- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Re: WLC + NPS + EAP-TLS + Machine certificate
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2019 12:09 AM - edited 07-05-2021 10:54 AM
Hi!
I'm a bit lost here trying to set up EAP-TLS. I want my laptops to automatically sign on to my corporate network using computer certificate (or user certificate, does not really matter – but I've tried both without any luck). I have the following "players" in my environment:
- WLC - Cisco 2500 Wireless Controller
- Radius NPS Windows 2012
- Windows 10 clients
- Local CA (Windows 2016)
I have followed a few different guides, without any luck and I've decided to reach out instead of trying more
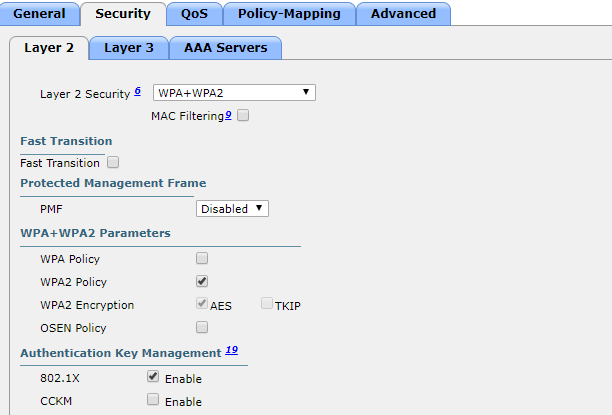
But, I've noticed that when I have when I (from my WLC) have configured the WPA+WPA2 settings under layer 2 for the specific WLAN, the connection from the client computer gets an 'X' over itself and can't be connected (see screenshots below).
And when I configure 802.1X under Layer 2 security I am unable to choose a certificate issued by my Certificate Authority.
I've added some screenshots of my configuration. Any tips are appreciated!
With kind regards,
TB
Solved! Go to Solution.
- Labels:
-
Wireless LAN Controller
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2019 06:32 AM
Thought I'd update everyone. The issue was resolved when I removed the 'EAP authentication' method requirement from the 'Network Policies' 'Condition'-tab. From Event Viewer I can see that it still communicates via EAP and certificate, but it just worked when I removed this additional setting. The Constrataints still require EAP Type for Smart card or certificate, so maybe there was one EAP requirement to much?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2019 02:33 AM
you must select WPA/WPA2 as layer 2 security + 802.1x as auth key mgmt.
Please check this guide:
https://networklessons.com/uncategorized/peap-and-eap-tls-on-server-2008-and-cisco-wlc
https://www.petenetlive.com/KB/Article/0001420
Regards
Dont forget to rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2019 02:57 AM
Dear Sandeep,
Thanks for your swift reply - but as you can see in my original post (attachment name: WLC_WLAN_Security_L2), I've setup the WPA/WPA2 as per your recommendation. I've read through the two guides and do not see any difference between my setup and theirs. Also, there is currently no communication between my RADIUS server and WLC, so as far as I can tell the connection is unsuccessful from the laptop to the WLC.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2019 06:29 AM
Hi There,
Double-check your certificates on the 2012 server the NPS is hosted on and what certificate the NPS is using. I've had situations before where the Windows server had multiple certificates and the NPS chose the incorrect certificate or the GPO would auto-enrol a cert on the NPS after you fixed it. Ensure your certs template on the CA are compatible with 2012 servers.
Also if you don't pick up any NPS errors in event viewer related to a client, you most certainly have an issue with your certificates, either the client, NPS or CA.
The WLC setup is the easiest and simplest part of the setup as it's simply forwarding and receiving the RADIUS requests from the client and NPS. Therefore the configuring WPA2/AES with 802.1X and the IP's of your RADIUS servers is pretty much the basic requirement you need to get the 802.1X authentication to work.
The tricky part can be your template on the CA, check this guide from page 58 that will show you how to setup your templates correctly on the CA:
https://www.cisco.com/c/dam/en/us/td/docs/solutions/CVD/Aug2014/CVD-CampusDot1XDesignGuide-AUG14.pdf
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-02-2019 12:59 AM - edited 09-02-2019 06:49 AM
----Update----
My checkpoint FW apparently drop the package and ignore the policy, without a reference to any access rules. So, I guess I know why I have issues... Still do not know why the checkpoints drop it however...
---Update----
Dear Jurgens,
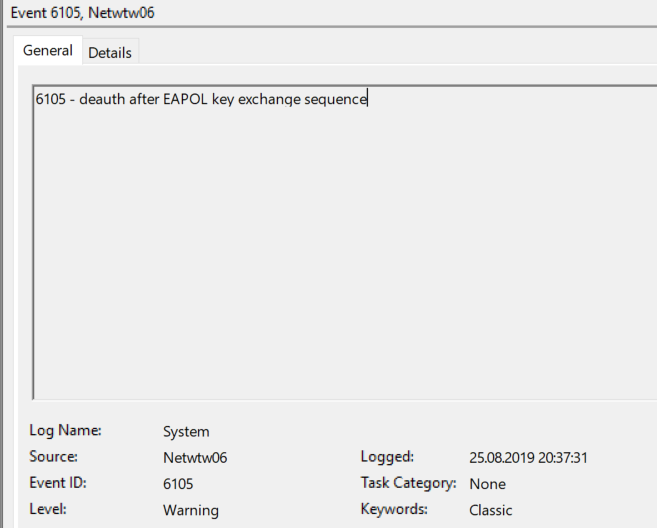
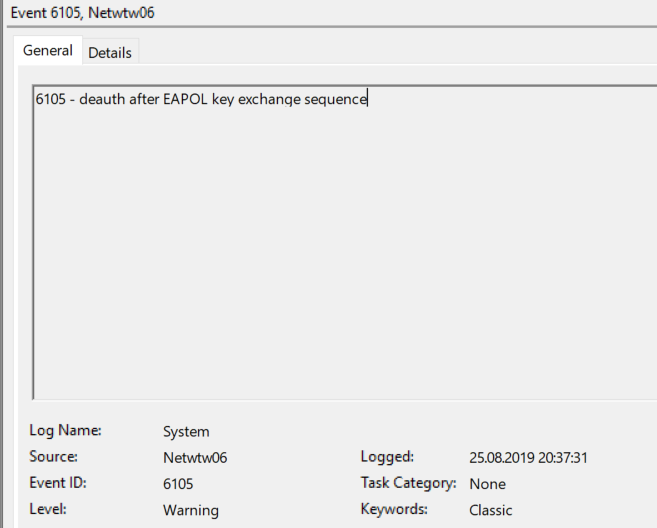
Thanks for your reply and sorry for my late follow-up. I would like to mention that I am an "accidental Network administrator" – and that I have limited knowledge about this. But, from all the guides I've read it appears that it is enough to have a "client authentication"-certificate with PKE for my clients. The Radius server (NPS) needs Client & Server authentication with PKE. But, I think you are correct in that the problem lies in the certificate. As mentioned above, from the client machine – when I attempt to connect to the wlan, I receive this event ID: "deauth after EAPOL key exchange sequence."
Is there any settings I need to configure on the APs? Or do I need to upload the root & intermediate certificate to the WCL?
Additional information:
When I generate a wlanraport ("netsh wlan show wlanreport" from cmd) I can see:
Wireless security started
Wireless 802.1x authentication started
Wireless 802.1x authentication was restarted
User Uses Saved Credentials
Wireless 802.1x authentication was restarted
User Uses Saved Credentials
then it loops.
From the WLCs message logs:
*spamApTask7: Sep 02 12:53:20.868: %LWAPP-3-REPLAY_ERR: spam_lrad.c:41295 The system has received replay error on slot 0, WLAN ID 4, count 1 from AP 70:69:5a:xx:xx:xx
*Dot1x_NW_MsgTask_2: Sep 02 12:53:16.525: %DOT1X-3-AAA_AUTH_SEND_FAIL: 1x_aaa.c:849 Unable to send AAA message for client a4:34:d9xx:xx:xx
*Dot1x_NW_MsgTask_2: Sep 02 12:53:16.505: %DOT1X-3-ABORT_AUTH: 1x_bauth_sm.c:450 Authentication Aborted for client a4:34:d9:xx:xx:xx Abort Reason:DOT1X RESTARTED DUE TO EAPOL-START/CLIENT ROAM
*spamApTask0: Sep 02 12:53:09.810: %LWAPP-3-REPLAY_ERR: spam_lrad.c:41295 The system has received replay error on slot 0, WLAN ID 4, count 4 from AP 40:01:7a:xx:xx:xx
*Dot1x_NW_MsgTask_2: Sep 02 12:52:58.499: %DOT1X-3-AAA_AUTH_SEND_FAIL: 1x_aaa.c:849 Unable to send AAA message for client a4:34:d9:xx:xx:xx
With best regards,
Theodor
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2019 08:14 PM
Under your event viewer you need to look at the NPS filter as this will give you more information as that is where all the intelligence is happening. With your issue I would not be surprised if you don’t see any logs related to authentication errors, which in my book is a red flag that you have certification issues.
Think as your AP and WLC as a trusted bridge between the client and the NPS, it simply forwards RADIUS requests from the clients. You only required to setup your SSID with WPA2/AES and 802.1X, pointing to your RADIUS services to the NPS server. That will be enough to get your authentication to work on the WLC side. You can load certificates onto your WLC and AP’s however this is more for a solution where you need AP’s in remote branches to serve clients with EAP-TLS authentications in the event of a WAN link failure (NPS unreachable). This is also something you do once you have first tested the basic functionality of your EAP-TLS authentication.
90% of the work is on the Microsoft end, therefore I would go through the guide I referred to you on my previous post and also verify your Domain certificates are installed properly, mapped to the NPS and compatible with the version of Windows server the NPS is using since your CA is running on 2016.
Setting this up the first time will take a lot of your time and the troubleshooting can be frustrating. Most of the deployment guides are long but if you take a step back and go thoroughly through them I’m sure you will get it right. There is nothing more satisfying when you see the client connected via EAP-TLS for the first time 😊
Good Luck
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2019 06:32 AM
Thought I'd update everyone. The issue was resolved when I removed the 'EAP authentication' method requirement from the 'Network Policies' 'Condition'-tab. From Event Viewer I can see that it still communicates via EAP and certificate, but it just worked when I removed this additional setting. The Constrataints still require EAP Type for Smart card or certificate, so maybe there was one EAP requirement to much?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide