- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless - Mobility Knowledge Base
- Integration of ISE (Identity Services Engine) with Cisco WLC (Wireless LAN Controller)
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
08-26-2011 08:22 AM - edited 11-18-2020 02:54 AM
- Introduction
- What is ISE
- Key features of ISE
- What happens behind the boxes
- Components Used
- Network Diagram
- Configuration
- Cisco 5500 Wireless LAN Controller Configuration
- ISE Configuration
- Limitations
- ISE is from NAC-OOB – this differences are as per IS Ever 1.0
- Related Information
- Related Links
- More Information
Introduction
This document provides a sample configuration for Integration of ISE (Identity Services Engine) with Cisco Wireless LAN Controller.
NOTE:- This document is about posturing the client and based on 7.0.116.0. The same information is also mentioned in the VoD.
What is ISE
Cisco Identity Services Engine (ISE) is a security policy management and control platform. It automates and simplifies access control and security compliance for wired, wireless, and VPN connectivity. Cisco ISE is primarily used to provide secure access and guest access, support BYOD initiatives, and enforce usage policies in conjunction with Cisco TrustSec.
Key features of ISE
- AAA protocols - it uses RADUIS Protocol for Authentication, Authorization and Accounting. ISE NAC and WLC uses RADUIS protocol to communicate with each other.
- Authentication protocols – It supports various types of authentication protocols. PAP, MS-CHAP, EAP-MD5, PEAP, EAP-FAST, EAP-TLS.
- Access control – it provides wide range of access control mechanism like - URL Redirect, Vlan Assignment, downloadable access control lists dACLs), and SGA tagging.
- Posture – ISE verifies endpoint’s posture assessment via either a NAC-client-Agent or web agent. An admin can configure various kinds of posture conditions like – latest OS patches, Antivirus etc.-
- Profiling – Profiling is for identifying and analyzing end-points in the network, end-points can be any device in the network which try to access network like – iPhone, iPad, laptop, printers etc. ISE comes with several pre-defined profiles for end-points. We can also create our own and we can define specific authorization policy to those profile.
- Policy model – policy model offers attributes and rule based policies for creating flexible and more specific access control policy.
- Guest lifecycle management - this feature is used to create a lobby admin, in ISE terminology, it is called sponsor user who can create login credentials for guest user.
- Platform options - ISE available as a physical or virtual appliance. It can also be installed on VMware.
- Monitoring, Troubleshooting and Reporting are easy and user friendly.
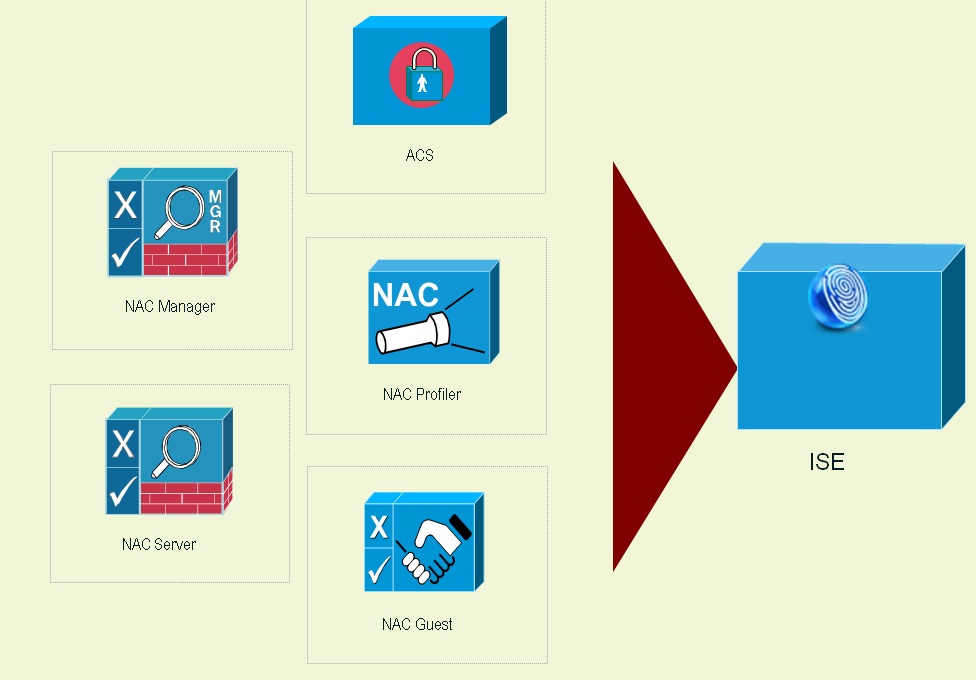
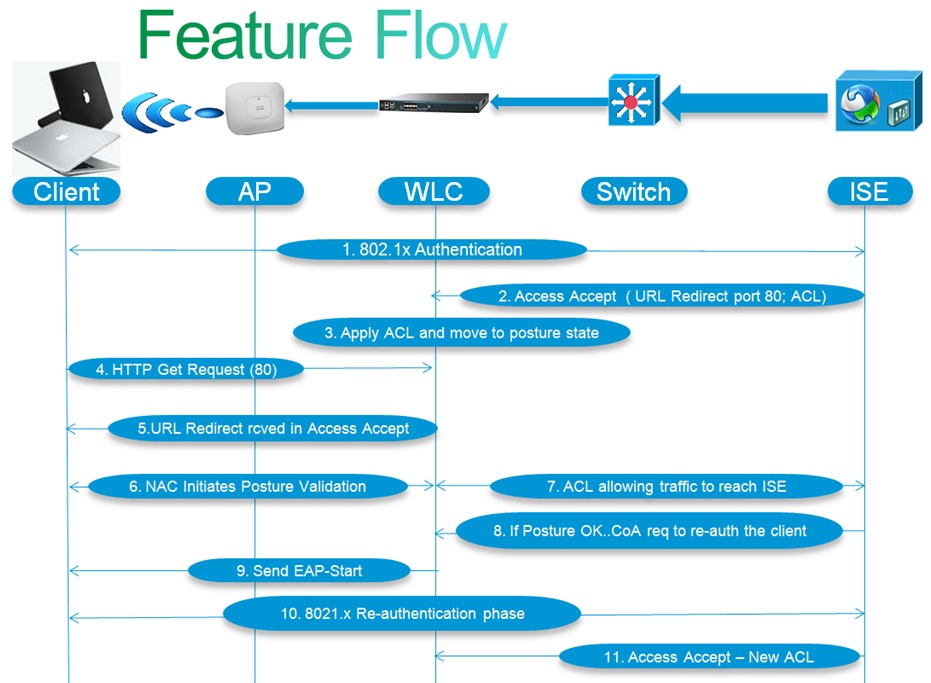
What happens behind the boxes
2) In the authentication process, ISE will send Access Accept that carries redirect URL for port 80, ACLs and other attributes, if configured. Access Accept will be sent to the WLC.
5) WLC will redirect this request to the pre-define URL that was provided by ISE in Access Accept. ISE responds to the client and provides a page to initiates posture validation.
6) Once client completes assessment, ISE will send a Radius CoA-Req with re-auth service sent to WLC. (CoA stands for Change of Authorization)
7) Then WLC will initiate re-authentication of the client by sending EAP-START to the client.
9) ISE sends new profile and Access Accept carries new ACL (if any) to provide full access (as per ACL rules) to the network.
Components Used
- Cisco 5500 series Wireless LAN Controller
- Cisco Identity Services Engine (ISE) Appliance
- Windows Client
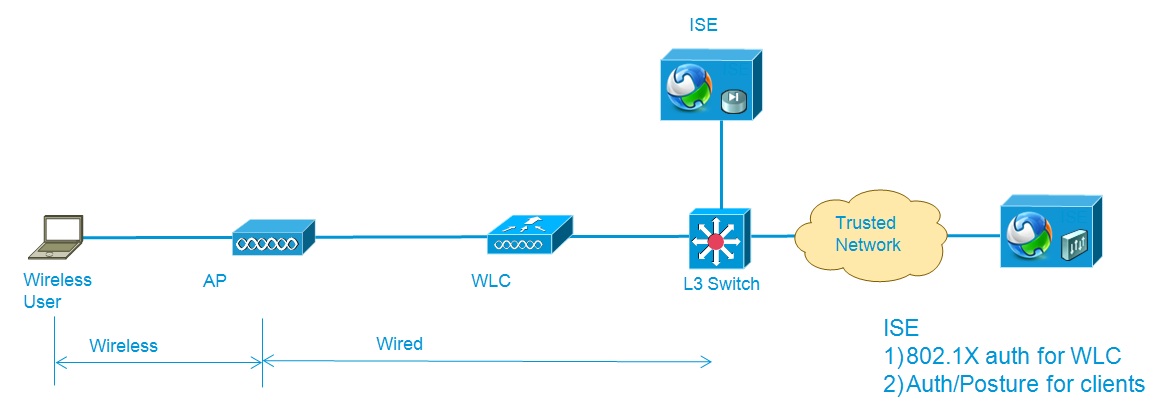
Network Diagram
We have an AP and a WLC, connected to a switch. The traffic will be encapsulated using CAPWAP protocol between AP and WLC. An ISE is sitting somewhere in the network and have connectivity to the WLC for posturing, authentication etc. Clients are associated to the WLC.
Configuration
Now, let’s discuss what are the things need to be configured on Cisco WLC –
- WLAN with dot1x security
- AAA-Override on WLAN
- Radius NAC on WLAN
- ACLs
- ISA as AAA server
Cisco 5500 Wireless LAN Controller Configuration
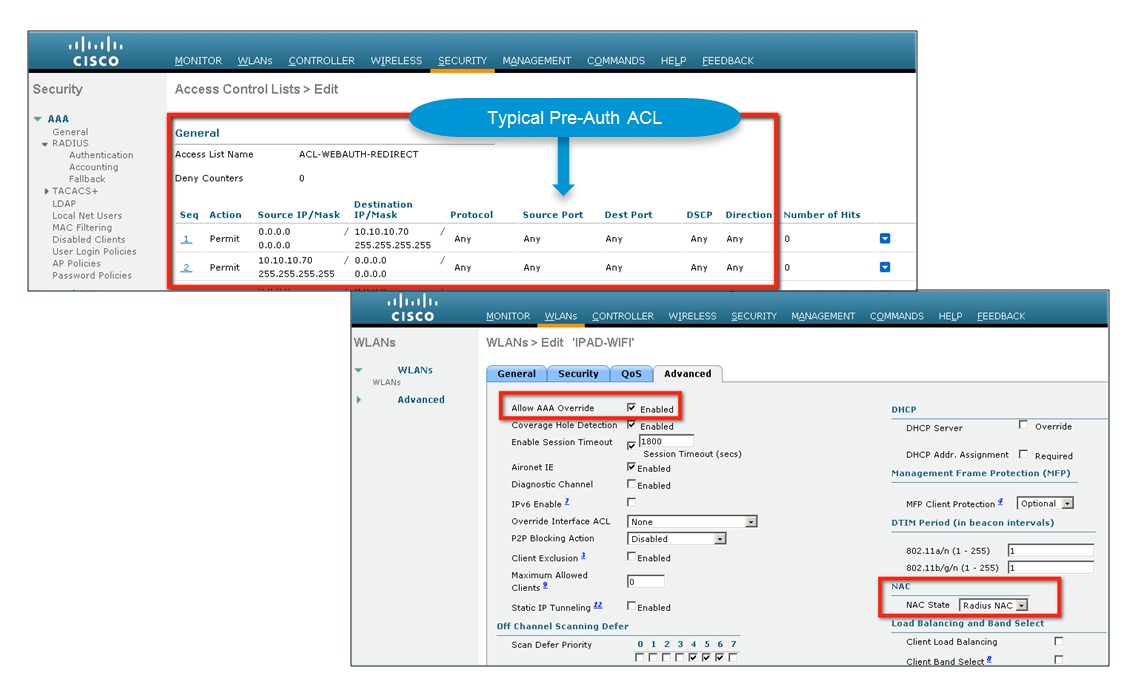
WLAN is named as ISEnWLC. Keeping security with default Wpa2. Advance Tab --> Enable Radius NAC. When we enable Radius NAC, AAA-Override feature will be enabled automatically.
NOTE:- If we configure it through CLI, AAA override should be configured first before configuring Radius-NAC on the WLAN.
Creating ACLs:-
ISE differentiates client in to 3 categories and we need to configure 3 different ACLs in order to give specific access to clients. It’s not mandatory to have 3 ACLs. We can also use only 2 ACLs. Suppose an admin does not want to differentiate unknown and non-compliant users and do not want to give different access policy to them for him. In that case, he can use 2 ACL, One ACL for unknown and non-compliant clients and second ACL for compliant clients.
It all depends on how Admin wants to configure it. We have created only 2 ACLs. we are treating unknown and non-compliant client in the same way.
Go to Security -> click on Access control lists--> We have configured 2 ACLs -
Limited_Access and Full_Access
Limited_Access will allow only ISE traffic and Full_Access will not block anything.
Now we add the ISE as AAA server. On the Security Tab --> select Authentication –> give ip address, shared secret. Shared secret should be same on ISE as well.
As per Cisco recommendation, an admin should configure 3 ACLs. let’s discuss more on ACLs and Posture state of clients/users.
Basically ISE differentiates a client into three categories, in order to do Posture:-
- Unknown – when a new client/user associates. It will be unknown to ISE.
- Non-Compliant – when client is not able to remediate itself within a time window then ISE puts the client into Non-compliant state.
- Compliant – when client is able to meet the posture requirements.
So we need 3 different access profiles for unknown, non-compliant and compliant. Each profile will have an ACL. As per user/client’s state, ISE will send the profile to the controller. Then controller will apply the ACL and other attribute into the client database.
Let’s see what kind of traffic should be allowed:-
- ACL for unknown should allow traffic so user can access ISE or I would say that user should able to get the ISE page for posturing and it should also allow the traffic so clients can remediate itself.
- ACL for Compliant – it should allow all the traffic but it all depends on the Admin and company’s policies.
- ACL for Non-Compliant – it should block everything.
It’s recommended to configure 3 ACLs for posture but not mandatory
ISE Configuration
The main purpose of this Document is to discuss posture and integration of ISE NAC and WLC. There are so many options, combination, attributes on ISE to configure but it’s tough to cover all in this document, so we will discuss some of the basic configuration ISE for wireless clients in order to do posture:-
Administration –
- Identity Group
- Identity…..instead of local user we can also configure Active Directory.
- WLC with shared secret.
Policy Elements
Condition -
- Posture Condition.
Results -
- Authorization Profile for pre and post posture.
- Posture Requirement – map the posture condition.
- Client Provisioning – upload agent software (client or web agent).
Client Provisioning -
- Here we map the NAC_Agent to the Identity Group.
Authorization -
- Creating rules. Give the specific Authorization to clients..like non-compliant or compliant….etc.
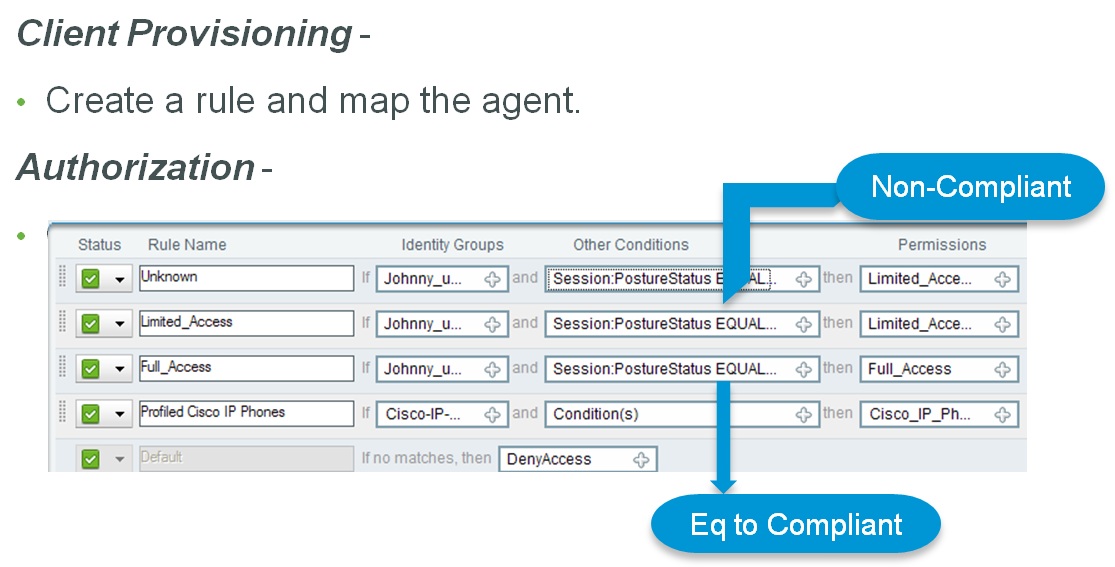
Limitations
- No support for guest clients – posture for guest user is not supported.
- Hreap local switching is not supported -
- No support for wlans without 802.1x support
- Client will go through posture during slow roam – when client is associated used 802.1x (not wpa2 or cckm) then when client roams from one wlc to other – wlc will send new session ID hence client will again go through posture validation process.
- No support for guest tunneling mobility
- Mac auth bypass is not supported
- Vlan pooling is not supported.
- No support for WGB AP
- No support for AP group.
ISE is from NAC-OOB – this differences are as per IS Ever 1.0

- ISE is a single box solution but in NAC-OOB, you will have to deploy multiple appliances for complete solution like – profiler, guest server, CAM, CAS etc.
- ISE uses Radius protocol and NAC-OOB uses SNMP.
- In ISE, client will be restricted by pushing ACL , vlan can also be pushed to the client but change of vlan not yet supported for wireless client after posture validation as per wlc 7.0.116.0.
- Since ISE uses Radius protocol, wlan has to be configured with dot1x security. In other hand NAC-OOB supports all types of security.
Related Information
We have Two Video's from Hemant Sharma. Hemant is a software engineer in the Wireless Business Unit at Cisco.
Please Rate the Videos. PART 1 and PART 2.
Related Links
More Information
Ask the Expert: Cisco BYOD Wireless Solution: ISE and WLC Integration
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Are there any plans to intergrate HREAP local-switching with ISE
Regards
NikhiL
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Nikhil,
sorry can not disclose here about cisco's plan.
Thanks
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Hemant,
I work in the middle east and I have a customer who have multiple offices connected to a Data Centre location and is planning for HREAP. They are planning for ISE also.
Can you help me with the features that are supported on the HREAP + ISE in the current release
Thanks
NikhiL
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi
It's not very clear about L2, i.e. VLAN. Where and how I need to place VLANs and trunks?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Vinay,
Very good article, thanks! A couple of questions, it will be really nice to have a single Controller/General setting for ISE to get all types of information on WLC attached clients(via AP), as I understand it, even though all clients terminate on the WLC, it cannot do DHCP snooping, will need to specifically add SNMP trap destinations pointing to ISE, and there is no easy way to forward all client http traffic to ISE. It may be nice to be able to integrate the ISE for profiling purposes with the WLC at a central page on the WLC, where all or part of the above are turned on.
Also, the NAC state turn on on the Wlan is that all that is needed to turn on CoA (in addition to AAA override)?
Thanks,
Prakash
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
it is written :"
In ISE, client will be restricted by pushing ACL , vlan can also be pushed to the client but change of vlan not yet supported for wireless client after posture validation as per wlc 7.0.116.0"
Is that possible in wlc 7.2 ?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
good one vinay.
thanks
swap
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Its an Amazing Document!!!! Really Helpful!!!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
This document is really old. Is it still relevant for ISE 2.X platforms?
RADIUS NAC is not an option in my WLC running code ver 8. The option is now ISE NAC. Also does this document assume you are already using ISE for your clients to authenticate?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello All,
recently I have instilled ISE version 2.3.
so far I have configured the ISE upto TACACS,
the questions are, what is next?
do I have to add the domain then client?
Or do I have add AAA?
can someone kindly advice me the process to take or send me the manual documentation please?
Appreciated with any help.
Regards,
Star
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: