- Cisco Community
- Technology and Support
- Security
- VPN
- Radius through VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Radius through VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2012 07:20 AM
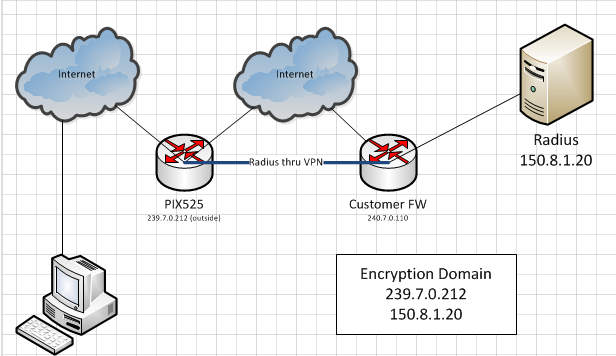
I have a Pix 525 that remote users will be dialing into via EasyVPN.
In this scenario, I only have one interface to use, the outside interface, as the inside interface has been setup as a management interface.
Basically I need to be able to authenticate my easyvpn users via radius, through a VPN connection to a customer site. The problem I have is that I don't seem to be able to assign a source IP to the radius request, or even assign another IP to the PIX for the encryption domain (e.g., through a subinterface or vlan, etc).
The end result would be that the radius request needs to come from the same device that is terminating the VPN which provides access to the radius server.
Is this even possible? I would prefer to do it on the 525, and may be able to assign a real, routable address to the inside itnerface, but then how would I determine which IP the radius request comes from (required for it to be a part of the encryption domain). I was thinking it might be possible with scenario like this http://www.cisco.com/en/US/products/hw/vpndevc/ps2030/products_configuration_example09186a0080094469.shtml , but then that example has different subnets on the different interfaces, which my current environment does not.
If not on this Pix, is there a make/model that would be able to perform the task of terminating remote-access VPNs, a site-to-site VPN, and passing radius through that site-to-site all on the same interface (with different IPs).
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2012 07:29 AM
Try this:
!--- Create the AAA server group "server-group-name" and specify the protocol as RADIUS.
!--- Specify the radius server as a member of the "server-group-name" and provide the
!--- location and key.
aaa-server vpn protocol radius
max-failed-attempts 5
aaa-server vpn (OUTSIDE) host
timeout 30
key cisco123
Where OUTSIDE should be the name of the outisde interface in your scenario
let me know how it worksgoes.
Regards,
Jatin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2012 07:48 AM
I turned on debugging with
debug aaa authentication
debug aaa common
debug crypto isakmp 10
debug crypto ipsec 10
debug crypto condition peer 240.7.0.110
and I get
testfw# AAA_BindServer: No server found
ERROR: No error
And no errors at all for the site-to-site VPN, implying that it doesn't even try to bring up the tunnel
Here is my config
testfw# show running-config
: Saved
:
PIX Version 8.0(4)
!
hostname testfw
domain-name mydomain.com
enable password aGXoT1pAdhA/KwIt encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface Ethernet0
nameif outside
security-level 0
ip address 239.7.0.212 255.255.255.248
!
interface Ethernet1
nameif inside
security-level 100
ip address 10.2.201.148 255.255.255.248
!
interface GigabitEthernet0
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1
shutdown
no nameif
no security-level
no ip address
!
ftp mode passive
dns server-group DefaultDNS
domain-name mydomain.com
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
access-list outside_cryptomap extended permit ip host 239.7.0.213 host 139.7.146.116
access-list inside_nat0_outbound extended permit ip any 192.168.1.0 255.255.255.128
pager lines 24
logging enable
logging buffered debugging
logging asdm informational
mtu outside 1500
mtu inside 1500
ip local pool vpnpool 192.168.1.1-192.168.1.100 mask 255.255.255.0
no failover
icmp unreachable rate-limit 1 burst-size 1
asdm image flash:/asdm
no asdm history enable
arp timeout 14400
nat (inside) 0 access-list inside_nat0_outbound
route outside 0.0.0.0 0.0.0.0 139.7.0.209 1
route inside 10.2.140.0 255.255.255.224 10.2.201.145 1
route inside 10.2.140.32 255.255.255.224 10.2.201.145 1
route inside 10.2.190.244 255.255.255.255 10.2.201.145 1
route inside 10.2.190.253 255.255.255.255 10.2.201.145 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
aaa-server 139.7.146.116 protocol radius
aaa-server 139.7.146.116 (outside) host 139.7.146.116
aaa authentication ssh console LOCAL
http server enable
http 192.168.1.0 255.255.255.0 outside
http 192.168.1.0 255.255.255.0 inside
http 10.216.0.0 255.255.0.0 inside
http 10.2.140.32 255.255.255.224 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set pfs group1
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set security-association lifetime seconds 28800
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set security-association lifetime kilobytes 4608000
crypto map outside_map1 1 match address outside_cryptomap
crypto map outside_map1 1 set pfs
crypto map outside_map1 1 set peer 240.7.0.110
crypto map outside_map1 1 set transform-set ESP-DES-SHA
crypto map outside_map1 1 set security-association lifetime seconds 28800
crypto map outside_map1 1 set security-association lifetime kilobytes 4608000
crypto map outside_map1 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map outside_map1 interface outside
crypto isakmp enable outside
crypto isakmp policy 5
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto isakmp policy 10
authentication pre-share
encryption des
hash sha
group 2
lifetime 86400
telnet 10.216.5.112 255.255.255.255 inside
telnet timeout 5
ssh 192.168.1.0 255.255.255.0 outside
ssh 10.2.140.32 255.255.255.224 inside
ssh 10.2.190.244 255.255.255.255 inside
ssh 10.2.190.253 255.255.255.255 inside
ssh 192.168.1.0 255.255.255.0 inside
ssh timeout 60
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
group-policy GroupPolicy1 internal
group-policy GroupPolicy1 attributes
vpn-tunnel-protocol IPSec
group-policy Dialup internal
group-policy Dialup attributes
dns-server value 4.2.2.2
vpn-tunnel-protocol IPSec
default-domain value mydomain.com
group-policy jtest internal
group-policy jtest attributes
dns-server value 4.2.2.2
vpn-tunnel-protocol IPSec
username admin password tyDfOYX4uN2t7tDf encrypted
tunnel-group 240.7.0.110 type ipsec-l2l
tunnel-group 240.7.0.110 ipsec-attributes
pre-shared-key *
tunnel-group Dialup type remote-access
tunnel-group Dialup general-attributes
address-pool vpnpool
authentication-server-group 150.8.1.20
default-group-policy Dialup
tunnel-group Dialup ipsec-attributes
pre-shared-key *
tunnel-group jtest type remote-access
tunnel-group jtest general-attributes
address-pool vpnpool
default-group-policy jtest
tunnel-group jtest ipsec-attributes
pre-shared-key *
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect netbios
inspect rsh
inspect rtsp
inspect skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect tftp
inspect sip
inspect xdmcp
!
service-policy global_policy global
prompt hostname context
Cryptochecksum:9b27ab018288bc417d9441671e9593b1
: end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2012 08:08 AM
I assume the above mentioned configuration is from PIX 525. If yes so based on that I would like you to perform few test.
1.] Ping outside 139.7.146.116
2.] Test aaa authentication 139.7.146.116 host 139.7.146.116
username:
pasword:
3.] What is the name of the tunnel-group users are trying to connect with?
Post me the o/p of the above tests.
Regards,
Jatin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2012 10:16 AM
Hi Justin,
Please try this and let me know.
aaa-server My-Radius protocol radius
aaa-server My-Radius host 150.8.1.20
key Your-Radius-shared-key-goes-here
tunnel-group DefaultRAGroup general-attributes
authentication-server-group (outside) My-Radius
tunnel-group Dialup general-attributes
authentication-server-group My-Radius
Please add this an additional entry on your ACL "outside_cryptomap"
access-list outside_cryptomap extended permit ip host 239.7.0.213 host 150.8.1.20
Likewise the reverse the IPs at other end of the tunnel.
access-list outside_cryptomap extended permit ip host 150.8.1.20 host 239.7.0.213
Please let me know, if this helps.
thanks
Rizwan Rafeek
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2012 12:27 AM
I've tried that and I get the same issue
testfw# test aaa-server authentication 139.7.146.116
Server IP Address or name: 139.7.146.116
Username: adsf
Password: ****
INFO: Attempting Authentication test to IP address <139.7.146.116> (timeout: 12 seconds)
ERROR: Authentication Server not responding: No error
with
debug aaa common 10
debug crypto ipsec 10
debug crypto isakmp 10
I still get no debug messages from crypto, and I get the same from aaa (with more verbosity)
AAA API: In aaa_open
AAA session opened: handle = 19
AAA API: In aaa_process_async
aaa_process_async: sending AAA_MSG_PROCESS
AAA task: aaa_process_msg(1ea95a8) received message type 0
AAA FSM: In AAA_StartAAATransaction
AAA FSM: In AAA_InitTransaction
Initiating authentication to primary server (Svr Grp: 139.7.146.116)
------------------------------------------------
AAA FSM: In AAA_BindServer
AAA_BindServer: Using server: 139.7.146.116
AAA FSM: In AAA_SendMsg
User: Cebit004
Resp:
callback_aaa_task: status = -2, msg =
AAA FSM: In aaa_backend_callback
aaa_backend_callback: Handle = 19, pAcb = 4c7eeb4
aaa_backend_callback: Error:
Timeout to RADIUS server.
......
Would this work if I had both interfaces up with routable IPs? If not on this device which firewall could I test it with that would work?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-20-2012 02:31 AM
The solution was to use the outside interface for both VPNs and the radius auth instead of trying to use 2 IPs (one for the interface, one for the encryption domain)
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide