- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Re: reason (Cred Fail) on Interface capwap
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
reason (Cred Fail) on Interface capwap
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2023 10:01 AM
Hello friends, I have a virtual WLC 9800 running version 17.6.5. A client is unable to connect from a specific PC, but can connect successfully from other devices. I have verified the credentials, and they are correct. The specific PC can connect normally to a WLC 2504.
2023/12/04 13:29:00.654796 {wncd_x_R0-0}{1}: [client-orch-sm] [17015]: (note): MAC: ec2e.9835.cc35 Association received. BSSID 00d7.8f2f.6c2d, WLAN lab_doble_authe, Slot 1 AP 00d7.8f2f.6c20, AP_REUNIONES
2023/12/04 13:29:00.655090 {wncd_x_R0-0}{1}: [client-orch-state] [17015]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_INIT -> S_CO_ASSOCIATING
2023/12/04 13:29:00.655422 {wncd_x_R0-0}{1}: [dot11-validate] [17015]: (ERR): MAC: ec2e.9835.cc35 Failed to dot11 ie validate aironet ipaddr. Aironet ipaddr IE is not present in Assoc Request
2023/12/04 13:29:00.655826 {wncd_x_R0-0}{1}: [dot11] [17015]: (note): MAC: ec2e.9835.cc35 Association success. AID 4, Roaming = False, WGB = False, 11r = False, 11w = False Fast roam = False
2023/12/04 13:29:00.656069 {wncd_x_R0-0}{1}: [client-orch-state] [17015]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_ASSOCIATING -> S_CO_L2_AUTH_IN_PROGRESS
2023/12/04 13:29:00.656460 {wncd_x_R0-0}{1}: [client-auth] [17015]: (note): MAC: ec2e.9835.cc35 ADD MOBILE sent. Client state flags: 0x71 BSSID: MAC: 00d7.8f2f.6c2d capwap IFID: 0x90000009, Add mobiles sent: 1
2023/12/04 13:29:00.662780 {wncd_x_R0-0}{1}: [client-auth] [17015]: (note): MAC: ec2e.9835.cc35 L2 Authentication initiated. method DOT1X, Policy VLAN 0, AAA override = 0 , NAC = 0
2023/12/04 13:29:00.664541 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [17015]: (note): Authentication Success. Resolved Policy bitmap:11 for client ec2e.9835.cc35
2023/12/04 13:29:07.229614 {wncd_x_R0-0}{1}: [errmsg] [17015]: (note): %DOT1X-5-FAIL: R0/0: wncd: Authentication failed for client (ec2e.9835.cc35) with reason (Cred Fail) on Interface capwap_90000009 AuditSessionID 320A16AC00001A8B35E04467 Username: rosario
2023/12/04 13:29:07.229914 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [17015]: (ERR): SANET_AUTHC_FAILURE - Cred Fail, username rosario, audit session id 320A16AC00001A8B35E04467
2023/12/04 13:29:07.229939 {wncd_x_R0-0}{1}: [errmsg] [17015]: (note): %SESSION_MGR-5-FAIL: R0/0: wncd: Authorization failed or unapplied for client (ec2e.9835.cc35) on Interface capwap_90000009 AuditSessionID 320A16AC00001A8B35E04467. Failure reason: Authc fail. Authc failure reason: Cred Fail.
2023/12/04 13:29:07.230915 {wncd_x_R0-0}{1}: [client-orch-sm] [17015]: (note): MAC: ec2e.9835.cc35 Client delete initiated. Reason: CO_CLIENT_DELETE_REASON_CLIENT_CREDENTIAL_FAILURE, details: , fsm-state transition 00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|01|07|13|1a|23|
2023/12/04 13:29:07.231175 {wncd_x_R0-0}{1}: [client-orch-sm] [17015]: (note): MAC: ec2e.9835.cc35 Delete mobile payload sent forbssid: 00d7.8f2f.6c2d WTP mac: 00d7.8f2f.6c20 slot id: 1
2023/12/04 13:29:07.231193 {wncd_x_R0-0}{1}: [client-orch-state] [17015]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_L2_AUTH_IN_PROGRESS -> S_CO_DELETE_IN_PROGRESS
2023/12/04 13:29:07.231321 {wncd_x_R0-0}{1}: [client-orch-sm] [17015]: (ERR): MAC: ec2e.9835.cc35 CLT populate Record: failed to populate anchor ip
2023/12/04 13:29:07.231666 {wncd_x_R0-0}{1}: [sanet-shim-translate] [17015]: (note): MAC: ec2e.9835.cc35 Session manager disconnect event called, session label: 0x23000a86
2023/12/04 13:29:07.233024 {wncd_x_R0-0}{1}: [client-orch-state] [17015]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_DELETE_IN_PROGRESS -> S_CO_DELETED
2023/12/04 13:29:07.437295 {wncd_x_R0-0}{1}: [client-orch-sm] [17015]: (note): MAC: ec2e.9835.cc35 Re-Association received. BSSID 00d7.8f2f.6c22, WLAN lab_doble_authe, Slot 0 AP 00d7.8f2f.6c20, AP_REUNIONES
2023/12/04 13:29:07.438081 {wncd_x_R0-0}{1}: [client-orch-state] [17015]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_INIT -> S_CO_ASSOCIATING
2023/12/04 13:29:07.438332 {wncd_x_R0-0}{1}: [dot11-validate] [17015]: (ERR): MAC: ec2e.9835.cc35 Failed to dot11 ie validate aironet ipaddr. Aironet ipaddr IE is not present in Assoc Request
2023/12/04 13:29:07.438379 {wncd_x_R0-0}{1}: [apmgr-db] [17015]: (ERR): Failed to get opt roam statusInvalid (null) rf common record
2023/12/04 13:29:07.438380 {wncd_x_R0-0}{1}: [dot11k] [17015]: (ERR): MAC: ec2e.9835.cc35 Rssi check failed, Unable to get the smart roam status for rf profile default_rf_5gh
2023/12/04 13:29:07.438642 {wncd_x_R0-0}{1}: [dot11] [17015]: (note): MAC: ec2e.9835.cc35 Association success. AID 6, Roaming = False, WGB = False, 11r = False, 11w = False Fast roam = False
2023/12/04 13:29:07.438872 {wncd_x_R0-0}{1}: [client-orch-state] [17015]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_ASSOCIATING -> S_CO_L2_AUTH_IN_PROGRESS
2023/12/04 13:29:07.439180 {wncd_x_R0-0}{1}: [client-auth] [17015]: (note): MAC: ec2e.9835.cc35 ADD MOBILE sent. Client state flags: 0x71 BSSID: MAC: 00d7.8f2f.6c22 capwap IFID: 0x90000009, Add mobiles sent: 1
2023/12/04 13:29:07.443490 {wncd_x_R0-0}{1}: [client-auth] [17015]: (note): MAC: ec2e.9835.cc35 L2 Authentication initiated. method DOT1X, Policy VLAN 0, AAA override = 0 , NAC = 0
2023/12/04 13:29:07.445179 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [17015]: (note): Authentication Success. Resolved Policy bitmap:11 for client ec2e.9835.cc35
2023/12/04 13:29:14.051602 {wncd_x_R0-0}{1}: [errmsg] [17015]: (note): %DOT1X-5-FAIL: R0/0: wncd: Authentication failed for client (ec2e.9835.cc35) with reason (Cred Fail) on Interface capwap_90000009 AuditSessionID 320A16AC00001A8C35E05EE4 Username: rosario
2023/12/04 13:29:14.051993 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [17015]: (ERR): SANET_AUTHC_FAILURE - Cred Fail, username rosario, audit session id 320A16AC00001A8C35E05EE4
2023/12/04 13:29:14.052023 {wncd_x_R0-0}{1}: [errmsg] [17015]: (note): %SESSION_MGR-5-FAIL: R0/0: wncd: Authorization failed or unapplied for client (ec2e.9835.cc35) on Interface capwap_90000009 AuditSessionID 320A16AC00001A8C35E05EE4. Failure reason: Authc fail. Authc failure reason: Cred Fail.
2023/12/04 13:29:14.052691 {wncd_x_R0-0}{1}: [client-orch-sm] [17015]: (note): MAC: ec2e.9835.cc35 Client delete initiated. Reason: CO_CLIENT_DELETE_REASON_CLIENT_CREDENTIAL_FAILURE, details: , fsm-state transition 00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|01|07|13|1a|23|
2023/12/04 13:29:14.053158 {wncd_x_R0-0}{1}: [client-orch-sm] [17015]: (note): MAC: ec2e.9835.cc35 Delete mobile payload sent forbssid: 00d7.8f2f.6c22 WTP mac: 00d7.8f2f.6c20 slot id: 0
2023/12/04 13:29:14.053183 {wncd_x_R0-0}{1}: [client-orch-state] [17015]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_L2_AUTH_IN_PROGRESS -> S_CO_DELETE_IN_PROGRESS
2023/12/04 13:29:14.053318 {wncd_x_R0-0}{1}: [client-orch-sm] [17015]: (ERR): MAC: ec2e.9835.cc35 CLT populate Record: failed to populate anchor ip
2023/12/04 13:29:14.053781 {wncd_x_R0-0}{1}: [sanet-shim-translate] [17015]: (note): MAC: ec2e.9835.cc35 Session manager disconnect event called, session label: 0xd9000a87
2023/12/04 13:29:14.055192 {wncd_x_R0-0}{1}: [client-orch-state] [17015]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_DELETE_IN_PROGRESS -> S_CO_DELETED
2023/12/04 13:29:21.134272 {wncd_x_R0-0}{1}: [client-orch-sm] [17015]: (note): MAC: ec2e.9835.cc35 Association received. BSSID 00d7.8f2f.6c2d, WLAN lab_doble_authe, Slot 1 AP 00d7.8f2f.6c20, AP_REUNIONES
2023/12/04 13:29:21.134588 {wncd_x_R0-0}{1}: [client-orch-state] [17015]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_INIT -> S_CO_ASSOCIATING
2023/12/04 13:29:21.134920 {wncd_x_R0-0}{1}: [dot11-validate] [17015]: (ERR): MAC: ec2e.9835.cc35 Failed to dot11 ie validate aironet ipaddr. Aironet ipaddr IE is not present in Assoc Request
2023/12/04 13:29:21.135369 {wncd_x_R0-0}{1}: [dot11] [17015]: (note): MAC: ec2e.9835.cc35 Association success. AID 5, Roaming = False, WGB = False, 11r = False, 11w = False Fast roam = False
2023/12/04 13:29:21.135582 {wncd_x_R0-0}{1}: [client-orch-state] [17015]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_ASSOCIATING -> S_CO_L2_AUTH_IN_PROGRESS
2023/12/04 13:29:21.135969 {wncd_x_R0-0}{1}: [client-auth] [17015]: (note): MAC: ec2e.9835.cc35 ADD MOBILE sent. Client state flags: 0x71 BSSID: MAC: 00d7.8f2f.6c2d capwap IFID: 0x90000009, Add mobiles sent: 1
2023/12/04 13:29:21.140043 {wncd_x_R0-0}{1}: [client-auth] [17015]: (note): MAC: ec2e.9835.cc35 L2 Authentication initiated. method DOT1X, Policy VLAN 0, AAA override = 0 , NAC = 0
2023/12/04 13:29:21.142386 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [17015]: (note): Authentication Success. Resolved Policy bitmap:11 for client ec2e.9835.cc35
2023/12/04 13:29:28.503154 {wncd_x_R0-0}{1}: [errmsg] [17015]: (note): %DOT1X-5-FAIL: R0/0: wncd: Authentication failed for client (ec2e.9835.cc35) with reason (Cred Fail) on Interface capwap_90000009 AuditSessionID 320A16AC00001A8D35E09465 Username: rosario
2023/12/04 13:29:28.503468 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [17015]: (ERR): SANET_AUTHC_FAILURE - Cred Fail, username rosario, audit session id 320A16AC00001A8D35E09465
2023/12/04 13:29:28.503497 {wncd_x_R0-0}{1}: [errmsg] [17015]: (note): %SESSION_MGR-5-FAIL: R0/0: wncd: Authorization failed or unapplied for client (ec2e.9835.cc35) on Interface capwap_90000009 AuditSessionID 320A16AC00001A8D35E09465. Failure reason: Authc fail. Authc failure reason: Cred Fail.
2023/12/04 13:29:28.505974 {wncd_x_R0-0}{1}: [client-orch-sm] [17015]: (note): MAC: ec2e.9835.cc35 Client delete initiated. Reason: CO_CLIENT_DELETE_REASON_CLIENT_CREDENTIAL_FAILURE, details: , fsm-state transition 00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|01|07|13|1a|23|
2023/12/04 13:29:28.506260 {wncd_x_R0-0}{1}: [client-orch-sm] [17015]: (note): MAC: ec2e.9835.cc35 Delete mobile payload sent forbssid: 00d7.8f2f.6c2d WTP mac: 00d7.8f2f.6c20 slot id: 1
2023/12/04 13:29:28.506292 {wncd_x_R0-0}{1}: [client-orch-state] [17015]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_L2_AUTH_IN_PROGRESS -> S_CO_DELETE_IN_PROGRESS
2023/12/04 13:29:28.506436 {wncd_x_R0-0}{1}: [client-orch-sm] [17015]: (ERR): MAC: ec2e.9835.cc35 CLT populate Record: failed to populate anchor ip
2023/12/04 13:29:28.506809 {wncd_x_R0-0}{1}: [sanet-shim-translate] [17015]: (note): MAC: ec2e.9835.cc35 Session manager disconnect event called, session label: 0x90000a88
2023/12/04 13:29:28.508729 {wncd_x_R0-0}{1}: [client-orch-state] [17015]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_DELETE_IN_PROGRESS -> S_CO_DELETED
2023/12/04 13:29:28.627648 {wncd_x_R0-0}{1}: [client-orch-sm] [17015]: (note): MAC: ec2e.9835.cc35 Re-Association received. BSSID 00d7.8f2f.6c22, WLAN lab_doble_authe, Slot 0 AP 00d7.8f2f.6c20, AP_REUNIONES
2023/12/04 13:29:28.627947 {wncd_x_R0-0}{1}: [client-orch-state] [17015]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_INIT -> S_CO_ASSOCIATING
2023/12/04 13:29:28.628278 {wncd_x_R0-0}{1}: [dot11-validate] [17015]: (ERR): MAC: ec2e.9835.cc35 Failed to dot11 ie validate aironet ipaddr. Aironet ipaddr IE is not present in Assoc Request
2023/12/04 13:29:28.628338 {wncd_x_R0-0}{1}: [apmgr-db] [17015]: (ERR): Failed to get opt roam statusInvalid (null) rf common record
2023/12/04 13:29:28.628340 {wncd_x_R0-0}{1}: [dot11k] [17015]: (ERR): MAC: ec2e.9835.cc35 Rssi check failed, Unable to get the smart roam status for rf profile default_rf_5gh
2023/12/04 13:29:28.628656 {wncd_x_R0-0}{1}: [dot11] [17015]: (note): MAC: ec2e.9835.cc35 Association success. AID 8, Roaming = False, WGB = False, 11r = False, 11w = False Fast roam = False
2023/12/04 13:29:28.628893 {wncd_x_R0-0}{1}: [client-orch-state] [17015]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_ASSOCIATING -> S_CO_L2_AUTH_IN_PROGRESS
2023/12/04 13:29:28.629273 {wncd_x_R0-0}{1}: [client-auth] [17015]: (note): MAC: ec2e.9835.cc35 ADD MOBILE sent. Client state flags: 0x71 BSSID: MAC: 00d7.8f2f.6c22 capwap IFID: 0x90000009, Add mobiles sent: 1
2023/12/04 13:29:28.653824 {wncd_x_R0-0}{1}: [client-auth] [17015]: (note): MAC: ec2e.9835.cc35 L2 Authentication initiated. method DOT1X, Policy VLAN 0, AAA override = 0 , NAC = 0
2023/12/04 13:29:28.655626 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [17015]: (note): Authentication Success. Resolved Policy bitmap:11 for client ec2e.9835.cc35
2023/12/04 13:29:33.880699 {wncd_x_R0-0}{1}: [errmsg] [17015]: (note): %DOT1X-5-FAIL: R0/0: wncd: Authentication failed for client (ec2e.9835.cc35) with reason (Cred Fail) on Interface capwap_90000009 AuditSessionID 320A16AC00001A8E35E0B1BE Username: rosario
2023/12/04 13:29:33.881008 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [17015]: (ERR): SANET_AUTHC_FAILURE - Cred Fail, username rosario, audit session id 320A16AC00001A8E35E0B1BE
2023/12/04 13:29:33.881037 {wncd_x_R0-0}{1}: [errmsg] [17015]: (note): %SESSION_MGR-5-FAIL: R0/0: wncd: Authorization failed or unapplied for client (ec2e.9835.cc35) on Interface capwap_90000009 AuditSessionID 320A16AC00001A8E35E0B1BE. Failure reason: Authc fail. Authc failure reason: Cred Fail.
2023/12/04 13:29:33.881822 {wncd_x_R0-0}{1}: [client-orch-sm] [17015]: (note): MAC: ec2e.9835.cc35 Client delete initiated. Reason: CO_CLIENT_DELETE_REASON_CLIENT_CREDENTIAL_FAILURE, details: , fsm-state transition 00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|01|07|13|1a|23|
2023/12/04 13:29:33.882080 {wncd_x_R0-0}{1}: [client-orch-sm] [17015]: (note): MAC: ec2e.9835.cc35 Delete mobile payload sent forbssid: 00d7.8f2f.6c22 WTP mac: 00d7.8f2f.6c20 slot id: 0
2023/12/04 13:29:33.882098 {wncd_x_R0-0}{1}: [client-orch-state] [17015]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_L2_AUTH_IN_PROGRESS -> S_CO_DELETE_IN_PROGRESS
2023/12/04 13:29:33.882269 {wncd_x_R0-0}{1}: [client-orch-sm] [17015]: (ERR): MAC: ec2e.9835.cc35 CLT populate Record: failed to populate anchor ip
2023/12/04 13:29:33.882802 {wncd_x_R0-0}{1}: [sanet-shim-translate] [17015]: (note): MAC: ec2e.9835.cc35 Session manager disconnect event called, session label: 0xa6000a89
2023/12/04 13:29:33.883957 {wncd_x_R0-0}{1}: [client-orch-state] [17015]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_DELETE_IN_PROGRESS -> S_CO_DELETED
- Labels:
-
Wireless LAN Controller
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2023 10:09 AM
- Update the WiFi driver(s) on the particular client to latest version , if not yet done ,
M.
-- Each morning when I wake up and look into the mirror I always say ' Why am I so brilliant ? '
When the mirror will then always repond to me with ' The only thing that exceeds your brilliance is your beauty! '
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2023 10:11 AM
I have already updated the drivers, but the issue persists.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2023 10:21 AM
- Below is the output from https://cway.cisco.com/wireless-debug-analyzer/ , for your debugging file (original post) ; Show All flag was checked :
Since EAP is involved , check radius logs too for this authentication , if used. Also use WirelessDebugAnalyzer further on too when troubleshooting the client again
M.
TimeTaskTranslated
| Connection attempt #1 | |||
| Connection attempt #2 | |||
| 2023/12/04 13:29:07.229 | errmsg | Client failed EAP authentication with following reason: Cred Fail | |
| Connection attempt #3 | |||
| 2023/12/04 13:29:14.051 | errmsg | Client failed EAP authentication with following reason: Cred Fail | |
| Connection attempt #4 | |||
| 2023/12/04 13:29:28.503 | errmsg | Client failed EAP authentication with following reason: Cred Fail | |
| Connection attempt #5 | |||
| 2023/12/04 13:29:33.880 | errmsg | Client failed EAP authentication with following reason: Cred Fail | |
-- Each morning when I wake up and look into the mirror I always say ' Why am I so brilliant ? '
When the mirror will then always repond to me with ' The only thing that exceeds your brilliance is your beauty! '
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2023 11:01 AM
The credentials are not incorrect; the same user connects from other devices. I checked the NPS server, and I don't find any records of rejections for that user
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2023 11:56 PM
>...The credentials are not incorrect; the same user connects from other devices. I checked the NPS server, and I don't find any records of rejections for that user
- Upgrade controller to 17.9.4a (recommended release) and try again
M.
-- Each morning when I wake up and look into the mirror I always say ' Why am I so brilliant ? '
When the mirror will then always repond to me with ' The only thing that exceeds your brilliance is your beauty! '
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
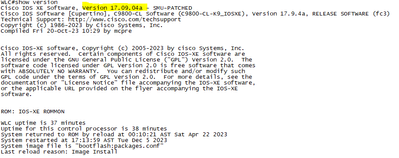
12-05-2023 01:53 PM
I upgraded to version 17.09.04a, but I'm still experiencing issues
Logging display requested on 2023/12/05 17:45:04 (AST) for Hostname: [WLC], Model: [C9800-CL-K9], Version: [17.09.04a], SN: [9T55JTSG6NS], MD_SN: [9T55JTSG6NS]
2023/12/05 17:40:40.043149685 {wncd_x_R0-0}{1}: [client-orch-sm] [19713]: (note): MAC: ec2e.9835.cc35 Association received. BSSID 00d7.8f2f.6c2d, WLAN lab_doble_authe, Slot 1 AP 00d7.8f2f.6c20, AP_REUNIONES
2023/12/05 17:40:40.043488100 {wncd_x_R0-0}{1}: [client-orch-state] [19713]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_INIT -> S_CO_ASSOCIATING
2023/12/05 17:40:40.044254651 {wncd_x_R0-0}{1}: [dot11] [19713]: (note): MAC: ec2e.9835.cc35 Association success. AID 2, Roaming = False, WGB = False, 11r = False, 11w = False Fast roam = False
2023/12/05 17:40:40.044573223 {wncd_x_R0-0}{1}: [client-orch-state] [19713]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_ASSOCIATING -> S_CO_L2_AUTH_IN_PROGRESS
2023/12/05 17:40:40.044932687 {wncd_x_R0-0}{1}: [client-auth] [19713]: (note): MAC: ec2e.9835.cc35 ADD MOBILE sent. Client state flags: 0x71 BSSID: MAC: 00d7.8f2f.6c2d capwap IFID: 0x9000000c, Add mobiles sent: 1
2023/12/05 17:40:40.048771851 {wncd_x_R0-0}{1}: [client-auth] [19713]: (note): MAC: ec2e.9835.cc35 L2 Authentication initiated. method DOT1X, Policy VLAN 0, AAA override = 0 , NAC = 0
2023/12/05 17:40:40.050732324 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [19713]: (note): Authentication Success. Resolved Policy bitmap:11 for client ec2e.9835.cc35
2023/12/05 17:40:44.725916355 {wncd_x_R0-0}{1}: [errmsg] [19713]: (note): %DOT1X-5-FAIL: R0/0: wncd: Authentication failed for client (ec2e.9835.cc35) with reason (Cred Fail) on Interface capwap_9000000c AuditSessionID 320A16AC0000002B3BED0408 Username: rosario
2023/12/05 17:40:44.726535676 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [19713]: (ERR): SANET_AUTHC_FAILURE - Cred Fail, username rosario, audit session id 320A16AC0000002B3BED0408
2023/12/05 17:40:44.726576695 {wncd_x_R0-0}{1}: [errmsg] [19713]: (note): %SESSION_MGR-5-FAIL: R0/0: wncd: Authorization failed or unapplied for client (ec2e.9835.cc35) on Interface capwap_9000000c AuditSessionID 320A16AC0000002B3BED0408. Failure reason: Authc fail. Authc failure reason: Cred Fail.
2023/12/05 17:40:44.727380005 {wncd_x_R0-0}{1}: [client-orch-sm] [19713]: (note): MAC: ec2e.9835.cc35 Client delete initiated. Reason: CO_CLIENT_DELETE_REASON_CLIENT_CREDENTIAL_FAILURE, details: , fsm-state transition 00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|01|07|15|1e|27|
2023/12/05 17:40:44.727627926 {wncd_x_R0-0}{1}: [client-orch-sm] [19713]: (note): MAC: ec2e.9835.cc35 Delete mobile payload sent for BSSID: 00d7.8f2f.6c2d WTP mac: 00d7.8f2f.6c20 slot id: 1
2023/12/05 17:40:44.727642843 {wncd_x_R0-0}{1}: [client-orch-state] [19713]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_L2_AUTH_IN_PROGRESS -> S_CO_DELETE_IN_PROGRESS
2023/12/05 17:40:44.727765743 {wncd_x_R0-0}{1}: [client-orch-sm] [19713]: (ERR): MAC: ec2e.9835.cc35 CLT populate Record: failed to populate anchor ip
2023/12/05 17:40:44.728135683 {wncd_x_R0-0}{1}: [sanet-shim-translate] [19713]: (note): MAC: ec2e.9835.cc35 Session manager disconnect event called, session label: 0xa2000021
2023/12/05 17:40:44.729689462 {wncd_x_R0-0}{1}: [client-orch-state] [19713]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_DELETE_IN_PROGRESS -> S_CO_DELETED
2023/12/05 17:42:54.135937259 {wncd_x_R0-0}{1}: [client-orch-sm] [19713]: (note): MAC: ec2e.9835.cc35 Association received. BSSID 00d7.8f2f.5b8d, WLAN lab_doble_authe, Slot 1 AP 00d7.8f2f.5b80, AP_GRADAS
2023/12/05 17:42:54.136273086 {wncd_x_R0-0}{1}: [client-orch-state] [19713]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_INIT -> S_CO_ASSOCIATING
2023/12/05 17:42:54.137006678 {wncd_x_R0-0}{1}: [dot11] [19713]: (note): MAC: ec2e.9835.cc35 Association success. AID 1, Roaming = False, WGB = False, 11r = False, 11w = False Fast roam = False
2023/12/05 17:42:54.137398721 {wncd_x_R0-0}{1}: [client-orch-state] [19713]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_ASSOCIATING -> S_CO_L2_AUTH_IN_PROGRESS
2023/12/05 17:42:54.137744099 {wncd_x_R0-0}{1}: [client-auth] [19713]: (note): MAC: ec2e.9835.cc35 ADD MOBILE sent. Client state flags: 0x71 BSSID: MAC: 00d7.8f2f.5b8d capwap IFID: 0x9000000d, Add mobiles sent: 1
2023/12/05 17:42:54.149960676 {wncd_x_R0-0}{1}: [client-auth] [19713]: (note): MAC: ec2e.9835.cc35 L2 Authentication initiated. method DOT1X, Policy VLAN 0, AAA override = 0 , NAC = 0
2023/12/05 17:42:54.151707796 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [19713]: (note): Authentication Success. Resolved Policy bitmap:11 for client ec2e.9835.cc35
2023/12/05 17:43:01.924021039 {wncd_x_R0-0}{1}: [errmsg] [19713]: (note): %DOT1X-5-FAIL: R0/0: wncd: Authentication failed for client (ec2e.9835.cc35) with reason (Cred Fail) on Interface capwap_9000000d AuditSessionID 320A16AC0000002E3BEF0FDE Username: rosario
2023/12/05 17:43:01.924272854 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [19713]: (ERR): SANET_AUTHC_FAILURE - Cred Fail, username rosario, audit session id 320A16AC0000002E3BEF0FDE
2023/12/05 17:43:01.924321685 {wncd_x_R0-0}{1}: [errmsg] [19713]: (note): %SESSION_MGR-5-FAIL: R0/0: wncd: Authorization failed or unapplied for client (ec2e.9835.cc35) on Interface capwap_9000000d AuditSessionID 320A16AC0000002E3BEF0FDE. Failure reason: Authc fail. Authc failure reason: Cred Fail.
2023/12/05 17:43:01.924805379 {wncd_x_R0-0}{1}: [client-orch-sm] [19713]: (note): MAC: ec2e.9835.cc35 Client delete initiated. Reason: CO_CLIENT_DELETE_REASON_CLIENT_CREDENTIAL_FAILURE, details: , fsm-state transition 00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|01|07|15|1e|27|
2023/12/05 17:43:01.924978784 {wncd_x_R0-0}{1}: [client-orch-sm] [19713]: (note): MAC: ec2e.9835.cc35 Delete mobile payload sent for BSSID: 00d7.8f2f.5b8d WTP mac: 00d7.8f2f.5b80 slot id: 1
2023/12/05 17:43:01.924990423 {wncd_x_R0-0}{1}: [client-orch-state] [19713]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_L2_AUTH_IN_PROGRESS -> S_CO_DELETE_IN_PROGRESS
2023/12/05 17:43:01.925123134 {wncd_x_R0-0}{1}: [client-orch-sm] [19713]: (ERR): MAC: ec2e.9835.cc35 CLT populate Record: failed to populate anchor ip
2023/12/05 17:43:01.925418396 {wncd_x_R0-0}{1}: [sanet-shim-translate] [19713]: (note): MAC: ec2e.9835.cc35 Session manager disconnect event called, session label: 0xa3000024
2023/12/05 17:43:01.926440936 {wncd_x_R0-0}{1}: [client-orch-state] [19713]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_DELETE_IN_PROGRESS -> S_CO_DELETED
2023/12/05 17:44:25.731847786 {wncd_x_R0-0}{1}: [dot11] [19713]: (info): Failed to dot11 map external to internal ie type. Unsupported IE received, skip decode . IE Type :150
2023/12/05 17:44:25.731849739 {wncd_x_R0-0}{1}: [dot11] [19713]: (info): Failed to dot11 map external to internal ie type. Unsupported IE received, skip decode . IE Type :199
2023/12/05 17:44:25.748725145 {wncd_x_R0-0}{1}: [client-orch-sm] [19713]: (note): MAC: ec2e.9835.cc35 Association received. BSSID 00d7.8f2f.6c2d, WLAN lab_doble_authe, Slot 1 AP 00d7.8f2f.6c20, AP_REUNIONES
2023/12/05 17:44:25.748822710 {wncd_x_R0-0}{1}: [client-orch-sm] [19713]: (debug): MAC: ec2e.9835.cc35 Received Dot11 association request. Processing started,SSID: auth, Policy profile: poli_doble_auth, AP Name: AP_REUNIONES, Ap Mac Address: 00d7.8f2f.6c20BSSID MAC0000.0000.0000wlan ID: 4RSSI: -57, SNR: 36
2023/12/05 17:44:25.749156167 {wncd_x_R0-0}{1}: [client-orch-state] [19713]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_INIT -> S_CO_ASSOCIATING
2023/12/05 17:44:25.749633842 {wncd_x_R0-0}{1}: [dot11-validate] [19713]: (info): MAC: ec2e.9835.cc35 Dot11 ie validate ext/supp rates. Validation Passed for Supported rates radio_type 2
2023/12/05 17:44:25.749640719 {wncd_x_R0-0}{1}: [dot11-validate] [19713]: (info): MAC: ec2e.9835.cc35 WiFi direct: Dot11 validate P2P IE. P2P IE not present.
2023/12/05 17:44:25.749876754 {wncd_x_R0-0}{1}: [dot11] [19713]: (debug): MAC: ec2e.9835.cc35 dot11 send association response. Framing association response with resp_status_code: 0
2023/12/05 17:44:25.749877465 {wncd_x_R0-0}{1}: [dot11] [19713]: (info): MAC: ec2e.9835.cc35 Dot11 capability privacy bit set TRUE
2023/12/05 17:44:25.749884299 {wncd_x_R0-0}{1}: [dot11] [19713]: (debug): MAC: ec2e.9835.cc35 Dot11 Capability info byte1 11, byte2: 11
2023/12/05 17:44:25.749960709 {wncd_x_R0-0}{1}: [dot11-frame] [19713]: (info): MAC: ec2e.9835.cc35 WiFi direct: skip build Assoc Resp with P2P IE: Wifi direct policy disabled
2023/12/05 17:44:25.750165763 {wncd_x_R0-0}{1}: [dot11] [19713]: (info): MAC: ec2e.9835.cc35 dot11 send association response. Sending assoc response of length: 280 with resp_status_code: 0, DOT11_STATUS: DOT11_STATUS_SUCCESS
2023/12/05 17:44:25.750213327 {wncd_x_R0-0}{1}: [dot11] [19713]: (note): MAC: ec2e.9835.cc35 Association success. AID 1, Roaming = False, WGB = False, 11r = False, 11w = False Fast roam = False
2023/12/05 17:44:25.750277403 {wncd_x_R0-0}{1}: [dot11k] [19713]: (info): MAC: ec2e.9835.cc35 Sending measurement request for meas_type=5 of length=149...
2023/12/05 17:44:25.750428894 {wncd_x_R0-0}{1}: [dot11] [19713]: (info): MAC: ec2e.9835.cc35 DOT11 state transition: S_DOT11_INIT -> S_DOT11_ASSOCIATED
2023/12/05 17:44:25.750550122 {wncd_x_R0-0}{1}: [client-orch-sm] [19713]: (debug): MAC: ec2e.9835.cc35 Station Dot11 association is successful.
2023/12/05 17:44:25.750613762 {wncd_x_R0-0}{1}: [client-orch-sm] [19713]: (debug): MAC: ec2e.9835.cc35 Starting L2 authentication. Bssid in state machine:00d7.8f2f.6c2d Bssid in request is:00d7.8f2f.6c2d
2023/12/05 17:44:25.750653476 {wncd_x_R0-0}{1}: [client-orch-state] [19713]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_ASSOCIATING -> S_CO_L2_AUTH_IN_PROGRESS
2023/12/05 17:44:25.750784737 {wncd_x_R0-0}{1}: [ewlc-qos-client] [19713]: (info): MAC: ec2e.9835.cc35 Client QoS add mobile cb
2023/12/05 17:44:25.751027759 {wncd_x_R0-0}{1}: [ewlc-qos-client] [19713]: (info): MAC: ec2e.9835.cc35 Failed to install QoS client policy in process add mobile callback: AP Mac: 00:D7:8F:2F:6C:20 slotId=1, wlan_id=4
2023/12/05 17:44:25.751111136 {wncd_x_R0-0}{1}: [client-auth] [19713]: (note): MAC: ec2e.9835.cc35 ADD MOBILE sent. Client state flags: 0x71 BSSID: MAC: 00d7.8f2f.6c2d capwap IFID: 0x9000000c, Add mobiles sent: 1
2023/12/05 17:44:25.751146984 {wncd_x_R0-0}{1}: [client-auth] [19713]: (info): MAC: ec2e.9835.cc35 Client auth-interface state transition: S_AUTHIF_INIT -> S_AUTHIF_ADD_MOBILE_ACK_WAIT_DOT1X
2023/12/05 17:44:25.762409328 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Received EAPOL packet - Version : 1,EAPOL Type : START, Payload Length : 0
2023/12/05 17:44:25.762479178 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [0000.0000.0000:capwap_9000000c] Dequeued pkt: CODE = 0,TYPE = 0,LEN = 0
2023/12/05 17:44:25.762489334 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [0000.0000.0000:capwap_9000000c] Received pkt saddr = ec2e.9835.cc35 , daddr = 00d7.8f2f.6c22, pae-ether-type = 0x888E
2023/12/05 17:44:25.762495611 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [0000.0000.0000:capwap_9000000c] Couldn't find the supplicant in the list
2023/12/05 17:44:25.762557366 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] New client detected, sending session start event for ec2e.9835.cc35
2023/12/05 17:44:25.762601446 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Session Start event called from dot1x, vlan: 0
2023/12/05 17:44:25.779205095 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Session Start event called from SANET-SHIM, vlan: 0
2023/12/05 17:44:25.779228074 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Wireless session sequence, create context with method Dot1X
2023/12/05 17:44:25.779236166 {wncd_x_R0-0}{1}: [auth-mgr-feat_wireless] [19713]: (info): Wireless dot1x configs:
EAPID req max retries = 3 EAP req max retries = 3 EAPID req timeout = 40 Supp Timeout = 40
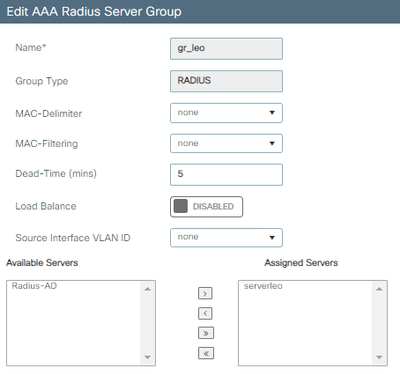
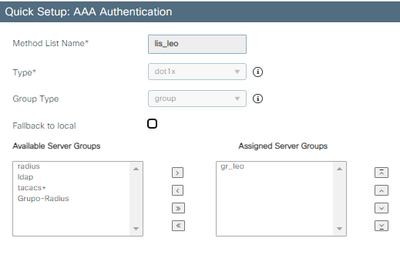
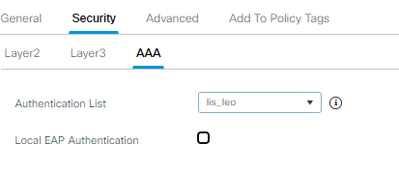
2023/12/05 17:44:25.779273855 {wncd_x_R0-0}{1}: [auth-mgr-feat_wireless] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] - authc_list: lis_leo
2023/12/05 17:44:25.779276063 {wncd_x_R0-0}{1}: [auth-mgr-feat_wireless] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] - authz_list: Not present under wlan configuration
2023/12/05 17:44:25.779348929 {wncd_x_R0-0}{1}: [client-auth] [19713]: (note): MAC: ec2e.9835.cc35 L2 Authentication initiated. method DOT1X, Policy VLAN 0, AAA override = 0 , NAC = 0
2023/12/05 17:44:25.779355696 {wncd_x_R0-0}{1}: [client-auth] [19713]: (info): MAC: ec2e.9835.cc35 Client auth-interface state transition: S_AUTHIF_ADD_MOBILE_ACK_WAIT_DOT1X -> S_AUTHIF_AWAIT_DOT1XAUTH_START_RESP
2023/12/05 17:44:25.779585100 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:unknown] auth mgr attr add/change notification is received for attr iif-id(952)
2023/12/05 17:44:25.779694877 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] auth mgr attr add/change notification is received for attr swbidb(1263)
2023/12/05 17:44:25.779737924 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] auth mgr attr add/change notification is received for attr aaa-unique-id(220)
2023/12/05 17:44:25.779777653 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] auth mgr attr add/change notification is received for attr iif-id(952)
2023/12/05 17:44:25.779816121 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Retrieved Client IIF ID 0xd20007ed
2023/12/05 17:44:25.779900989 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] auth mgr attr add/change notification is received for attr audit-session-id(819)
2023/12/05 17:44:25.779919524 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Allocated audit session id 320A16AC0000002F3BF075CB
2023/12/05 17:44:25.780565308 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Applying policy for WlanId: 4, bssid : 00d7.8f2f.6c2d, slotid: 1 bssid hdl : 12364632846386595091
2023/12/05 17:44:25.780571235 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Wlan vlan-id from bssid hdl 0
2023/12/05 17:44:25.780611734 {wncd_x_R0-0}{1}: [svm] [19713]: (info): SVM_INFO: Applying Svc Templ wlan_svc_poli_doble_auth_local (ML:NONE)
2023/12/05 17:44:25.780993824 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] auth mgr attr add/change notification is received for attr vlan-id(965)
2023/12/05 17:44:25.781025318 {wncd_x_R0-0}{1}: [epm] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Vlan tag name is dima_203, pref is 1048575 vlan num is 203
2023/12/05 17:44:25.781120921 {wncd_x_R0-0}{1}: [epm] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Feature (EPM Vlan PLUG-IN) has been started (status Success)
2023/12/05 17:44:25.781162428 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] SM Reauth Plugin: Received valid timeout = 1800, effective timeout = 1800
2023/12/05 17:44:25.781224165 {wncd_x_R0-0}{1}: [epm] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Feature (SM Reauth PLUG-IN) has been started (status Success)
2023/12/05 17:44:25.781318040 {wncd_x_R0-0}{1}: [svm] [19713]: (info): SVM_INFO: Response of epm is SYNC with return code Success
2023/12/05 17:44:25.781427257 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Raising ext evt Template Activated (9) on this session, client (unknown) (0)
2023/12/05 17:44:25.781741522 {wncd_x_R0-0}{1}: [llbridge-main] [19713]: (debug): MAC: ec2e.9835.cc35 Link-local bridging not enabled for this client, not checking VLAN validity
2023/12/05 17:44:25.781860487 {wncd_x_R0-0}{1}: [svm] [19713]: (info): SVM_INFO: SVM Apply user profile
2023/12/05 17:44:25.782070695 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Initialising auth state
2023/12/05 17:44:25.782080083 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Setting Auth state to disconnected
2023/12/05 17:44:25.782086124 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Entering restart state
2023/12/05 17:44:25.782092526 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Override cfg - MAC ec2e.9835.cc35 - profile (none)
2023/12/05 17:44:25.782095267 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Override cfg - SuppTimeout 40s, ReAuthMax 3, MaxReq 3, TxPeriod 40s
2023/12/05 17:44:25.782100564 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Sending create new context event to EAP for 0x00000019 (ec2e.9835.cc35)
2023/12/05 17:44:25.782208025 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Entering init state
2023/12/05 17:44:25.782215642 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Entering idle state
2023/12/05 17:44:25.782239626 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Dot1x authentication started for (ec2e.9835.cc35)
2023/12/05 17:44:25.782250992 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Context changing state from 'Idle' to 'Running'
2023/12/05 17:44:25.782257389 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Method dot1x changing state from 'Not run' to 'Running'
2023/12/05 17:44:25.782295265 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] SM will not send event Template Activated to PRE for 0x38000025
2023/12/05 17:44:25.782387892 {wncd_x_R0-0}{1}: [client-auth] [19713]: (info): MAC: ec2e.9835.cc35 Client auth-interface state transition: S_AUTHIF_AWAIT_DOT1XAUTH_START_RESP -> S_AUTHIF_DOT1XAUTH_PENDING
2023/12/05 17:44:25.782396627 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [19713]: (note): Authentication Success. Resolved Policy bitmap:11 for client ec2e.9835.cc35
2023/12/05 17:44:25.782402699 {wncd_x_R0-0}{1}: [client-auth] [19713]: (info): MAC: ec2e.9835.cc35 Client auth-interface state transition: S_AUTHIF_DOT1XAUTH_PENDING -> S_AUTHIF_DOT1XAUTH_PENDING
2023/12/05 17:44:25.782503360 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Posting !EAP_RESTART on Client
2023/12/05 17:44:25.782509697 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Enter connecting state
2023/12/05 17:44:25.782515901 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Restart connecting
2023/12/05 17:44:25.782523799 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Posting RX_REQ on Client
2023/12/05 17:44:25.782529060 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Authenticating state entered
2023/12/05 17:44:25.782548948 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Connecting authenticating action
2023/12/05 17:44:25.782582225 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Entering request state
2023/12/05 17:44:25.782615310 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [0000.0000.0000:capwap_9000000c] Setting EAPOL eth-type to 0x888e, destination mac to ec2e.9835.cc35
2023/12/05 17:44:25.782618053 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [0000.0000.0000:capwap_9000000c] Sending out EAPOL packet
2023/12/05 17:44:25.782826623 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Sent EAPOL packet - Version : 3,EAPOL Type : EAP, Payload Length : 5, EAP-Type = Identity
2023/12/05 17:44:25.782830877 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] EAP Packet - REQUEST, ID : 0x1
2023/12/05 17:44:25.782846604 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [0000.0000.0000:unknown] Pkt body: 01 01 00 05 01
2023/12/05 17:44:25.782853806 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] EAPOL packet sent to client
2023/12/05 17:44:34.357672875 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Received EAPOL packet - Version : 1,EAPOL Type : EAP, Payload Length : 12, EAP-Type = Identity
2023/12/05 17:44:34.357676834 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] EAP Packet - RESPONSE, ID : 0x1
2023/12/05 17:44:34.357683541 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [0000.0000.0000:unknown] Pkt body: 02 01 00 0c 01 72 6f 73 61 72 69 6f
2023/12/05 17:44:34.357689237 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [0000.0000.0000:capwap_9000000c] Queuing an EAPOL pkt on Authenticator Q
2023/12/05 17:44:34.357722477 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [0000.0000.0000:capwap_9000000c] Dequeued pkt: CODE = 2,TYPE = 1,LEN = 12
2023/12/05 17:44:34.357770673 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [0000.0000.0000:capwap_9000000c] Received pkt saddr = ec2e.9835.cc35 , daddr = 00d7.8f2f.6c22, pae-ether-type = 0x888E
2023/12/05 17:44:34.358578579 {wncd_x_R0-0}{1}: [caaa-authen] [19713]: (info): [CAAA:AUTHEN:38000025] NULL ATTR LIST
2023/12/05 17:44:34.358998055 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Raised identity update event for eap method Identity
2023/12/05 17:44:34.359080932 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Entering idle state
2023/12/05 17:44:34.359094791 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Posting AUTH_FAIL on Client
2023/12/05 17:44:34.359260503 {wncd_x_R0-0}{1}: [errmsg] [19713]: (note): %DOT1X-5-FAIL: R0/0: wncd: Authentication failed for client (ec2e.9835.cc35) with reason (Cred Fail) on Interface capwap_9000000c AuditSessionID 320A16AC0000002F3BF075CB Username: rosario
2023/12/05 17:44:34.359278994 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Authc failure from Dot1X, Auth event fail
2023/12/05 17:44:34.359295874 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Method dot1x changing state from 'Running' to 'Authc Failed'
2023/12/05 17:44:34.359336583 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Raised event RX_METHOD_AUTHC_FAIL (6)
2023/12/05 17:44:34.359355338 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Raised event REMOVE_USER_PROFILE (15)
2023/12/05 17:44:34.359417229 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Context changing state from 'Running' to 'Authc Failed'
2023/12/05 17:44:34.359532094 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] auth mgr attr add/change notification is received for attr username(450)
2023/12/05 17:44:34.359587328 {wncd_x_R0-0}{1}: [auth-mgr-feat_acct] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] SM Notified attribute Add/Update username rosario
2023/12/05 17:44:34.359597198 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Received User-Name rosario for client ec2e.9835.cc35
2023/12/05 17:44:34.359658661 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] AUTHC_FAIL - unauthorize by default
2023/12/05 17:44:34.359666573 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Signalling Authc fail for client ec2e.9835.cc35
2023/12/05 17:44:34.359733047 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [19713]: (ERR): SANET_AUTHC_FAILURE - Cred Fail, username rosario, audit session id 320A16AC0000002F3BF075CB
2023/12/05 17:44:34.359761310 {wncd_x_R0-0}{1}: [errmsg] [19713]: (note): %SESSION_MGR-5-FAIL: R0/0: wncd: Authorization failed or unapplied for client (ec2e.9835.cc35) on Interface capwap_9000000c AuditSessionID 320A16AC0000002F3BF075CB. Failure reason: Authc fail. Authc failure reason: Cred Fail.
2023/12/05 17:44:34.359771063 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Authz failed/unapplied), method: dot1x. Signal switch PI.
2023/12/05 17:44:34.359824569 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] auth mgr attr add/change notification is received for attr method(757)
2023/12/05 17:44:34.359857874 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Context changing state from 'Authc Failed' to 'Authz Failed'
2023/12/05 17:44:34.360043942 {wncd_x_R0-0}{1}: [llbridge-main] [19713]: (debug): MAC: ec2e.9835.cc35 Link-local bridging not enabled for this client, not checking VLAN validity
2023/12/05 17:44:34.360188662 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : username 0 "rosario"
2023/12/05 17:44:34.360194761 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : service-type 0 2 [Framed]
2023/12/05 17:44:34.360197594 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : Framed-MTU 0 1485 (0x5cd)
2023/12/05 17:44:34.360199605 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : EAP-Message 0 <hidden>
2023/12/05 17:44:34.360201458 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : Message-Authenticator 0 <hidden>
2023/12/05 17:44:34.360203521 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : EAP-session-id 0 ""
2023/12/05 17:44:34.360205884 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : audit-session-id 0 "320A16AC0000002F3BF075CB"
2023/12/05 17:44:34.360208467 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : hwidb 0 2415919116 (0x9000000c)
2023/12/05 17:44:34.360211008 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : method 0 0 [dot1x]
2023/12/05 17:44:34.360213203 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : aaa-authen-type 0 8 (0x8)
2023/12/05 17:44:34.360215457 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : aaa-authen-service 0 19 (0x13)
2023/12/05 17:44:34.360219723 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : clid-mac-addr 0 ec 2e 98 35 cc 35
2023/12/05 17:44:34.360222351 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : target-scope 0 0 [client]
2023/12/05 17:44:34.360224565 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : aaa-unique-id 0 47 (0x2f)
2023/12/05 17:44:34.360226947 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : client-iif-id 0 3523217389 (0xd20007ed)
2023/12/05 17:44:34.360229198 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : vlan-id 0 203 (0xcb)
2023/12/05 17:44:34.360231029 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : session-linksec-secured 0 False
2023/12/05 17:44:34.360250054 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : nas-ip-address 0 0x0
2023/12/05 17:44:34.360252527 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : nas-ipv6-Address 0 ""
2023/12/05 17:44:34.360254598 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : interface 0 ""
2023/12/05 17:44:34.360257792 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : port-type 0 19 [802.11 wireless]
2023/12/05 17:44:34.360260042 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : nas-port 0 21012 (0x5214)
2023/12/05 17:44:34.360262133 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : cisco-wlan-ssid 0 "auth"
2023/12/05 17:44:34.360264226 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : wlan-profile-name 0 "lab_doble_authe"
2023/12/05 17:44:34.360266329 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : dnis 0 "00-d7-8f-2f-6c-20:auth"
2023/12/05 17:44:34.360268440 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : formatted-clid 0 "ec-2e-98-35-cc-35"
2023/12/05 17:44:34.360270703 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : bsn-wlan-id 0 4 (0x4)
2023/12/05 17:44:34.360272813 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : nas-identifier-wireless 0 "WLC"
2023/12/05 17:44:34.360275041 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : wlan-group-cipher 0 ""
2023/12/05 17:44:34.360276892 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : wlan-pairwise-cipher 0 ""
2023/12/05 17:44:34.360278733 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : wlan-akm-suite 0 ""
2023/12/05 17:44:34.360280841 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : dnis 0 "00-D7-8F-2F-6C-20"
2023/12/05 17:44:34.360282816 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : formatted-clid 0 "EC-2E-98-35-CC-35"
2023/12/05 17:44:34.360284817 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : audit-session-id 0 "320A16AC0000002F3BF075CB"
2023/12/05 17:44:34.360288508 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : clid-mac-addr 0 ec 2e 98 35 cc 35
2023/12/05 17:44:34.360290779 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : intf-id 0 2415919116 (0x9000000c)
2023/12/05 17:44:34.360325469 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Posting_AUTHZ_FAIL on Client
2023/12/05 17:44:34.360390447 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [0000.0000.0000:capwap_9000000c] Setting EAPOL eth-type to 0x888e, destination mac to ec2e.9835.cc35
2023/12/05 17:44:34.360392858 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [0000.0000.0000:capwap_9000000c] Sending out EAPOL packet
2023/12/05 17:44:34.360567161 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Sent EAPOL packet - Version : 3,EAPOL Type : EAP, Payload Length : 4, EAP-Type = 0
2023/12/05 17:44:34.360570874 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] EAP Packet - FAILURE, ID : 0x1
2023/12/05 17:44:34.360573665 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [0000.0000.0000:unknown] Pkt body: 04 01 00 04
2023/12/05 17:44:34.360579842 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] EAPOL packet sent to client
2023/12/05 17:44:34.360802306 {wncd_x_R0-0}{1}: [client-auth] [19713]: (info): MAC: ec2e.9835.cc35 Client auth-interface state transition: S_AUTHIF_DOT1XAUTH_PENDING -> S_WAIT_FOR_CO_DELETE
2023/12/05 17:44:34.360860141 {wncd_x_R0-0}{1}: [client-orch-sm] [19713]: (info): MAC: ec2e.9835.cc35 Deleting the client, reason: 93, CO_CLIENT_DELETE_REASON_CLIENT_CREDENTIAL_FAILURE, Client state S_CO_L2_AUTH_IN_PROGRESS
2023/12/05 17:44:34.360905526 {wncd_x_R0-0}{1}: [client-orch-sm] [19713]: (note): MAC: ec2e.9835.cc35 Client delete initiated. Reason: CO_CLIENT_DELETE_REASON_CLIENT_CREDENTIAL_FAILURE, details: , fsm-state transition 00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|01|07|15|1e|27|
2023/12/05 17:44:34.361242641 {wncd_x_R0-0}{1}: [client-orch-sm] [19713]: (note): MAC: ec2e.9835.cc35 Delete mobile payload sent for BSSID: 00d7.8f2f.6c2d WTP mac: 00d7.8f2f.6c20 slot id: 1
2023/12/05 17:44:34.361260239 {wncd_x_R0-0}{1}: [client-orch-state] [19713]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_L2_AUTH_IN_PROGRESS -> S_CO_DELETE_IN_PROGRESS
2023/12/05 17:44:34.361433914 {wncd_x_R0-0}{1}: [client-orch-sm] [19713]: (ERR): MAC: ec2e.9835.cc35 CLT populate Record: failed to populate anchor ip
2023/12/05 17:44:34.361575179 {wncd_x_R0-0}{1}: [ewlc-qos-voice] [19713]: (info): MAC: ec2e.9835.cc35 Successfully freed the bw for sip client
2023/12/05 17:44:34.361676121 {wncd_x_R0-0}{1}: [multicast-main] [19713]: (info): MAC: ec2e.9835.cc35 No Flex/Fabric main record exists for client
2023/12/05 17:44:34.361776555 {wncd_x_R0-0}{1}: [client-iplearn] [19713]: (info): MAC: ec2e.9835.cc35 IP-learn state transition: S_IPLEARN_INIT -> S_IPLEARN_DELETE_IN_PROGRESS
2023/12/05 17:44:34.361840148 {wncd_x_R0-0}{1}: [mm-transition] [19713]: (info): MAC: ec2e.9835.cc35 MMIF FSM transition: S_MA_INIT -> S_MA_LOCAL_DELETE_PROCESSED_TR on E_MA_CO_DELETE_RCVD
2023/12/05 17:44:34.361956557 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Raised event DELETE (19)
2023/12/05 17:44:34.361962946 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000c] Disconnect request from SANET-SHIM (15) for ec2e.9835.cc35 / 0x38000025 - term: none, abort: Unknown, disc: (default)
2023/12/05 17:44:34.361964652 {wncd_x_R0-0}{1}: [sanet-shim-translate] [19713]: (note): MAC: ec2e.9835.cc35 Session manager disconnect event called, session label: 0x38000025
2023/12/05 17:44:34.361991820 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): [ Applied attribute :bsn-vlan-interface-name 0 "dima_203" ]
2023/12/05 17:44:34.361994891 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): [ Applied attribute : timeout 0 1800 (0x708) ]
2023/12/05 17:44:34.362005836 {wncd_x_R0-0}{1}: [client-auth] [19713]: (info): MAC: ec2e.9835.cc35 Client auth-interface state transition: S_WAIT_FOR_CO_DELETE -> S_SANET_DELETE_IN_PROGRESS
2023/12/05 17:44:34.362053825 {wncd_x_R0-0}{1}: [dot11] [19713]: (info): MAC: ec2e.9835.cc35 Total length of Deauth/Disassoc: 2
2023/12/05 17:44:34.362197819 {wncd_x_R0-0}{1}: [dot11] [19713]: (info): MAC: ec2e.9835.cc35 Sent disassoc to client, disassoc reason: 23, CLIENT_DEAUTH_REASON_8021X_AUTH_FAILED delete reason: 93, CO_CLIENT_DELETE_REASON_CLIENT_CREDENTIAL_FAILURE.
2023/12/05 17:44:34.362335429 {wncd_x_R0-0}{1}: [dot11] [19713]: (info): MAC: ec2e.9835.cc35 Total length of Deauth/Disassoc: 2
2023/12/05 17:44:34.362469142 {wncd_x_R0-0}{1}: [dot11] [19713]: (info): MAC: ec2e.9835.cc35 Sent deauth to client, deauth reason: 23, CLIENT_DEAUTH_REASON_8021X_AUTH_FAILED delete reason: 93, CO_CLIENT_DELETE_REASON_CLIENT_CREDENTIAL_FAILURE.
2023/12/05 17:44:34.362659030 {wncd_x_R0-0}{1}: [dot11] [19713]: (info): MAC: ec2e.9835.cc35 DOT11 state transition: S_DOT11_ASSOCIATED -> S_DOT11_DELETED
2023/12/05 17:44:34.363538301 {wncd_x_R0-0}{1}: [caaa-acct] [19713]: (info): [CAAA:ACCT] Not a webauth call
2023/12/05 17:44:34.364261495 {wncd_x_R0-0}{1}: [client-auth] [19713]: (info): MAC: ec2e.9835.cc35 Client auth-interface state transition: S_SANET_DELETE_IN_PROGRESS -> S_AUTHIF_DELETED
2023/12/05 17:44:34.364449179 {wncd_x_R0-0}{1}: [client-orch-state] [19713]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_DELETE_IN_PROGRESS -> S_CO_DELETED
2023/12/05 17:44:45.035122023 {wncd_x_R0-0}{1}: [dot11] [19713]: (info): Failed to dot11 map external to internal ie type. Unsupported IE received, skip decode . IE Type :150
2023/12/05 17:44:45.035124074 {wncd_x_R0-0}{1}: [dot11] [19713]: (info): Failed to dot11 map external to internal ie type. Unsupported IE received, skip decode . IE Type :199
2023/12/05 17:44:45.035519040 {wncd_x_R0-0}{1}: [client-orch-sm] [19713]: (note): MAC: ec2e.9835.cc35 Association received. BSSID 00d7.8f2f.5b8d, WLAN lab_doble_authe, Slot 1 AP 00d7.8f2f.5b80, AP_GRADAS
2023/12/05 17:44:45.035630363 {wncd_x_R0-0}{1}: [client-orch-sm] [19713]: (debug): MAC: ec2e.9835.cc35 Received Dot11 association request. Processing started,SSID: auth, Policy profile: poli_doble_auth, AP Name: AP_GRADAS, Ap Mac Address: 00d7.8f2f.5b80BSSID MAC0000.0000.0000wlan ID: 4RSSI: -61, SNR: 32
2023/12/05 17:44:45.035878289 {wncd_x_R0-0}{1}: [client-orch-state] [19713]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_INIT -> S_CO_ASSOCIATING
2023/12/05 17:44:45.036273979 {wncd_x_R0-0}{1}: [dot11-validate] [19713]: (info): MAC: ec2e.9835.cc35 Dot11 ie validate ext/supp rates. Validation Passed for Supported rates radio_type 2
2023/12/05 17:44:45.036280885 {wncd_x_R0-0}{1}: [dot11-validate] [19713]: (info): MAC: ec2e.9835.cc35 WiFi direct: Dot11 validate P2P IE. P2P IE not present.
2023/12/05 17:44:45.036541801 {wncd_x_R0-0}{1}: [dot11] [19713]: (debug): MAC: ec2e.9835.cc35 dot11 send association response. Framing association response with resp_status_code: 0
2023/12/05 17:44:45.036542493 {wncd_x_R0-0}{1}: [dot11] [19713]: (info): MAC: ec2e.9835.cc35 Dot11 capability privacy bit set TRUE
2023/12/05 17:44:45.036549028 {wncd_x_R0-0}{1}: [dot11] [19713]: (debug): MAC: ec2e.9835.cc35 Dot11 Capability info byte1 11, byte2: 11
2023/12/05 17:44:45.036601838 {wncd_x_R0-0}{1}: [dot11-frame] [19713]: (info): MAC: ec2e.9835.cc35 WiFi direct: skip build Assoc Resp with P2P IE: Wifi direct policy disabled
2023/12/05 17:44:45.036808930 {wncd_x_R0-0}{1}: [dot11] [19713]: (info): MAC: ec2e.9835.cc35 dot11 send association response. Sending assoc response of length: 280 with resp_status_code: 0, DOT11_STATUS: DOT11_STATUS_SUCCESS
2023/12/05 17:44:45.036846039 {wncd_x_R0-0}{1}: [dot11] [19713]: (note): MAC: ec2e.9835.cc35 Association success. AID 1, Roaming = False, WGB = False, 11r = False, 11w = False Fast roam = False
2023/12/05 17:44:45.036914146 {wncd_x_R0-0}{1}: [dot11k] [19713]: (info): MAC: ec2e.9835.cc35 Sending measurement request for meas_type=5 of length=149...
2023/12/05 17:44:45.037081234 {wncd_x_R0-0}{1}: [dot11] [19713]: (info): MAC: ec2e.9835.cc35 DOT11 state transition: S_DOT11_INIT -> S_DOT11_ASSOCIATED
2023/12/05 17:44:45.037213345 {wncd_x_R0-0}{1}: [client-orch-sm] [19713]: (debug): MAC: ec2e.9835.cc35 Station Dot11 association is successful.
2023/12/05 17:44:45.037298099 {wncd_x_R0-0}{1}: [client-orch-sm] [19713]: (debug): MAC: ec2e.9835.cc35 Starting L2 authentication. Bssid in state machine:00d7.8f2f.5b8d Bssid in request is:00d7.8f2f.5b8d
2023/12/05 17:44:45.037339404 {wncd_x_R0-0}{1}: [client-orch-state] [19713]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_ASSOCIATING -> S_CO_L2_AUTH_IN_PROGRESS
2023/12/05 17:44:45.037451789 {wncd_x_R0-0}{1}: [ewlc-qos-client] [19713]: (info): MAC: ec2e.9835.cc35 Client QoS add mobile cb
2023/12/05 17:44:45.037664802 {wncd_x_R0-0}{1}: [ewlc-qos-client] [19713]: (info): MAC: ec2e.9835.cc35 Failed to install QoS client policy in process add mobile callback: AP Mac: 00:D7:8F:2F:5B:80 slotId=1, wlan_id=4
2023/12/05 17:44:45.037727130 {wncd_x_R0-0}{1}: [client-auth] [19713]: (note): MAC: ec2e.9835.cc35 ADD MOBILE sent. Client state flags: 0x71 BSSID: MAC: 00d7.8f2f.5b8d capwap IFID: 0x9000000d, Add mobiles sent: 1
2023/12/05 17:44:45.037746881 {wncd_x_R0-0}{1}: [client-auth] [19713]: (info): MAC: ec2e.9835.cc35 Client auth-interface state transition: S_AUTHIF_INIT -> S_AUTHIF_ADD_MOBILE_ACK_WAIT_DOT1X
2023/12/05 17:44:45.041244624 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Session Start event called from SANET-SHIM, vlan: 0
2023/12/05 17:44:45.041284965 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Wireless session sequence, create context with method Dot1X
2023/12/05 17:44:45.041292373 {wncd_x_R0-0}{1}: [auth-mgr-feat_wireless] [19713]: (info): Wireless dot1x configs:
EAPID req max retries = 3 EAP req max retries = 3 EAPID req timeout = 40 Supp Timeout = 40
2023/12/05 17:44:45.041330031 {wncd_x_R0-0}{1}: [auth-mgr-feat_wireless] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] - authc_list: lis_leo
2023/12/05 17:44:45.041332279 {wncd_x_R0-0}{1}: [auth-mgr-feat_wireless] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] - authz_list: Not present under wlan configuration
2023/12/05 17:44:45.041385947 {wncd_x_R0-0}{1}: [client-auth] [19713]: (note): MAC: ec2e.9835.cc35 L2 Authentication initiated. method DOT1X, Policy VLAN 0, AAA override = 0 , NAC = 0
2023/12/05 17:44:45.041390944 {wncd_x_R0-0}{1}: [client-auth] [19713]: (info): MAC: ec2e.9835.cc35 Client auth-interface state transition: S_AUTHIF_ADD_MOBILE_ACK_WAIT_DOT1X -> S_AUTHIF_AWAIT_DOT1XAUTH_START_RESP
2023/12/05 17:44:45.041593109 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:unknown] auth mgr attr add/change notification is received for attr iif-id(952)
2023/12/05 17:44:45.041667378 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] auth mgr attr add/change notification is received for attr swbidb(1263)
2023/12/05 17:44:45.041728196 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] auth mgr attr add/change notification is received for attr aaa-unique-id(220)
2023/12/05 17:44:45.041776647 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] auth mgr attr add/change notification is received for attr iif-id(952)
2023/12/05 17:44:45.041806116 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Retrieved Client IIF ID 0x79000803
2023/12/05 17:44:45.041906652 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] auth mgr attr add/change notification is received for attr audit-session-id(819)
2023/12/05 17:44:45.041936056 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Allocated audit session id 320A16AC000000303BF0C109
2023/12/05 17:44:45.042697493 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Applying policy for WlanId: 4, bssid : 00d7.8f2f.5b8d, slotid: 1 bssid hdl : 12364632849758815192
2023/12/05 17:44:45.042705845 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Wlan vlan-id from bssid hdl 0
2023/12/05 17:44:45.042757123 {wncd_x_R0-0}{1}: [svm] [19713]: (info): SVM_INFO: Applying Svc Templ wlan_svc_poli_doble_auth_local (ML:NONE)
2023/12/05 17:44:45.043216648 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] auth mgr attr add/change notification is received for attr vlan-id(965)
2023/12/05 17:44:45.043247062 {wncd_x_R0-0}{1}: [epm] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Vlan tag name is dima_203, pref is 1048575 vlan num is 203
2023/12/05 17:44:45.043360210 {wncd_x_R0-0}{1}: [epm] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Feature (EPM Vlan PLUG-IN) has been started (status Success)
2023/12/05 17:44:45.043382591 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] SM Reauth Plugin: Received valid timeout = 1800, effective timeout = 1800
2023/12/05 17:44:45.043415298 {wncd_x_R0-0}{1}: [epm] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Feature (SM Reauth PLUG-IN) has been started (status Success)
2023/12/05 17:44:45.043506314 {wncd_x_R0-0}{1}: [svm] [19713]: (info): SVM_INFO: Response of epm is SYNC with return code Success
2023/12/05 17:44:45.043597461 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Raising ext evt Template Activated (9) on this session, client (unknown) (0)
2023/12/05 17:44:45.043846340 {wncd_x_R0-0}{1}: [llbridge-main] [19713]: (debug): MAC: ec2e.9835.cc35 Link-local bridging not enabled for this client, not checking VLAN validity
2023/12/05 17:44:45.043924430 {wncd_x_R0-0}{1}: [svm] [19713]: (info): SVM_INFO: SVM Apply user profile
2023/12/05 17:44:45.044120662 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Initialising auth state
2023/12/05 17:44:45.044128754 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Setting Auth state to disconnected
2023/12/05 17:44:45.044134626 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Entering restart state
2023/12/05 17:44:45.044140893 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Override cfg - MAC ec2e.9835.cc35 - profile (none)
2023/12/05 17:44:45.044143661 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Override cfg - SuppTimeout 40s, ReAuthMax 3, MaxReq 3, TxPeriod 40s
2023/12/05 17:44:45.044148695 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Sending create new context event to EAP for 0x6600001A (ec2e.9835.cc35)
2023/12/05 17:44:45.044290076 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Entering init state
2023/12/05 17:44:45.044302519 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Entering idle state
2023/12/05 17:44:45.044313947 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Dot1x authentication started for (ec2e.9835.cc35)
2023/12/05 17:44:45.044329719 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Context changing state from 'Idle' to 'Running'
2023/12/05 17:44:45.044339762 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Method dot1x changing state from 'Not run' to 'Running'
2023/12/05 17:44:45.044391055 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] SM will not send event Template Activated to PRE for 0xB8000026
2023/12/05 17:44:45.044507398 {wncd_x_R0-0}{1}: [client-auth] [19713]: (info): MAC: ec2e.9835.cc35 Client auth-interface state transition: S_AUTHIF_AWAIT_DOT1XAUTH_START_RESP -> S_AUTHIF_DOT1XAUTH_PENDING
2023/12/05 17:44:45.044512690 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [19713]: (note): Authentication Success. Resolved Policy bitmap:11 for client ec2e.9835.cc35
2023/12/05 17:44:45.044518849 {wncd_x_R0-0}{1}: [client-auth] [19713]: (info): MAC: ec2e.9835.cc35 Client auth-interface state transition: S_AUTHIF_DOT1XAUTH_PENDING -> S_AUTHIF_DOT1XAUTH_PENDING
2023/12/05 17:44:45.044622677 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Posting !EAP_RESTART on Client
2023/12/05 17:44:45.044628801 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Enter connecting state
2023/12/05 17:44:45.044650222 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Restart connecting
2023/12/05 17:44:45.044662568 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Posting RX_REQ on Client
2023/12/05 17:44:45.044668440 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Authenticating state entered
2023/12/05 17:44:45.044688996 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Connecting authenticating action
2023/12/05 17:44:45.044705240 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Entering request state
2023/12/05 17:44:45.044736314 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [0000.0000.0000:capwap_9000000d] Setting EAPOL eth-type to 0x888e, destination mac to ec2e.9835.cc35
2023/12/05 17:44:45.044739280 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [0000.0000.0000:capwap_9000000d] Sending out EAPOL packet
2023/12/05 17:44:45.045001151 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Sent EAPOL packet - Version : 3,EAPOL Type : EAP, Payload Length : 5, EAP-Type = Identity
2023/12/05 17:44:45.045005272 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] EAP Packet - REQUEST, ID : 0x1
2023/12/05 17:44:45.045009066 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [0000.0000.0000:unknown] Pkt body: 01 01 00 05 01
2023/12/05 17:44:45.045015415 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] EAPOL packet sent to client
2023/12/05 17:44:45.045919019 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Received EAPOL packet - Version : 1,EAPOL Type : START, Payload Length : 0
2023/12/05 17:44:45.045948359 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [0000.0000.0000:capwap_9000000d] Dequeued pkt: CODE = 0,TYPE = 0,LEN = 0
2023/12/05 17:44:45.045955839 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [0000.0000.0000:capwap_9000000d] Received pkt saddr = ec2e.9835.cc35 , daddr = 00d7.8f2f.5b82, pae-ether-type = 0x888E
2023/12/05 17:44:45.046004696 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Posting EAPOL_START on Client
2023/12/05 17:44:45.046126523 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Entering init state
2023/12/05 17:44:45.046150743 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Entering idle state
2023/12/05 17:44:45.046161746 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Posting !AUTH_ABORT on Client
2023/12/05 17:44:45.046211238 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Entering restart state
2023/12/05 17:44:45.046215274 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Resetting the client 0x6600001A
2023/12/05 17:44:45.046243054 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Override cfg - MAC ec2e.9835.cc35 - profile (none)
2023/12/05 17:44:45.046245588 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Override cfg - SuppTimeout 40s, ReAuthMax 3, MaxReq 3, TxPeriod 40s
2023/12/05 17:44:45.046250524 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Sending create new context event to EAP for 0x6600001A (ec2e.9835.cc35)
2023/12/05 17:44:45.046425795 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Posting !EAP_RESTART on Client
2023/12/05 17:44:45.046431369 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Enter connecting state
2023/12/05 17:44:45.046437180 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Restart connecting
2023/12/05 17:44:45.046460742 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Posting RX_REQ on Client
2023/12/05 17:44:45.046466486 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Authenticating state entered
2023/12/05 17:44:45.046487415 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Connecting authenticating action
2023/12/05 17:44:45.046503182 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Entering request state
2023/12/05 17:44:45.046529917 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [0000.0000.0000:capwap_9000000d] Setting EAPOL eth-type to 0x888e, destination mac to ec2e.9835.cc35
2023/12/05 17:44:45.046532291 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [0000.0000.0000:capwap_9000000d] Sending out EAPOL packet
2023/12/05 17:44:45.046691941 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Sent EAPOL packet - Version : 3,EAPOL Type : EAP, Payload Length : 5, EAP-Type = Identity
2023/12/05 17:44:45.046712075 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] EAP Packet - REQUEST, ID : 0x1
2023/12/05 17:44:45.046715403 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [0000.0000.0000:unknown] Pkt body: 01 01 00 05 01
2023/12/05 17:44:45.046720952 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] EAPOL packet sent to client
2023/12/05 17:44:52.315398205 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Received EAPOL packet - Version : 1,EAPOL Type : EAP, Payload Length : 12, EAP-Type = Identity
2023/12/05 17:44:52.315402131 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] EAP Packet - RESPONSE, ID : 0x1
2023/12/05 17:44:52.315408673 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [0000.0000.0000:unknown] Pkt body: 02 01 00 0c 01 72 6f 73 61 72 69 6f
2023/12/05 17:44:52.315414332 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [0000.0000.0000:capwap_9000000d] Queuing an EAPOL pkt on Authenticator Q
2023/12/05 17:44:52.315484658 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [0000.0000.0000:capwap_9000000d] Dequeued pkt: CODE = 2,TYPE = 1,LEN = 12
2023/12/05 17:44:52.315494651 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [0000.0000.0000:capwap_9000000d] Received pkt saddr = ec2e.9835.cc35 , daddr = 00d7.8f2f.5b82, pae-ether-type = 0x888E
2023/12/05 17:44:52.316073597 {wncd_x_R0-0}{1}: [caaa-authen] [19713]: (info): [CAAA:AUTHEN:b8000026] NULL ATTR LIST
2023/12/05 17:44:52.316518576 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Raised identity update event for eap method Identity
2023/12/05 17:44:52.316587856 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Entering idle state
2023/12/05 17:44:52.316598992 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Posting AUTH_FAIL on Client
2023/12/05 17:44:52.316743601 {wncd_x_R0-0}{1}: [errmsg] [19713]: (note): %DOT1X-5-FAIL: R0/0: wncd: Authentication failed for client (ec2e.9835.cc35) with reason (Cred Fail) on Interface capwap_9000000d AuditSessionID 320A16AC000000303BF0C109 Username: rosario
2023/12/05 17:44:52.316777401 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Authc failure from Dot1X, Auth event fail
2023/12/05 17:44:52.316795966 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Method dot1x changing state from 'Running' to 'Authc Failed'
2023/12/05 17:44:52.316836658 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Raised event RX_METHOD_AUTHC_FAIL (6)
2023/12/05 17:44:52.316855796 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Raised event REMOVE_USER_PROFILE (15)
2023/12/05 17:44:52.316900046 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Context changing state from 'Running' to 'Authc Failed'
2023/12/05 17:44:52.317000563 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] auth mgr attr add/change notification is received for attr username(450)
2023/12/05 17:44:52.317074927 {wncd_x_R0-0}{1}: [auth-mgr-feat_acct] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] SM Notified attribute Add/Update username rosario
2023/12/05 17:44:52.317084730 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Received User-Name rosario for client ec2e.9835.cc35
2023/12/05 17:44:52.317127562 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] AUTHC_FAIL - unauthorize by default
2023/12/05 17:44:52.317135374 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Signalling Authc fail for client ec2e.9835.cc35
2023/12/05 17:44:52.317211383 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [19713]: (ERR): SANET_AUTHC_FAILURE - Cred Fail, username rosario, audit session id 320A16AC000000303BF0C109
2023/12/05 17:44:52.317241950 {wncd_x_R0-0}{1}: [errmsg] [19713]: (note): %SESSION_MGR-5-FAIL: R0/0: wncd: Authorization failed or unapplied for client (ec2e.9835.cc35) on Interface capwap_9000000d AuditSessionID 320A16AC000000303BF0C109. Failure reason: Authc fail. Authc failure reason: Cred Fail.
2023/12/05 17:44:52.317251925 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Authz failed/unapplied), method: dot1x. Signal switch PI.
2023/12/05 17:44:52.317334822 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] auth mgr attr add/change notification is received for attr method(757)
2023/12/05 17:44:52.317370860 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Context changing state from 'Authc Failed' to 'Authz Failed'
2023/12/05 17:44:52.317543862 {wncd_x_R0-0}{1}: [llbridge-main] [19713]: (debug): MAC: ec2e.9835.cc35 Link-local bridging not enabled for this client, not checking VLAN validity
2023/12/05 17:44:52.317618188 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : username 0 "rosario"
2023/12/05 17:44:52.317621864 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : service-type 0 2 [Framed]
2023/12/05 17:44:52.317624615 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : Framed-MTU 0 1485 (0x5cd)
2023/12/05 17:44:52.317626666 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : EAP-Message 0 <hidden>
2023/12/05 17:44:52.317628524 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : Message-Authenticator 0 <hidden>
2023/12/05 17:44:52.317645357 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : EAP-session-id 0 ""
2023/12/05 17:44:52.317647930 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : audit-session-id 0 "320A16AC000000303BF0C109"
2023/12/05 17:44:52.317650500 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : hwidb 0 2415919117 (0x9000000d)
2023/12/05 17:44:52.317653091 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : method 0 0 [dot1x]
2023/12/05 17:44:52.317655324 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : aaa-authen-type 0 8 (0x8)
2023/12/05 17:44:52.317657557 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : aaa-authen-service 0 19 (0x13)
2023/12/05 17:44:52.317661854 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : clid-mac-addr 0 ec 2e 98 35 cc 35
2023/12/05 17:44:52.317664450 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : target-scope 0 0 [client]
2023/12/05 17:44:52.317666682 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : aaa-unique-id 0 48 (0x30)
2023/12/05 17:44:52.317669038 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : client-iif-id 0 2030045187 (0x79000803)
2023/12/05 17:44:52.317671294 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : vlan-id 0 203 (0xcb)
2023/12/05 17:44:52.317673079 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : session-linksec-secured 0 False
2023/12/05 17:44:52.317675315 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : nas-ip-address 0 0x0
2023/12/05 17:44:52.317677406 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : nas-ipv6-Address 0 ""
2023/12/05 17:44:52.317679394 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : interface 0 ""
2023/12/05 17:44:52.317682042 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : port-type 0 19 [802.11 wireless]
2023/12/05 17:44:52.317684335 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : nas-port 0 21012 (0x5214)
2023/12/05 17:44:52.317686423 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : cisco-wlan-ssid 0 "auth"
2023/12/05 17:44:52.317688502 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : wlan-profile-name 0 "lab_doble_authe"
2023/12/05 17:44:52.317690517 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : dnis 0 "00-d7-8f-2f-5b-80:auth"
2023/12/05 17:44:52.317692578 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : formatted-clid 0 "ec-2e-98-35-cc-35"
2023/12/05 17:44:52.317694803 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : bsn-wlan-id 0 4 (0x4)
2023/12/05 17:44:52.317696861 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : nas-identifier-wireless 0 "WLC"
2023/12/05 17:44:52.317709452 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : wlan-group-cipher 0 ""
2023/12/05 17:44:52.317711643 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : wlan-pairwise-cipher 0 ""
2023/12/05 17:44:52.317713526 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : wlan-akm-suite 0 ""
2023/12/05 17:44:52.317715694 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : dnis 0 "00-D7-8F-2F-5B-80"
2023/12/05 17:44:52.317717647 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : formatted-clid 0 "EC-2E-98-35-CC-35"
2023/12/05 17:44:52.317719630 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : audit-session-id 0 "320A16AC000000303BF0C109"
2023/12/05 17:44:52.319815936 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : clid-mac-addr 0 ec 2e 98 35 cc 35
2023/12/05 17:44:52.319823035 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): Applying Attribute : intf-id 0 2415919117 (0x9000000d)
2023/12/05 17:44:52.319860511 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Posting_AUTHZ_FAIL on Client
2023/12/05 17:44:52.319917095 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [0000.0000.0000:capwap_9000000d] Setting EAPOL eth-type to 0x888e, destination mac to ec2e.9835.cc35
2023/12/05 17:44:52.319919813 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [0000.0000.0000:capwap_9000000d] Sending out EAPOL packet
2023/12/05 17:44:52.320113514 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Sent EAPOL packet - Version : 3,EAPOL Type : EAP, Payload Length : 4, EAP-Type = 0
2023/12/05 17:44:52.320117268 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] EAP Packet - FAILURE, ID : 0x1
2023/12/05 17:44:52.320120026 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [0000.0000.0000:unknown] Pkt body: 04 01 00 04
2023/12/05 17:44:52.320125817 {wncd_x_R0-0}{1}: [dot1x] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] EAPOL packet sent to client
2023/12/05 17:44:52.320361963 {wncd_x_R0-0}{1}: [client-auth] [19713]: (info): MAC: ec2e.9835.cc35 Client auth-interface state transition: S_AUTHIF_DOT1XAUTH_PENDING -> S_WAIT_FOR_CO_DELETE
2023/12/05 17:44:52.320438410 {wncd_x_R0-0}{1}: [client-orch-sm] [19713]: (info): MAC: ec2e.9835.cc35 Deleting the client, reason: 93, CO_CLIENT_DELETE_REASON_CLIENT_CREDENTIAL_FAILURE, Client state S_CO_L2_AUTH_IN_PROGRESS
2023/12/05 17:44:52.320469639 {wncd_x_R0-0}{1}: [client-orch-sm] [19713]: (note): MAC: ec2e.9835.cc35 Client delete initiated. Reason: CO_CLIENT_DELETE_REASON_CLIENT_CREDENTIAL_FAILURE, details: , fsm-state transition 00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|01|07|15|1e|27|
2023/12/05 17:44:52.320760826 {wncd_x_R0-0}{1}: [client-orch-sm] [19713]: (note): MAC: ec2e.9835.cc35 Delete mobile payload sent for BSSID: 00d7.8f2f.5b8d WTP mac: 00d7.8f2f.5b80 slot id: 1
2023/12/05 17:44:52.320776583 {wncd_x_R0-0}{1}: [client-orch-state] [19713]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_L2_AUTH_IN_PROGRESS -> S_CO_DELETE_IN_PROGRESS
2023/12/05 17:44:52.320901159 {wncd_x_R0-0}{1}: [client-orch-sm] [19713]: (ERR): MAC: ec2e.9835.cc35 CLT populate Record: failed to populate anchor ip
2023/12/05 17:44:52.321060728 {wncd_x_R0-0}{1}: [ewlc-qos-voice] [19713]: (info): MAC: ec2e.9835.cc35 Successfully freed the bw for sip client
2023/12/05 17:44:52.321163705 {wncd_x_R0-0}{1}: [multicast-main] [19713]: (info): MAC: ec2e.9835.cc35 No Flex/Fabric main record exists for client
2023/12/05 17:44:52.321342739 {wncd_x_R0-0}{1}: [client-iplearn] [19713]: (info): MAC: ec2e.9835.cc35 IP-learn state transition: S_IPLEARN_INIT -> S_IPLEARN_DELETE_IN_PROGRESS
2023/12/05 17:44:52.321414885 {wncd_x_R0-0}{1}: [mm-transition] [19713]: (info): MAC: ec2e.9835.cc35 MMIF FSM transition: S_MA_INIT -> S_MA_LOCAL_DELETE_PROCESSED_TR on E_MA_CO_DELETE_RCVD
2023/12/05 17:44:52.321532346 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Raised event DELETE (19)
2023/12/05 17:44:52.321538595 {wncd_x_R0-0}{1}: [auth-mgr] [19713]: (info): [ec2e.9835.cc35:capwap_9000000d] Disconnect request from SANET-SHIM (15) for ec2e.9835.cc35 / 0xb8000026 - term: none, abort: Unknown, disc: (default)
2023/12/05 17:44:52.321539861 {wncd_x_R0-0}{1}: [sanet-shim-translate] [19713]: (note): MAC: ec2e.9835.cc35 Session manager disconnect event called, session label: 0xb8000026
2023/12/05 17:44:52.321567371 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): [ Applied attribute :bsn-vlan-interface-name 0 "dima_203" ]
2023/12/05 17:44:52.321570640 {wncd_x_R0-0}{1}: [aaa-attr-inf] [19713]: (info): [ Applied attribute : timeout 0 1800 (0x708) ]
2023/12/05 17:44:52.321581828 {wncd_x_R0-0}{1}: [client-auth] [19713]: (info): MAC: ec2e.9835.cc35 Client auth-interface state transition: S_WAIT_FOR_CO_DELETE -> S_SANET_DELETE_IN_PROGRESS
2023/12/05 17:44:52.321612844 {wncd_x_R0-0}{1}: [dot11] [19713]: (info): MAC: ec2e.9835.cc35 Total length of Deauth/Disassoc: 2
2023/12/05 17:44:52.321758061 {wncd_x_R0-0}{1}: [dot11] [19713]: (info): MAC: ec2e.9835.cc35 Sent disassoc to client, disassoc reason: 23, CLIENT_DEAUTH_REASON_8021X_AUTH_FAILED delete reason: 93, CO_CLIENT_DELETE_REASON_CLIENT_CREDENTIAL_FAILURE.
2023/12/05 17:44:52.321763128 {wncd_x_R0-0}{1}: [dot11] [19713]: (info): MAC: ec2e.9835.cc35 Total length of Deauth/Disassoc: 2
2023/12/05 17:44:52.321914304 {wncd_x_R0-0}{1}: [dot11] [19713]: (info): MAC: ec2e.9835.cc35 Sent deauth to client, deauth reason: 23, CLIENT_DEAUTH_REASON_8021X_AUTH_FAILED delete reason: 93, CO_CLIENT_DELETE_REASON_CLIENT_CREDENTIAL_FAILURE.
2023/12/05 17:44:52.322107110 {wncd_x_R0-0}{1}: [dot11] [19713]: (info): MAC: ec2e.9835.cc35 DOT11 state transition: S_DOT11_ASSOCIATED -> S_DOT11_DELETED
2023/12/05 17:44:52.322830128 {wncd_x_R0-0}{1}: [caaa-acct] [19713]: (info): [CAAA:ACCT] Not a webauth call
2023/12/05 17:44:52.323678614 {wncd_x_R0-0}{1}: [client-auth] [19713]: (info): MAC: ec2e.9835.cc35 Client auth-interface state transition: S_SANET_DELETE_IN_PROGRESS -> S_AUTHIF_DELETED
2023/12/05 17:44:52.323814843 {wncd_x_R0-0}{1}: [client-orch-state] [19713]: (note): MAC: ec2e.9835.cc35 Client state transition: S_CO_DELETE_IN_PROGRESS -> S_CO_DELETED
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2023 12:33 AM
>...I upgraded to version 17.09.04a, but I'm still experiencing issues
- I would advice to save user data on the PC , reinstall it from scratch and try again ,
M.
-- Each morning when I wake up and look into the mirror I always say ' Why am I so brilliant ? '
When the mirror will then always repond to me with ' The only thing that exceeds your brilliance is your beauty! '
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2023 10:12 AM
What l2 secuirty you use ?
Can you share screenshots of wlan security page.
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2023 10:14 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2023 10:22 AM
Ok' now the screenshots of AAA page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2023 11:04 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2023 11:13 AM
You add aaa server to WLC but you dont config wlan to use it.
In wlan ->secuirty->aaa
Add this server to make wlan use it to auth any wifi client connect
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2023 11:21 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2023 12:06 PM
Every thing is correct'
No issue except
Source interface is none
Select any vlan (that map to this wlan or vlan of mgmt).
MHM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide