- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Cant get EasyVPN with NEM to work
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cant get EasyVPN with NEM to work
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2010 07:16 AM
Hi!
OK, i have made the following test setup:
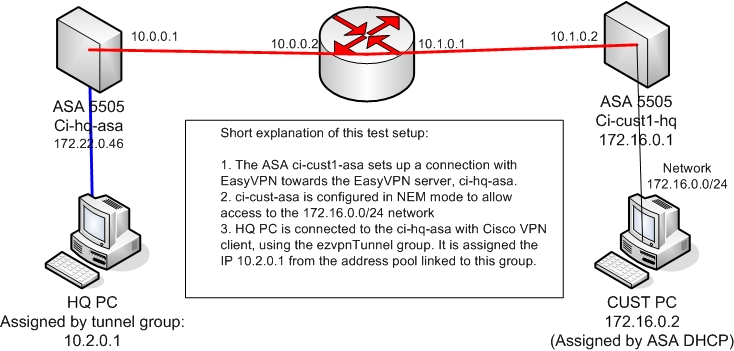
Im trying to get the following:
1. Connection from the HQ PC to the CUST PC
2. Cust PC to HQ PC
But my pings keep timeing out!!!!
Im using the attached configs
Id really appreciate some help guys its starting to annoy me
Thanks!
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2010 09:28 AM
hi,
On host hostname ci-hq-asa you have a route "route inside 172.16.0.0 255.240.0.0 172.22.0.1" but network 172.16.0.0/24 is outside. Can you revise your routing. check that you have the respective routes pointing in the right direction.
thanks
john
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2010 12:57 AM
Tried it but it doesnt change anything.
Also that rule is needed in the real environment for this to function there. The 172.16.0.0 network exists at the HQ site.
So the test environment has to mimic that.
For some reason it seems no data is send through the tunnel.
It should just sent packets from over one tunnel through the other tunnel and vice versa but its not doing that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2010 04:23 AM
Hello, first thing I noticed is routing problem. When you say :
"route inside 172.16.0.0 255.240.0.0 172.22.0.1 1" it meens that networks :
172.16.0.0, 172.17.0.0, 172.18.0.0,..172.22.0.0, ..172.31.0.0 all goes via 172.22.0.1!!!
So I will look at this first!
Likely solution is that you can be more specific when configuring routing on ci-hq-asa :
Live the old route because you said that you need it :
route inside 172.16.0.0 255.240.0.0 172.22.0.1 1
and add more specific for remote LAN :
route outside 172.16.0.0 255.255.255.0 10.1.0.2 1
I hope it helps,
good luck!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2010 07:00 AM
tried it out but i cant seem to get the routing correct
Anyone who can put the routes right for me?
I think it has something to do with the ACL....since NO traffic is passing through any of the 2 tunnels.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2010 07:15 AM
Ok, I will look later again, I'm bussy right now,
but you can do some troubleshooting that could help.
Try to ping continuously remote host and enable logging :
If you initiated console session do this and capture logs :
logging console informational
logging enable
logging on
You should receive usefull information on console session:
If you receive to much log lines and can not filter usefull information, try
to buffer logs :
logging console buffered
logging enable
logging on
and than use : show logging buffered
You should see some interesting information regarding your problem!
If you are using telnet or ssh use these commands:
logging monitor informational
logging enable
logging on
terminal monitor
or buffered :
logging bufered informational
logging enable
logging on
terminal monitor
One more command that could help is packet tracer command,
try with question mark!
Good luck!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2010 07:35 AM
Hello again,
I was thinking about your problem again and find small mistake
in my first reply. I wrote that you should add more specific route
route outside 172.16.0.0 255.255.255.0 10.1.0.2 1,
yes, but I made mistake, because next hop is not right (10.1.0.2),
it should be 10.0.0.2, your next hop, router!
So, correct is that you should add this route :
route outside 172.16.0.0 255.255.255.0 10.0.0.2 1
It should work, everything else looks fine!
Good luck
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2010 07:51 AM
Hi!
I've changed the route but still couldnt ping from 10.2.0.1 to 172.16.0.2.
I can also not ping from 10.0.0.1 to 172.16.0.2 but i CAN ping from 172.16.0.2 to 10.0.0.1....
Also i have been trying to find out what was wrong using tracert on the HQ PC and it keeps sending the pings over the wrong network interface.
It doesnt use the VPN adapter but the normal network adapter which is linked to a different network....
this shit is confusing
Appreciate the help though!
Stan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2010 07:53 AM
Do you have NAT-T configured on your VPN server?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2010 08:05 AM
Hi!
Yes, NAT-T is on, RRI is off.
Stan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2010 09:06 AM
Hello again,
I can not understand all of this because I have not the all information needed.
On HQ PC you mentioned some kind VPN adapter and multiple interfaces ?
Please give me routing table on HQ pc :
do this if it is a windows machine: open command prompt and enter command : route print, than press enter,
copy output and post to me in reply!
One more thing! Because Ci-Cust1-hq ASA is Easy VPN Remote client you should try first to ping from host Cust-PC to 10.2.0.1 address
to force tunnel to go up, than from HQ PC to remote PC - Cust-PC!!!
Good Luck
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2010 12:22 AM
Tried what you said with the pinging but it didn’t work.
The HQ PC is a VM, one interface is connected to the network here, the other is the VPN adapter.
I think the problem is the top route, as all connections to 172.16.0.2 use that route, but I didn’t put it in there.
Also I thought that when a VPN is connected all traffic is ALWAYS send over the VPN and the local connection is lost.
This HQ PC is connected with Cisco VPN client to the HQ ASA (simple IPSEC tunnel).
===========================================================================
Active Routes:
Network Destination Netmask Gateway Interface Metric
0.0.0.0 0.0.0.0 192.168.253.129 192.168.253.156 10
10.2.0.0 255.255.255.248 10.2.0.2 10.2.0.2 10
10.2.0.0 255.255.255.0 10.2.0.1 10.2.0.2 1
10.2.0.2 255.255.255.255 127.0.0.1 127.0.0.1 10
10.255.255.255 255.255.255.255 10.2.0.2 10.2.0.2 10
127.0.0.0 255.0.0.0 127.0.0.1 127.0.0.1 1
172.22.0.46 255.255.255.255 192.168.253.129 192.168.253.156 1
192.168.253.128 255.255.255.128 192.168.253.156 192.168.253.156 10
192.168.253.129 255.255.255.255 192.168.253.156 192.168.253.156 1
192.168.253.156 255.255.255.255 127.0.0.1 127.0.0.1 10
192.168.253.255 255.255.255.255 192.168.253.156 192.168.253.156 10
224.0.0.0 240.0.0.0 10.2.0.2 10.2.0.2 10
224.0.0.0 240.0.0.0 192.168.253.156 192.168.253.156 10
255.255.255.255 255.255.255.255 10.2.0.2 10.2.0.2 1
255.255.255.255 255.255.255.255 192.168.253.156 10004 1
255.255.255.255 255.255.255.255 192.168.253.156 192.168.253.156 1
Default Gateway: 192.168.253.129
===========================================================================
Persistent Routes:
None
Does this make sense to you?
EDIT: Also the VPN adapter does not seem to have a default gateway! :S
Kind Regards,
Stan Damen
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2010 12:42 AM
Hello again,
you right, all traffic goes via default route.
You can add persistent route on HQ PC for remote LAN, try this :
First disconect from VPN on HQ pc, then add foloving persistent route :
route -p ADD 172.16.0.0 MASK 255.255.255.0 172.22.0.46 METRIC 1
Now on your routing table from HQ you should see this route in
bottom of the output from route print command !
Than connect to VPN again, and than try to ping again!
Good Luck
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2010 12:53 AM
Hello again,
I forgot to remind you to first try to ping from remote cust-PC to HQ PC, to force tunnel to come up,
and then from HQ to remote! You should see encripting and decripting packets increase
on output from :
show cryptyo ipsec sa command on booth ASAs!
Good Luck!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2010 02:25 AM
I managed to fix it by using different IPSEC profiles and Group Policies for the 2 VPN connections.
Now i can ping from side to side without any problems.
I found a new problem now, but gunna work on that for a while.
Thanks for the input and help though! would not have found the issue without you
Stan
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide