- Cisco Community
- Technology and Support
- Security
- VPN
- Block an IP Address Trying to Brute Force into VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2023 01:10 PM
Hello,
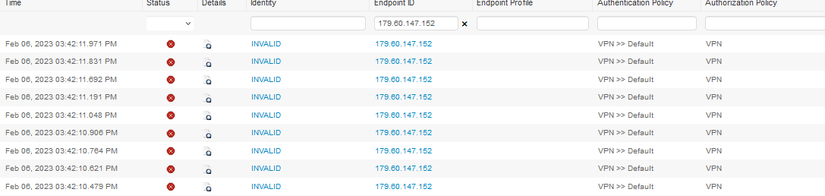
I noticed last week this IP Address attempting to VPN into our system. I noticed in our ISE LiveLogs this IP Address attempting to connect 100s of times a minute.
In an attempt to stop this address from even attempting the VPN, I looked on our ASA.
ASDM > Configuration > Firewall > Access Rules.
On the outside interface there was already the top rule configured to Deny access to a Network Object Group that just has a list of IP Addresses. So I added this questionable IP Address to that Object Group. However, I am still seeing the IP Address in ISE attempting to VPN in.
Any ideas why this address is still able to attempt auth, even though it should be getting denied before it even gets that far?
ASA Access Rule:
The IP address in question has been added to this "denied_access" group.
ISE LiveLogs:
Is adding this IP Address to the Access Rules applied to the outside interface, not the correct place to prevent this IP Address from even attempting a VPN connection?
Thanks in Advance,
Matt
Solved! Go to Solution.
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2023 01:13 PM - edited 02-06-2023 01:47 PM
@Matthew Martin a normal ACL on the ASA controls traffic "through" the ASA, not "to" one of the ASA's interfaces. You need can use a control plane ACL to restrict this IP address.
Create a normal ACL to deny the source IP address, then assign the ACL to the outside interface and append control-plane to the end. Example:-
access-group CPLANE in interface OUTSIDE control-plane
This control plane ACL won't interfere with the normal traffic through the ASA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2023 01:13 PM - edited 02-06-2023 01:47 PM
@Matthew Martin a normal ACL on the ASA controls traffic "through" the ASA, not "to" one of the ASA's interfaces. You need can use a control plane ACL to restrict this IP address.
Create a normal ACL to deny the source IP address, then assign the ACL to the outside interface and append control-plane to the end. Example:-
access-group CPLANE in interface OUTSIDE control-plane
This control plane ACL won't interfere with the normal traffic through the ASA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2023 10:18 AM
Thanks Rob, I created a network object-group and inserted a couple more IPs that I noticed in ISE, which was hitting our outside interface frequently and attempting to auth through VPN. I then created the deny ACL and applied the network object-group to it. And finally, ran the access-group command.
!
object-group network BLACKLIST_OUTSIDE
description Blacklisted IP Addresses for the Outside interface
network-object host xxx.xxx.xxx.xxx
network-object host yyy.yyy.yyy.yyy
network-object host zzz.zzz.zzz.zzz
!
!
access-list CPLANE_OUTSIDE extended deny ip object-group BLACKLIST_OUTSIDE any log
!
!
access-group CPLANE_OUTSIDE in interface outside control-plane
!So far so good. It's been about an hour since I applied the commands above and I have not seen anymore VPN attempts from those addresses in our ISE server's LiveLogs.
Thanks for the assistance, much appreciated!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2025 07:28 AM
Wierd thing.... done this on 4 pairs of ASA5516 (9.8(4)41) and it works...BUT
on my 5515, (same software version) I get no hits on the acl i.e. a show access-list CPLANE_OUTSIDE shows (hitcnt=0)
but in the logs I can see IP addresses in my object-group being used to attempt connection
Gone through the config many times, rebooted etc.etc.etc. Feel I am missing something obvious....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2023 01:57 PM
can you more elaborate ?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide