- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Help setup routing through VPN tunnel
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-08-2022 06:15 PM
Hi,
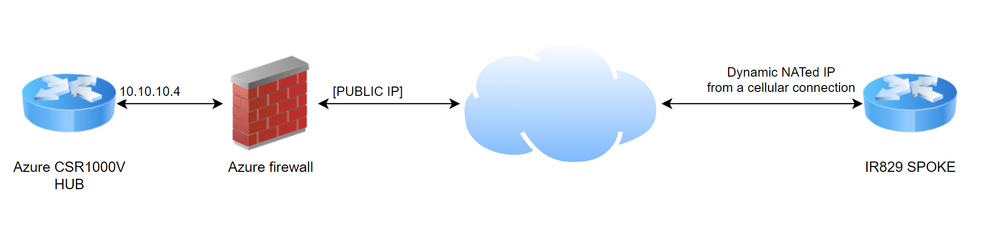
I have the following setup and I have the HUB and SPOKE connected through a IKEV2 tunnel using FlexVPN. The problem is I can't ping remote subnets from either router.
- 172.16.5.0 VLAN @ ISR
- 172.16.5.0 VLAN @ ISR
- 172.16.11.0 @ CSR (A loopback just for now)
I don't have any dynamic routing. I've tried setting up different access lists and static routs but none of them work. I've confirmed the VPN is up and ready using "show crypto ikev2 sa".
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-09-2022 12:45 AM
Try sending the routes static instead of using the ACL.
crypto ikev2 authorization policy IKEV2_AUTHORIZATION
route set interface
route set remote ipv4 172.15.5.0 255.255.255.0
route set remote ipv4 172.15.6.0 255.255.255.0
Alternatively you could use EIGRP to distribute the routes
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-08-2022 11:40 PM
@nadeesh.sam you've only got the FlexVPN authorisation policy applied on CISCOCloudRouter and not the IR829, so I doubt IR829 is sending its routes to the other router.
Can you provide the output of "show crypto ikev2 sa detail"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-09-2022 12:03 AM - edited 06-09-2022 04:31 PM
Hi Rob!
Thanks for taking look. What do I have to change to assign the authorisation policy? IKEV2 SA details are below for your reference.
This is the SPOKE
IR829#sh crypto ikev2 sa detailed
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
1 172.16.2.5/4500 [PUBLIC IP]/4500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA512, Hash: SHA512, DH Grp:5, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/48 sec
CE id: 1002, Session-id: 2
Status Description: Negotiation done
Local spi: 53BEAF22B9E02AA5 Remote spi: E67F6B961F4390D5
Local id: SPOKE.FLEXVPN.LAB
Remote id: HUB.FLEXVPN.LAB
Local req msg id: 2 Remote req msg id: 0
Local next msg id: 2 Remote next msg id: 0
Local req queued: 2 Remote req queued: 0
Local window: 5 Remote window: 5
DPD configured for 0 seconds, retry 0
Fragmentation not configured.
Dynamic Route Update: disabled
Extended Authentication not configured.
NAT-T is detected inside
Cisco Trust Security SGT is disabled
Initiator of SA : Yes
Remote subnets:
192.168.1.254 255.255.255.255
10.10.0.0 255.255.0.0
172.16.11.0 255.255.255.0
0.0.0.0 0.0.0.0
Post NATed Address : 123.456.789.000
IPv6 Crypto IKEv2 SA
This is the HUB
CISCOCloudRouter#sh crypto ikev2 sa detailed
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
1 10.10.10.4/4500 123.123.123.123/64916 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA512, Hash: SHA512, DH Grp:5, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/64 sec
CE id: 1001, Session-id: 1
Status Description: Negotiation done
Local spi: E67F6B961F4390D5 Remote spi: 53BEAF22B9E02AA5
Local id: HUB.FLEXVPN.LAB
Remote id: SPOKE.FLEXVPN.LAB
Local req msg id: 0 Remote req msg id: 2
Local next msg id: 0 Remote next msg id: 2
Local req queued: 0 Remote req queued: 2
Local window: 5 Remote window: 5
DPD configured for 0 seconds, retry 0
Fragmentation not configured.
Dynamic Route Update: enabled
Extended Authentication not configured.
NAT-T is detected inside
Cisco Trust Security SGT is disabled
Initiator of SA : No
Post NATed Address : [PUBLIC IP]
IPv6 Crypto IKEv2 SA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-09-2022 12:08 AM - edited 06-09-2022 12:08 AM
@nadeesh.sam you just need to reference the authorisation policy under the IKEv2 Profile. You've already got the authorisation policy IKEV2_AUTHORIZATION defined, you just haven't referenced it.
crypto ikev2 profile IKEV2_PROFILE
aaa authorization group psk list FLEXVPN_LOCAL IKEV2_AUTHORIZATION
From your output I can tell the IR829 has received the routes (Remote Subnets) from the Hub
Remote subnets:
192.168.1.254 255.255.255.255
10.10.0.0 255.255.0.0
172.16.11.0 255.255.255.0
0.0.0.0 0.0.0.0
....but no routes (Remote subnets) on the IR829.
So by applying the authorisation policy this will send the routes defined in the ACL FLEXVPN_ROUTES to the hub.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-09-2022 12:29 AM
I really appreciate you taking the time to help. I added following like to the IR829 but I still can't see the remote subnets on the HUB
crypto ikev2 profile IKEV2_PROFILE
aaa authorization group psk list FLEXVPN_LOCAL IKEV2_AUTHORIZATION
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-09-2022 12:31 AM - edited 06-09-2022 12:32 AM
@nadeesh.sam you will need to clear the IKEv2 SA in order for the routes to be sent during the IKEv2 exchange.
clear crypto ikev2 sa
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-09-2022 12:34 AM - edited 06-09-2022 04:32 PM
Just did that. Still getting the same result on the HUB
Tunnel-id Local Remote fvrf/ivrf Status
1 10.10.10.4/4500 123.123.123.123/64916 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA512, Hash: SHA512, DH Grp:5, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/8 sec
CE id: 1004, Session-id: 4
Status Description: Negotiation done
Local spi: 8C22E0DFECB924F4 Remote spi: 83186C49BD5F10B0
Local id: HUB.FLEXVPN.LAB
Remote id: SPOKE.FLEXVPN.LAB
Local req msg id: 0 Remote req msg id: 2
Local next msg id: 0 Remote next msg id: 2
Local req queued: 0 Remote req queued: 2
Local window: 5 Remote window: 5
DPD configured for 0 seconds, retry 0
Fragmentation not configured.
Dynamic Route Update: enabled
Extended Authentication not configured.
NAT-T is detected inside
Cisco Trust Security SGT is disabled
Initiator of SA : No
Post NATed Address : [PUBLIC IP]
IPv6 Crypto IKEv2 SA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-09-2022 12:45 AM
Try sending the routes static instead of using the ACL.
crypto ikev2 authorization policy IKEV2_AUTHORIZATION
route set interface
route set remote ipv4 172.15.5.0 255.255.255.0
route set remote ipv4 172.15.6.0 255.255.255.0
Alternatively you could use EIGRP to distribute the routes
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-09-2022 04:44 PM
Hi Rob,
I'm back at the router. I've added the routes manually and I'm still getting the same SA on the HUB. I'll look at EIGRP to see how to set it up.
What would be the reason for this not to work? It's doing NAT-T but I assume its not the issue here.\\
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-19-2022 06:44 PM
I made both routers to send static routes and removed ACL from the config. And it works now. Thanks Rob!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-09-2022 02:25 AM
I had to leave the office. I'll try this tomorrow and post an update. Thank you!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide