- Cisco Community
- Technology and Support
- Security
- VPN
- Re: LDAP Attribute Map on FTD
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
LDAP Attribute Map on FTD
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2019 02:44 AM - edited 03-12-2019 05:33 AM
Hello Expert,
I have configured LDAP Attribute Map on FTD for Anyconnect VPN. but it is not working.
Does someone know how to make it work please?
FMC 6.2.3.7
FTD 6.2.3.7
Regard,
Zanga
- Labels:
-
AnyConnect
-
Other VPN Topics
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2019 04:44 AM
You can only use LDAP for basic authentication, not authorization.
"LDAP/AD authorization and accounting are not supported for Remote Access VPN."
Reference:
As of the current release 6.3, you'd need to use an external RADIUS server (like Cisco ISE) as an intermediary to provide granular user authorization based on LDAP attributes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2019 07:19 AM
Hello Marvin Rhoads,
Thanks for your reply.
Can I use microsoft radius for that ?
Regards,
Zanga
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2020 03:48 PM
Check out this guide: https://www.cisco.com/c/en/us/support/docs/security/firepower-ngfw/214283-configure-anyconnect-ldap-mapping-on-fir.html
I got it working for a customer I believe was running 6.3.
A different customer that was running 6.4 would throw an error trying to run the "aaa-server" command.
Apparently there's a bug (that's what TAC said); as soon as we changed "ldap attribute-map" to "lda attribute-map" (leave off the "p") and "aaa-server" to "aaa-serve" (leave off the "r") it took the FlexConfig.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2020 02:19 AM
Hello.
Was it possible to implement a similar scheme for connecting remote users? I try to configure it according to this article, but without success...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2020 04:28 AM
Can you share your details? Such as: version of Firepower, your current Flexconfig, what results you are seeing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2020 04:55 AM - edited 04-06-2020 05:01 AM
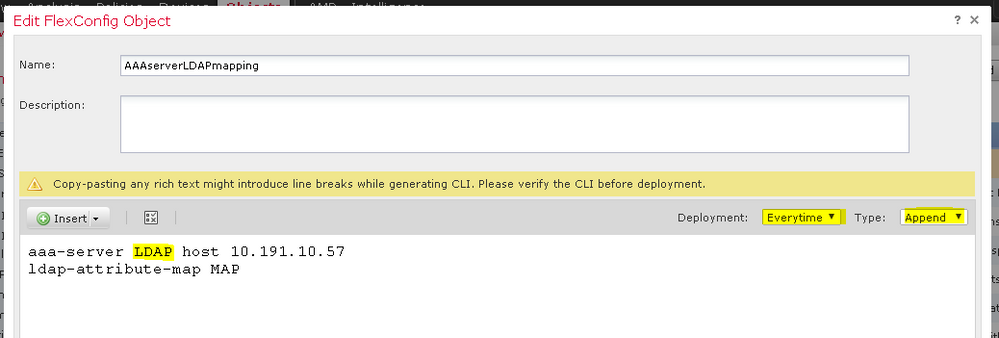
Cisco Firepower 1140 Threat Defense 6.4.0
FMC 6.4.0.7
in this particular case LDAP - realm name
10.191.10.57 - ad dc
Group10 and Group192 - group policy name
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
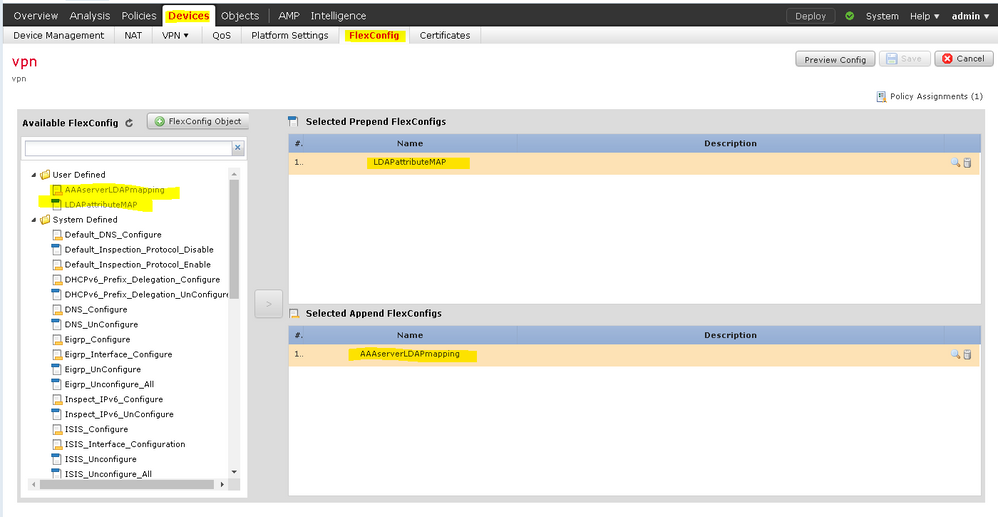
04-06-2020 09:06 AM
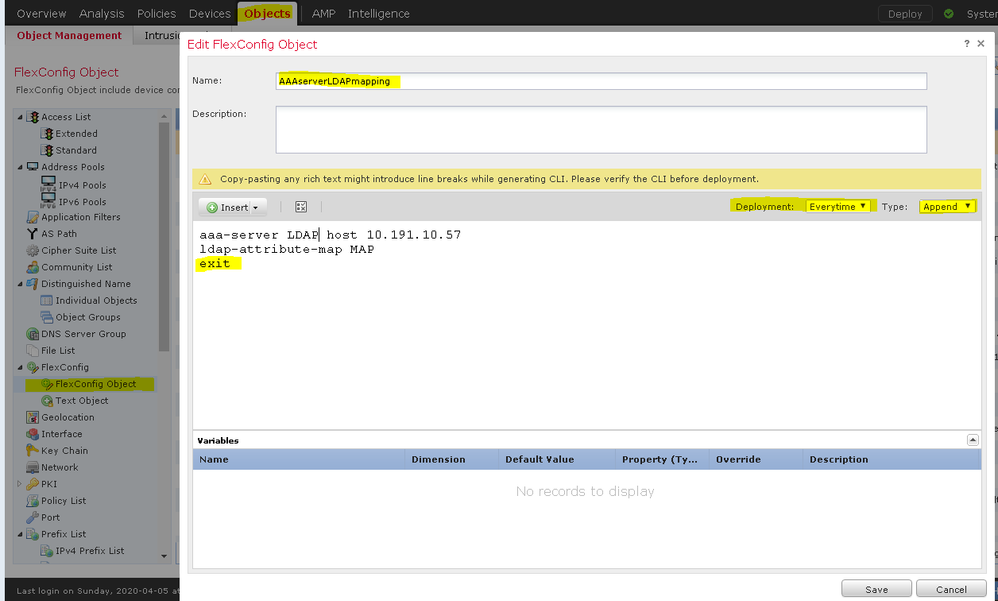
Got it. Screen with correct settings.
aaa-server <LDAP/AD_Realm_name> host <AD Server IP>
ldap-attribute-map <LDAP_Map_for_VPN_Access>
exit
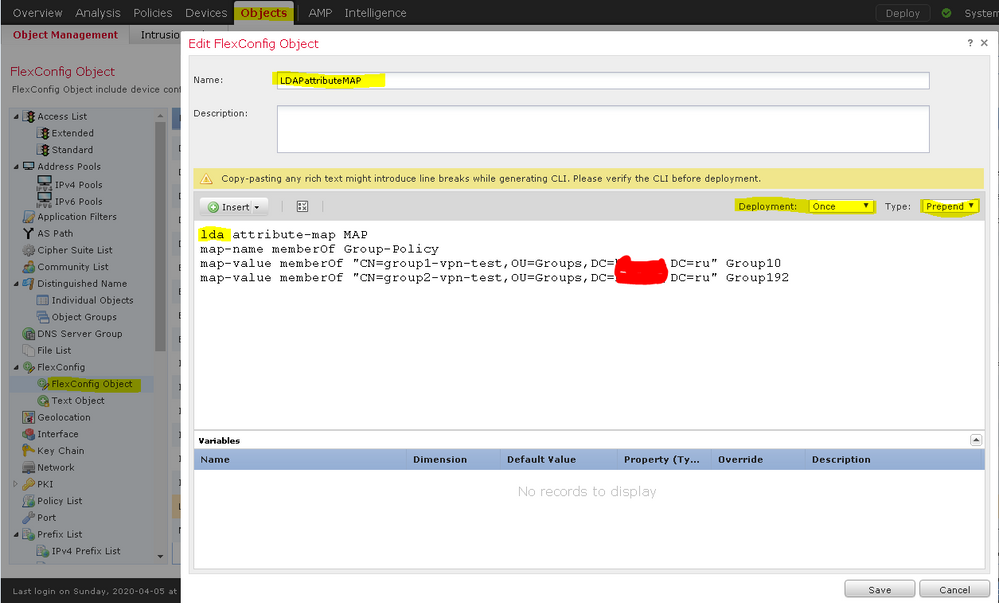
in this case LDAP - its realm name
lda attribute-map <LDAP_Map_for_VPN_Access>
map-name memberOf Group-Policy
map-value memberOf CN=APP-SSL-VPN Managers,CN=Users,OU=stbu,DC=cisco,DC=com LabAdminAccessGroupPolicy
map-value memberOf CN=cisco-Eng,CN=Users,OU=stbu,DC=cisco,DC=com VPNAccessGroupPolicy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2020 09:12 AM
Sorry yes correct that is the realm name.
Also one funny thing I noticed. If you have to go back and add a group later the deploy fails with an error that the attribute map already exists.
I put this at the beginning of my attribute map:
no lda attribute-map <LDAP_Map_for_VPN_Access>
With that, any time I update the map and deploy, it removes the map and re-creates it. I no longer received errors when I try to update the attribute map.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide