- Cisco Community
- Technology and Support
- Security
- VPN
- Re: IPSEC VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 02:56 AM
Hello Team,
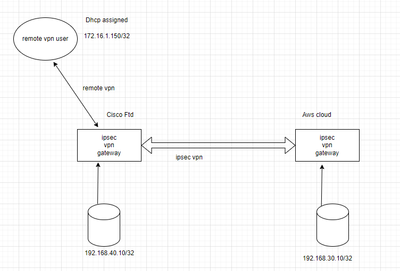
I have below topology : -
I have ipsec vpn from on-prem to aws cloud. the two endpoints [192.168.40.10/32, 192.168.30.10/32] work fine as they are allowed on the encryption domain.
I have users using remote vpn to connect to on-prem dc to access on-prem resources - they can reach 192.168.40.10/32. There is a need for them to reach a portal on aws cloud [192.168.30.10/32].
How can I achieve this?
Your support will be appreciated.
Solved! Go to Solution.
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 03:01 AM
Two simple point
One add RA VPN pool to ACL of ipsec VPN
Second use no-NAT that includes the RA VPN and subnet .30
That it.
By the way you have other post about ikev2 did you try ikev1? Was that issue solved?
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 03:48 AM
I think you are referring to the security ACLs in this case, not the encryption domains ACLs? anyway, if you want to allow the remote users traffic to hit AWS portal you would need to treat the remote users subnet as if it is a local subnet to the on-prem firewall, which means it has to be added to the on-prem local encryption domains to AWS VPN tunnel, a NAT exemption rule with (nat (outside,outside) ...) must be created (I assumed your on-prem firewall external interface is called outside), and on AWS side the remote users VPN subnet must be configured to be routed back to the on-prem firewall over the VPN tunnel.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 03:01 AM
Two simple point
One add RA VPN pool to ACL of ipsec VPN
Second use no-NAT that includes the RA VPN and subnet .30
That it.
By the way you have other post about ikev2 did you try ikev1? Was that issue solved?
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 03:03 AM
not yet, its on prod, approval process is yet to conclude, then i can test. i put it on hold till done with approval.
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 03:05 AM
what about allowed networks/encryption domain?
assume i have multiple ipsec vpns, the acl am touching is just specific to this ipsec vpn? cause i kinda have bundled all my ipsec acls together.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 03:07 AM
Sorry it mandatory to add RA VPN pool to ACL.
And using one ACL is work but not optimal.
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 03:28 AM
do i need to add it to the encryption domain? or under access control on policies? am using cisco ftd
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 03:28 AM
What do you mean by bundled all my IPsec ACLs together?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 03:38 AM
if i have 40 ipsec tunnels, i dont have corresponding 40 acls, i have 2 acls, one for incoming , one for outgoing, but in each all protected networks are in each acl respectively ie. if its incoming, one acl, has entries for all remote networks as destination and all local subnets for local network.
Hope i make sense.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 03:48 AM
I think you are referring to the security ACLs in this case, not the encryption domains ACLs? anyway, if you want to allow the remote users traffic to hit AWS portal you would need to treat the remote users subnet as if it is a local subnet to the on-prem firewall, which means it has to be added to the on-prem local encryption domains to AWS VPN tunnel, a NAT exemption rule with (nat (outside,outside) ...) must be created (I assumed your on-prem firewall external interface is called outside), and on AWS side the remote users VPN subnet must be configured to be routed back to the on-prem firewall over the VPN tunnel.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 04:08 AM
understood,
so ideally if like an addition local on-prem subnet.
Got it thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 03:32 AM - edited 04-25-2024 03:34 AM
the protected networks is what am referring to as encryption domain, so am adding the ra pool here, or under policies, or both?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 03:35 AM - edited 04-25-2024 03:36 AM
Protect network' add RA VPN in this part of vpn topolgy.
Also I forget you need route in other Peer for RA VPN.
And for policy' if you meaning ACP you also need to add it there.
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 03:39 AM
AWS Peer? or on-prem peer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 03:41 AM
AWS friend
Prem peer RA VPN is direct connect so no need route
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 04:13 AM
Other point sure you will ask it later
No-NAT
If the RA VPN is connect to same IPsec interface then no-NAT will be
Nat(out'out)
If the RA VPN have different interface than IPsec then
Nat(RA VPN interface, IPsec interface)
Goodluck in your task
MHM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide