- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Various questions about iPSK and WPA3
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Various questions about iPSK and WPA3
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2019 04:04 AM - edited 07-05-2021 11:11 AM
I recently implemented iPSK on a small Mobility Express deployment, and it seems to work well.
Earlier this week, I updated to the newly-released 8.10.105.0 code, and was eager to try out WPA3-Personal. However I noticed these limitations mentioned in the release notes:
- IPSK with SAE is not supported.
- FT with SAE is not supported.
I found that enabling WPA3 on an existing WPA2-PSK SSID (so that it operates in mixed mode) works fine - ie all the WPA2-only clients can still associate using WPA2, and the few WPA3-capable clients I have begin to use WPA3. Although strangely I noticed that while the controller reports my Pixel 3 XL phone as having associated using WPA3 & SAE, it reports my Windows 10 laptops (with Intel 8265 wifi chips) as having associated using WPA3 & PSK... I thought a core feature of WPA3-Personal was its use of SAE instead of PSK, so I find it strange that the controller reports the Windows 10 clients to be using WPA3 without SAE. Does that make any sense?
Anyway, having got both iPSK and WPA3-Personal working independently, I tried enabling WPA3 on my SSID which is configured for iPSK. The behaviour seems to be that my WPA3-capable Pixel 3 XL can now associate using the default PSK configured for the SSID, but not with its unique iPSK, confirming the restriction mentioned in the release notes. I have not yet tested whether WPA2-only clients can still connect to the mixed-mode WPA2/3 iPSK SSID using their unique iPSKs, but I'm guessing they probably can if the limitation is specific to SAE. (I'll update this if I get a chance to test that).
My main question is whether this is just a temporary limitation, which will be lifted in a future release - or will iPSK and WPA3 SAE never work together? Any ideas?
Separately I noticed a new option in the Mobility Express GUI named "AutoConfig iPSK". However I cannot find any documentation about it. Does anyone know what it does? Note that my existing SSID on which iPSK is working does not have that new option enabled, so it's clearly not essential for iPSK. Also I have found that it is not possible to have both "WPA3" and "AutoConfig iPSK" enabled simultaneously (if I enable both in the GUI, and click Save, the SSID is automatically disabled, and I can only enable it again if I disable one of those two options).
I'd be similarly interested in knowing whether the lack of support for having SAE and FT enabled at the same time is likely to be lifted in a future release - does anyone know?
Finally (perhaps I should have split this into multiple separate threads...), has anyone seen any documentation from Cisco on which models of access point support WPA3? My deployment has both 2802i and 3702i access points. And although the Mobility Express controller allows me to configure WPA3-Personal SSIDs, I am finding that the one client I have which supports SAE (my Pixel 3 XL phone) will only associate to the 2802i access points when using an SSID on which WPA3 is enabled. So I suspect that the 3702i does not actually support SAE. However I can't find any documentation from Cisco showing which AP models support it.
Alex
- Labels:
-
Mobility Express
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2019 01:11 PM
Autoconfigure iPSK requires that you have AAA override enabled and MacFiltering also enabled.
I'm playing with the 8.5.105 release at the moment, and there are some quirky things, it boots devices at 24 hours, not so much of a problem but the time it takes to re-establish the connection means that things such as VoIP WiFi phones end up dropping the call...or the AppleTV that is streaming SkyNews will drop the connection and stop the video from working.
From a macOS 10.15 machine I can connect using WPA3 and that uses SAE too - I would suggest upgrading your Win 10 network drivers, and also check the advanced settings on the adapter itself, there maybe something there that's impacting on your connection method.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2019 04:28 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2019 05:45 PM
I’m also not a fan of over complicating configurations as it causes more issues down the road. I didn’t like iPSK due to some devices not working well with that setup. Also WPA3 is new and should take some time before it works as intended. This also goes for the client side.
*** Please rate helpful posts ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2019 03:13 AM
Out of interest, what kind of devices don't work well with iPSK? Surely it's just an alternative way of defining (on the wireless infrastructure side) what the PSK should be in a given situation - ie from a client's perspective it is no different to connecting to an ordinary PSK-based SSID.
The only potential issue I can think of is the fact it is reliant on identifying clients by their MAC addresses, and some client platforms seem to randomize their wireless MACs by default nowadays. However Android does this in a way that doesn't actually cause problems - it uses a different randomized MAC for each SSID the device knows about, but each time it connects to a given SSID it always presents the same randomized MAC. So the iPSK deployment will just match on the particular randomized MAC that the device has generated for use with the iPSK-based SSID, and everything will work as expected. Admittedly I've not looked at the behaviour on iPhones (as I don't have one).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2019 06:49 AM
@timgrantham wrote:Autoconfigure iPSK requires that you have AAA override enabled and MacFiltering also enabled.
But how is it different from normal iPSK (which I already have working, and which similarly requires AAA override and MacFiltering, but doesn't need "AutoConfig iPSK" to be enabled)?
@timgrantham wrote:From a macOS 10.15 machine I can connect using WPA3 and that uses SAE too - I would suggest upgrading your Win 10 network drivers, and also check the advanced settings on the adapter itself, there maybe something there that's impacting on your connection method.
Yeah I'm already running the latest drivers from Intel - but I can believe it's a client limitation - perhaps the Intel 8265 wifi chips don't do SAE. I was just surprised that it seems to be possible to connect using WPA3 but without SAE.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2019 02:16 PM
Did you upgrade an from an old system such as from 8.5.x.x? I always find that it's best to reset to factory defaults and reconfigure.
I'm wondering if SAE hasn't been enabled on your configuration.
do a "show wlan x" - replacing x with the number of the wlan which can be found by punching in "show wlan summary".
This is what I get
Security 802.11 Authentication:........................ Open System FT Support.................................... Adaptive Static WEP Keys............................... Disabled 802.1X........................................ Disabled Wi-Fi Protected Access (WPA/WPA2/WPA3)........ Enabled WPA (SSN IE)............................... Disabled WPA2 (RSN IE).............................. Enabled WPA3 (RSN IE).............................. Enabled WPA2/WPA3 Encryption Ciphers TKIP Cipher............................. Disabled CCMP128/AES Cipher...................... Enabled CCMP256 Cipher.......................... Disabled GCMP128 Cipher.......................... Disabled GCMP256 Cipher.......................... Disabled OSEN IE.................................... Disabled Auth Key Management 802.1x.................................. Disabled 802.1x-SHA2............................. Disabled PSK..................................... Enabled PSK-SHA2................................ Disabled CCKM.................................... Disabled FT-1X(802.11r).......................... Disabled FT-PSK(802.11r)......................... Disabled OSEN-1X................................. Disabled SUITEB-1X............................... Disabled SUITEB192-1X............................ Disabled OWE..................................... Disabled SAE..................................... Enabled OWE Transition Mode........................ Disabled OWE Transition Mode WLAN id................ 0 Auto Key PSK .............................. Disabled FT Reassociation Timeout................... 20 FT Over-The-DS mode........................ Disabled GTK Randomization.......................... Disabled SKC Cache Support.......................... Disabled CCKM TSF Tolerance......................... 1000 Wi-Fi Direct policy configured................ Disabled EAP-Passthrough............................... Disabled
Have a look to see if SAE is enabled for sure...
If it's not enabled you could try enabling in using "config wlan security wpa akm sae enable xx". replacing xx with the wlan ID.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2019 03:06 AM
Yes it was an upgrade from 8.5 (I think I've had this deployment running 8.5, then 8.8, then 8.9, and now 8.10). But SAE is definitely enabled, since it works with my smartphone (as mentioned in my original post). Here's the equivalent output from the show wlan command on my setup... in looks identical to yours:
Security
802.11 Authentication:........................ Open System
FT Support.................................... Adaptive
Static WEP Keys............................... Disabled
802.1X........................................ Disabled
Wi-Fi Protected Access (WPA/WPA2/WPA3)........ Enabled
WPA (SSN IE)............................... Disabled
WPA2 (RSN IE).............................. Enabled
WPA3 (RSN IE).............................. Enabled
WPA2/WPA3 Encryption Ciphers
TKIP Cipher............................. Disabled
CCMP128/AES Cipher...................... Enabled
CCMP256 Cipher.......................... Disabled
GCMP128 Cipher.......................... Disabled
GCMP256 Cipher.......................... Disabled
OSEN IE.................................... Disabled
Auth Key Management
802.1x.................................. Disabled
802.1x-SHA2............................. Disabled
PSK..................................... Enabled
PSK-SHA2................................ Disabled
CCKM.................................... Disabled
FT-1X(802.11r).......................... Disabled
FT-PSK(802.11r)......................... Disabled
OSEN-1X................................. Disabled
SUITEB-1X............................... Disabled
SUITEB192-1X............................ Disabled
OWE..................................... Disabled
SAE..................................... Enabled
OWE Transition Mode........................ Disabled
OWE Transition Mode WLAN id................ 0
Auto Key PSK .............................. Disabled
FT Reassociation Timeout................... 20
FT Over-The-DS mode........................ Disabled
GTK Randomization.......................... Disabled
SKC Cache Support.......................... Disabled
CCKM TSF Tolerance......................... 1000
Wi-Fi Direct policy configured................ Disabled
EAP-Passthrough............................... Disabled
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2019 05:40 PM
Here are a few links that can help you out
WPA3 Support
WPA3 and SAE
https://wificoops.com/2019/07/28/wi-fi-security-enhancements-part-1-wpa3-personal-sae/
*** Please rate helpful posts ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2019 08:31 PM
SAE + IPSK is supported with Catalyst 9800. I don't believe it will be supported with AireOS. Also here are the WPA3 supported WLC and AP according to the technote:
- Cisco Catalyst®wireless platforms: 9800-40, 9800-80, 9800-L and 9800-CL
- Cisco Unified Wireless Network wireless controllers: 3504, 5520 Series, 8540 Series, and Virtual Wireless Controller
- 802.11ac Wave 1 and Wave 2 access points: Cisco Aironet®1800 Series, 2802, 3802, 4800, and the 1540, 1560, 1700, 2700, 3700, and 1570 Series
- 802.11ax access points: Cisco Catalyst 9115AX, 9117AX, and 9120AX Series
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2020 12:09 PM
Hey @Alex Moore , I think you have a very well thought out and posed question. I'm surprised that over 6 months later there is no response to the new feature "AutoConfig iPSK" and that there still seems to be no supporting documentation on it. I am building a WLAN standard for iPSK out in a large deployment and want to make sure I'm not disabling important features right out the gate! As I continue testing in dev, I'll post here if I find the answer.
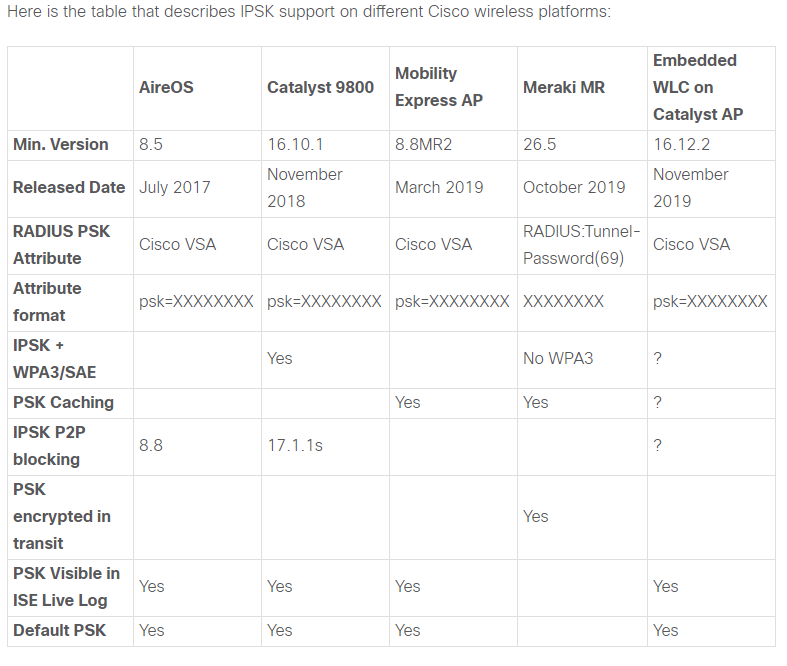
I thought it's possible that it's related to iPSK P2P blocking but that feature was released in 8.8. Showing in the table from @howon below.
On another thought about production code version; I know that TAC is still recommending 8.5 and I hear your thoughts @Scott Fella but I personally feel more confident with iPSK on more developed versions than the one it was initially released on.
We have seen excellent stability with almost 100 5520s on 8.8.125.0 and are currently testing 8.10 as our next release for interoperability with DNA and our 9800s and it is looking very promising so far!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide