- Cisco Community
- Technology and Support
- Security
- VPN
- "IPsec over GRE with OSPF" using Loopbacks
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
"IPsec over GRE with OSPF" using Loopbacks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-10-2011 04:31 AM - edited 02-21-2020 05:20 PM
Hi All ,
I have the following scenario :
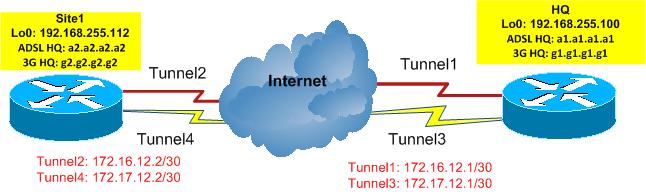
I'm going to make two connections between the HQ office and site1 using GRE over IPsec with OSPF routing,at each site I'm using ADSL line besides 3G (as backup), and the target is to use Loopbacks as source and destination for one IPsec channel that connects the two sites.
First of all I've configured two GRE tunnels on both sites and did the OSPF confiugration , it worked, they saw each other and I can ping the loopbacks from each side and everything is fine.
additional info :
tunnel 1 :-
source: dialer1 (ADSL interface)
dest: a2.a2.a2.a2
Tunnel2:
source: dialer1
dest: a1.a1.a1.a1
-----------------------------
tunnel 3 :-
source: cellular0/3/0 (3G interface)
dest: g2.g2.g2.g2
Tunnel4:
source: cellular0/1/0
dest: g1.g1.g1.g1
Then ,I've applied the IPsec using the following configuration :
HQ:
crypto isakmp policy 1
authentication pre-share
crypto isakmp key XXXX address 0.0.0.0 0.0.0.0
!
!
crypto ipsec transform-set strong esp-3des esp-md5-hmac
mode transport
!
crypto map vpn 1234 ipsec-isakmp
set peer a2.a2.a2.a2
set peer g2.g2.g2.g2
set transform-set strong
match address 112
!
interface Loopback0
ip address 192.168.255.100 255.255.255.255
!
interface Tunnel1
ip address 172.16.12.1 255.255.255.252
ip ospf cost 12
tunnel source Dialer1
tunnel destination a2.a2.a2.a2
crypto map vpn
!
interface Tunnel3
ip address 172.17.12.1 255.255.255.252
ip ospf cost 1233
tunnel source Cellular0/3/0
tunnel destination g2.g2.g2.g2
crypto map vpn
ip route g2.g2.g2.g2 255.255.255.255 Cellular0/3/0
ip route a2.a2.a2.a2 255.255.255.255 Dialer1
!
=======================================================================
Site1 :
crypto isakmp policy 1
authentication pre-share
crypto isakmp key XXXX address 0.0.0.0 0.0.0.0
!
!
crypto ipsec transform-set strong esp-3des esp-md5-hmac
mode transport
!
crypto map vpn 1234 ipsec-isakmp
set peer a1.a1.a1.a1
set peer g1.g1.g1.g1
set transform-set strong
match address 116
!
!
!
!
!
interface Loopback0
ip address 192.168.255.112 255.255.255.255
!
interface Tunnel2
ip address 172.17.12.2 255.255.255.252
ip ospf cost 1233
tunnel source Cellular0/1/0
tunnel destination g1.g1.g1.g1
crypto map vpn
!
interface Tunnel4
ip address 172.16.12.2 255.255.255.252
ip ospf cost 12
tunnel source Dialer1
tunnel destination a1.a1.a1.a1
crypto map vpn
!
ip route g1.g1.g1.g1 255.255.255.255 Cellular0/1/0
ip route a1.a1.a1.a1 255.255.255.255 Dialer1
!
It works fine as well, I have two IPsec channels that encrypt the data using Public IP addresses as source/destination of channels .
Now I wanna apply my target to use the Loopback as the source/destination of traffic and to establish one IPsec channel instead of two ones .
So how can I get this scenario implemented ?
when I use Crypto map vpn local-address , I loose the connectivity !
so what can I do ?
Appreciate your help and thanks in advance.
- Labels:
-
IPSEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-10-2011 08:59 AM
For them to connect -
They need to route to each other
HTH>
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide