- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
LAN-to-LAN VPN issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2017 04:33 AM
Hi,
I just setup a lan-to-lan vpn lab. The structure is simple as the picture shows. VPN is working well. PCs on each LAN can ping PCs on another LAN. I try to make PCs on both LAN visit Internet via gateway. So how can I do it?
I try to use ip nat inside source list 1 interface FastEthernet0/0 overload on r1. But VPN is down.
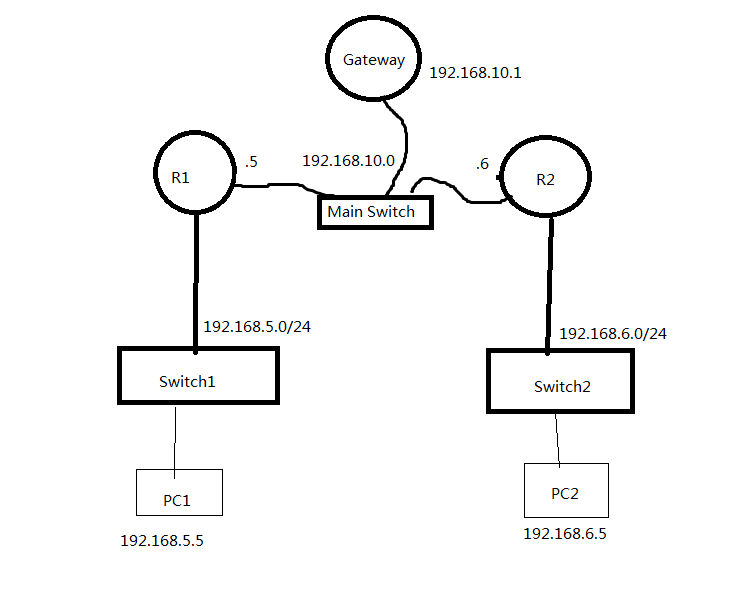
R1 configuration is as below:
Current configuration : 1174 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname r1
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 20
!
!
dot11 syslog
!
!
ip cef
!
!
!
multilink bundle-name authenticated
!
!
voice-card 0
no dspfarm
!
crypto isakmp policy 10
hash md5
authentication pre-share
crypto isakmp key vpnuser address 192.168.10.6
!
!
crypto ipsec transform-set myset esp-des esp-md5-hmac
!
crypto map mymap 10 ipsec-isakmp
set peer 192.168.10.6
set transform-set myset
match address 100
!
archive
log config
hidekeys
!
!
!
!
!
!
interface FastEthernet0/0
ip address 192.168.10.5 255.255.255.0
duplex auto
speed auto
crypto map mymap
!
interface FastEthernet0/1
ip address 192.168.5.1 255.255.255.0
duplex auto
speed auto
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 192.168.10.1
!
!
ip http server
no ip http secure-server
!
access-list 100 permit ip 192.168.5.0 0.0.0.255 192.168.6.0 0.0.0.255
!
!
!
!
!
!
control-plane
!
!
!
!
!
!
!
!
!
!
line con 0
line aux 0
line vty 0 4
login
!
scheduler allocate 20000 1000
!
end
=============================================
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2017 05:21 AM
I would try the following -
On the Gateway Outside Interface (facing the Internet) add the command
ip nat outside
I would also try adding the following global config commands on the Gateway
ip nat inside source list 1 interface "Whatever your Outside Interface is"
access-list 1 permit 192.168.5.0 0.0.0.255
access-list 1 permit 192.168.6.0 0.0.0.255
On R1 add the ip nat inside command
interface FastEthernet0/1
ip address 192.168.5.1 255.255.255.0
duplex auto
speed auto
ip nat inside
My thinking is that your Crypto ACL will be matched outbound on Fa0/0 for PC2 based traffic. All other traffic should then follow default route to the GW where you will have NAT configured and appropriate routing.
Then do similar for R2, but focus on getting R1 working first.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2017 05:32 AM
Or I see you are actually treating R1 as the Outside router essentially, and Gateway would be the ISP in your case.
In this case, ignore what i initially wrote :-) Will involve something different..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2017 09:38 PM
An ACL for VPN traffic uses the source and destination IP addresses after NAT.If the NAT overload is used, then a route-map should be used in order to exempt the VPN traffic of interest from translation
Below configuration will resolve this issue.
access-list 111 remark NAT exemption access-list
access-list 111 deny ip 192.168.5.0 0.0.0.255 192.168.6.0 0.0.0.255
access-list 111 permit ip 192.168.5.0 0.0.0.255 any
interface FastEthernet0/0
ip nat outside
interface FastEthernet0/1
ip nat inside
route-map nonat permit 10
match ip address 111
ip nat inside source route-map nonat interface FastEthernet0/0 overload
Regards,
Safwan
Please rate helpful post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2017 03:53 AM
Hi Safwan,
Just to help me understand this also - I am looking at the order of operations for Inside to Outside -
192.168.5.0 wants to go to Internet. Your NAT ACL is saying to not NAT between 192.168.5.0 and 192.168.6.0 and NAT everything else essentially. This I understand.
access-list 111 remark NAT exemption access-list
access-list 111 deny ip 192.168.5.0 0.0.0.255 192.168.6.0 0.0.0.255
access-list 111 permit ip 192.168.5.0 0.0.0.255 any
Why do we need the route-map in the NAT statement? is it not enough to just add the following -
ip nat inside source list 111 interface FastEthernet 0/0 overload
Traffic between sites won't be NAT'd (as denied in ACL 111). Anything else will be.
- If IPSec, then check input access list
- Decryption—for Cisco Encryption Technology (CET) or IPSec
- Check input access list
- Check input rate limits
- Input accounting
- Policy routing
- Routing
- Redirect to Web cache
- NAT inside to outside (local to global translation)
- Crypto (check map and mark for encryption)
- Check output access list
- Inspect context-based access control (CBAC)
- TCP intercept
- Encryption
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-26-2017 12:11 AM
Hi,
I got the similar problem. Is packet from 192.168.5.0 coming to 192.168.6.0 is dropped from overload or it comes through VPN?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-26-2017 12:08 AM
Hi Safwan,
Thanks for your help. I did what you said. This time PC1 can access internet. But PC1 still can not ping PC2 on the other side. I am confused about ACL order used in my case. When packet from 192.168.5.0 comes to 192.168.6.0 subnet, does it be dropped based on ip nat inside source route-map nonat interface FastEthernet0/0 overload, or it comes through VPN tunnel?
================================================
r1#show run
Building configuration...
Current configuration : 1801 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname r1
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 20
!
!
dot11 syslog
!
!
ip cef
no ip dhcp use vrf connected
!
ip dhcp pool jack
network 192.168.5.0 255.255.255.0
default-router 192.168.5.1
domain-name jackitservice.local
dns-server 8.8.8.8
!
!
!
multilink bundle-name authenticated
!
!
voice-card 0
no dspfarm
!
crypto isakmp policy 10
hash md5
authentication pre-share
crypto isakmp key vpnuser address 192.168.86.153
!
!
crypto ipsec transform-set myset esp-des esp-md5-hmac
crypto ipsec transform-set vpnnew esp-aes esp-sha-hmac
!
crypto map mymap 10 ipsec-isakmp
set peer 192.168.86.153
set transform-set vpnnew
match address 100
!
archive
log config
hidekeys
!
interface FastEthernet0/0
ip address dhcp
ip nat outside
ip virtual-reassembly
duplex auto
speed auto
crypto map mymap
!
interface FastEthernet0/1
ip address 192.168.5.1 255.255.255.0
ip nat inside
ip virtual-reassembly
duplex auto
speed auto
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 192.168.86.1
!
!
ip http server
no ip http secure-server
ip nat inside source route-map nonat interface FastEthernet0/0 overload
!
access-list 1 permit 192.168.5.0 0.0.0.255
access-list 100 permit ip 192.168.5.0 0.0.0.255 192.168.6.0 0.0.0.255
access-list 111 remark NAT exemption access-list
access-list 111 deny ip 192.168.5.0 0.0.0.255 192.168.6.0 0.0.0.255
access-list 111 permit ip 192.168.5.0 0.0.0.255 any
!
!
!
route-map nonat permit 10
match ip address 111
!
!
!
!
control-plane
!
!
!
!
!
!
!
!
!
!
line con 0
line aux 0
line vty 0 4
login
!
scheduler allocate 20000 1000
!
end
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide