- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE in Radius Proxy mode
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-20-2017 02:54 PM
Hi All
... ISE should work in radius proxy mode for Airline-A. Because ISE just forwards requests ..., how can we assign different vlans to different AD groups in Airline-A AD?
Second question; other airlines will also not let Customer-A's ISE to connect their AD. So how many different external radius servers can be used on ISE? I know we support multiple external radius. But is there any limitation for the number?
Third question; will this setup work together with Customer-A's own users' AD auth method? Multiple external radius servers and local AD auth simultaneously?
Thanks
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-20-2017 04:32 PM
1. ISE external RADIUS sequence has an option [ ]
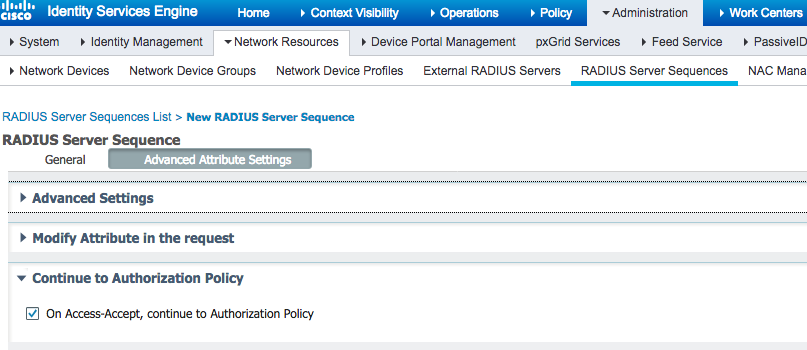
Thus, ISE may check the attributes returned by the external servers and use them to determine on the authorization profiles and TrustSec groups.
2. Same limit as NADs.
3. Yes, but we need ISE authentication policy rules to determine when to proxy and when not to.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-20-2017 04:32 PM
1. ISE external RADIUS sequence has an option [ ]

Thus, ISE may check the attributes returned by the external servers and use them to determine on the authorization profiles and TrustSec groups.
2. Same limit as NADs.
3. Yes, but we need ISE authentication policy rules to determine when to proxy and when not to.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-21-2017 02:13 PM
Hi Hsing
By clicking "On Access-Accept, continue to Authorization Policy" i will be able to assign VLAN,etc and ignore what radius says, right? But in this case i will not be able to see domain groups on ISE and will not able able to configure authorisation profile per AD group, am i right?
Or oppositely, can i leave plan assignment job to the radius server? Because radius server will be directly talking to AD, it will have domain group info. So it can assign VLAN,etc and dictate to ISE, right?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-21-2017 06:12 PM
Hi Ozgur,
As proxy, ISE forwards only the authentication and accounting request to the Radius server. When the external Radius server sends access accept, ISE processes the authorization policy with the option turned on.
If you are using IGA ISE server as proxy and THY ACS server has access to AD, then IGA server cannot authorize using the AD group since it has no idea of AD.
Now as part of Access Accept, ACS server can authorize and send VLAN values back to ISE. ISE in turn will forward that to the network device. So ISE will be just a proxy for the users and everything is done in ACS.
For this to happen you have to uncheck the option “On Access-Accept, continue to Authorization policy”.
Thanks
Krishnan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-28-2018 07:42 AM
Hi Krishnan,
Have a question for the exact same place IGA :)
What happens if we want to prevent the external radius to use a specific vlan id.
Can we make use of Modify attributes before access accept ?
I tried to prevent this by adding a condition on my authorization rule defining Radius Tunnel Private Group id, but it was not hitting this rule. (Although i can see in the details of the logs, its getting this tunnel private group id.)
(I answered my own question while asking you a question :))))
I changed my condition to Radius : Tunnel-Private-Group-Id equals (tag=0) 205 then it started hitting this policy.
I think i'll be able to restrict every external radius with specified vlans?
I'd really appreciate your comment.
Kind regards
Sadik
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2018 04:00 AM
Hi,
we have customer which has hosted AD on Azure & ISE is on premise.
plan is to make ISE as radius proxy, where ISE will forward request to External radius server which i have hosted on Azure cloud.
so wanted to check whether this scenario will work or not. Typicall user traffic will be as below
WLC >> On Premise ISE ( Proxy Radius) >> Azure Radius Server >> Azure AD
Regards,
Pratik Gandhi
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2018 04:33 AM
Likely will work but not tested by our teams specifically with that configuration
ISE In general supports radius proxy
Please explain why you want or need to do this
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2018 04:37 AM
Hi Jason,
Reason why such setting is required as ISE is not supporting Azure AD & ISE is present on-premise at the site where WLC is there
Please throw some lights if we have Azure AD & ISE at site
Regards,
Pratik Gandhi
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2018 07:19 AM
Please do start this in a separate thread with appropriate title as this thread is over a year old. Some comments from our SME hslai
It’s up to the remote RADIUS server to use Azure AD as the ID store and ISE simply proxied to it. If the problem occurs between the remote RADIUS and Azure AD, that is beyond our scope of support.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

