- Cisco Community
- Technology and Support
- Networking
- Routing
- ACL Trouble
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2020 12:45 AM
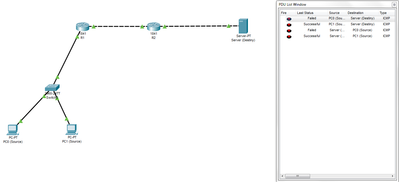
Hello there please help me, I'm learning about ACL and using the standard in the trials that I do. I think it works but it's different from what I expected, I want the server to ping the client but the client can't ping the server and what I get is that the server and client won't ping each other. Anyone can tell me what's wrong, I'm very confused. This is the topology that I made, please check.
Solved! Go to Solution.
- Labels:
-
Routing Protocols
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2020 01:44 AM
Hello,
you could configure CBAC (Context Based Access Control) on R2. The config would look like below (important parts marked in bold). The revised .pkt file is attached.
Building configuration...
Current configuration : 827 bytes
!
version 12.4
no service timestamps log datetime msec
no service timestamps debug datetime msec
no service password-encryption
!
hostname Router
!
ip cef
no ipv6 cef
!
ip inspect name ICMP icmp timeout 10
spanning-tree mode pvst
!
interface FastEthernet0/0
ip address 192.168.2.1 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet0/1
ip address 12.12.12.2 255.255.255.252
ip access-group BLOCK_ALL in
ip inspect ICMP out
duplex auto
speed auto
!
interface Vlan1
no ip address
shutdown
!
ip classless
ip route 192.168.1.0 255.255.255.0 12.12.12.1
!
ip flow-export version 9
!
ip access-list extended BLOCK_ALL
deny ip any any
!
line con 0
!
line aux 0
!
line vty 0 4
login
!
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2020 01:32 AM
i do not have packet tracer to test your Zip file.
you can use established syntax for who intiate the connection
Look at the example :
Example: Allowing SMTP E-mail and Established TCP Connections
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2020 01:44 AM
Hello,
you could configure CBAC (Context Based Access Control) on R2. The config would look like below (important parts marked in bold). The revised .pkt file is attached.
Building configuration...
Current configuration : 827 bytes
!
version 12.4
no service timestamps log datetime msec
no service timestamps debug datetime msec
no service password-encryption
!
hostname Router
!
ip cef
no ipv6 cef
!
ip inspect name ICMP icmp timeout 10
spanning-tree mode pvst
!
interface FastEthernet0/0
ip address 192.168.2.1 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet0/1
ip address 12.12.12.2 255.255.255.252
ip access-group BLOCK_ALL in
ip inspect ICMP out
duplex auto
speed auto
!
interface Vlan1
no ip address
shutdown
!
ip classless
ip route 192.168.1.0 255.255.255.0 12.12.12.1
!
ip flow-export version 9
!
ip access-list extended BLOCK_ALL
deny ip any any
!
line con 0
!
line aux 0
!
line vty 0 4
login
!
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2020 02:19 AM
Cam you give me ScreenShots Sir?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2020 02:32 AM
Thank you, sir, for your help
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide