- Cisco Community
- Technology and Support
- Security
- VPN
- Re: VPN - ISE Authentication Policy - Azure SAML
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
VPN - ISE Authentication Policy - Azure SAML
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2023 12:26 PM
Hello All,
Components Used: Cisco FMC + FTD 1120, Cisco ISE, Azure SAML/SSO
We're moving from ASA + ISE + Duo 2FA to Azure SSO authentication. But, we still want to use ISE as the Authorization and Accounting server. As well as posture assessment.
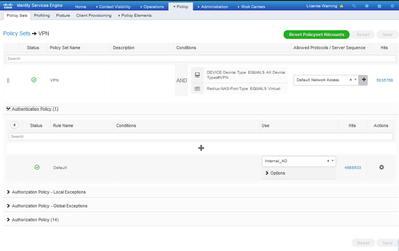
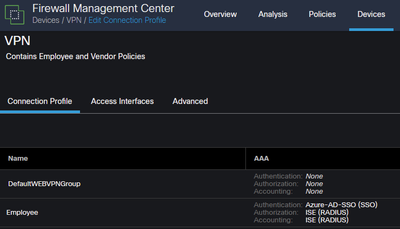
Now, I've gotten the FTD and Azure pieces configured. When I use AnyConnect and connect to the VPN I get prompted for my Microsoft creds and I am able to successfully connect. On ISE however, it shows as authentication failed, which I;m sure is because the VPN Authentication policy still points to our internal Active Directory server.
This FTD/FMC setup is for a secondary location. We will eventually be moving all ASAs to FTD devices. So, my question is, do I need to create a 2nd Authentication policy, one that doesn't point at our internal AD servers? If so, what do I choose here?
I'm confused about what to do here since technically the Authentication is being done by Azure/Microsoft.
ISE:
FMC:
Any thoughts or suggestions would be greatly appreciated!
Thanks in Advance,
Matt
- Labels:
-
Remote Access
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2023 02:26 PM
Check this nice doc from Michael Lorincz out:
https://www.lookingpoint.com/blog/ra-vpn-on-ftd-with-aad-duo-authc-and-ise-authz
That guide seems to point pretty much the same implementation you are trying to do.
Hope this helps!
-JP-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-01-2023 08:58 AM
Hey JP, thanks for the reply, and sorry for the delay.
I'll check out that link and reply back. Thanks again!
-Matt
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide