- Cisco Community
- Technology and Support
- Security
- VPN
- Site-to-site VPN, FIREPOWER 1010 software 6.6.1-xx, not connecting
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Site-to-site VPN, FIREPOWER 1010 software 6.6.1-xx, not connecting
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2021 10:07 PM
Hello everyone, can someone please advise me to solve this problem;
I have 3 Cisco @Firepower 1010 Threat Defense Software
software 6.6.1-xx
I want to configure @site-to-site VPN. I have done all the configuration that the wizard guides me but the connection between sites is not successful,
I have created the security policies to allow incoming and outgoing traffic, the local and remote network are different subnets
* 192.168.100.0 / 24
* 192.168.50.0/ 24
I have public IPs assigned to the port WAN of each Firepower (internet connection is ok), the ping reaches the public IPs. I suppose that the problem is in the exit policies, I already reviewed it but there is no positive result.
Can someone guide me or give me an idea on how to solve the problem?
Thanks
Greetings
Louis
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2021 12:36 AM
Have you tried generating traffic from the local network to the destination in order for the VPN to establish? The VPN will not establish unless interesting traffic is sent.
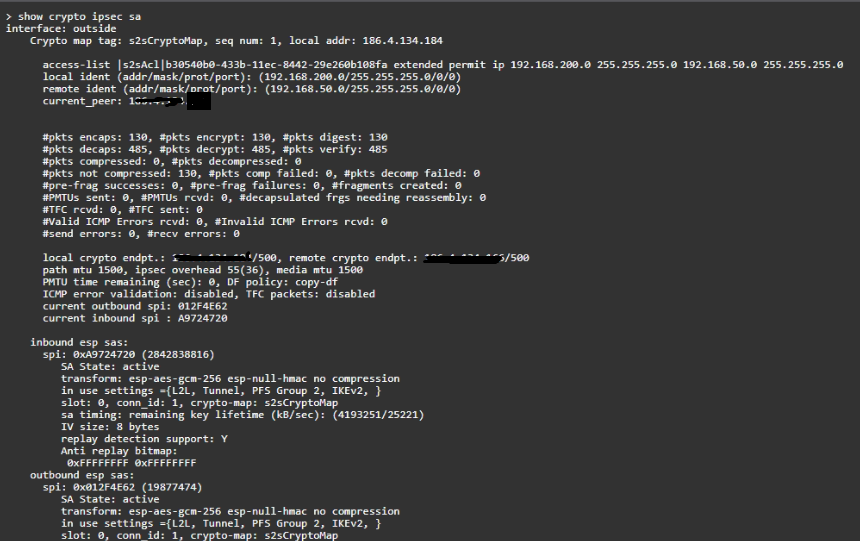
Has a VPN actually been established, run "show crypto ipsec sa" and provide the output for review.
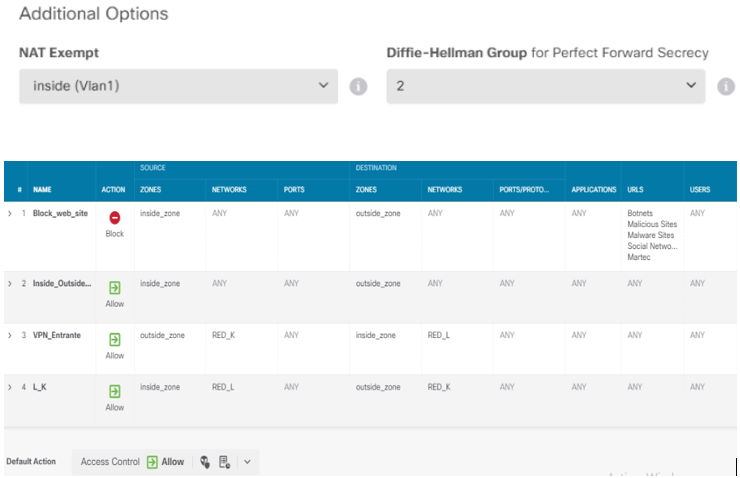
Have you configured NAT exemption rules to ensure traffic between the local and remote networks are not unintentially translated?
Run packet-tracer from the CLI twice and provide the output from the 2nd.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2021 11:06 AM - edited 11-14-2021 11:06 AM
Thinking the same, NAT exemption? Didn’t see anything from your first post regarding NAT exemption.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2021 01:57 PM
Hello Rob.
Thanks for supporting,
Is there a command to generate traffic to the remote network.?
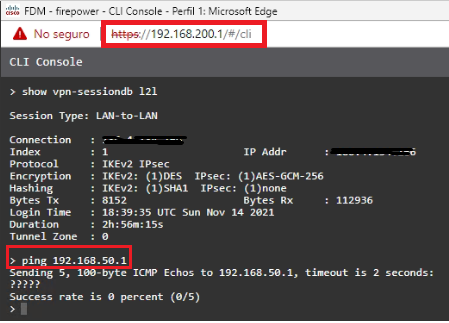
The problem is that the ping is not reached from the local network 192.168.200.0/24 to the remote network 192.168.50.0/24, even in reverse.
In this case ping gateway to gateway through the VPN
The NAT exention configuration is as shown in the capture
Subnet K: 192.168.50.0/24
Subnet L: 192.168.200.0/24
I hope you can help me,
Thank you
Regards,
Luis
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2021 02:09 PM
@Luis.Rodrigo the VPN is up as the IPSec SAs have been established, the fact that the encaps|decaps counters are increasing confirms it is working.
You cannot test from the FW itself as the ping would be from the egress interface (outside), not the inside (192.168.200.1). You need to test connectivity by sending traffic (a ping or anything) from a device behind the FW such as a PC to a device behind the other firewall.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-15-2021 05:59 PM
Hi Rob, sorry for the delay.
I have tried the ping to the other network from the FPR and from an internal computer and the ping does not respond. The VPN connection is active, I have used the command that you advised me to check and everything is ok
The issue is definitely in the inbound / outbound rules.
Can you advise me how I should make the configuration.? I thank you and I appreciate your help very much.
Greetings
Luis
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2021 10:58 AM
@Luis.Rodrigo if the counters are going up and the output of packet-tracer confirms an "allow", it looks like everything is working ok with the VPN, ACP rules and NAT.
Can you confirm the device you are pinging doesn't have a local firewall enabled that is blocking the traffic?
You can run system support firewall-engine-debug from the CLI of the FTD, filter on the traffic (source or destination IP), generate some traffic and confirm which rule the traffic is matching and whether it is permitted.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide