Resolved! Can we re-image SNS-3595 to ISE PIC ?
I have a router serving as a l2tp server. Clients connect to my router through internet and the authentication procedure is carried out by AAA (ISE 2.4 - Radius) server. The AAA is joined to a domain controller for the procedure. Clients can connect ...
Hello, I have tried to import 508 mac addresses to identity group. Even though I got a message that 508 were imported successfully I could only see 382. I was trying several times with the same result. I reduced amount of mac addresses to 200 in the ...
Hello,We want to implement the following guest flow in our organisation: 1. Guest uses self registration option to create an account 2. The request goes for approval to sponsor 1 3. Once Sponsor 1 approves the request, it must go for app...
Hi Guys, My customer would like to transfer ISE license from current 3395 node to a new ISE node.I have the procedures but just wondering how long would it takes to transfer the license?Would there be any downtime?If so, what is the best way to avoi...
Dear Experts,My customer’s requirement is the L2TP VPDN.They want to deploy a Radius server behind the LAC (L2TP Access Concentrator), which is used to return the LNS (L2TP Network Server) address to the LAC, when L2TP client initiates the Dial-in pr...
I am receiving the following error when trying to use the user's certificates with EAP chaining. ERROR:No valid certificates available. Please insert a smart card or install a valid certificate. I am able to use the machine certificate with EAP chain...
We have a AD domain added to ISE with two sub-organizations, say orgA and orgB - these are the two OU's. We want to use ISE to match computer objects from only a single OU (orgB). So for example we have Domain Computers AD group, but the objects in t...
Hi Guys, i want ISE install on VMware for POC (more then 100 users). but i am not to able to select the right image from cisco software site.can some body tell me which is the image should i download from cisco software portal as there are so many im...
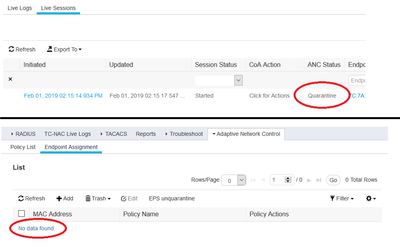
How do you unquarantine an endpoint once FMC has instructed ISE to quarantine it? Manually entering the MAC address under 'Operations->Adaptive Network Control -> Endpoints -> EPS Unquarantine' doesn't do anything...it's also confusing because the en...
How can I view AAA local logs in ISE which are older than 30 days. “Live Logs” can go “Last 24 Hours” and under reports you can go back 30 days.We are using ISE 2.4 and the retention is set to 200 days, but I don't know how to access records older th...
I'm trying to deploy ldap authentication (MS AD) for router vty login. I used manual like this - http://www.cisco.com/en/US/docs/ios-xml/ios/sec_usr_ldap/configuration/15-2mt/sec_conf_ldap.htmlBut my scenario was unluckyMy config is..._____aaa new-mo...
Hi, I am trying to troubleshoot an SNMP issue with ISE where a secondary admin node has stopped responding to the SNMP queries. I have verified from TCPdump that the SNMP request is coming to the ISE but it is not responding back. I enabled SNMP de...
Hello Everyone I've been checking the IBNS 2.0 supported Switch page, which only states Catalyst Switches but no word of any industrial switch support. So we are asking ourself if IBNS 2.0 is supported on the IE3000/4000 Series Switches.Has anyone tr...
How to import netwok devices using REST API or Python or any other scripts? We want to automate the import process as everyday there is some network device addition/modification/deletion.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
| Subject | Author | Posted |
|---|---|---|
| 01-20-2026 04:53 AM | ||
| 01-14-2026 05:54 AM | ||
| 01-11-2026 01:46 AM | ||
| 01-08-2026 06:15 AM | ||
| 11-26-2025 07:27 AM |
| User | Count |
|---|---|
| 6 | |
| 3 | |
| 1 | |
| 1 | |
| 1 |