- Cisco Community
- Technology and Support
- Collaboration
- IP Telephony and Phones
- Not able to view Backup devices on CUCM/Call manager
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-23-2018 12:50 PM - edited 03-17-2019 12:16 PM
Hi Guys,
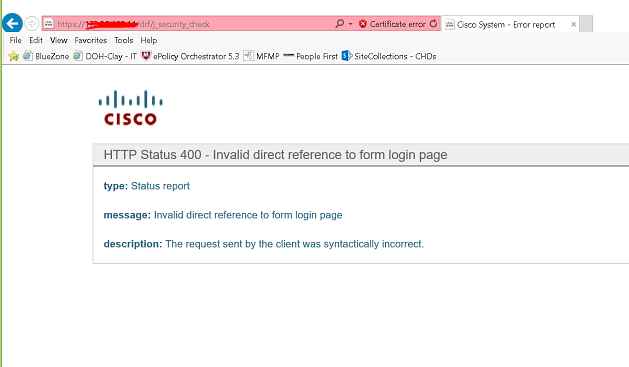
I am getting these error while trying to view Backup devices on call manager.
Any help please?
Solved! Go to Solution.
- Labels:
-
Other IP Telephony
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2018 03:35 PM
Complete these steps in the below order:
1) Log into Cisco Unified Communications Manager OS Administration page.
2) Choose Security > Certificate Management. The Certificate List window displays.
3) You can use the Find controls in order to filter the certificate list.
4) Click the ipsec.pem file, and then click Regenerate.
5) After the successful regeneration of the ipsec.pem file, Restart the Master Agent (MA)/Local Agent (LA).
The IPsec certificate is primarily used for DRS, Secure SIP profiles, CTL Client, and secure connections to gateways. If the IPsec certificate is renewed, reset DRF Master and DRF Local on the publisher AND DRF local on the subscribers. Restarting these will restart the DRS feature (DRS is used for backups and restoring for backup).
If this doesn't help you might want to consider a reboot of the server, the uptime is 180+ . I've seen issues popping up for some environments with that much uptime.
Please rate if you find this helpful.
Regards,
Aeby
Please rate if you find this helpful.
Regards,
Aeby
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-23-2018 10:36 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-23-2018 11:53 PM
Hi,
Firstly, Check for NTP server reachability from CUCM. Secondly, try restarting Cisco DRF Master and Local in PUB.
regds,
aman
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2018 01:13 AM
Hi,
I tried to use different browser, restarted DRF and TOMCAT. Got the NTP fixed still the same issue.
Thanks,
Muk
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2018 02:40 PM
Hi @voipeee,
you are using a Linux OS account (used by OS Admin and DRS) ... are you able to log in the OS Admin with no problem?
Best regards,
Marcelo Morais
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2018 05:33 AM
Hi @Marcelo Morais,
Yes, everything works fine. Even I am able to login to Admin,OS as well as DRS page. But when I click Backup devices nothing happens.
I thing this problem started after I regenerated few certificates before sometime however, I am not sure about this. And I regenerated Cisco Tomcat and restarted the service after that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2018 03:35 PM
Complete these steps in the below order:
1) Log into Cisco Unified Communications Manager OS Administration page.
2) Choose Security > Certificate Management. The Certificate List window displays.
3) You can use the Find controls in order to filter the certificate list.
4) Click the ipsec.pem file, and then click Regenerate.
5) After the successful regeneration of the ipsec.pem file, Restart the Master Agent (MA)/Local Agent (LA).
The IPsec certificate is primarily used for DRS, Secure SIP profiles, CTL Client, and secure connections to gateways. If the IPsec certificate is renewed, reset DRF Master and DRF Local on the publisher AND DRF local on the subscribers. Restarting these will restart the DRS feature (DRS is used for backups and restoring for backup).
If this doesn't help you might want to consider a reboot of the server, the uptime is 180+ . I've seen issues popping up for some environments with that much uptime.
Please rate if you find this helpful.
Regards,
Aeby
Please rate if you find this helpful.
Regards,
Aeby
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2018 12:45 AM
Hi,
In addition to what Vinod has mentioned, are the IP addresses of sftp created under Backup devices reachable from CUCM?
regds,
aman
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2018 05:38 AM
Hi @Aman Soi,
Thanks but I think it has nothing to do with the reachable because even if I have to add the devices I have to go to the same page.
Thanks,
Muk
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2018 02:11 AM
Hi,
I was referring to Backup devices if already created in CUCM.
Good the issue got resolved.
regds,
aman
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2018 05:36 AM
Hi @Aeby Vinod,
I agree with you and this might be the case. I will update you about the status.
Thanks in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2018 06:28 AM
Hi @Aeby Vinod,
The ipsec certificate is valid. I have pasted here certificate along with the expiry date. Thanks for your help.
| CallManager 02/08/2023 Self-signed certificate generated by system |
| CallManager-ECDSA 08/19/2022 Self-signed certificate generated by system |
| CallManager-trust CAPF-16f3496d Self-signed RSA CAPF 12/16/2016 |
| CallManager-trust Cisco_Manufacturing_CA_SHA2 CA-signed RSA Cisco_Manufacturing_CA_SHA2 Cisco_Root_CA_M2 11/12/2037 |
| CallManager-trust Cisco_Root_CA_M2 Self-signed RSA Cisco_Root_CA_M2 Cisco_Root_CA_M2 11/12/2037 |
| CallManager-trust CAPF-d201ea8d Self-signed RSA CAPF-d201ea8d CAPF-d201ea8d 02/08/2023 |
| CallManager-trust Cisco_Manufacturing_CA CA-signed RSA Cisco_Manufacturing_CA Cisco_Root_CA_2048 05/14/2029 |
| CallManager-trust 02/08/2023 Trust Certificate |
| CallManager-trust CAPF-962bd1bb Self-signed RSA CAPF-962bd1bb CAPF-962bd1bb 03/26/2018 |
| CallManager-trust CAPF-49e87588 Self-signed RSA CAPF-49e87588 CAPF-49e87588 12/16/2016 Trust Certificate |
| CallManager-trust 12/16/2016 Trust Certificate |
| CallManager-trust Cisco_Root_CA_2048 Self-signed RSA Cisco_Root_CA_2048 Cisco_Root_CA_2048 05/14/2029 |
| CallManager-trust CAP-RTP-001 Self-signed RSA CAP-RTP-001 CAP-RTP-001 02/06/2023 |
| CallManager-trust CAPF-0aa24f9a Self-signed RSA CAPF-0aa24f9a CAPF-0aa24f9a 02/08/2023 Trust Certificate |
| CallManager-trust ACT2_SUDI_CA CA-signed RSA ACT2_SUDI_CA Cisco_Root_CA_2048 05/14/2029 |
| CallManager-trust CAP-RTP-002 Self-signed RSA CAP-RTP-002 CAP-RTP-002 10/10/2023 |
| CallManager-trust CAPF-1ddfa6e0 Self-signed RSA CAPF-1ddfa6e0 CAPF-1ddfa6e0 03/26/2018 Trust Certificate |
| CAPF CAPF-d201ea8d Self-signed RSA CAPF-d201ea8d 02/08/2023 Self-signed certificate generated by system |
| CAPF-trust CAPF-16f3496d Self-signed RSA CAPF-16f3496d CAPF-16f3496d 12/16/2016 |
| CAPF-trust Cisco_Manufacturing_CA_SHA2 CA-signed RSA Cisco_Manufacturing_CA_SHA2 Cisco_Root_CA_M2 11/12/2037 |
| CAPF-trust Cisco_Root_CA_M2 Self-signed RSA Cisco_Root_CA_M2 Cisco_Root_CA_M2 11/12/2037 |
| CAPF-trust CAPF-d201ea8d Self-signed RSA CAPF-d201ea8d CAPF-d201ea8d 02/08/2023 |
| CAPF-trust Cisco_Manufacturing_CA CA-signed RSA Cisco_Manufacturing_CA Cisco_Root_CA_2048 05/14/2029 |
| CAPF-trust CAPF-962bd1bb Self-signed RSA CAPF-962bd1bb CAPF-962bd1bb 03/26/2018 |
| CAPF-trust Cisco_Root_CA_2048 Self-signed RSA Cisco_Root_CA_2048 Cisco_Root_CA_2048 05/14/2029 |
| CAPF-trust CAP-RTP-001 Self-signed RSA CAP-RTP-001 CAP-RTP-001 02/06/2023 |
| CAPF-trust ACT2_SUDI_CA CA-signed RSA ACT2_SUDI_CA Cisco_Root_CA_2048 05/14/2029 |
| CAPF-trust CAP-RTP-002 Self-signed RSA CAP-RTP-002 CAP-RTP-002 10/10/2023 |
| ipsec 02/08/2023 Self-signed certificate generated by system |
| ipsec-trust 02/08/2023 Trust Certificate |
| ITLRecovery 08/15/2037 Self-signed certificate generated by system |
| tomcat 02/08/2023 Self-signed certificate generated by system |
| tomcat-ECDSA 08/19/2022 Self-signed certificate generated by system |
| tomcat-trust 08/19/2022 Trust Certificate |
| tomcat-trust 08/19/2022 Trust Certificate |
| tomcat-trust 09/26/2022 Trust Certificate |
| tomcat-trust 02/08/2023 Trust Certificate |
| tomcat-trust 09/25/2022 Trust Certificate |
| tomcat-trust 02/08/2023 Trust Certificate |
| tomcat-trust VeriSign_Class_3_Secure_Server_CA_-_G3 CA-signed RSA VeriSign_Class_3_Secure_Server_CA_-_G3 VeriSign_Class_3_Public_Primary_Certification_Authority_-_G5 02/07/2020 Trust Certificate |
| tomcat-trust 09/25/2022 Trust Certificate |
| tomcat-trust 09/26/2022 Trust Certificate |
| TVS fl.us 12/13/2016 |
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2018 01:19 PM
Hey Abey,
This worked for me. Basically I regenerated this ipsec before few days and it displayed to restart DRS M/A however, this is out of mind now. Thank you so much for your help! I really appreciate.
Thanks,
Muk
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide