- Cisco Community
- Technology and Support
- Networking
- Routing
- You can use the interface IP
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco ASA 5505. Access to DMZ from outside network
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2017 06:33 AM - edited 03-05-2019 08:34 AM
Hello all,
I'm writing my bachelor thesis and have to configure Cisco Asa Appliance. My network is more complicated but for this question it's better to look like this:
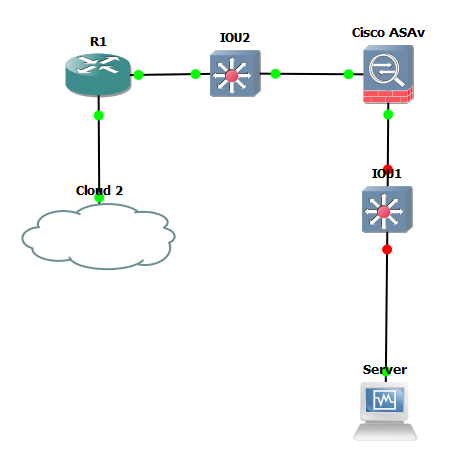
Server is in inside DMZ network. I want asa to translate outside ip address on 80 port to server at 80. I followed this tutorial: http://www.cisco.com/c/en/us/support/docs/security/asa-5500-x-series-next-generation-firewalls/115904-asa-config-dmz-00.html
First, I don't know is it possible to configure it as I want if outside interface is dhcp client? If so please tell me how, because from this tutorial it looks like it was impossible.
In the first part of tutorial they set up outside protocol and then in dmz part configure it like this:
object network webserver-external-ip
host 198.51.100.101
!
object network webserver
host 192.168.1.100
nat (dmz,outside) static webserver-external-ip service tcp www www
I don't know where is this 198.51.100.101 address from? Mind you outside ip address is set up dynamically. I thought that maybe it's just another configuration with static outside ip. But when I set it up like this and tried to configure with this nat command an error occured:
ERROR: Address 198.51.100.101 overlaps with outside2 interface address.
ERROR: NAT Policy is not downloaded
I will be very gratefull if someone could help me with this issue and maybe get this issue through to me.
- Labels:
-
Other Routing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2017 07:31 AM
The 198.51.100.101 IP is just a spare IP in the subnet of public IPs.
When you connect to an ISP they usually give you a number of IPs, one of which you assign to an interface on the ASA and the rest you can use for NAT statements.
It looks from the error message that you have assigned that IP to another interface. You do not need to do that, just use it in your NAT statement.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2017 01:55 PM
Jon, thank you for your answer! :)
I'm new in the asa world and I'm a bit confused now. So that means I have for ex. 2 addresses given form ISP and one is used to interface address and the second for nat? I tried to find some studies about this topic but I couldn't :(
I thought that I can have one static IP address on interface and just forward the network traffic from this interface address on port 80 to server in dmz using nat (interface address = translated address).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2017 02:09 AM
You can use the interface IP for NAT if you want to and that would work fine as long as you specify the ports.
It all depends on the number of public IPs you receive from the ISP. So a quite common scenario is one where they give part of a class C eg. a /29 and you are free to use these however you want..
There are no hard and fast rules really but usually the interface IP is used for translating the internal user IPs as they access the internet and then, assuming you have other IPs, these are used for static NATs for servers etc. you want to give access to from the internet.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2017 03:22 AM
But I as I wrote when I want to use the same IP for interface and port 80 translation an error occured.
The problem is also with configuration with 2 addresses. Now I have 10.0.0.31 on interface and 10.0.0.32 for NAT translate. I can ping from outside 10.0.0.31 but *.32 not. I really don't understand the idea of ip address which is not assigned to any interface. How is that possible to make it visible in network. Or maybe I don't understand it at all :)
P.S Packet tracer simulator is good: asa translated 10.0.0.32 to server address. But I can't just get it from outside network.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2017 03:50 AM
In your original configuration try this -
"nat (dmz,outside) static interface service tcp www www"
and see if that works.
As for IPs that are not assigned to any interfaces. When you configure a NAT statement with an IP that is not assigned to an interface the ASA in effect takes ownership of the IP.
All that then matters is that traffic for that IP ends up at the ASA. How this happens is either with the ASA answering an arp request for that IP or the traffic for that IP simply being routed to the ASA depending on the actual setup in terms of IP addressing.
Hope that makes sense, feel free to ask further.
Jon
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
