- Cisco Community
- Technology and Support
- Security
- VPN
- Re: IPSEC lan to lan VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
IPSEC lan to lan VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2012 10:49 AM - edited 02-21-2020 06:05 PM
Hi,
I have some problem with ipsec configuration. Here is a topology:
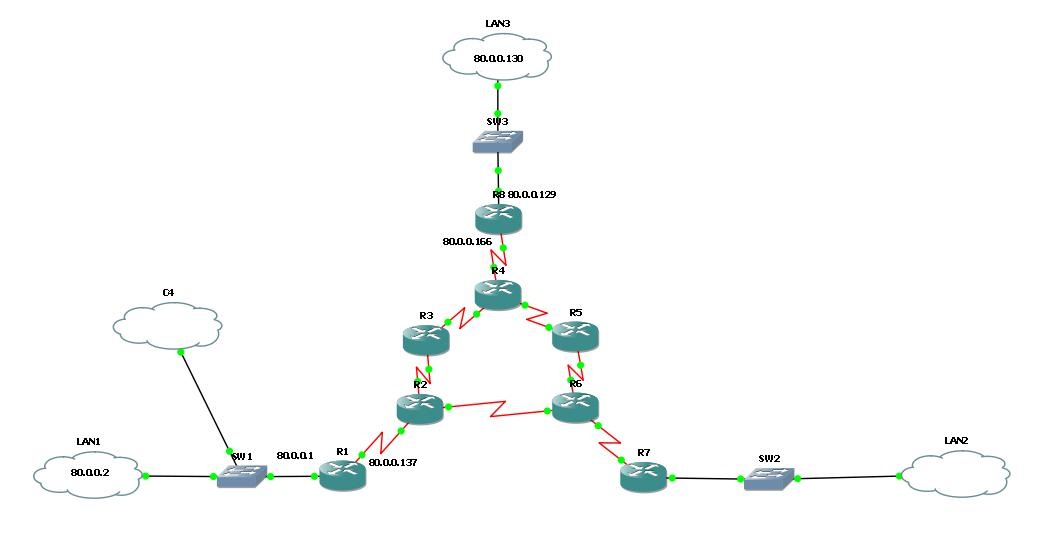
I want to create VPNs between LANs so i started co configure vpn from LAN1 to LAN3. The problem is that packets are encrypted only when source (and/or destination) address of ping is the addres of router interface. When i want to ping from host to one of LANs, (ex. on R1: 'ping 80.0.0.130 source 80.0.0.1') im geting a massage:
%CRYPTO-4-RECVD_PKT_NOT_IPSEC: Rec'd packet not an IPSEC packet. (ip) vrf/dest_addr= /80.0.0.1, src_addr= 80.0.0.130, prot= 1
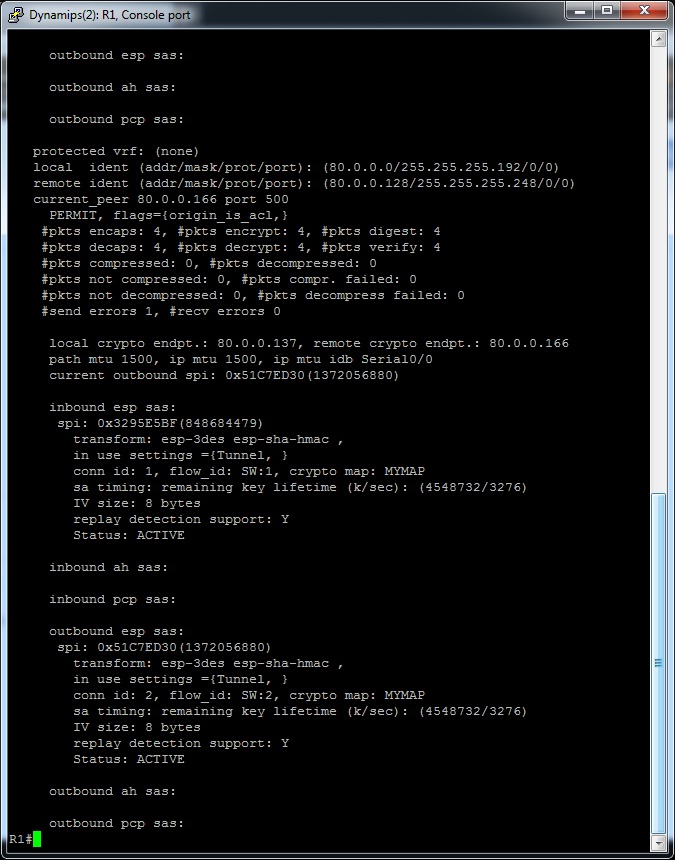
Ping 80.0.0.129 source 80.0.0.1 works fine, and 'show crypto ipsec sa' confims that packets are encrypted, also wireshark confirms encryption.
Lan1: 80.0.0.0 /26
Lan3: 80.0.0.128/29
All three LAN interfaces, ale Windows Loopback.
Can someone help me, and tell where i made a mistake ?
Here is a configuration:
R1:
!
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R1
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
ip cef
!
!
!
!
!
multilink bundle-name authenticated
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
archive
log config
hidekeys
!
!
crypto isakmp policy 110
encr 3des
hash sha
authentication pre-share
crypto isakmp key 6 cisco1234 address 80.0.0.166
!
crypto ipsec transform-set ZESTAW esp-3des esp-sha-hmac
mode transport
!
crypto map MYMAP 10 ipsec-isakmp
set peer 80.0.0.166
set transform-set ZESTAW
match address 102
!
!
!
!
!
!
!
interface FastEthernet0/0
ip address 80.0.0.1 255.255.255.192
duplex auto
speed auto
mpls ip
!
interface Serial0/0
ip address 80.0.0.137 255.255.255.252
mpls ip
clock rate 2000000
crypto map MYMAP
!
interface FastEthernet0/1
no ip address
shutdown
duplex auto
speed auto
!
interface Serial0/1
no ip address
shutdown
clock rate 2000000
!
router ospf 1
log-adjacency-changes
network 80.0.0.0 0.0.0.63 area 0
network 80.0.0.136 0.0.0.3 area 0
!
ip forward-protocol nd
!
!
ip http server
no ip http secure-server
!
access-list 102 permit ip 80.0.0.0 0.0.0.63 80.0.0.128 0.0.0.7
access-list 102 permit ip 80.0.0.0 0.0.0.63 80.0.0.64 0.0.0.63
!
!
!
!
!
!
control-plane
!
!
!
!
!
!
!
!
!
!
line con 0
line aux 0
line vty 0 4
login
!
!
end
R8:
!
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R8
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
ip cef
!
!
!
!
!
multilink bundle-name authenticated
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
archive
log config
hidekeys
!
!
crypto isakmp policy 110
encr 3des
hash sha
authentication pre-share
crypto isakmp key 6 cisco1234 address 80.0.0.137
!
!
crypto ipsec transform-set ZESTAW esp-3des esp-sha-hmac
mode transport
!
crypto map MYMAP 10 ipsec-isakmp
set peer 80.0.0.137
set transform-set ZESTAW
match address 102
!
!
!
!
!
!
!
interface FastEthernet0/0
ip address 80.0.0.129 255.255.255.248
duplex auto
speed auto
mpls ip
!
interface Serial0/0
ip address 80.0.0.166 255.255.255.252
mpls ip
clock rate 2000000
crypto map MYMAP
!
interface FastEthernet0/1
no ip address
shutdown
duplex auto
speed auto
!
interface Serial0/1
no ip address
shutdown
clock rate 2000000
!
router ospf 1
log-adjacency-changes
network 80.0.0.128 0.0.0.7 area 0
network 80.0.0.164 0.0.0.3 area 0
!
!
ip forward-protocol nd
!
!
ip http server
no ip http secure-server
!
access-list 102 permit ip 80.0.0.128 0.0.0.7 80.0.0.0 0.0.0.63
access-list 102 permit ip 80.0.0.128 0.0.0.7 80.0.0.64 0.0.0.63
!
!
!
!
!
!
control-plane
!
!
!
!
!
!
!
!
!
!
line con 0
line aux 0
line vty 0 4
login
!
!
end
- Labels:
-
IPSEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2012 08:40 PM
The crypto ACL 102 does not mirror image on both routers.
You should only have the following configured:
R1:
access-list 102 permit ip 80.0.0.0 0.0.0.63 80.0.0.128 0.0.0.7
R8:
access-list 102 permit ip 80.0.0.128 0.0.0.7 80.0.0.0 0.0.0.63
Also make sure that routing is correct for both sides.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2012 01:16 AM
Thank you for the reply!
Unfortunately, i've tried a lot of acl, also the one you have suggest and it still doesnt work.
I also tried acl:
R1:
access-list 102 permit ip host 80.0.0.2 host 80.0.0.130
R8:
access-list 102 permit ip host 80.0.0.130 host 80.0.0.2 (use qemu host/ loopback/ vbox host)
And its still:
%CRYPTO-4-RECVD_PKT_NOT_IPSEC: Rec'd packet not an IPSEC packet. (ip) vrf/dest_addr= /80.0.0.1, src_addr= 80.0.0.130, prot= 1
but when i use router interfaces:
R1:
access-list 102 permit ip host 80.0.0.1 host 80.0.0.129
R8:
access-list 102 permit ip host 80.0.0.129 host 80.0.0.1
Encryption and pings goes fine.
About the rouring, i use ospf on entire network and without IPSec i can ping every node form all places.
I really dont know whats going on, everything looks fine in config.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2012 05:35 AM
Did you clear the ipsec tunnel on both end after making the changes on the acl?
clear cry sa
clear cry isa sa
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2012 03:03 PM
Thank you for the reply!
Now ive done this, but it still doesnt work. When im changing ACL, to make it faster im doing it in cfg file, and then reload the router, so i think, all SA are cleared anyway ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2012 03:06 PM
Yes, if you reload the router, it will clear all the SA. And I assume that you do save the config after you change it before reloading the router?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2012 03:29 PM
Yes, im checking 'sh runn' after reload to be sure its all right.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

