- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Re: 9800 - Locally switched WLAN with AP connected to access port
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
9800 - Locally switched WLAN with AP connected to access port
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-08-2021 05:16 AM
Dear all,
anyone has any recommendation what are the requirements from Catalyst 9800 (IOS-XE 17.3.3) configuration point of view (Flex Profile, Policy profile,...) in case you have an AP which suppose to broadcast locally switched WLAN, however on location AP is physically connected to is a flat network, that mean single VLAN for everything and switch port AP is connected to is simply access port (not a trunk)?
Just wondering is there is a easy way, how to configure an AP to ignore VLAN information if AP is connected to an access port? Since you have to define Native VLAN ID in Flex profile (therefore the very same VLAN as local one from where AP gets an IP address from) but also there is VLAN definition within policy profile (Access Policies tab) which you need to specify (this is then VLAN clients connecting to locally switched WLAN get's an IP address from).
Scenario might be either all is in VLAN 1 or any other VLAN you can think of. Is there any "blunt" config how to prepare AP configuration with TAGs (policies, flex,...) so clients are able to get an IP?
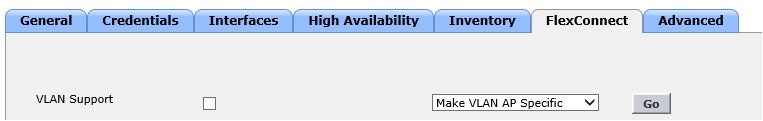
So far I can get this work in case Flex profile (Native VLAN ID) and Policy Profile reflect the very same VLAN ID. But that is quite extensive to prepare for each and every scenario. On Legacy WLC (AireOS based) you simply disable VLAN Support and that worked.
OR there is no such way and simply it means I have to define for each of such scenario dedicated Flex profile (with Native VLAN ID reflecting the VLAN ID on site), Policy Profile (reflecting the same VLAN ID as is Native one) but this to be done for each and every location?
Baring in mind there might be 20 location where is VLAN1, then other 30 locations with VLAN2 and other locations with VLAN10 etc....
Thank you
Martin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2021 02:53 PM
Not recommended, butt to make it work you can have the VLAN configured under Policy profile set to 1. This way all clients are set to Native VLAN set under the Flex profile. This way you are reducing the number of policy profiles, but Flex profile per site type is required.
I would say work on redesigning the network to include a dedicated AP Management VLAN at least. This way you will save lot of troubles.
TAC recommended codes for AireOS WLC's
Best Practices for AireOS WLC's
TAC recommended codes for 9800 WLC's
Best Practices for 9800 WLC's
Cisco Wireless compatibility matrix
___________________________________________
Arshad Safrulla
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2021 03:51 AM
Hello Arshad,
But will VLAN=1 configured in Policy Profile reflect always the right Native VLAN in the FLEX profile? As not always it is VLAN1 on site where the "flat" design is in place. There are locations where vlan is 1 but also other locations where it is 2 or 130 or 510 etc.
So If I keep Policy Profile with VLAN 1, and it is assigned to the AP which has flex profile with Native VLAN = 130, does it mean that clients connected to such WLAN will be really on native VLAN even though PolicyProfile has 1?
Obviously it would be best to have AP Management VLAN (no doubt and I would love to achieve that...) however it is not always an easy task to reconfigure hundreds of locations....
Thank you
Martin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2021 04:18 AM
So If I keep Policy Profile with VLAN 1, and it is assigned to the AP which has flex profile with Native VLAN = 130, does it mean that clients connected to such WLAN will be really on native VLAN even though PolicyProfile has 1?
Yes, last time I checked was on 16.12.4a. I can confirm it worked there. If you in any new version I would recommend you test it in a lab environment first.
TAC recommended codes for AireOS WLC's
Best Practices for AireOS WLC's
TAC recommended codes for 9800 WLC's
Best Practices for 9800 WLC's
Cisco Wireless compatibility matrix
___________________________________________
Arshad Safrulla
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-13-2021 02:18 AM
Hi Arshadaf,
Nope this is not the case with release 17.3.x (17.3.3 to be precise). If you have Flex profile with defined Native VLAN 1 and then Policy Profile which says clients are in VLAN 100 (obviously AP mode = Flex mode and there are some centrally and also locally switched WLANs), then such clients are not able to connect to locally switched WLAN while switch port is configured as access port.
Issue is with actual traffic as clients won't get an IP address because AP assume clients are in VLAN 100 but port is access port in VLAN 1.
With AireOS you just simply disabled "VLAN Support" on the AP level and it worked even though you had WLAN configured for clients to be in VLAN 100.
It seems it not anymore available to have it "that" simple.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-13-2021 02:58 AM
This is my approach to reduce Policy Profiles in C9800.
- Create a common Policy Profile pointing VLAN to a VLAN name, not VLAN Id. I'm using a policy profrile named "LOCAL_CORP" mapped to VLAN "corpvlan01", but you can create different ones for different policy features with "corpvlan02" and so on.
- Next step is to create a Flex Profile for every site where you define the Native VLAN and WLAN-2-VLAN mapping. Let's say for example "Madrid_Flex" using "Native Vlan=1" and "corpvlan01=100", and "Paris_Flex" using "Native Vlan=1" and "corpvlan01=200"
- Now create new Site Tags mapping every Flex Profile to the Common Policy Profile.
- That's it.
With this approach, and depending on the standardization of your network, you can have only ONE Policy profile (as me) and then a Flex profile per site. And even for the case of small sites with 1-AP only, I have created a comon Flex Profile for all of them in the same country so reducing the amount of Flex profiles and Site tags ("Spain_Flex" and "France_Flex"). In this case I need to take care not to associate more that 150 APs to the same Flex profiles as per the best practices.
With this approach you can deal with AP switchports configured in access mode in whatever VLAN, as far as the native vlan and your "corpvlan01" matches. Same happened in AireOS.
HTH
-Jesus
*** Please rate helpful responses ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-13-2021 06:34 AM
Hi Jesus,
Does VLAN Name must be the same on local site at switch AP is connected to? I suppose not.
Using Flex profiles with different WLAN-2-VLAN mapping means that each of such Flex profile you have to assign to an AP by Site Tag (which basically applies Flex). Then such site tags you should keep a tag per location to prevent unnecessary data being transferred between more sites and APs (hard rule which can be easily misused). Therefore ideally you need a site tag per location which might not be easily maintained if you have 1000+ locations.
However if you are utilizing TAG assignment with Filters (based on regex) there is also a limitation of 1024 filters in total...Which might be tough if you have more locations to always assign right site tags containing correct Flex profile etc.
With disabled "VLAN Support" I saw it was fairly easy to e maintained.
I will try to look into your idea, but kind of tend to believe it might be again unnecessary complicated from global scale perspective.
But thanks for your idea how you have achieved that.
Just let me know if in your case usage of VLAN Name instead of VLAN ID has some relation to the real VLAN name onsite (location where AP is connected to).
Thanks a lot
Martin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-13-2021 08:56 AM
Hi @Martin Jelinek ,
Your guess is right, VLAN name under c9800 does not have to match VLAN name on the switch side, it's only a local way to reference that.
And again, your guess is right with regards of the multiple sites associated to different Site tags (which applies to Flex profiles). For this approach, and for small sites, I'm using Flex/Sites per Country or Region. For example, all small sites with less than 2 APs in a country are using the same Flex/Site config, hence I have between 5 to 50+ sites sharing the same one "FRANCE-CLIENT-FLEX" / "FRANCE-CLIENT-SITE", thus minimising the administative task as they all have the same topology (VLAN 100) for locally forwarded WLAN.
The side effect of this approach is that all APs under the same Site tag share their cached credentials, and they download the new firmware from one of them when using ap image pre-download feature. Nothing to worry about I hope.
HTH
-Jesus
*** Please rate helpful responses ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2021 01:45 AM
Hi @JPavonM
Thanks for further info. Looks you are lucky to have even all small sites the very same topology. In our case if might not always be ideal and even in the country more small locations might have different VLAN used in the flat design.
And in combination to automate or to make deployment as easy as possible with 9800 we are trying to utilize Filter TAG assgnment based on AP hostname regular expression. Which can be done very easily if proper naming standard is in place. But just the "stupid" limitation for max. number of filters be 1024 (because of priorities) which I do hope will be fixed of extended in future releases at least.
I will try to look into this as you suggest, just still hoped for VLAN Support be disabled option which seems is not in there...
Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2021 02:11 AM
@Martin Jelinek it has been a lot of work to standardise all the deployment with a common VLAN for small sites, and same VLANs for every service in bigger ones, but that work allowed us to unify not only wireless configurations but also other services such as security.
With regards of your small and plain sites, you can also use this approach to create just one Flex profile for all of them. The only thing you need to do is to use the same Native VLAN Id than the WLAN-2-VLAN Id. Remember that in this case the AP forward the traffic without any VLAN tag so you can configure the switchport of the AP in access mode to receive untagged packets in whatever VLAN, so allowing you to aggregate all those APs under the same Flex profile.
HTH
-Jesus
*** Please rate helpful responses ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2021 02:35 AM
Thanks, I will try to look into this and do some testing as well.
Certainly it is a hint worth to give a try in our case if that can at least simplify something.
Thank you
Martin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2021 07:45 AM
There is always a time when you have to assess how the network is designed and determine if things need to change. It seems like you can start to standardize and simplify the environment, but it comes down to planning and execution. I have worked on many migrations because of old designs that do not scale well. All it takes is starting small and migrating one site at a time. Eventually all the sites will get migrated and standardized and life will be easier. Always look at what can be improved and figure out how to get there.
*** Please rate helpful posts ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2021 10:59 PM
Agree
Therefore migration is ongoing and site standardization as well, just this one will take about a year to be finalized, while migration must be completed much sooner.
However that is true it must be done and will be...one day.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-25-2021 02:17 AM
I know… I’ve been in that position and you just focus on migrating wireless one site at a time which makes your configuration complex. Then it’s the migration after the fact when the subnets gets migrated and you now how to create a new configuration, but hopefully a simple config that you can migrate site aps to.
*** Please rate helpful posts ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2021 12:11 AM
Hi @Martin Jelinek you can also look at the option of Flex Central DHCP and NAT option. In this case all the clients connecting at remote branches will be assigned an IP centrally, but when the traffic leaves the AP, AP will NAT all the traffic for that SSID using AP's management IP. (Similar to Meraki NAT mode AP's if you are aware)
TAC recommended codes for AireOS WLC's
Best Practices for AireOS WLC's
TAC recommended codes for 9800 WLC's
Best Practices for 9800 WLC's
Cisco Wireless compatibility matrix
___________________________________________
Arshad Safrulla
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide