- Cisco Community
- Technology and Support
- Security
- VPN
- Problem to connect ASA site-to-site VPN from Checkpoint
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Problem to connect ASA site-to-site VPN from Checkpoint
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-05-2019 05:55 PM
I tried to connect the VPN with the client but it's failed. They are using the ASA with IOS version 7. And they have the strange debug messages when trying to connect the IKE phase1. Seem the ASA cannot decode a message which sending from CP...
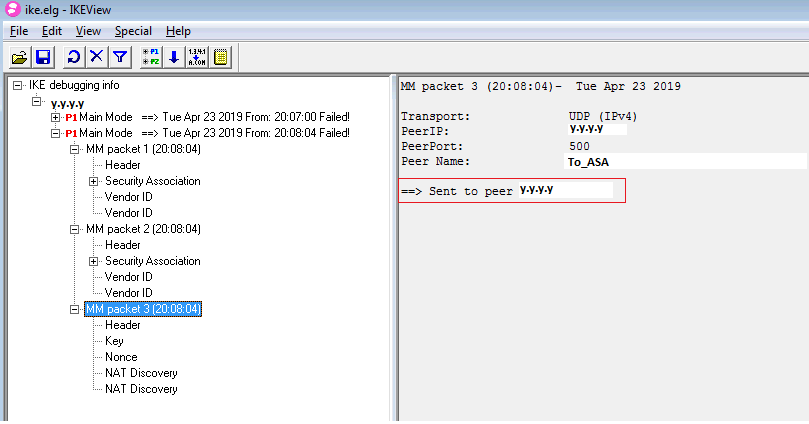
Also tried to enable the debug on CP, and saw the Main mode Message packet3 was sent to ASA but stopped to reply back from ASA. I think the MM3 is using to complete the IKE negotiation
Can someone help please?
Checkpoint= x.x.x.x
ASA= y.y.y.y
<DEBUG LOG from ASA>
Apr 24 12:01:12 [IKEv1]: IP = x.x.x.x, IKE_DECODE RECEIVED Message (msgid=0) with payloads : HDR + SA (1) + VENDOR (13) + VENDOR (13) + NONE (0) total length : 148
Apr 24 12:01:12 [IKEv1 DEBUG]: IP = x.x.x.x, processing SA payload
Apr 24 12:01:12 [IKEv1 DEBUG]: IP = x.x.x.x, Oakley proposal is acceptable
Apr 24 12:01:12 [IKEv1 DEBUG]: IP = x.x.x.x, processing VID payload
Apr 24 12:01:12 [IKEv1 DEBUG]: IP = x.x.x.x, Received NAT-Traversal RFC VID
Apr 24 12:01:12 [IKEv1 DEBUG]: IP = x.x.x.x, processing VID payload
Apr 24 12:01:12 [IKEv1 DEBUG]: IP = x.x.x.x, processing IKE SA payload
Apr 24 12:01:12 [IKEv1 DEBUG]: IP = x.x.x.x, IKE SA Proposal # 1, Transform # 1 acceptable Matches global IKE entry # 6
Apr 24 12:01:12 [IKEv1 DEBUG]: IP = x.x.x.x, constructing ISAKMP SA payload
Apr 24 12:01:12 [IKEv1 DEBUG]: IP = x.x.x.x, constructing NAT-Traversal VID ver RFC payload
Apr 24 12:01:12 [IKEv1 DEBUG]: IP = x.x.x.x, constructing Fragmentation VID + extended capabilities payload
Apr 24 12:01:12 [IKEv1]: IP = x.x.x.x, IKE_DECODE SENDING Message (msgid=0) with payloads : HDR + SA (1) + VENDOR (13) + VENDOR (13) + NONE (0) total length : 128
Apr 24 12:01:12 [IKEv1]: IP = x.x.x.x, IKE_DECODE RECEIVED Message (msgid=0) with payloads : HDR + KE (4) + NONCE (10) + UNKNOWN (20), *** ERROR *** + UNKNOWN (20), *** ERROR *** + NONE (0) total length : 232
Apr 24 12:01:12 [IKEv1 DEBUG]: IP = x.x.x.x, processing ke payload
Apr 24 12:01:12 [IKEv1 DEBUG]: IP = x.x.x.x, processing ISA_KE payload
Apr 24 12:01:12 [IKEv1 DEBUG]: IP = x.x.x.x, processing nonce payload
Apr 24 12:01:12 [IKEv1]: IP = x.x.x.x, IKE_DECODE SENDING Message (msgid=0) with payloads : HDR + NOTIFY (11) + NONE (0) total length : 41
Apr 24 12:01:12 [IKEv1 DEBUG]: IP = x.x.x.x, IKE MM Responder FSM error history (struct &0xcbc672c8) <state>, <event>: MM_DONE, EV_ERROR-->MM_WAIT_MSG3, EV_PROCESS_MSG-->MM_WAIT_MSG3, EV_RCV_MSG-->MM_WAIT_MSG3, NullEvent-->MM_SND_MSG2, EV_SND_MSG-->MM_SND_MSG2, EV_START_TMR-->MM_BLD_MSG2, EV_BLD_MSG2-->MM_BLD_MSG2, EV_CREATE_TMR
Apr 24 12:01:12 [IKEv1 DEBUG]: IP = x.x.x.x, IKE SA MM:1ef2aaae terminating: flags 0x01000002, refcnt 0, tuncnt 0
Apr 24 12:01:12 [IKEv1 DEBUG]: IP = x.x.x.x, sending delete/delete with reason message
Apr 24 12:01:12 [IKEv1]: IP = x.x.x.x, Removing peer from peer table failed, no match!
Apr 24 12:01:12 [IKEv1]: IP = x.x.x.x, Error: Unable to remove PeerTblEntry
Apr 24 12:01:14 [IKEv1]: IP = x.x.x.x, Header invalid, missing SA payload! (next payload = 4)
Apr 24 12:01:14 [IKEv1]: IKE_DECODE SENDING Message (msgid=0) with payloads : HDR + NOTIFY (11) + NONE (0) total length : 68
Apr 24 12:01:16 [IKEv1]: IP = x.x.x.x, Header invalid, missing SA payload! (next payload = 4)
Apr 24 12:01:16 [IKEv1]: IKE_DECODE SENDING Message (msgid=0) with payloads : HDR + NOTIFY (11) + NONE (0) total length : 68
Apr 24 12:01:18 [IKEv1]: IP = x.x.x.x, Header invalid, missing SA payload! (next payload = 4)
Apr 24 12:01:20 [IKEv1]: IP = x.x.x.x, Header invalid, missing SA payload! (next payload = 4)
Apr 24 12:01:20 [IKEv1]: IKE_DECODE SENDING Message (msgid=0) with payloads : HDR + NOTIFY (11) + NONE (0) total length : 68
Apr 24 12:01:22 [IKEv1]: IP = x.x.x.x, Header invalid, missing SA payload! (next payload = 4)
Apr 24 12:01:22 [IKEv1]: IKE_DECODE SENDING Message (msgid=0) with payloads : HDR + NOTIFY (11) + NONE (0) total length : 68
Apr 24 12:01:24 [IKEv1]: IP = x.x.x.x, Header invalid, missing SA payload! (next payload = 4)
Apr 24 12:01:24 [IKEv1]: IKE_DECODE SENDING Message (msgid=0) with payloads : HDR + NOTIFY (11) + NONE (0) total length : 68
Apr 24 12:01:28 [IKEv1]: IP = x.x.x.x, Header invalid, missing SA payload! (next payload = 4)
Apr 24 12:01:28 [IKEv1]: IKE_DECODE SENDING Message (msgid=0) with payloads : HDR + NOTIFY (11) + NONE (0) total length : 68
Apr 24 12:01:32 [IKEv1]: IP = x.x.x.x, Header invalid, missing SA payload! (next payload = 4)
Apr 24 12:01:36 [IKEv1]: IP = x.x.x.x, Header invalid, missing SA payload! (next payload = 4)
Apr 24 12:01:40 [IKEv1]: IP = x.x.x.x, Header invalid, missing SA payload! (next payload = 4)
Apr 24 12:01:44 [IKEv1]: IP = x.x.x.x, Header invalid, missing SA payload! (next payload = 4)
<TCPDUMP on Checkpoint>
<LOG>
21:22:44.813690 IP (tos 0x0, ttl 240, id 23696, offset 0, flags [none], proto UDP (17), length 69)
y.y.y.y.500 > x.x.x.x.500: [udp sum ok] isakmp 1.0 msgid 00000000 cookie dbaac3c5ee56e029->28b49e9ecbb2a8d2: phase 1 R inf:
(n: doi=ipsec proto=#0 type=INVALID-PAYLOAD-TYPE orig=([|isakmp]))
21:22:46.624601 IP (tos 0x0, ttl 64, id 4731, offset 0, flags [none], proto UDP (17), length 260)
x.x.x.x.500 > y.y.y.y.500: [udp sum ok] isakmp 1.0 msgid 00000000 cookie dbaac3c5ee56e029->28b49e9ecbb2a8d2: phase 1 I ident:
(ke: key len=128 5923e97066d911745c16100254d44f80aa5109bf1eb332044270a65e7eac95a2afaa8d4b4ca2fdab3488fe272a784a29901d20f5973fc33b72d6e308548be942a7ff7391bf14243fbc095df224e9f36d4f7c1f5165b4a7c50383f63cefb4ec8489b261e9bedf5adbf7302ec18548f1eeee69b8a0531947ad1ee88f726163d310)
(nonce: n len=20 8cbf20670413ff2b0678509decb6f3e892377965)
(pay20)
(pay20)
21:22:46.816850 IP (tos 0x0, ttl 240, id 15015, offset 0, flags [none], proto UDP (17), length 96)
y.y.y.y.500 > x.x.x.x.500: [udp sum ok] isakmp 1.0 msgid 00000000 cookie dbaac3c5ee56e029->28b49e9ecbb2a8d2: phase 1 R inf:
(n: doi=ipsec proto=#0 type=INVALID-COOKIE orig=(isakmp 0.0 msgid 41590c09 cookie 800f4fc8e08eabcb->0200000003000000:))
21:22:48.634608 IP (tos 0x0, ttl 64, id 4732, offset 0, flags [none], proto UDP (17), length 260)
x.x.x.x.500 > y.y.y.y.500: [udp sum ok] isakmp 1.0 msgid 00000000 cookie dbaac3c5ee56e029->28b49e9ecbb2a8d2: phase 1 I ident:
(ke: key len=128 5923e97066d911745c16100254d44f80aa5109bf1eb332044270a65e7eac95a2afaa8d4b4ca2fdab3488fe272a784a29901d20f5973fc33b72d6e308548be942a7ff7391bf14243fbc095df224e9f36d4f7c1f5165b4a7c50383f63cefb4ec8489b261e9bedf5adbf7302ec18548f1eeee69b8a0531947ad1ee88f726163d310)
(nonce: n len=20 8cbf20670413ff2b0678509decb6f3e892377965)
(pay20)
(pay20)
<IKE Debug on CP>
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-06-2019 03:29 AM
check this information help you. :
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-06-2019 05:42 PM
Thanks, it is still not helpful to fix my problem..... I have read this before, but still have no luck....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-06-2019 10:39 PM
Can you post bot the side configuration in related to VPN validated before we suggest something.
Also give us the ASA version of code, checkpoint 77.X or 80.X ?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide