- Cisco Community
- Technology and Support
- Security
- VPN
- Re: IKEV2 VPN Erro"Login Denied , unauthorized connection mechanism , contact your administrator"
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
IKEV2 VPN Erro"Login Denied , unauthorized connection mechanism , contact your administrator"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2019 10:40 AM
Dear All,
I´m trying to configure an IKEV2 VPN anyconnect on my ASA 5505 and when I try to connect in the anyconnect client, I receive the msg: "Login Denied , unauthorized connection mechanism , contact your administrator".
Can you help please
Kind Regards
- Labels:
-
AnyConnect
-
Remote Access
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2019 11:56 AM
At first glance it doesnt look like you have only assigned the ASDM_Launcher_Access_TrustPoint_0 to the inside interface while you have enabled IKEv2 only on the outside interface. Try assigning the trustpoint to the outside interface and test. Or if you are testing on the inside interface, enable ikev2 on the inside interface.
ssl trust-point ASDM_Launcher_Access_TrustPoint_0 inside vpnlb-ip
ssl trust-point ASDM_Launcher_Access_TrustPoint_0 inside
crypto ikev2 enable outside client-services port 443
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2019 11:02 AM
Hi marius,
Thanks for your reply.
I have tried your config, but still does not work.
best Regards
Hamid
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2019 03:03 PM
Hi all
Just I found, I can establish connection using my iPhone, but I can not connect to internet.
Still no connection in windows 10 using anyconnect.
can you help ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2019 03:24 PM
Without seeing your configuration it is difficult to tell what the issue is. Most likely you either do not have a nat statment for outside to outside ex. nat (outside,outside)... and maybe missing same-security-traffic permit intra-interface command.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2019 03:33 PM
Hi
Please see the attachments file and below.
ftp mode passive
same-security-traffic permit intra-interface
object network obj_any
subnet 0.0.0.0 0.0.0.0
object network NETWORK_OBJ_192.168.100.0_28
subnet 192.168.100.0 255.255.255.240
object network obi-inside
subnet 192.168.1.0 255.255.255.0
object network obj-AnyconnectPool
subnet 192.168.100.0 255.255.255.0
object network obj-inside
subnet 192.168.1.0 255.255.255.0
object network NETWORK_OBJ_192.168.10.0_24
subnet 192.168.10.0 255.255.255.0
pager lines 24
logging enable
logging asdm informational
mtu inside 1500
mtu outside 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
nat (inside,outside) source static any any destination static NETWORK_OBJ_192.168.100.0_28 NETWORK_OBJ_192.168.100.0_28 no-proxy-arp route-lookup
!
object network obj_any
nat (inside,outside) dynamic interface
object network obj-AnyconnectPool
nat (outside,outside) dynamic interface
object network obj-inside
nat (inside,outside) dynamic interface
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
http server enable
http 192.168.1.0 255.255.255.0 inside
no snmp-server location
no snmp-server contact
crypto ipsec ikev2 ipsec-proposal DES
protocol esp encryption des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal 3DES
protocol esp encryption 3des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES
protocol esp encryption aes
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES192
protocol esp encryption aes-192
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES256
protocol esp encryption aes-256
protocol esp integrity sha-1 md5
crypto ipsec security-association pmtu-aging infinite
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev2 ipsec-proposal AES256 AES192 AES 3DES DES
crypto map outside_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map outside_map interface outside
crypto ca trustpoint ASDM_Launcher_Access_TrustPoint_0
enrollment self
fqdn none
subject-name CN=192.168.1.1,CN=ciscoasa
keypair ASDM_LAUNCHER
crl configure
crypto ca trustpool policy
crypto ca certificate chain ASDM_Launcher_Access_TrustPoint_0
certificate 86a7b55d
308201c9 30820132 a0030201 02020486 a7b55d30 0d06092a 864886f7 0d010105
05003029 3111300f 06035504 03130863 6973636f 61736131 14301206 03550403
130b3139 322e3136 382e312e 31301e17 0d313931 30323731 34323731 325a170d
32393130 32343134 32373132 5a302931 11300f06 03550403 13086369 73636f61
73613114 30120603 55040313 0b313932 2e313638 2e312e31 30819f30 0d06092a
864886f7 0d010101 05000381 8d003081 89028181 00addaf3 40bc330e d092fc56
a567244f 54e3da66 f76b000e d2d2f83b d16560dc cb502059 3a7dba5d 6fa0a9bb
29031474 34cb1530 de34f217 b79d8266 8e85e5d8 2b742852 18456764 d7c0d0e2
6b7ab10a 279e6718 db3fbdce 263fd703 d3bd95bb 46021ab5 4057f9cf f51fa2aa
7a6b7297 1c6232b9 11db1ed4 3f42b6a6 410ee3e6 83020301 0001300d 06092a86
4886f70d 01010505 00038181 002148a3 7857c07e 6aaf8b72 4848ace9 8db83e38
67e4c3fa 50aa3900 55620070 5a24a4fa 7e56ba2c 47183e5c 69946cec 2b15ac2b
141d355e 5afb0146 6d365a7e 6922a7fd df54bc19 cb1062b6 511eca18 72c60cda
0a7907be b57c32bf c22fe17e 3097b92d a6f25f41 d17b7bef 7c7288ab 5abe2ad7
dc5f3c3f 58bcfc2a 60b9b158 0f
quit
crypto ikev2 policy 1
encryption aes-256
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 10
encryption aes-192
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 20
encryption aes
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 30
encryption 3des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 40
encryption des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 enable outside client-services port 443
crypto ikev2 remote-access trustpoint ASDM_Launcher_Access_TrustPoint_0
telnet timeout 5
no ssh stricthostkeycheck
ssh timeout 5
ssh key-exchange group dh-group1-sha1
console timeout 0
dhcpd auto_config outside
!
dhcpd address 192.168.1.5-192.168.1.254 inside
dhcpd enable inside
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ssl trust-point ASDM_Launcher_Access_TrustPoint_0 inside vpnlb-ip
ssl trust-point ASDM_Launcher_Access_TrustPoint_0 inside
webvpn
enable outside
anyconnect-essentials
anyconnect image disk0:/anyconnect-win-4.7.04056-webdeploy-k9.pkg 1
anyconnect profiles remote_client_profile disk0:/remote_client_profile.xml
anyconnect enable
tunnel-group-list enable
tunnel-group-preference group-url
group-policy GroupPolicy_remote internal
group-policy GroupPolicy_remote attributes
wins-server none
dns-server value 8.8.8.8
vpn-tunnel-protocol ikev2
default-domain none
webvpn
anyconnect profiles value remote_client_profile type user
username hamid password L0w/6yVKbR5Zm91N encrypted
tunnel-group remote type remote-access
tunnel-group remote general-attributes
address-pool vpnpool
default-group-policy GroupPolicy_remote
tunnel-group remote webvpn-attributes
group-alias remote enable
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2019 05:35 PM - edited 10-29-2019 05:36 PM
Hi Hamid,
I do not see the “same-security-traffic permit intra-interface” command on the config, as Marius stated on his previous reply.
Go ahead, add the command and test again the access to the internet.
Let us know about the results.
Rate if it helps.
Regards,
Josue Brenes
TAC - VPN Engineer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-30-2019 10:21 AM
Hi
The “same-security-traffic permit intra-interface” on second line of my configuration.
I did applied again, still no internet connection.
Best Regards
Hamid
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-30-2019 01:50 PM
Hi
I added the command below, I got internet connection, but as ssl vpn connection.
I need IKEv2 IPsec connection.
group-policy GroupPolicy_remote attributes
vpn-tunnel-protocol ikev2 ssl-client
Can you help ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2019 02:11 AM
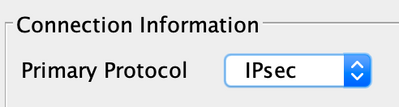
Have you enable "ipsec" instead of SSL i the AnyConnect profile remote_client_profile?
In the profile go to Server List and edit the server entry and under the Server tab (which should be the first tab) change Connection Information > Primary Protocol to IPsec
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2019 10:53 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2019 07:30 AM
It has been resolved by change the ip address in anyconnect profile
to the internet provider address and use down load automatic for anyconncet from the web as manually did not work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2019 10:59 PM
Also, I do not see any routing statements.
Please remember to select a correct answer and rate helpful posts
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide