asp drop <<- this good indication
asa# show service-policy inspect <<protocol inspect>>
Global policy:
Service-policy: global_policy
Class-map: inspection_default
Inspect: dns preset_dns_map, packet 0, lock fail 0, drop 0, reset-drop 0,
5-min-pkt-rate 0 pkts/sec, v6-fail-close 0
message-length maximum client auto, drop 0
message-length maximum 512, drop 0
dns-guard, count 0
protocol-enforcement, drop 0
nat-rewrite, count 0Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide