- Cisco Community
- Technology and Support
- Security
- VPN
- Re: VPN Tunnel connecting at a unconfigured setting - Phase 1 Timer
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 06:52 AM - edited 04-25-2024 07:12 AM
OK, so I've got a set of ASA's and we are migrating them to Firepowers, and all seems ok.
In the past we have noticed that for some reason on the ASA's, no matter what you specify as the parameters for phase 1, the rekey timer always connects at 3600 seconds.
We were hoping that when we moved to the Firepowers this issue would 'go away', however on testing we are seeing the following,
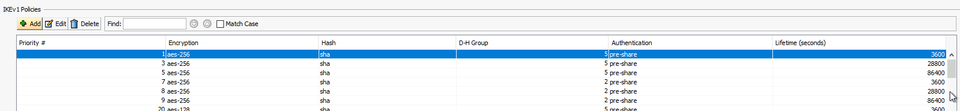
which is that on the ASA we have the following configured for IKEv1 -
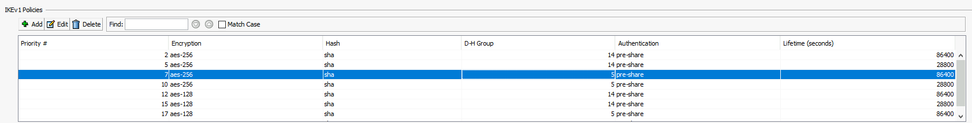
And on the firepower we have -
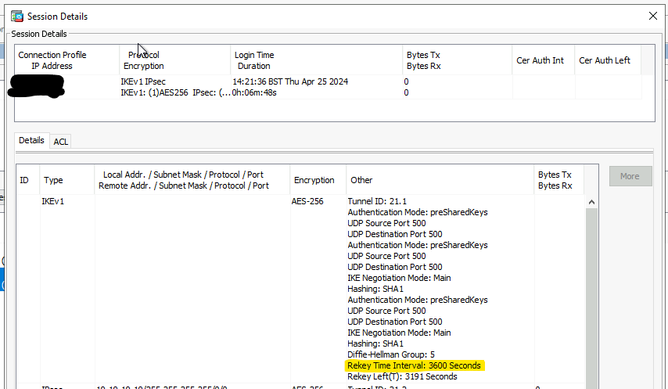
So when I run the packet tracer (from the ASA to the Firepower) to test the parameters of the link we see this on the firepower -see highlighted -
So how can this be ? there is no 3600 configured on the firepower - so how can the link be connecting ?
Is the ASA forcing something on the firepower ? Is this excepted behaviour ? is there any documentation out there that can shed light on this ?
Any help or advice gratefully received - otherwise I can see this being a TAC case.
Regards,
S
Solved! Go to Solution.
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 07:28 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 07:05 AM - edited 04-25-2024 08:25 AM
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 07:15 AM
OK, a couple of things - I've updated the text as it wasn't clear as to which end was which.
To the response from MHM... - well, yes I know the timeout is controlled by the initiator, but the 'thought' was that it was the " first best match" in the configured settings that each device then agrees upon.
So, No, the ASA isn't the responder in this case, and even if it were, it still asks the question - Why is the link rekey timer 'connecting' at 3600 ? when this option isn't on the firepower ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 07:30 AM - edited 04-25-2024 08:26 AM
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 07:23 AM
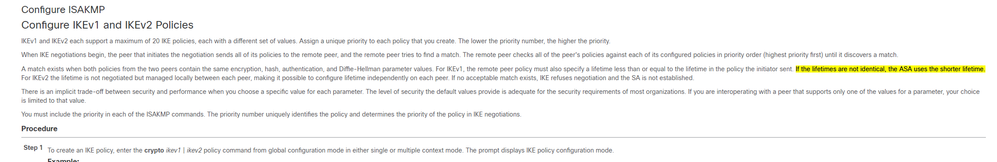
Hi Stephen, if I understand your question correctly, you are asking why the FTD is using a lifetime value that is not configured on itself? if so, the answer is because the lifetime value can have a different value on both peers, and when they start the negotiation they will agree on the lowest value. In fact, as you shared in the screenshots the FTD has a higher value, however, it uses the lower value that is configured on the remote peer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 07:28 AM
Aref, OK, that I can understand, but when you have 50 VPN's connecting to a device, and some (as they are customers) want to connected at 86400, some at 28800 and you get the picture - you are basically saying that that goes out of the window and the link will connect at the first configured option ? so why have a list and the ability to have multiple settings when on one for each 'variable' is needed ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 07:28 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 07:43 AM
Aref,
Thanks for the link, wish I'd found that beforehand.
I do have another question - in general a vpn link is made up of enc. hash, timer etc - apart from the rekey timer (as mentioned above) are there any other 'settings' that can be 'imposed' on a link when 'handshaking' ?
I referring to the DH group option, we have a link from the Firepower to AWS, and the end customer stated they wanted to use DH grp 5, yet when the handshake took place - the link connects at DH grp 14. Now at our end we have 5 and 14 configured (see firepower screenshot above) - so any ideas ? or is the customer wrong ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 08:00 AM
You're very welcome Stephen. The only value that can be different is the lifetime, all the other values hash, authentication type, encryption, and DH must match between the peers, otherwise the negotiation will evaluate the next policy, and if there is no match the tunnel won't be established.
Interesting they want to move away from DH 14 and go with DH 5, but regardless, if they said they wanted to move to DH 5 and the tunnel still gets established with DH 14 then they would most likely still have the DH 14 configured on a policy that is being elected during the negotiation. Otherwise as mentioned before the tunnel won't come up.
Also, I see on your Firepower you have multiple policies pretty much exactly the same and the only difference is the lifetime. You wouldn't need all those redundant policies, one is enough and as mentioned before, the lower lifetime value will be used.
Feel free to ask any further questions, I'm happy to help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 08:20 AM
Aref,
No further questions - what you have posted in this question has been very gratefully received - it will be put to good use.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 08:22 AM
Glad I could help, Stephen.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 07:58 AM - edited 04-25-2024 08:24 AM
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 08:00 AM - edited 04-25-2024 08:24 AM
MHM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide