- Cisco Community
- Technology and Support
- Data Center and Cloud
- Data Center Switches
- Re: Is this OSPF on top of vPC supported?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Is this OSPF on top of vPC supported?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-19-2021 06:44 AM - edited 02-21-2021 12:43 PM
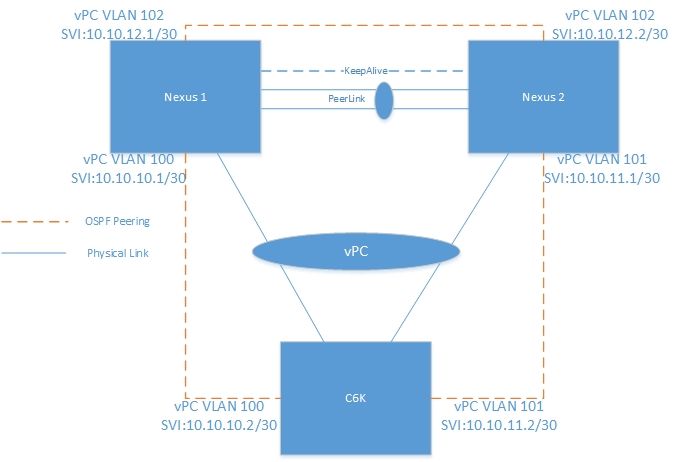
I think this attached topology is supported but I can not find any Cisco doc to reference it. But if it is not supported, please help me understand why.
Here is also the simple vPC configuration in place.
vpc domain 1
peer-keepalive destination 10.10.20.1 source 10.10.20.2
delay restore 180
peer-gateway
ip arp synchronize
Update/Clarify: this is a production setup running in one of my new customer environment. I want to understand the supportiveness, not trying to do this design for a deployment.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-19-2021 06:06 PM - edited 02-20-2021 05:58 AM
..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2021 05:39 AM
Take advantage of existing callings.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2021 06:00 AM - edited 02-20-2021 11:43 AM
....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2021 09:59 AM
This is from a very old CL presentation and looks like it refers to routing over vPC+ (vPC + Fabricpath).
This is the official supported topologies for routing over vPC is this: https://www.cisco.com/c/en/us/support/docs/ip/ip-routing/118997-technote-nexus-00.html
Cheers,
Sergiu
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2021 06:07 AM - edited 02-20-2021 11:43 AM
...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2021 09:57 AM
If your plan is to configure the SVI of a vpc vlan on only one vPC peer, that is not supported.
Best approach is to configure the SVI on all three devices, and bring up the ospf adjacency between all three (with L3 peer router enabled).
Have a look here as well for supported topologies: https://www.cisco.com/c/en/us/support/docs/ip/ip-routing/118997-technote-nexus-00.html
Stay safe,
Sergiu
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2021 01:44 PM
Thanks for the info and I am aware of the linked doc. But I do not think it covers my scenario...
I have three different vPC VLANs/SVIs, each is /30 P2P network, between C6K and Nexus 1; between C6K and Nexus 2; between Nexus 1 and Nexus 2. The OSPF peering is between these three pairs. I am not looking for peering with single vPC VLAN/SVI for the three devices. Hope this clarifies.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2021 02:36 PM - edited 02-21-2021 06:51 AM
...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2021 05:05 PM
Ok,
svi between two nexus peers any routing not support over L2
so only config this SVI over the vpc peer link
svi between how use different SVI between l3sw and nexus-a and l3sw and nexus-b ? I.e. how use different vlan for each connect?
simply use router port between l3sw and nexus-a/b.
or and I don’t see any doc. About this use SVI “select vlan not allow through vpc “. Between l3sw and nexus-a/b
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2021 07:04 AM - edited 02-21-2021 10:52 AM
You will need an SVI for each vPC vlan on each vPC peer for this to be supported, and you will need to enable layer3 peer-router on the vpc domain of each switch.
I am not sure of your design intentions, but it will not work as you have pictured due to the fact that first of all, you need an SVI to exist on both the vPC peers for vpc vlans if an SVI exists on any vPC peer, otherwise you will have a consistency check failure.
If you change the design to use /29 and create an SVI on each vPC peer for the vlans, as well as enabling layer3 peer-router feature in the vPC domain, the neighborships will form and your vPC should be healthy.
9K-1
9K-1(config-if)# sh ip ospf nei
OSPF Process ID 1 VRF default
Total number of neighbors: 5
Neighbor ID Pri State Up Time Address Interface
10.10.11.1 1 FULL/BDR 00:03:17 10.10.10.3 Vlan100
10.10.11.2 1 FULL/DR 00:03:17 10.10.10.2 Vlan100
10.10.11.1 1 FULL/BDR 00:00:48 10.10.12.2 Vlan102
10.10.11.1 1 FULL/BDR 00:03:12 10.10.11.1 Vlan101
10.10.11.2 1 FULL/DR 00:03:12 10.10.11.2 Vlan101
9K-1(config-if)# sh vpc br
Legend:
(*) - local vPC is down, forwarding via vPC peer-link
vPC domain id : 1
Peer status : peer adjacency formed ok
vPC keep-alive status : peer is alive
Configuration consistency status : success
Per-vlan consistency status : success
Type-2 consistency status : success
vPC role : primary
Number of vPCs configured : 1
Peer Gateway : Enabled
Dual-active excluded VLANs : -
Graceful Consistency Check : Enabled
Auto-recovery status : Disabled
Delay-restore status : Timer is off.(timeout = 180s)
Delay-restore SVI status : Timer is off.(timeout = 10s)
Operational Layer3 Peer-router : Enabled
Virtual-peerlink mode : Disabled
vPC Peer-link status
---------------------------------------------------------------------
id Port Status Active vlans
-- ---- ------ -------------------------------------------------
1 Po100 up 1,100-102
vPC status
----------------------------------------------------------------------------
Id Port Status Consistency Reason Active vlans
-- ------------ ------ ----------- ------ ---------------
1 Po1 up success success 1,100-102
9K-2
9K-2(config-if)# sh ip ospf nei
OSPF Process ID 1 VRF default
Total number of neighbors: 5
Neighbor ID Pri State Up Time Address Interface
10.10.10.1 1 FULL/DROTHER 00:04:15 10.10.11.3 Vlan101
10.10.11.2 1 FULL/DR 00:08:59 10.10.11.2 Vlan101
10.10.10.1 1 FULL/DR 00:01:51 10.10.12.1 Vlan102
10.10.10.1 1 FULL/DROTHER 00:04:21 10.10.10.1 Vlan100
10.10.11.2 1 FULL/DR 00:09:04 10.10.10.2 Vlan100
9K-2(config-if)# sh vpc br
Legend:
(*) - local vPC is down, forwarding via vPC peer-link
vPC domain id : 1
Peer status : peer adjacency formed ok
vPC keep-alive status : peer is alive
Configuration consistency status : success
Per-vlan consistency status : success
Type-2 consistency status : success
vPC role : secondary
Number of vPCs configured : 1
Peer Gateway : Enabled
Dual-active excluded VLANs : -
Graceful Consistency Check : Enabled
Auto-recovery status : Disabled
Delay-restore status : Timer is off.(timeout = 180s)
Delay-restore SVI status : Timer is off.(timeout = 10s)
Operational Layer3 Peer-router : Enabled
Virtual-peerlink mode : Disabled
vPC Peer-link status
---------------------------------------------------------------------
id Port Status Active vlans
-- ---- ------ -------------------------------------------------
1 Po100 up 1,100-102
vPC status
----------------------------------------------------------------------------
Id Port Status Consistency Reason Active vlans
-- ------------ ------ ----------- ------ ---------------
1 Po1 up success success 1,100-102
Please check "show vpc consistency-parameters vpc <vpc-num>" for the
consistency reason of down vpc and for type-2 consistency reasons for
any vpc.
VPC configuration
9K-2# sh run vpc
!Command: show running-config vpc
!Running configuration last done at: Sun Feb 21 15:00:22 2021
!Time: Sun Feb 21 15:03:10 2021
version 9.3(2) Bios:version 07.68
feature vpc
vpc domain 1
peer-keepalive destination 10.82.138.124
delay restore 180
peer-gateway
layer3 peer-router
ip arp synchronize
interface port-channel1
vpc 1
interface port-channel100
vpc peer-link
9K-2#
Let me know if you need any further clarification.
Edit: This reply was meant for the original poster. Replied to a comment by mistake.
RTP - DCRS TAC Engineer
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2021 07:45 AM
this is N5K not N9K so layer3 router not support
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2021 12:44 PM - edited 02-21-2021 12:45 PM
Thanks for the info. I should clarify, this is a production setup running in one of my new customer environment. I want to understand the supportiveness, not trying to do this design for a deployment. The N5K running does not support layer3 peer-router with the firmware.
The peering is done by three different VLAN SVIs, each is a /30 subnet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2021 07:37 AM
Hi @SIMMN
It does not cover your scenario because is not supported
That is the reason why I pointed you the link. Follow the recommended scenarios to avoid unexpected behavior in production. Unsupported simply means it was not tested enough by Cisco BU team or it did not passed all tests. And the problem with implementing an unsupported config/topology/etc is that everything might work fine for a while, but then BOOM an incident is happening few months later in your network. Then when you contact Cisco TAC, the feedback you will get is that this is unsupported and you will need to reconfigure everything.
Anyway, stick with supported config. If you do not want to use a /29 subnet with 3x SVIs on all devices, then go for dedicated routed ports.
Stay safe,
Sergiu
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2021 12:57 PM
...
Unsupported simply means it was not tested enough by Cisco BU team or it did not passed all tests. And the problem with implementing an unsupported config/topology/etc is that everything might work fine for a while, but then BOOM an incident is happening few months later in your network. Then when you contact Cisco TAC, the feedback you will get is that this is unsupported and you will need to reconfigure everything....
Thanks for the information. I do understand what the TAC supportiveness mean:) and appreciate the confirmation.
This is not a design I am trying to validate in community, then implement it in production...It is actually one of my new customer production environment. Due to the lack of "layer3 peer-router" support on N5K, they deployed this setup years ago...So far it has been running fine and hope never have to call TAC for any issue related.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide