- Cisco Community
- Technology and Support
- Security
- VPN
- Re: PPTP VPN passing through Cisco 1921
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
PPTP VPN passing through Cisco 1921
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-09-2019 03:34 AM
I hope this is the correct location to post this...I am not using AnyConnect, but this is VPN related.
I have a Spectrum Business Fiber connection at my office. The first device in my network after the Spectrum CPE is a Cisco 1921. The Cisco config is nothing spectacular (I'll post the config below). After the Cisco is a Barracuda Web Filter, followed by a Meraki MX64 which feeds all of my internal switches and such.
We recently merged with a company in Alabama which has Windows PPTP VPN server. That PPTP server is fully functional, and I can connect to it from my house in Wisconsin without issue.
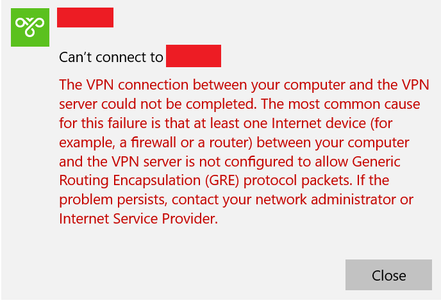
The issue I am having is as follows: While at my office in Wisconsin, I am unable to connect to the PPTP VPN in Alabama. I am using the same laptop at home and the Wisconsin office, so I can rule out that out as an issue. When I am at the Wisconsin office and I try to connect to the VPN, this is the error that I eventually see:
I am not sure what is causing this, but both Spectrum and Meraki are saying that it most likely has something to do with the Cisco 1921 that is in place. Looking at the configuration, I realize that I am a bit out of my depth of knowledge, so I thought I would reach out here to see if anyone can possibly see what may be causing the issue.
My computer at the office is wired into the network, it is not on WiFi. My internal IP is 172.16.10.x
Here is the configuration for my Cisco 1921:
Using 4635 out of 262136 bytes
!
! Last configuration change at 10:47:12 CDT Tue Sep 4 2018 by jhecker
! NVRAM config last updated at 10:47:13 CDT Tue Sep 4 2018 by jhecker
! NVRAM config last updated at 10:47:13 CDT Tue Sep 4 2018 by jhecker
version 15.2
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname CiscoRouter
!
boot-start-marker
boot-end-marker
!
!
logging buffered 51200 warnings
enable secret 5 ******************************
!
aaa new-model
!
!
aaa authentication login default local
aaa authorization exec default local
!
!
!
!
!
aaa session-id common
clock timezone CST -6 0
clock summer-time CDT recurring
!
ip cef
!
!
!
!
!
!
no ip domain lookup
ip domain name yourdomain.com
no ipv6 cef
multilink bundle-name authenticated
!
!
crypto pki trustpoint TP-self-signed-668782424
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-668782424
revocation-check none
rsakeypair TP-self-signed-668782424
!
!
crypto pki certificate chain TP-self-signed-668782424
certificate self-signed 01 nvram:IOS-Self-Sig#1.cer
license udi pid CISCO1921/K9 sn FTX181583CQ
!
!
file privilege 0
username ******** privilege 15 secret 5 ******************************
username ******* privilege 15 password 0 ***********
username ***** privilege 15 view enduserview password 0 ***********
!
!
!
!
!
!
interface Embedded-Service-Engine0/0
no ip address
shutdown
!
interface GigabitEthernet0/0
description *** Trunk to Inside Network ***
no ip address
duplex auto
speed auto
!
interface GigabitEthernet0/0.1
description Management VLAN 1 - Native VLAN
encapsulation dot1Q 1 native
ip address 172.16.1.1 255.255.255.0
!
interface GigabitEthernet0/0.10
description *** LAN VLAN ***
encapsulation dot1Q 10
ip address 172.16.10.1 255.255.254.0
ip helper-address 172.16.20.0
ip helper-address 172.16.11.0
!
interface GigabitEthernet0/0.20
description *** Wireless LAN VLAN ***
encapsulation dot1Q 20
ip address 172.16.20.1 255.255.255.0
ip helper-address 172.16.10.0
ip helper-address 172.16.10.10
ip helper-address 172.16.11.0
!
interface GigabitEthernet0/1
description *** Link to ASA Fa0/1 ***
ip address 172.16.250.2 255.255.255.248
duplex auto
speed auto
!
!
router eigrp 10
network 172.16.0.0
!
ip forward-protocol nd
!
ip http server
ip http authentication local
ip http secure-server
ip http timeout-policy idle 60 life 86400 requests 10000
!
ip route 0.0.0.0 0.0.0.0 172.16.250.1
ip route 192.168.1.0 255.255.255.0 172.16.250.1
!
!
!
!
!
!
control-plane
!
!
banner exec ^CC
---------------------------------------------------------------------------------------
!!! Authorized Access Only !!!
---------------------------------------------------------------------------------------
^C
banner login ^CC
---------------------------------------------------------------------------------------
!!! Authorized Access Only !!!
---------------------------------------------------------------------------------------
^C
parser view enduserview
secret 5 ******************************
commands interface include switchport
commands configure include cns trusted-server
commands configure include cns
commands configure include scheduler max-task-time
commands configure include scheduler
commands exec include dir all-filesystems
commands exec include dir
commands exec include write memory
commands exec include write
commands exec include configure terminal
commands exec include configure
commands exec include show ip interface brief
commands exec include show ip interface
commands exec include show ip
commands exec include show diag
commands exec include show version
commands exec include show running-config
commands exec include show interfaces
commands exec include show
!
!
line con 0
exec-timeout 120 0
password **********
logging synchronous
line aux 0
password **********
line 2
no activation-character
no exec
transport preferred none
transport output pad telnet rlogin lapb-ta mop udptn v120 ssh
stopbits 1
line vty 0 4
access-class 23 in
privilege level 15
password **********
transport input telnet ssh
line vty 5 15
access-class 23 in
privilege level 15
transport input telnet ssh
!
scheduler max-task-time 5000
scheduler allocate 20000 1000
ntp server 172.16.10.10
cns trusted-server all-agents yourname
!
end
Does it look like something in the Cisco configuration may be the issue, or do I need to continue looking elsewhere?
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-09-2019 03:45 AM
I don't see any configuration, as in no ACLs applied on an interface on this router that would cause and issue with the PPTP VPN being blocked. The description on GigabitEthernet0/1 interfaces does imply there is an ASA connected, which I assume refers to a Cisco ASA Firewall. This could be blocking the traffic.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-09-2019 03:56 AM
There used to be an ASA 5505 connected to GE0/1, that has been replaced with a Meraki MX64. I never bothered to change the description in the configuration of the 1921.
You said "I don't see any configuration". Not knowing much about Cisco devices, it begs me to ask the following: Is there something missing in the config (or lack thereof) that I posted which would be needed to allow PPTP/GRE traffic to pass through it? All other traffic goes through it fine, so I just assumed that the device was configured properly by whoever initially configured it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-09-2019 04:02 AM
The Meraki MX64 is a firewall though, that could be blocking traffic - assuming the PPTP VPN is routed through that device?
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-09-2019 04:13 AM
I initially thought the same thing, so I reached out to Meraki a few days ago, and they said:
After the client sends a configuration request we should be getting an ACK back. I am not seeing that.
The request is sent a few times with no response and then the connection is terminated.
There is nothing that points to this being a problem with the MX.
Can you get a packet capture on the server side?
They then followed up with:
I noticed on the packet capture that I took that there is a Cisco device upstream from the MX. (according to the dest mac address). The problem is likely caused by this device. Is that a service provider device?
You may need to contact them and verify they are allowing PPTP traffic through.
Our packet captures show that the server is not responding. If it is, the packets are not making it back to the MX.
The device they mention is the 1921. I did reach out to Spectrum and they confirmed that they do not block/filter any traffic. I'm at a complete loss of where else I can look.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-09-2019 04:17 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-09-2019 04:52 AM
Attached are the pcap files from the devices, as requested. Truth be told, this was the first time I ever did a packet capture on a Cisco device, so I am not sure if I did it correctly. However, the fact that I was able to export the file from the Cisco tells me that I I at least did something right :)
I started the packet capture on the Meraki, having it run for 90 seconds, then I immediately started the capture on the Cisco, then tried to connect to the VPN. The VPN failed while both captures were still active, so they should contain all of the information.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-09-2019 04:53 AM
The remote host in this case is 24.96.28.186
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-09-2019 05:08 AM
How are all the devices connected? Please provide a diagram if possible
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-09-2019 05:25 AM
Time to show off my lovely Visio skills, heh.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-09-2019 05:52 AM
Looking at the captures from the Meraki device, they appear to not have all of the data in it...so, I have created another set. It is a large capture, so I put it on Google Drive.
https://drive.google.com/file/d/1_46nho_hcpH5Hgx84MUJJB6pfdEXGtGT/view
It contains the captures for both the Meraki and the Cisco devices.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-09-2019 06:05 AM - edited 01-09-2019 06:19 AM
from looking at the capture i cant see any phase 1 or phase 2 packets in regards to vpn. only see the traffic port 443. your cisco router does not have any vpn config. when was the last time it was working?
you said you try to trigger the traffic for the vpn. if no config in router for vpn we cant see anything. i dont see anything in Maraki firewall either. were they devices had power outrage? where they working before and suddenly stop working?
looking in to the capture if find something intersting will update you.
Cisco Capture shows 172.16.10.158 is doing communicate to 24.96.28.186
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-09-2019 06:40 AM
interface GigabitEthernet0/0.10
description *** LAN VLAN ***
encapsulation dot1Q 10
ip address 172.16.10.1 255.255.254.0
Which device is the default gateway for the PC 172.16.10.158? the router or meraki?
I see no traffic in the meraki capture to 24.96.28.186 but I do in the cisco router capture, and those packets are out of order.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-09-2019 06:43 AM
My apologies, the Meraki is 172.16.250.1 and is connected to interface GigabitEthernet0/1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-09-2019 06:58 AM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide