- Cisco Community
- Technology and Support
- Security
- VPN
- DMVPN tunnel and dialer interface
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2020 07:06 AM
Currently the networking I'm on is using dynamic crypto maps to encrypt data going over an ISDN 30 link. We need to move away from this so I've configured up DMVPN with ipsec encryption. It looks like the DMVPN and encryption are working fine and I can ping each GRE tunnel on either end. But I think data isn't going over the tunnel interfaces, each router connects to each other via a dialer interface and I've assigned the dialer interface on both routers as the source of each tunnel.
But when I turn off a tunnel interface on one router I can still ping the other router's IP address and the LAN ip address on the inside of the other router. I also captured packets with Cisco monition capture to see if I can find anything, I captured packets from the tunnel interface and it shows data but no GRE tunnel headings in the packets.
How can I be certain that data is going over the tunnel and being encrypted? Are GRE tunnels compatible with dialer interfaces?
Any help will be greatly appreciated.
Solved! Go to Solution.
- Labels:
-
DMVPN
-
IPSEC
-
Other VPN Topics
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2020 09:07 AM
That sounds correct.
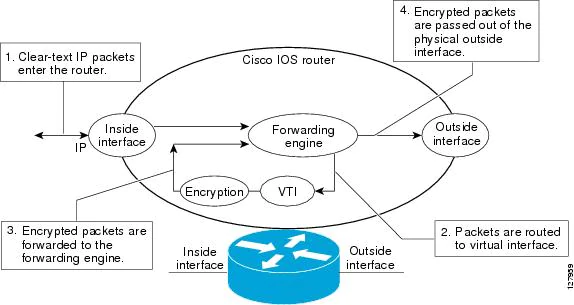
After packets arrive on the inside interface, the forwarding engine switches the packets to the VTI, where they are encrypted. The encrypted packets are handed back to the forwarding engine, where they are switched through the outside interface.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2020 07:20 AM
Hi,
No reason why this should not work. Run the command “show crypto ipsec sa” and check to see if encaps and decaps are increasing when you transmit data over the VPN.
Please provide the configuration for review and the output of that command.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2020 09:22 AM - edited 07-10-2020 01:55 PM
Hi Rob,
Here are the configs for hub and spoke. After doing some changes I think I've managed to get packets going over the tunnel as that crypto ipsec sa command shows the encaps and decaps increasing when I ping the inside address on the hub, but the ping still fails for some reason. I think the main issues was that the spoke was learning about the 192.168.254 address over the dialer interface, not the tunnel, so it was then sending data over the dialer, i stopped this by making the dialer passive on the hub but I still cant get it to fully work,
Regards,
Ben
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2020 09:33 AM
Has an eigrp adjacency been formed?
What IP address do you ping and what is the source?
Are the correct routes in the routing table?
Do encaps and decaps increase on both routers?
Provide the output of:
show dmvpn
show ip nhrp
show ip route
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2020 08:46 AM
Hello Rob,
Sorry for the late reply, it seems like I've got it working. I think the router was learning EIGRP routes from the dialer interface and not the tunnel itself. After making EIGRP passive on the dialer interface it looks like data is going over the tunnel.
But I've another question, when I do a monitor capture on the router (capturing data on the tunnel interface and serial 0/1/0:7) and look at the pcap file through wire shark it shows encrypted data on the serial 0/1/0:7 interface but the data on the tunnel capture is not encrypted. Is this working as intended? So if someone was listening in between the ISDN connection the data will be encrypted, even tho a monitor capture on the tunnel interface shows its not encrypted.
As when I take the encrypted profile off the tunnel interfaces on the hub and spoke routers no data is being encrypted on the serial 0/1/0:7 or the tunnel interface.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2020 09:07 AM
That sounds correct.
After packets arrive on the inside interface, the forwarding engine switches the packets to the VTI, where they are encrypted. The encrypted packets are handed back to the forwarding engine, where they are switched through the outside interface.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide