- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Cisco AnyConnect::How to hide "Security Warning : Untrusted Certificate"
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2014 05:45 AM - edited 02-21-2020 07:53 PM
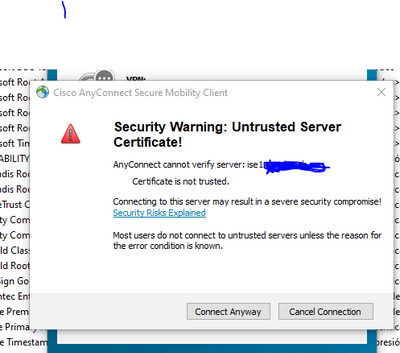
Whenever I connect to my ASA using Anyconnect client, attached warning message always appear and there is no option to Trust it or import certificate so that it should not appear next time.
Anyone please help to make the option visible to trust certificate or make this warning go away.
I tried Anyconnect 3.1.05152 and the latest also.
Solved! Go to Solution.
- Labels:
-
AnyConnect
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2014 07:29 AM
The best way is to purchase a certificate for your ASA and install it there.
If you can't or don't want to do that, then you should create a well-formed self-signed certificate on the ASA. You should ensure your have a good 2048-bit RSA key (or create a new one when you start).
If you use a fully qualified domain name (FQDN) for the VPN users to access the ASA that should be the Common Name (CN) in the certificate. That addresses item #1 in the warning.
Your clients will need to download and install the certificate into their trusted root CA store. You can do this by browsing to the web portal and using your browser tools to copy the ASA's SSL certificate to a local file and then importing it, overriding the default location and choosing the Trusted root CA store. That addresses item #2.
Item #3 is also due to how the self-signed certificate was created. If you follow the configuration guide you should have a well-formed certificate and not get that error.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2014 06:11 AM
Yes - it appears you are hitting that bug. Your configuration looks fine otherwise.
As noted in the bug search tool, the problem was fixed in 3.1(5160). So you can just upload the pkg files and image configuration lines on the ASA to the latest and that will get deployed to clients.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2014 07:27 AM
Simply install a third party, trusted certificate on the firewall
Cisco ASA 5500 - Using a Third Party Digital Certificate
Pete
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2014 07:29 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2014 07:29 AM
The best way is to purchase a certificate for your ASA and install it there.
If you can't or don't want to do that, then you should create a well-formed self-signed certificate on the ASA. You should ensure your have a good 2048-bit RSA key (or create a new one when you start).
If you use a fully qualified domain name (FQDN) for the VPN users to access the ASA that should be the Common Name (CN) in the certificate. That addresses item #1 in the warning.
Your clients will need to download and install the certificate into their trusted root CA store. You can do this by browsing to the web portal and using your browser tools to copy the ASA's SSL certificate to a local file and then importing it, overriding the default location and choosing the Trusted root CA store. That addresses item #2.
Item #3 is also due to how the self-signed certificate was created. If you follow the configuration guide you should have a well-formed certificate and not get that error.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2014 06:04 AM
Thanks for your answer.
I used Anyconnect wizard from ASDM to configure Anyconnect profile.
But when I try to select Group from Anyconnect Client (After putting IP of firewall and at the prompt to select group and enter login info), I am not able to select the Group that I want to. It always falls back to another Group...
What couild be the problem?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2014 06:16 AM
Are you saying that your selection is not honored when you login?
Or does the dropdown list always show something other than what you want at the top of the list?
The first issue would be because of the setup on the ASA locking certain users to certain profiles.
The second is just an artifact of how the client parses the set of available profiles stored locally (and whether or not the profile has been defined on the ASA).
If you share the following we can have a look at what's going on:
show run webvpn
show run group-policy
show run tunnel-group
(You can sanitize any sensitive information.)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2014 09:23 AM
Yes, when I select Group A in dropdown list, it starts processing and fall backs to Group B even before i enter a username.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2014 11:17 AM
Can you share the output of the show commands I mentioned?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2014 11:19 PM
Here is the output:
ASA# show run webvpn
webvpn
enable outside
anyconnect-essentials
anyconnect image disk0:/anyconnect-win-3.1.05152-k9.pkg 1
anyconnect image disk0:/anyconnect-win-2.5.2014-k9.pkg 2
anyconnect enable
tunnel-group-list enable
ASA# show run tunnel-group
tunnel-group 22.22.22.22 type ipsec-l2l
tunnel-group 22.22.22.22 general-attributes
default-group-policy GroupPolicy_22.22.22.22
tunnel-group 22.22.22.22 ipsec-attributes
ikev1 pre-shared-key *****
tunnel-group 33.33.33.33 type ipsec-l2l
tunnel-group 33.33.33.33 general-attributes
default-group-policy GroupPolicy_33.33.33.33
tunnel-group 33.33.33.33 ipsec-attributes
ikev1 pre-shared-key *****
tunnel-group Anyconnect-Wisconsin type remote-access
tunnel-group Anyconnect-Wisconsin general-attributes
address-pool Anyconnect-pool
authentication-server-group CA-LDAP-WM LOCAL
default-group-policy NO_VPN_ACCESS
tunnel-group Anyconnect-Wisconsin webvpn-attributes
group-alias Anyconnect-Wisconsin enable
tunnel-group RemoteAccess_Wisconsin type remote-access
tunnel-group RemoteAccess_Wisconsin general-attributes
address-pool Anyconnect-pool
authentication-server-group CA-LDAP-WM LOCAL
default-group-policy NO_VPN_ACCESS
tunnel-group RemoteAccess_Wisconsin ipsec-attributes
ikev1 pre-shared-key *****
tunnel-group WM-Wisconsin type remote-access
tunnel-group WM-Wisconsin general-attributes
address-pool Anyconnect-pool
authentication-server-group CA-LDAP-WM
default-group-policy GroupPolicy_WM-Wisconsin
tunnel-group WM-Wisconsin webvpn-attributes
group-alias WM-Wisconsin enable
ASA# show run group-policy
group-policy NO_VPN_ACCESS internal
group-policy NO_VPN_ACCESS attributes
vpn-simultaneous-logins 0
group-policy GroupPolicy_Anyconnect-Wisconsin internal
group-policy GroupPolicy_Anyconnect-Wisconsin attributes
wins-server none
dns-server value 10.155.17.246 10.198.72.46
vpn-simultaneous-logins 10
vpn-tunnel-protocol ssl-client
default-domain value XYZ-AG.org
group-policy GroupPolicy_WM-Wisconsin internal
group-policy GroupPolicy_WM-Wisconsin attributes
wins-server none
dns-server value 10.155.17.246
vpn-tunnel-protocol ssl-client
default-domain value XYZ-AG.org
group-policy GroupPolicy_33.33.33.33 internal
group-policy GroupPolicy_33.33.33.33 attributes
vpn-tunnel-protocol ikev1
group-policy GroupPolicy_22.22.22.22 internal
group-policy GroupPolicy_22.22.22.22 attributes
vpn-tunnel-protocol ikev1
group-policy GroupPolicy1 internal
group-policy GroupPolicy1 attributes
vpn-tunnel-protocol ikev1
group-policy RemoteAccess_Wisconsin internal
group-policy RemoteAccess_Wisconsin attributes
dns-server value 10.155.17.246 10.198.72.46
vpn-simultaneous-logins 10
vpn-tunnel-protocol ikev1
default-domain value XYZ-AG.org
Whenever I try to select WM-Wisconsin, It always falls back to Anyconnect-Wisconsin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2014 01:47 AM
Now I deleted Alias for Anyconnect-Wisconsin, now its letting me select other Group.
It looks like it is not letting me choose a group...but i don't see any config on ASA which does that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2014 02:05 AM
Hello Marvin,
This is weird but seems to be an issue of AnyConnect V 3.1.05152.
I upgraded to latest and its slved.
But how to make it work in 05152 ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2014 02:30 AM
Bug CSCum89178 ..... ASA 8.4 + AnyConnect 3.1.05152 create this problem.
Do you have any suggestions?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2014 06:11 AM
Yes - it appears you are hitting that bug. Your configuration looks fine otherwise.
As noted in the bug search tool, the problem was fixed in 3.1(5160). So you can just upload the pkg files and image configuration lines on the ASA to the latest and that will get deployed to clients.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2023 05:49 AM
You think using 3rd party and entering fictitious CN or FQDN is better way to keep discreet who the device belongs to?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-14-2021 03:22 PM
Hi,
How did you fix this issue , I have the same error but not with VPN , I'm using anyconnect just to authentication and posture. I downloaded de cisco ise cert and installed on my machine but it still happening, wich certificate should I install in my computer?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide