- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Key policies for Wireless device
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2022 01:07 AM
When I enable SSH/SSL in WLC 9800, Where is the private key stored?
Solved! Go to Solution.
- Labels:
-
Wireless LAN Controller
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2022 06:41 AM - edited 04-27-2022 06:42 AM
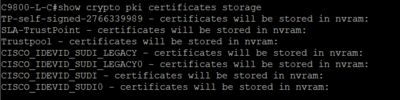
you can run the command
show crypto pki certificates storage
most likely it would be nvram
then execute
dir nvram: you will see .cer and .p7b certificate files
keep in mind that when generating the key pair, if you did not use the keyword exportable you wont be able to export it.
crypto key generate rsa exportable
usually I would not recommend exporting the private key, but I am sure you have use case for it.
hope this helps
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2022 01:11 AM
- In the running-config.
M.
-- Each morning when I wake up and look into the mirror I always say ' Why am I so brilliant ? '
When the mirror will then always repond to me with ' The only thing that exceeds your brilliance is your beauty! '
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2022 06:41 AM - edited 04-27-2022 06:42 AM
you can run the command
show crypto pki certificates storage
most likely it would be nvram
then execute
dir nvram: you will see .cer and .p7b certificate files
keep in mind that when generating the key pair, if you did not use the keyword exportable you wont be able to export it.
crypto key generate rsa exportable
usually I would not recommend exporting the private key, but I am sure you have use case for it.
hope this helps
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2022 12:14 PM
So FIPS-140 module doesn't save the crypto keys?
It's only for the key generation?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2022 07:08 PM - edited 04-27-2022 07:12 PM
Answer to both question is No.
FIPS (Federal Information Processing Standard) as the name suggests is security compliance standard for U.S. and Canadian government.
for e.g without FIPS Enabled you can use ssh client using sha1 to access 9800 but with FIPS enabled you can’t because it detects it as a non compliance security standard, many more standards like this/ list of appliance/ list of firmware make up FIPS.
you can read more about it here
I hope this helps
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-01-2022 12:43 PM
from the screenshot, I can see that the private keys are all stored in the devices. Can help to confirm there is no way to retrieve the private keys out of the device?
if there are ways to retrieve it out of the device, can it be used to spoof the device?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2022 04:41 PM
This was answered on this duplicate post:
https://community.cisco.com/t5/wireless/key-policies-for-wireless-device/td-p/4604199
Please click Helpful if this post helped you and Select as Solution (drop down menu at top right of this reply) if this answered your query.
------------------------------
TAC recommended codes for AireOS WLC's and TAC recommended codes for 9800 WLC's
Best Practices for AireOS WLC's, Best Practices for 9800 WLC's and Cisco Wireless compatibility matrix
Check your 9800 WLC config with Wireless Config Analyzer using "show tech wireless" output or "config paging disable" then "show run-config" output on AireOS and use Wireless Debug Analyzer to analyze your WLC client debugs
Field Notice: FN63942 APs and WLCs Fail to Create CAPWAP Connections Due to Certificate Expiration
Field Notice: FN72424 Later Versions of WiFi 6 APs Fail to Join WLC - Software Upgrade Required
Field Notice: FN72524 IOS APs stuck in downloading state after 4 Dec 2022 due to Certificate Expired
- Fixed in 8.10.196.0, latest 9800 releases, 8.5.182.12 (8.5.182.13 for 3504) and 8.5.182.109 (IRCM, 8.5.182.111 for 3504)
Field Notice: FN70479 AP Fails to Join or Joins with 1 Radio due to Country Mismatch, RMA needed
How to avoid boot loop due to corrupted image on Wave 2 and Catalyst 11ax Access Points (CSCvx32806)
Field Notice: FN74035 - Wave2 APs DFS May Not Detect Radar After Channel Availability Check Time
Leo's list of bugs affecting 2800/3800/4800/1560 APs
Default AP console baud rate from 17.12.x is 115200 - introduced by CSCwe88390
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide