- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: DMVPN ,EIGRP And IPsec with CA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
DMVPN ,EIGRP And IPsec with CA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2019 09:15 AM - edited 03-05-2019 11:11 AM
Dear All,
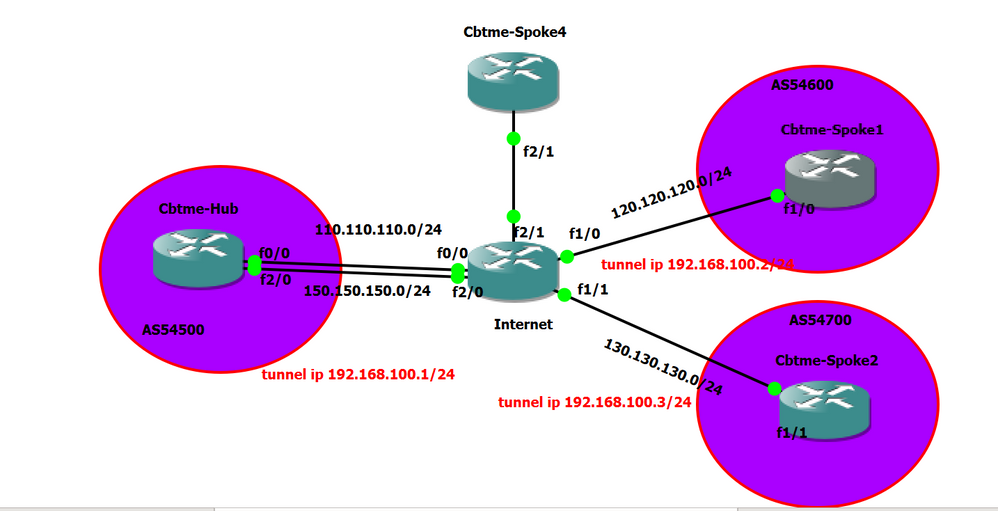
I would request to help me to fix DMVPN error.I try to configure DMVPN with ipsec .before I apply ipsec profile to DMVPN tunnel ,DMVPN is working.after applying ipsec profile ,DMVPN is down.why I don't know.I can say Ipsec configuration correct because it is work propely site to site VPN in operation.But this configuration is doesn't work with DMVPN.I don't know why? Please help me.
=~=~=~=~=~=~=~=~=~=~=~= PuTTY log 2019.01.20 00:33:07 =~=~=~=~=~=~=~=~=~=~=~=
*Jan 20 00:33:02.395: %CRYPTO-4-RECVD_PKT_NOT_IPSEC: Rec'd packet not an IPSEC packet. (ip) vrf/dest_addr= /110.110.110.1, src_addr= 130.130.130.1, prot= 47
Cbtme-Hub(config-if)#sh run
end
Cbtme-Hub#len
Cbtme-Hub#len
*Jan 20 00:33:13.323: %SYS-5-CONFIG_I: Configured from console by console
Cbtme-Hub#len
termi
Cbtme-Hub#terminal len
Cbtme-Hub#terminal length 0
Cbtme-Hub#sh run
Building configuration...
Current configuration : 9508 bytes
!
! Last configuration change at 00:33:13 UTC Sun Jan 20 2019
!
version 15.2
service timestamps debug datetime msec
service timestamps log datetime msec
!
hostname Cbtme-Hub
!
boot-start-marker
boot-end-marker
!
!
!
no aaa new-model
no ip icmp rate-limit unreachable
ip cef
!
!
!
!
!
!
no ip domain lookup
ip domain name crypto.local
no ipv6 cef
!
!
multilink bundle-name authenticated
!
crypto pki trustpoint my-ca
enrollment terminal
serial-number none
fqdn cbtme-hub.crypto.local
ip-address none
subject-name cn=cbtme-hub.crypto.local
revocation-check none
!
!
crypto pki certificate chain my-ca
certificate 3C000000168AF8583CBDCFD97E000000000016
30820583 3082046B A0030201 0202133C 00000016 8AF8583C BDCFD97E 00000000
0016300D 06092A86 4886F70D 01010B05 00304B31 15301306 0A099226 8993F22C
64011916 056C6F63 616C3116 3014060A 09922689 93F22C64 01191606 63727970
746F311A 30180603 55040313 11637279 70746F2D 53554243 412D4341 2D31301E
170D3139 30313139 31363135 35395A17 0D323031 31323930 39313833 305A3021
311F301D 06035504 03131663 62746D65 2D687562 2E637279 70746F2E 6C6F6361
6C308201 22300D06 092A8648 86F70D01 01010500 0382010F 00308201 0A028201
0100CCB4 CD4686C9 64BF82D3 D43F09D9 13CA4EE6 A119D003 91333E6F 9F227516
636817EC 818787B2 AFDF1DC4 8758F227 06073797 0F0053AD F0857EB3 99A1F434
FCC8290F 111A7CD3 68480BE1 5643522E BC28D137 9B70C99C 1648EF92 208D4876
1428598B BDAC373C 4A9435E7 59304E52 7B1BA07A A6267129 364B2ED4 D5D4E9AF
5BCE236A 3FE2F32D C3CE5D99 7FEB3643 B08C301C 82F71333 950A76ED 9F1749E7
7531734B 3C252BE9 6D191148 0D947BBD 282D199C 9ECC9DC4 1DC11D76 0AD70432
D3B2EC71 B61AFBEB 81700DB0 9CC92FF4 499376B2 DFD8687F 5B6E6D8D 526E98EE
0F0FDC53 3120C2E3 672DA207 C70E6B68 FCE09C79 02394335 5259B259 127573F2
063B0203 010001A3 82028830 82028430 0E060355 1D0F0101 FF040403 0205A030
1D060355 1D0E0416 0414D5F4 250CB031 74A99CA0 0B39E4A9 0BD548CF 0E82301F
0603551D 23041830 1680145A 5B753B27 2969744B F221001B 7A52CDC9 58765E30
81CE0603 551D1F04 81C63081 C33081C0 A081BDA0 81BA8681 B76C6461 703A2F2F
2F434E3D 63727970 746F2D53 55424341 2D43412D 312C434E 3D537562 43412C43
4E3D4344 502C434E 3D507562 6C696325 32304B65 79253230 53657276 69636573
2C434E3D 53657276 69636573 2C434E3D 436F6E66 69677572 6174696F 6E2C4443
3D637279 70746F2C 44433D6C 6F63616C 3F636572 74696669 63617465 5265766F
63617469 6F6E4C69 73743F62 6173653F 6F626A65 6374436C 6173733D 63524C44
69737472 69627574 696F6E50 6F696E74 3081C406 082B0601 05050701 010481B7
3081B430 81B10608 2B060105 05073002 8681A46C 6461703A 2F2F2F43 4E3D6372
7970746F 2D535542 43412D43 412D312C 434E3D41 49412C43 4E3D5075 626C6963
2532304B 65792532 30536572 76696365 732C434E 3D536572 76696365 732C434E
3D436F6E 66696775 72617469 6F6E2C44 433D6372 7970746F 2C44433D 6C6F6361
6C3F6341 43657274 69666963 6174653F 62617365 3F6F626A 65637443 6C617373
3D636572 74696669 63617469 6F6E4175 74686F72 69747930 3C06092B 06010401
82371507 042F302D 06252B06 01040182 371508C6 9D6A81EB 9E5184C5 8F3C82F7
E70482F1 DE7B813C 87FB9D35 F9F72102 01640201 04302706 03551D25 0420301E
06082B06 01050507 03060608 2B060105 05080202 06082B06 01050507 03023033
06092B06 01040182 37150A04 26302430 0A06082B 06010505 07030630 0A06082B
06010505 08020230 0A06082B 06010505 07030230 0D06092A 864886F7 0D01010B
05000382 01010078 38B2FEDF 15D36505 9DF4BBEA 45E808ED 3A3C498A 6A271604
2A86C908 8681EC3F DF597FA0 126785E4 D657D7A7 3ACAF40B DCB1698A B64B8995
CE254154 B4B60EDC 731E51E7 F91AF78B 4197C3F2 DF96E455 27251DD1 8C9AC426
DC9274EC 8088B62B 43B5EB51 C2AC7B78 FE21CE6B 18E77936 06426AB1 C6596B9B
00B598E7 D5B5818E 17EAFD16 1917BED9 CC98B4E6 ED0EBD25 CBD4CD9C 18B74F69
E1504FA9 56EDF9E0 21FFA552 982B6C3E 3AB44CE7 195EA185 E35AF71C DC3D877E
9871674E A0C875B0 72AD47FE 502F4E89 358335B8 ADAC41B8 F252F561 7DC93654
8A59EAA8 6C6196F3 2496D22E FB95C4A0 3BCDE38A 55FC55DA 1A29C5FB B6A296A3
057E3A5F FA7458
quit
certificate ca 540000000278F61229E46F3DDB000000000002
3082054D 30820435 A0030201 02021354 00000002 78F61229 E46F3DDB 00000000
0002300D 06092A86 4886F70D 01010B05 00304A31 15301306 0A099226 8993F22C
64011916 056C6F63 616C3116 3014060A 09922689 93F22C64 01191606 63727970
746F3119 30170603 55040313 10637279 70746F2D 524F4F54 43412D43 41301E17
0D313831 31323930 39303833 305A170D 32303131 32393039 31383330 5A304B31
15301306 0A099226 8993F22C 64011916 056C6F63 616C3116 3014060A 09922689
93F22C64 01191606 63727970 746F311A 30180603 55040313 11637279 70746F2D
53554243 412D4341 2D313082 0122300D 06092A86 4886F70D 01010105 00038201
0F003082 010A0282 010100BA 351C4BF6 9CCACBCF D34D9D1D A66D6ACD 97F50EFD
E5D04A86 665AFAF6 F8A38E41 4C9094B2 56983D88 0271E33E D88B5C2C 1BE1F3C5
0B071B2F 495C65DA 16F35FED 797B0083 6EFE0AFA 792C2FF8 ED68A7A3 FC023786
FC8E07E5 FBBF2F6D 6CA4DA10 B011967A 50721DB1 55417D3F 6D4D6EA6 3A6C5669
2C971388 02995D2F 90C58C42 0D693F64 47FA2182 50F3D37C 0C14A968 A6498963
FFCC24D9 AE68DF55 8404F5C7 4A628962 E46DA5BE 1610352A E0869FE1 3A426CD5
49C0EB70 90244D34 4834B7E4 45F803E0 ADB4291D CB033DF7 D50147E2 4C468624
6614E623 8A869EB6 9D5320FE BE8A0DDC 58F91AE9 37D397A7 8A7AA8BB 8B0BFC8A
61655720 B96B0464 8A4FA702 03010001 A3820229 30820225 30100609 2B060104
01823715 01040302 0100301D 0603551D 0E041604 145A5B75 3B272969 744BF221
001B7A52 CDC95876 5E301906 092B0601 04018237 1402040C 1E0A0053 00750062
00430041 300E0603 551D0F01 01FF0404 03020186 300F0603 551D1301 01FF0405
30030101 FF301F06 03551D23 04183016 8014EAE7 98FDF125 A1E58467 80EFFFC7
83928290 3CED3081 CE060355 1D1F0481 C63081C3 3081C0A0 81BDA081 BA8681B7
6C646170 3A2F2F2F 434E3D63 72797074 6F2D524F 4F544341 2D43412C 434E3D52
6F6F7443 412C434E 3D434450 2C434E3D 5075626C 69632532 304B6579 25323053
65727669 6365732C 434E3D53 65727669 6365732C 434E3D43 6F6E6669 67757261
74696F6E 2C44433D 63727970 746F2C44 433D6C6F 63616C3F 63657274 69666963
61746552 65766F63 6174696F 6E4C6973 743F6261 73653F6F 626A6563 74436C61
73733D63 524C4469 73747269 62757469 6F6E506F 696E7430 81C30608 2B060105
05070101 0481B630 81B33081 B006082B 06010505 07300286 81A36C64 61703A2F
2F2F434E 3D637279 70746F2D 524F4F54 43412D43 412C434E 3D414941 2C434E3D
5075626C 69632532 304B6579 25323053 65727669 6365732C 434E3D53 65727669
6365732C 434E3D43 6F6E6669 67757261 74696F6E 2C44433D 63727970 746F2C44
433D6C6F 63616C3F 63414365 72746966 69636174 653F6261 73653F6F 626A6563
74436C61 73733D63 65727469 66696361 74696F6E 41757468 6F726974 79300D06
092A8648 86F70D01 010B0500 03820101 0035B7D1 A2D72FB8 6A87DA5E EF20D5FE
200B5502 298D2792 C0D21AD3 003A57DE C52FD774 9E24D28C AB7E9B06 114B1789
8668CF66 7ECDDC0B 3C62E120 EDD70912 77612379 104187A8 561C9410 06EBC267
22D5D4D3 C8F38806 6C10F16E 3F4F9370 FCFB7E1A 544C6382 C6D3FCFE 43EE4144
A137BF03 177C56D6 C22948E2 75062245 1A47A6B8 CDC04EA8 2A870010 F532EB9B
45FDE964 0AD5D8AE A4555293 314BB317 9ACC3361 46D0DF36 FA6EF533 F32FE149
75E08FEE 9372F000 87D0C012 3297696D 0E08A9E7 D93F4ED1 141C0D85 6A016720
3D0B82B0 757A25D9 60FCD394 8E6437F4 49175569 BD73A215 BAA1DFA5 DFD2A8C7
F79277D7 63755C50 B7BD3437 AFBB7BB1 14
quit
!
!
!
!
!
!
!
ip tcp synwait-time 5
!
!
crypto ikev2 proposal aes-cbc-256-proposal1
encryption aes-cbc-256
integrity sha256
group 14
!
crypto ikev2 policy policy
match address local 110.110.110.1
proposal aes-cbc-256-proposal1
!
!
crypto ikev2 profile profile
description IKEv2 profile
match identity remote address 120.120.120.2 255.255.255.255
identity local address 110.110.110.1
authentication remote rsa-sig
authentication local rsa-sig
pki trustpoin my-ca
!
!
!
crypto ipsec transform-set TS-ESP-AES-SHA esp-aes 256 esp-sha256-hmac
mode tunnel
!
crypto ipsec profile IPSecProfile
set transform-set TS-ESP-AES-SHA
set ikev2-profile profile
!
!
!
!
!
!
!
interface Loopback0
ip address 1.1.1.1 255.255.255.0
!
interface Loopback1
ip address 11.11.11.11 255.255.255.0
!
interface Tunnel0
ip address 192.168.200.1 255.255.255.0
no ip redirects
ip nhrp map multicast dynamic
ip nhrp network-id 200
shutdown
tunnel source 150.150.150.1
tunnel mode gre multipoint
tunnel key 1
!
interface Tunnel1
ip address 192.168.100.1 255.255.255.0
no ip redirects
ip mtu 1400
no ip split-horizon eigrp 10
ip nhrp map multicast dynamic
ip nhrp network-id 111
ip nhrp redirect
ip tcp adjust-mss 1360
tunnel source 110.110.110.1
tunnel mode gre multipoint
tunnel key 1
tunnel protection ipsec profile IPSecProfile
!
interface FastEthernet0/0
ip address 110.110.110.1 255.255.255.0
duplex full
!
interface FastEthernet1/0
no ip address
shutdown
speed auto
duplex auto
!
interface FastEthernet1/1
no ip address
shutdown
speed auto
duplex auto
!
interface FastEthernet2/0
ip address 150.150.150.1 255.255.255.0
speed auto
duplex auto
!
interface FastEthernet2/1
no ip address
shutdown
speed auto
duplex auto
!
!
router eigrp 10
network 1.1.1.0 0.0.0.255
network 11.11.11.0 0.0.0.255
network 192.168.100.1 0.0.0.0
!
router bgp 101
bgp log-neighbor-changes
neighbor 110.110.110.2 remote-as 100
neighbor 150.150.150.2 remote-as 100
!
ip forward-protocol nd
!
!
no ip http server
no ip http secure-server
!
!
!
!
control-plane
!
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
stopbits 1
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
stopbits 1
line vty 0 4
login
!
!
end
Cbtme-Hub#wr
Building configuration...
[OK]
Cbtme-Hub#
*Jan 20 00:34:03.835: %CRYPTO-4-RECVD_PKT_NOT_IPSEC: Rec'd packet not an IPSEC packet. (ip) vrf/dest_addr= /110.110.110.1, src_addr= 130.130.130.1, prot= 47
Cbtme-Hub#dm s do dmvp
Cbtme-Hub#do dmvpn
^
% Invalid input detected at '^' marker.
Cbtme-Hub#do sh dmvpn
^
% Invalid input detected at '^' marker.
Cbtme-Hub#sh dmvpn
Legend: Attrb --> S - Static, D - Dynamic, I - Incomplete
N - NATed, L - Local, X - No Socket
# Ent --> Number of NHRP entries with same NBMA peer
NHS Status: E --> Expecting Replies, R --> Responding, W --> Waiting
UpDn Time --> Up or Down Time for a Tunnel
==========================================================================
Cbtme-Hub#
- Labels:
-
Other Routers
-
Routing Protocols
-
WAN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-20-2019 10:48 AM
You aren't using FVRF, so you'd don't need to specifically configure anything. You'd use VRF's if you wanted a different routing table for the outside interface and another unique routing table for the inside network. Useful when the inside network needs to tunnel all traffic over the VPN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2019 03:45 AM - edited 01-21-2019 06:07 PM
Hi RJI,
Now DMVPN is work properly as you advice.but now i got the new problem. int DMVPN router i create new point to point tunnel and add other new IPSec profile.
So i have one point to point tunnel and one dmvpn tunnel ,and then two IPSec profile for each tunnel.
Let me know i can use different IPSec profile (one for point to point,one for DMVPN )? becaus now DMVPN tunnels is up and work properly but point to point tunnel is doesn't up. Sorry i don't know how attachment with file in message box.
This is point to point IPSec Profile:
crypto ikev2 proposal aes-cbc-256-proposal1
encryption aes-cbc-256
integrity sha256
group 14
crypto ikev2 policy policy
match address local 10.1.14.70
proposal aes-cbc-256-proposal1
crypto ikev2 profile profile
description IKEv2 profile
match identity remote address 10.1.14.80 255.255.255.255
identity local address 10.1.14.70
authentication local rsa-sig
authentication remote rsa-sig
pki trustpoint my-ca
!
This is DMVPN IPSec profile:
crypto pki certificate map CERT-MAP-DMVPN-IKEv2 10
subject-name co crypto.local
crypto ikev2 proposal IKEv2-PROPOSAL
encryption aes-cbc-256 aes-cbc-192 3des
integrity sha512 sha256 md5
group 14 5 2
crypto ikev2 policy IKEv2-POLICY
proposal IKEv2-PROPOSAL
crypto ikev2 profile DMVPN-ISAKMP-IKEv2
match certificate CERT-MAP-DMVPN-IKEv2
identity local dn
authentication local rsa-sig
authentication remote rsa-sig
pki trustpoint my-ca
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2019 07:46 AM
Hi,
Thanks for your help.now I got the confuse.I want to DMVPN fail over but I can search dual hub single ISP or dual ISP.I didn't see single hub dual ISP.I don't want to use vrf also.
So I would to know for my design
1.do I need to sperate nhrp id?
2.do I need to run two eigrp on single router.
3.how to do to go traffic on active link(I already configured 150.150.150.1 link is secondary link in gbp)
4.how to spoke know which hub tunnel is primary?
Please help
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2019 11:02 AM
Hi,
So on the spoke you can have 1 tunnel, same nhrp id, same eigrp AS, on the tunnel interface you would specify both hubs. You can either use an eigrp delay on the tunnel interface to prefer 1 tunnel over the other or alternatively use the priority command inconjunction with "max-connections 1" and therefore only 1 tunnel will be up, if that fails the other tunnel will come up.
interface Tunnel0
ip nhrp map multicast 1.1.1.1
ip nhrp map 10.5.0.1 1.1.1.1
ip nhrp map multicast 2.2.2.1
ip nhrp map 10.5.0.2 2.2.2.1
ip nhrp nhs 10.5.0.1 priority 1 cluster 1
ip nhrp nhs 10.5.0.2 priority 2 cluster 1
ip nhrp nhs cluster 1 max-connections 1
This post shows example of the failover I've described and will help you determine which tunnel is active/primary.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2019 03:03 PM
Hi ,
I am using single router now.
I have two ISP in one router(single).
I don't know how to configure for tunnel 2 in hub without using vrf.
Can I run one eigrp AS in hub?
Tunnel 2 should be nhrp client of tunnel 1(primary)?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2019 04:01 AM
I assume you have 2 ISP's on the hub only?
Any reason why you don't wish to use FVRF? When you have 2 ISP you would have a default route conflict, using FVRF resolves this issue. In this scenario, FVRF is the recommended solution and the most elegant. The FVRF is only used for the ISP interfaces, the inside interface is within the global routing table.
Alternatively you could use IP SLA to track the ISP-1 interface and/or internet reachability via ISP-1, if that goes down then using tracking will failover to ISP-2.
The spoke routers would be configured as my previous suggestion above, with 1 active hub and if connectivity is lost failover to the other.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2019 01:15 AM
Dear All,
I have still problem.my spoke run one dmvpn tunnel to DC1 and one point to point (ipsec) tunnel to DC2.In spoke router ,the both of tunnels ( dmvpn and ptp) are working and ipsec sa and ikev2 are up.In my DC 1 ,i run DMVPN tunnel and poinit to point tunnel to DC2 .now i got the problem in DC1.in my DC1 ,all DMVPN tunnel is up and working.but my Point to point tunnel to DC1 didn't up and not working.i use different IPsec policy and diffenent pofile but. it is same as my spoke site why i don't know my DC site is got the problem.In my DC i am running local preference and prepend.It will effect to my tunnel ?
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide