- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2020 08:19 AM
I'm pretty sure the answer to this is no, but I'd like to check just in case there's a workaround.
Is it possible for the management interface to be shared with the SFR module, so I can manage the ASA via SSH / ASDM via an IP on the management interface, and have the SFR configured and running on the same subnet?
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2020 11:24 AM
Yes - that's the recommended design. Both the ASA and the sfr module share the physical management interface. They have different IP addresses on the same subnet. Think of them as VMs on the same host (rough analogy).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2020 11:24 AM
Yes - that's the recommended design. Both the ASA and the sfr module share the physical management interface. They have different IP addresses on the same subnet. Think of them as VMs on the same host (rough analogy).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2020 11:22 PM
Thanks Marvin,
If that's the recommended design why does all the documentation I've found / read imply that the two must be on separate interfaces?
Either way I'm happy I don't have to burn up an interface to utilise the SFR module.
Cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-14-2020 12:04 PM
What that document is stating is that you cannot set the management1/1 ASA IP to the same subnet that is already configured on the inside interface. This is because the ASA will not allow two interfaces with an IP on the same subnet. You can however set the same subnet on the FTD management1/1 interface as this is considered to be a seperate system from the ASA. If you set a subnet for both the ASA and FTD management1/1 interface that is seperate from a subnet that already exists on the ASA system (and do routing on a L3 switch for example) then you can have an IP for both ASA and FTD management1/1 interface.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-14-2020 11:18 PM
Just so. +5 :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-15-2020 03:28 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2020 11:31 AM
The ASA and SFR module share the management interface. The IP subnet of both the ASA and SFR mgmt interface must be the same though.
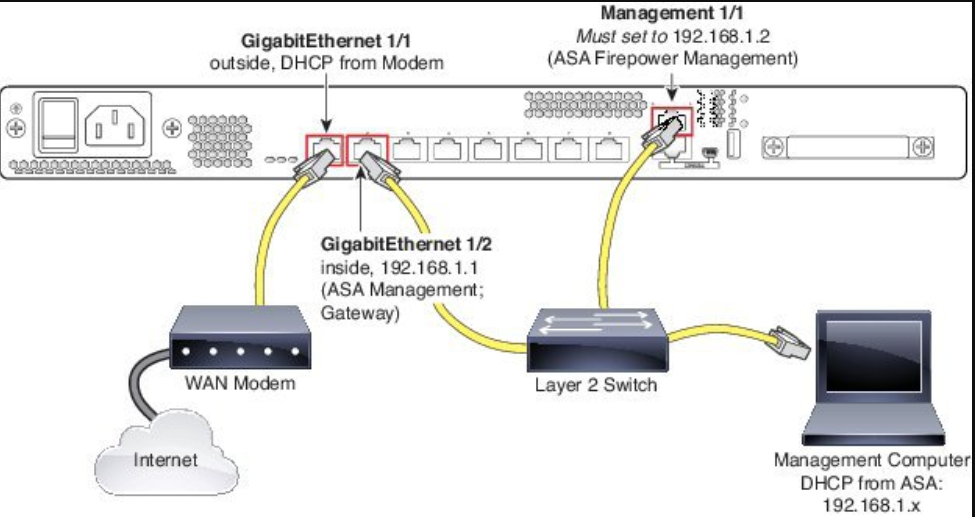
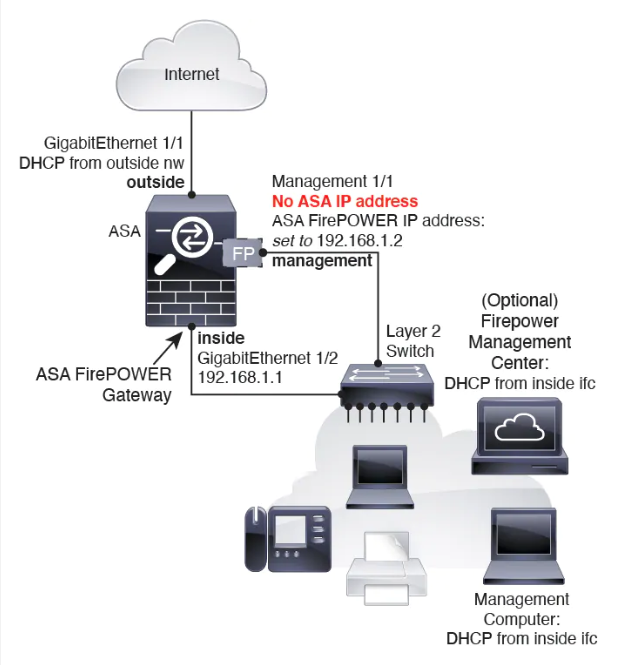
ASA 5506-X (9.6 and Earlier) through ASA 5555-X (Software Module) in Routed Mode
Note![]() : The ASA 5506-X and 5512-X do not support the FirePOWER module in 9.10 and later.
: The ASA 5506-X and 5512-X do not support the FirePOWER module in 9.10 and later.
These models run the ASA FirePOWER module as a software module, and the ASA FirePOWER module shares the Management 0/0 or Management 1/1 interface (depending on your model) with the ASA.
All management traffic to and from the ASA FirePOWER module must enter and exit the Management interface. The ASA FirePOWER module also needs Internet access. Management traffic cannot pass through the ASA over the backplane; therefore you need to physically cable the management interface to an ASA interface to reach the Internet.
If you do not configure a name and IP address in the ASA configuration for Management, then the interface belongs exclusively to the module. In this case, the Management interface is not a regular ASA interface, and you can:
1.![]() Configure the ASA FirePOWER IP address to be on the same network as a regular ASA data interface.
Configure the ASA FirePOWER IP address to be on the same network as a regular ASA data interface.
2.![]() Specify the data interface as the ASA FirePOWER gateway.
Specify the data interface as the ASA FirePOWER gateway.
3.![]() Directly connect the Management interface to the data interface (using a Layer2 switch).
Directly connect the Management interface to the data interface (using a Layer2 switch).
https://www.cisco.com/c/en/us/td/docs/security/asa/quick_start/sfr/firepower-qsg.html
Please remember to select a correct answer and rate helpful posts