- Cisco Community
- Technology and Support
- Security
- VPN
- Confirming Phase 1 and Phase 2 issues
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Confirming Phase 1 and Phase 2 issues
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2016 11:05 AM
I am having an issue with an older Cisco ASA running ASDM. I am trying to initiate a Site to Site VPN with a customer who has a Dell SonicWALL. Unfortunately for me, Cisco is not as straight forward when setting up VPN.
Here are the parameters needed :
IKE Phase 1-
Main
Group2
3DES
SHA1
28800 Seconds lifetime
IPsec Phase 2
ESP
3DES
SH1
GROUP 2
28800 Seconds Lifetime
My fist step was to run through the setup wizard which have me the opportunity to select my interface, network objects for interesting traffic, and to select ikev1 and ikev2.
The wizard does not allow me to select exactly which set of parameters to use for phase 1 just a series of default settings.
How do I know that the correct phase 1 and phase 2 settings were selected? I have a series of error messages (IKE policy is global. It is shared by all IPsec connection profiles)
Because of this, I cannot know for sure whether I am configured correctly on my end for phase 1. I do get some granularity (And I stress some) with Phase 2.
Additionally, I cannot add crypto isakmp policy, it only allows ikev1 policy.
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2016 12:23 PM
Hi
First, if you have a newer version of the ASA the code will say ikev1 instead of isakmp. So you have probably been looking at an older guide.
The easiet way to verify that you have configured it correctly is through the CLI, but it is also possible from ASDM (Monitoring>VPN).
Verify phase 1 using CLI:
show crypto ikev1 sa
You should see the remote peers public IP address in the list.
Very phase 2 using the CLI:
show crypto ipsec sa peer <peer-ip-address>
You will need to first initiate some traffic so that it tries to traverse the VPN, or else it wont come up. You can either use a real host or the packet-tracer utility in the ASA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2016 06:25 AM
I have been attemping an L2L vpn setup using the ASDM wizard. The wizard defaults to a seriesof global phase 1 and phase 2 policies. I have a customer with a Dell SonicWALL and they have specific parameters for IKE and IPSec. How can I override the global settings and configure specific settings for this customer? Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2016 09:51 AM
Hi Allan,
You can definitely create a custom configuration on the wizard:

If you are only using IKev1

In this step you can select the ikev1 policies and ipsec policies that you need to match with the other site:

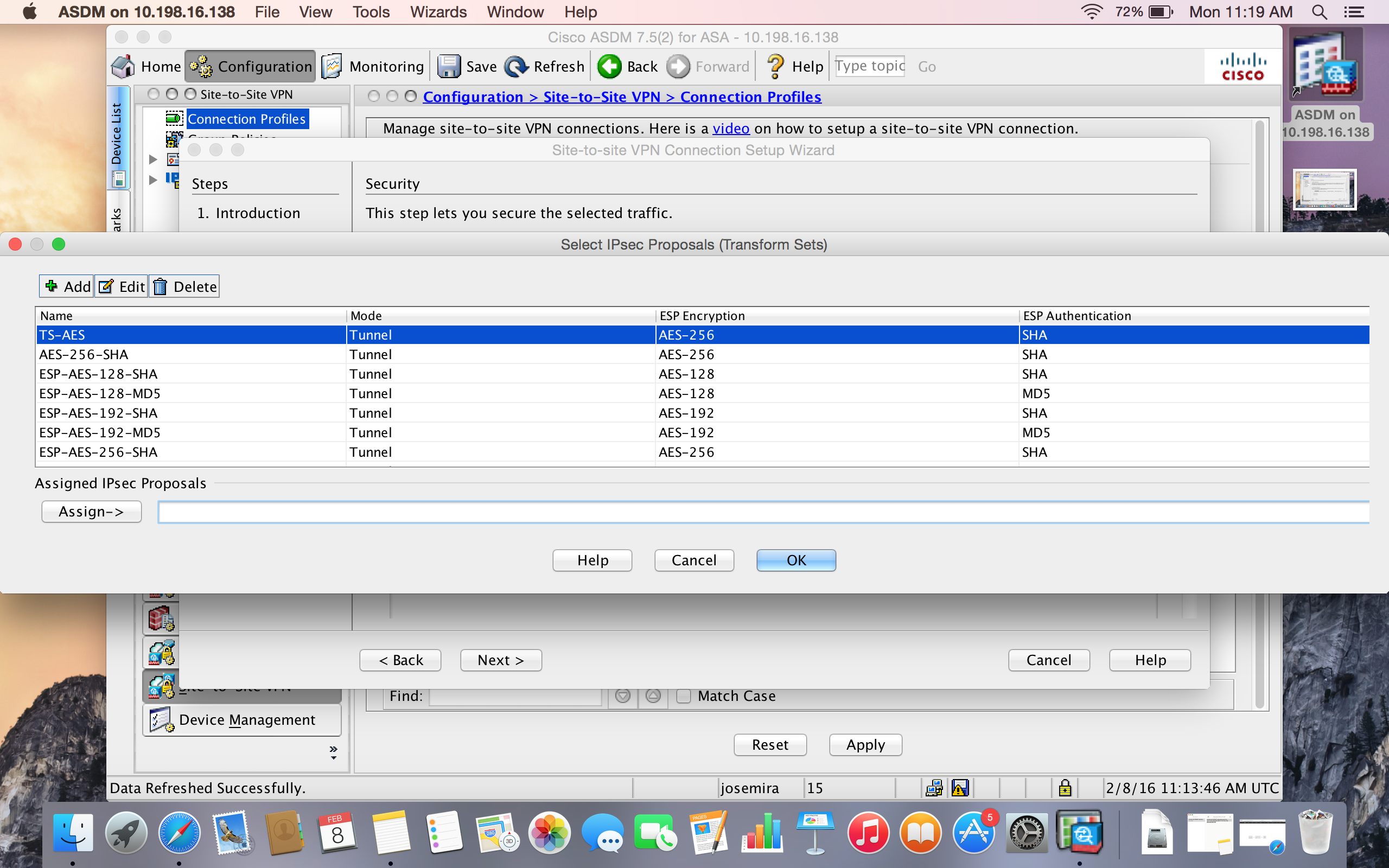
Remember that phase 2 also requires interesting traffic or the ACL on the crypto map to be mirrored.
-JP-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2016 10:00 AM
The IKE Policy is greyed out. When i select manage I receive the follwoing message "IKE policy is global. It is shared by all IPSec connection profiles". How can i overcome this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2016 01:49 PM
When you click manage you should be also able to click on and add the ikev1 policy that you need.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2016 03:08 PM
I agree that you should but the global policy does not allow you to customize the ike settings. there are a number of settings listed by priority number. I am unable to customize.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

