- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2020 11:01 AM
Hello Team,
I m looking for an option enable AAA Radius in ISE for NAD both switches and wireless controller.
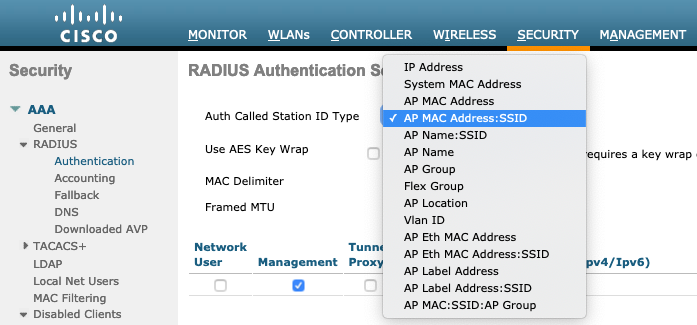
Currently, Wireless clients authenticating in ISE Radius Server, calling station id is AP MAC address SSID
i added network device ( wireless controller ) in ISE NAD Group and created a Authentication policy login via AD user ID and Authorization policy but no Radius request hitting at ISE end.
Question here, should i make change in called station ID from AP MAC address SSID in Wireless controller ? does it affect for wireless client users if i made change in Auth called station ID type ?
what Auth called station ID should i use to authenticate and Authorization for both wireless client and Wireless NAD via ISE Radius..
Thanks in advance .
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2020 02:22 PM
Sounds like you have a RADIUS configuration problem. See these guides for AAA configuration:
- ISE+9800: ISE and Catalyst 9800 Series Integration Guide
- ISE+AireOS: AireOS WLC configuration for ISE
Wireless controllers offer many options for the RADIUS Called-Station-ID:
You said you are using AP MAC address:SSID which is a perfectly fine. It is your choice depending on how you might want to use this information in your ISE Authentication and Authorization policies. This allows you to match the SSID in your Authorization Policy to provide the appropriate level of access for that wireless service (Guest vs Corporate vs BYOD, etc.) with a rule like:
| Status | Rule Name | Conditions | Profiles | Security Groups | Hits | Actions | ||
|---|---|---|---|---|---|---|---|---|
| ✔ | Guest_Wireless |
|
Internet_Only | Guest | 0 | ⚙ |
If you then change your WLC's Called-Station-ID to something that did not end with :SSID then you affect your authorization policy matching with potentially bad affects.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2020 02:23 PM
If you're not seeing any RADIUS traffic in ISE from the Wireless controller, then the problem could also be elsewhere. E.g. if you're WLAN is configured for 802.1X (or MAB or iPSK) then of course you have to specify your RADIUS servers.
1) Are the IP addresses of the RADIUS server correct? Can you ping ISE from the WLC CLI?
2) Are the RADIUS shared secrets matching on WLC and ISE?
3) What does your ISE LiveLog look like? No activity at all? Then I would run a tcpdump on that ISE node to see if anything is coming in.
The Called-Station ID is correct for your needs. The SSID is very useful in Authorization Policies if you need to go down to that granular level.
Clients are not affected by this change made at the RADIUS level (of course as long as the RADIUS flow still works as expected and completes as expected - but the format of individual attributes is not visible to the clients.)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-15-2020
10:21 AM
- last edited on
03-09-2022
11:04 PM
by
smallbusiness
![]()
Hello Arne,
you're WLAN is configured for 802.1X (or MAB or iPSK) then of course you have to specify your RADIUS servers. - WLAN is configured for 802.1X and wireless client able to authenticate sucessfully
1) Are the IP addresses of the RADIUS server correct? Can you ping ISE from the WLC CLI? - Yes ISE Radius IP rechable
2) Are the RADIUS shared secrets matching on WLC and ISE? yes its matching
My question here, what calling station id should i set on Authentication and Authorization under Security to login into wireless controller via Radius ISE using AD credential,
already 802.1X client using AP MAC SSID Attriubuite. How do i achieve login into Wireless controller via AD account,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-15-2020 07:40 PM
Since you are not seeing the Login authentication request from WLC on ISE, I believe that you have not checked the Management checkbox under the Radius authentication server.
Regarding the attribute that you can use as a condition in the authorization policy, use Radius·Service-Type EQUALS Outbound along with WLC IP address and login user AD group membership instead of using the calling station ID attribute.
Now you can create 3 different “Authorization Profiles” under “Policy->Policy Elements -> Results” section with different RADIUS attribute values:
For full administrative access you have to choose”Service-Type” Radius Attribute setting to “Administrative“.
For the Read-Only user, this setting should be set to “NAS-prompt”
For Lobby Ambassador it should be set to “Callback Administrative ”
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2020 02:22 PM
Sounds like you have a RADIUS configuration problem. See these guides for AAA configuration:
- ISE+9800: ISE and Catalyst 9800 Series Integration Guide
- ISE+AireOS: AireOS WLC configuration for ISE
Wireless controllers offer many options for the RADIUS Called-Station-ID:
You said you are using AP MAC address:SSID which is a perfectly fine. It is your choice depending on how you might want to use this information in your ISE Authentication and Authorization policies. This allows you to match the SSID in your Authorization Policy to provide the appropriate level of access for that wireless service (Guest vs Corporate vs BYOD, etc.) with a rule like:
| Status | Rule Name | Conditions | Profiles | Security Groups | Hits | Actions | ||
|---|---|---|---|---|---|---|---|---|
| ✔ | Guest_Wireless |
|
Internet_Only | Guest | 0 | ⚙ |
If you then change your WLC's Called-Station-ID to something that did not end with :SSID then you affect your authorization policy matching with potentially bad affects.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide