- Cisco Community
- Technology and Support
- Security
- VPN
- Re: site-site VPN frustration....
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-07-2019 01:44 PM - edited 02-21-2020 09:38 PM
Okay, I've been going F*****G crazy trying to figure this out... What am I missing?!
I'm attempting to get a site-site VPN setup in PT as a test before rolling out in prod, no matter what I do I can't seem to get it working...
The branch router is configured as below, but for some reason the VPN tunnel fails. Upon closer inspection, it looks like traffic from 192.168.1.0/24 destined for 192.168.0.0/24 isn't getting encrypted at all and is being sent to 10.0.0.6 unchanged and as 10.0.0.6 is 'The internet' it's no surprise the packets are being killed...
Thanks in advance for any help / advice!
crypto isakmp policy 1 authentication pre-share crypto isakmp key cisco123 address 10.0.0.1 crypto ipsec transform-set CRYPTOSET esp-aes esp-sha-hmac crypto map CRYPTOMAP 1 ipsec-isakmp set peer 10.0.0.1 set transform-set CRYPTOSET match address vpnacl interface GigabitEthernet0/0 ip address 10.0.0.5 255.255.255.252 duplex auto speed auto crypto map CRYPTOMAP interface GigabitEthernet0/1 ip address 192.168.1.254 255.255.255.0 duplex auto speed auto ip default-gateway 10.0.0.6 ip route 0.0.0.0 0.0.0.0 10.0.0.6 ip access-list extended vpnacl permit ip 192.168.1.0 0.0.0.255 192.168.0.0 0.0.0.255
Solved! Go to Solution.
- Labels:
-
Other VPN Topics
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2019 08:49 AM
VPN configuration looks ok. What about the NAT configuration? The VPN traffic could be being translated and therefore not matching the crypto ACL. You should deny traffic to the destination subnet in the NAT ACL, this should be above the permit (traffic to be natted).
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-07-2019 11:45 PM
Can you post other side configuration, and tell us how these are connected ? Since we see Private IP address here brach side ?
Do you have a reachability between these sites ?
what is the logs shows ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2019 12:26 AM
Hi,
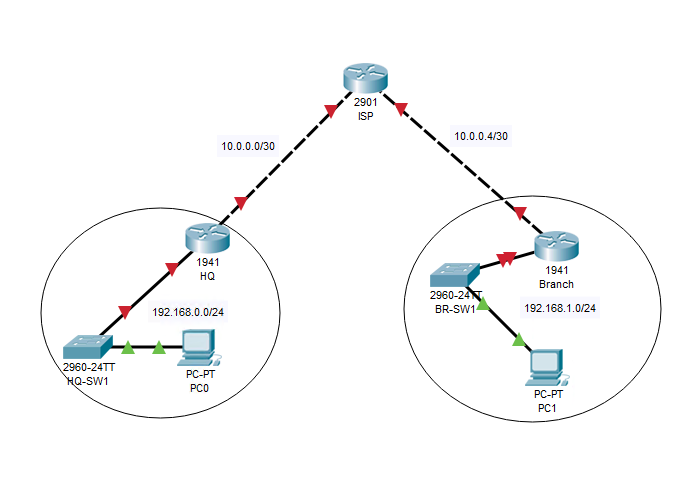
Below is a screenshot of the topology, I'm only using private IP addresses on the 'ISP' side of things as this was a topology that I had already used for another test last year, and I couldn't be bothered to change them, and I don't think that would make much difference for just a proof of concept in a PT session...
As for the config on the HQ side, it is the same as that of the branch, except for the obvious differences, such as IP addresses, host name, etc...
Also, the branch can get a web page from a web server on the HQ side with the configured dynamic NAT, so I know that both sites have inter-connectivity...
Thanks,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2019 08:49 AM
VPN configuration looks ok. What about the NAT configuration? The VPN traffic could be being translated and therefore not matching the crypto ACL. You should deny traffic to the destination subnet in the NAT ACL, this should be above the permit (traffic to be natted).
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2019 10:58 AM
That was exactly it, traffic was getting NAT'ed before getting encrypted...
Thanks for the advice!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide