- Cisco Community
- Technology and Support
- Security
- VPN
- Help configuring Anyconnect
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2012 10:01 AM - edited 02-21-2020 06:21 PM
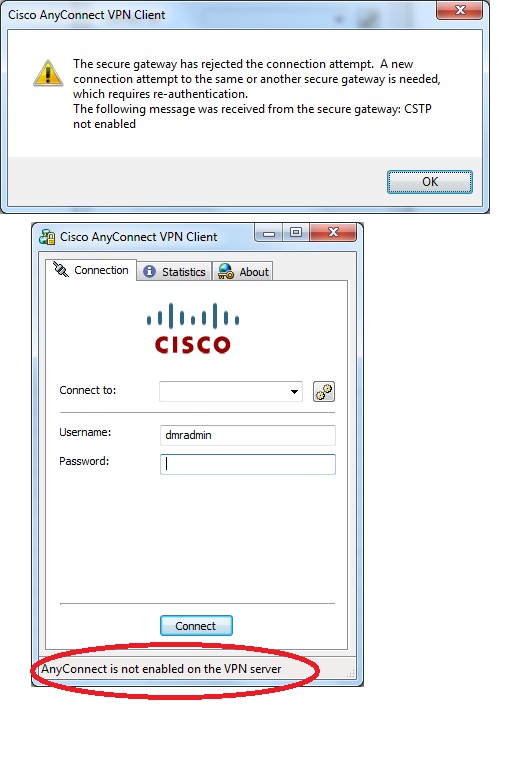
I am trying to configure Anyconnect for the 1st time via the GUI, though I am comfortable with the command line if required. I am familiar with PIX and IOS prior to 8.3 so this is my 1st time with newer versions. My equipment is in a lab environment at the moment but will be placed into production shortly. I recieve the following errors when trying to establish an Anyconnect VPN connection with the local account on the ASA. Below is my config
ASA Version 8.6(1)2
!
hostname TOR1PLXSD01
enable password sxZETAvnsVuPSnUc encrypted
passwd FomDbcd6ujnk.spR encrypted
names
!
interface GigabitEthernet0/0
description Management
speed 1000
duplex full
nameif Inside
security-level 100
ip address 172.21.20.1 255.255.255.0 standby 172.21.20.2
!
interface GigabitEthernet0/1
speed 1000
duplex full
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/1.20
description Plexxus Data
vlan 20
nameif data
security-level 50
ip address 172.16.18.1 255.255.255.0 standby 172.16.18.2
!
interface GigabitEthernet0/1.25
description DMZ
vlan 25
nameif DMZ
security-level 25
no ip address
!
interface GigabitEthernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/4
nameif Outside
security-level 0
ip address x.x.x.1 255.255.255.224 x.x.x.2
interface GigabitEthernet0/5
description LAN/STATE Failover Interface
!
interface Management0/0
nameif management
security-level 100
ip address 192.168.1.1 255.255.255.0
management-only
!
boot system disk0:/asa861-2-smp-k8.bin
ftp mode passive
dns domain-lookup data
dns server-group DefaultDNS
name-server 172.16.18.21
name-server 172.16.18.22
object network OBJ_INSIDE-HOSTS_172.21.20.0
subnet 172.21.20.0 255.255.255.0
object network OBJ_DATA-HOSTS_172.16.18.0
subnet 172.16.18.0 255.255.255.0
access-list acl_outside extended permit icmp any any
access-list acl_data extended permit icmp any any
access-list acl_inside extended permit icmp any any
access-list acl_dmz extended permit icmp any any
pager lines 24
logging enable
mtu Inside 1500
mtu data 1500
mtu DMZ 1500
mtu Outside 1500
mtu management 1500
ip local pool vpn_pool1 172.16.22.5-172.16.22.250 mask 255.255.255.0
ip local pool vpn_pool2 172.16.23.5-172.16.23.250 mask 255.255.255.0
failover
failover lan unit primary
failover lan interface Failover GigabitEthernet0/5
failover link Failover GigabitEthernet0/5
failover interface ip Failover 4.4.4.1 255.255.255.0 standby 4.4.4.2
icmp unreachable rate-limit 1 burst-size 1
icmp permit any Inside
icmp permit any data
icmp permit any DMZ
icmp permit any Outside
asdm image disk0:/asdm-66114.bin
no asdm history enable
arp timeout 14400
!
object network OBJ_INSIDE-HOSTS_172.21.20.0
nat (Inside,Outside) dynamic 68.71.198.102
object network OBJ_DATA-HOSTS_172.16.18.0
nat (data,Outside) dynamic 68.71.198.102
access-group acl_inside in interface Inside
access-group acl_data in interface data
access-group acl_dmz in interface DMZ
access-group acl_outside in interface Outside
route Outside 0.0.0.0 0.0.0.0 68.71.198.97 1
route data 172.16.5.0 255.255.255.0 172.16.18.3 1
route data 172.16.10.0 255.255.255.0 172.16.18.3 1
route data 172.16.13.0 255.255.255.0 172.16.18.3 1
route data 172.16.14.0 255.255.255.0 172.16.18.3 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
http server enable
http 172.21.20.0 255.255.255.0 Inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
telnet timeout 5
ssh 172.21.20.0 255.255.255.0 Inside
ssh timeout 5
console timeout 0
no vpn-addr-assign aaa
no vpn-addr-assign dhcp
dhcpd address 192.168.1.2-192.168.1.254 management
dhcpd enable management
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
enable Outside
anyconnect-essentials
anyconnect image disk0:/anyconnect-win-2.5.2014-k9.pkg 1
anyconnect enable
group-policy AnyConnectClientPolicy internal
group-policy AnyConnectClientPolicy attributes
wins-server none
dns-server value 172.16.18.21 172.16.18.22
vpn-tunnel-protocol ikev2 ssl-client
default-domain value plexxus.ca
address-pools value vpn_pool1 vpn_pool2
username dmradmin password 1ZwOzoVS5TWIvR0h encrypted
tunnel-group AnyConnectClientProfile type remote-access
tunnel-group AnyConnectClientProfile general-attributes
default-group-policy AnyConnectClientPolicy
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:659360d147ccf882ab6cbb6e170ca8d2
: end
TOR1PLXSD01
ASA Version 8.6(1)2
!
hostname TOR1PLXSD01
enable password sxZETAvnsVuPSnUc encrypted
passwd FomDbcd6ujnk.spR encrypted
names
!
interface GigabitEthernet0/0
description Management
speed 1000
duplex full
nameif Inside
security-level 100
ip address 172.21.20.1 255.255.255.0 standby 172.21.20.2
!
interface GigabitEthernet0/1
speed 1000
duplex full
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/1.20
description Plexxus Data
vlan 20
nameif data
security-level 50
ip address 172.16.18.1 255.255.255.0 standby 172.16.18.2
!
interface GigabitEthernet0/1.25
description DMZ
vlan 25
nameif DMZ
security-level 25
no ip address
!
interface GigabitEthernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/4
nameif Outside
security-level 0
ip address 68.71.198.100 255.255.255.224 standby 68.71.198.101
!
interface GigabitEthernet0/5
description LAN/STATE Failover Interface
!
interface Management0/0
nameif management
security-level 100
ip address 192.168.1.1 255.255.255.0
management-only
!
boot system disk0:/asa861-2-smp-k8.bin
ftp mode passive
dns domain-lookup data
dns server-group DefaultDNS
name-server 172.16.18.21
name-server 172.16.18.22
object network OBJ_INSIDE-HOSTS_172.21.20.0
subnet 172.21.20.0 255.255.255.0
object network OBJ_DATA-HOSTS_172.16.18.0
subnet 172.16.18.0 255.255.255.0
access-list acl_outside extended permit icmp any any
access-list acl_data extended permit icmp any any
access-list acl_inside extended permit icmp any any
access-list acl_dmz extended permit icmp any any
pager lines 24
logging enable
mtu Inside 1500
mtu data 1500
mtu DMZ 1500
mtu Outside 1500
mtu management 1500
ip local pool vpn_pool1 172.16.22.5-172.16.22.250 mask 255.255.255.0
ip local pool vpn_pool2 172.16.23.5-172.16.23.250 mask 255.255.255.0
failover
failover lan unit primary
failover lan interface Failover GigabitEthernet0/5
failover link Failover GigabitEthernet0/5
failover interface ip Failover 4.4.4.1 255.255.255.0 standby 4.4.4.2
icmp unreachable rate-limit 1 burst-size 1
icmp permit any Inside
icmp permit any data
icmp permit any DMZ
icmp permit any Outside
asdm image disk0:/asdm-66114.bin
no asdm history enable
arp timeout 14400
!
object network OBJ_INSIDE-HOSTS_172.21.20.0
nat (Inside,Outside) dynamic 68.71.198.102
object network OBJ_DATA-HOSTS_172.16.18.0
nat (data,Outside) dynamic 68.71.198.102
access-group acl_inside in interface Inside
access-group acl_data in interface data
access-group acl_dmz in interface DMZ
access-group acl_outside in interface Outside
route Outside 0.0.0.0 0.0.0.0 68.71.198.97 1
route data 172.16.5.0 255.255.255.0 172.16.18.3 1
route data 172.16.10.0 255.255.255.0 172.16.18.3 1
route data 172.16.13.0 255.255.255.0 172.16.18.3 1
route data 172.16.14.0 255.255.255.0 172.16.18.3 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
http server enable
http 172.21.20.0 255.255.255.0 Inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
telnet timeout 5
ssh 172.21.20.0 255.255.255.0 Inside
ssh timeout 5
console timeout 0
no vpn-addr-assign aaa
no vpn-addr-assign dhcp
dhcpd address 192.168.1.2-192.168.1.254 management
dhcpd enable management
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
enable Outside
anyconnect-essentials
anyconnect image disk0:/anyconnect-win-2.5.2014-k9.pkg 1
anyconnect enable
group-policy AnyConnectClientPolicy internal
group-policy AnyConnectClientPolicy attributes
wins-server none
dns-server value 172.16.18.21 172.16.18.22
vpn-tunnel-protocol ikev2 ssl-client
default-domain value plexxus.ca
address-pools value vpn_pool1 vpn_pool2
username dmradmin password 1ZwOzoVS5TWIvR0h encrypted
tunnel-group AnyConnectClientProfile type remote-access
tunnel-group AnyConnectClientProfile general-attributes
default-group-policy AnyConnectClientPolicy
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:659360d147ccf882ab6cbb6e170ca8d2
: end
Solved! Go to Solution.
- Labels:
-
AnyConnect
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2012 11:19 AM
I am glad to hear you fixed it
Please check this out:
object network VPN_POOL
subnet 192.168.1.0 255.255.255.0 --> adjust this to your real IP range
!
object-group network INTERNAL_NETWORKS_VPN
object-network 192.168.2.0 255.255.255.0 ----> This is the internal network you want to reach across the tunnel.
!
nat (inside,outside) 1 source static INTERNAL_NETWORKS_VPN INTERNAL_NETWORKS_VPN destination static
VPN_POOL VPN_POOL route-lookup
That is pretty much the NAT Exempt on 8.3, 8.4, 8.6...
Further information:
ASA Pre-8.3 to 8.3 NAT configuration examples
Keep me posted.
Thanks.
Portu.
Please rate any helpful posts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2012 10:33 AM
Hi Philippe,
Please make the following change:
tunnel-group AnyConnectClientProfile webvpn-attributes
group-url https://x.x.x.1/test
!
Then, in the AC connect field, enter: x.x.x.1/test
Let me know if that works for you.
Most likely, this is your issue:
ASA SSL VPN Tunnel Group Group-URL and Group-Alias selection methods
Keep me posted.
Thanks.
Please rate any helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2012 11:06 AM
Thanks,
I actually fixed it moments before your post.
I added
tunnel-group-list enable
tunnel-group AnyConnectClientProfile webvpn-attributes
group-alias AnyConnect enable
Seems that there is a check box in on the GUI that needs to be selected. Under Anyconnect connection profiles , check off Allow user to select connection profile......otherwise DefaultWebVPNGroup will be the connection profile
Though I could use help configuring the no nat access_lists since I am not familiar with the commands in 8.6
I am use to
access-list no_nat extended permit .....
nat (inside) 0 access-list no_nat
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2012 11:19 AM
I am glad to hear you fixed it
Please check this out:
object network VPN_POOL
subnet 192.168.1.0 255.255.255.0 --> adjust this to your real IP range
!
object-group network INTERNAL_NETWORKS_VPN
object-network 192.168.2.0 255.255.255.0 ----> This is the internal network you want to reach across the tunnel.
!
nat (inside,outside) 1 source static INTERNAL_NETWORKS_VPN INTERNAL_NETWORKS_VPN destination static
VPN_POOL VPN_POOL route-lookup
That is pretty much the NAT Exempt on 8.3, 8.4, 8.6...
Further information:
ASA Pre-8.3 to 8.3 NAT configuration examples
Keep me posted.
Thanks.
Portu.
Please rate any helpful posts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2012 11:34 AM
I think I get it...
I want VPN users to access the "data" interface only, not the "inside"
I created
object network OBJ_DATA-HOSTS_172.16.18.0
subnet 172.16.18.0 255.255.255.0
object network OBJ_VPN_SUBNETS_172.16.22.0-172.16.23.255
range 172.16.22.0 172.16.23.255
nat (data,Outside) source static OBJ_DATA-HOSTS_172.16.18.0 OBJ_DATA-HOSTS_172.16.18.0 destination static OBJ_VPN_SUBNETS_172.16.22.0-172.16.23.255 OBJ_VPN_SUBNETS_172.16.22.0-172.16.23.255
Is this correct ? What does the "route-lookup" command do ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2012 11:41 AM
Hi Philippe,
Yes it looks great.
On the other hand:
http://www.cisco.com/en/US/docs/security/asa/asa84/command/reference/no.html#wp1792563
Please let me know if you have further questions, otherwise please mark this post as answered.
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2012 12:25 PM
Thanks for all your help. Got it working.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2012 12:32 PM
Awesome
I hope you have a nice day.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide