- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2017 11:56 PM - edited 03-05-2019 08:22 AM
Please see the attached layout:
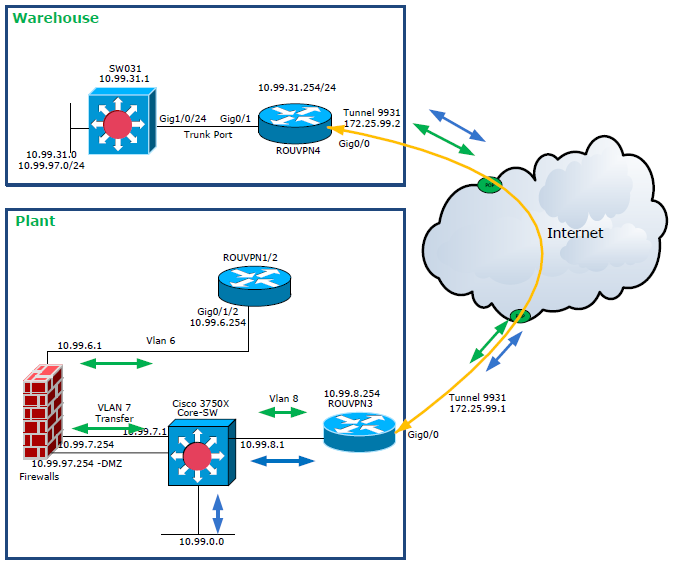
VLAN 97(DMZ) Default Gateway is on Firewall and i want allow whole subnet IP address(10.99.97.0/24) on warehouse via VPN but its not working.(cant ping from firewall.....traffic is not passing via FW)
Please provide me the guidance or solution to do it!!!
Thanks in advance
Solved! Go to Solution.
- Labels:
-
LAN Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2017 06:21 AM
All your incoming traffic to site Plant lands at router 3 and it has a default route to core switch 10.99.8.1. So you will need to configure an acl on the core switch and apply it to the interface that has 10.99.8.1 configured on it.
How many vlans/subnets are there that you don't want warehouse network to access? can you summarize them? because with summarization it would be easier to configure ACL unless you only have handful.
Basically you want network 10.99.31.x and 32/24 to have access to 10.99.97.0/24 and deny everything else.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2017 05:54 AM
ping 10.99.97.254 source 10.99.32.254. - This works
ping 10.99.21.254 source 10.99.32.254 - This doesn't work
What is 10.99.21.254?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-19-2017 01:46 AM
can anyone help on the issue!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-21-2017 11:51 AM
Hello,
Could probably use a little bit more information and configuration if possible. I also find this diagram a bit confusing. Is your LAN interface and DMZ Interface both connecting to the same Core switch? You generally have the DMZ off another firewall interface and completely separate from the LAN. Also, is this Core switch even a core switch? Based on the diagram, it looks to be more like an outside switch. Hard to tell where your DMZ is on your diagram.
Without a bit more information and clarity on the diagram, my only advice would be to double check your routing and access policies. Ensure your firewall sees 10.99.97.0/24 in its routing table and that there are no policies blocking that network.
Also, what type of firewall are you using? If you're using Cisco ASA, you can run a packet-tracer to get a little more information on what's happening.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2017 12:56 AM
Hi,
Thanks for reply.
Is your LAN interface and DMZ Interface both connecting to the same Core switch?
Yes LAN (VLAN7)and DMZ(VLAN 97) both are connecting to core switch. All VLAN have SVI configured on Core Switch except DMZ vlans(Default gateway is on Firewall).
Also, is this Core switch even a core switch?
Its a core switch. All edge switches are connected to it. All SVIs are configured here except DMZ.
what type of firewall are you using?
Palo Alto
Here is the config from each device.
Core Switch Configuration:
LAN:
interface GigabitEthernet0/24
description *** FW, Inside ***
switchport access vlan 7
switchport mode access
DMZ:
interface GigabitEthernet0/22
description *** DMZ ***
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 97
switchport mode trunk
Route:
ip route 0.0.0.0 0.0.0.0 10.99.7.254
ip route 10.99.31.0 255.255.255.0 10.99.8.254
ip route 10.99.97.0 255.255.255.0 10.99.8.254
ROUVPN3:
ip route 0.0.0.0 0.0.0.0 10.99.8.1
ip route 10.99.31.0 255.255.255.0 172.25.99.2
ip route 10.99.97.0 255.255.255.0 172.25.99.2
ROUVPN4:
interface FastEthernet0/1.31
encapsulation dot1Q 31
ip address 10.99.31.254 255.255.255.0
!
interface FastEthernet0/1.97
encapsulation dot1Q 97
ip address 10.99.97.1 255.255.255.0
!
ip route 0.0.0.0 0.0.0.0 172.25.99.1
SW031:
interface Vlan31
ip address 10.99.31.1 255.255.255.0
!
ip route 0.0.0.0 0.0.0.0 10.99.31.254
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2017 02:27 AM
I am assuming that your tunnel between these two location is up and running, but for some reason traffic from 10.99.97.0/24 is not passing through the FW at site named Plant. Can you debug traffic using an ACL at the core switch to make sure that traffic is reaching site plant? or did you check firewall logs if the traffic is getting denied? I would suggest to use firewall packet-tracer simulator as it can simulate actual traffic and will tell you if there is an issue with the traffic flow.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2017 02:48 AM
yes tunnel is active and running.
could you please provide me the steps to do on core swicth or router!!!
Info:
1. I don't have access to FW.
2. All DMZ clients are in main Plant are working normally.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2017 03:16 AM
You can run this either on core switch or rouvpn3:
(make sure access-list 101 already doesn't exist on the device and if there is replace it with a number that's available)
config mode#
ip access-list extended 101
permit ip host 10.99.97.x host x.x.x.x
privileged mode#
debug ip packet 101
and once you ping from host to destination you can just look at the hit counters of this acl or do sh log. But most likely issue seems to be on the firewall located at site PLANT but this will confirm that the traffic is reaching there. I would reach out to firewall admin and check with her/him if traffic is hitting the firewall and is allowed .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2017 04:39 AM
i created the ACL on core switch.....and dont see any matches...
Client: 10.99.97.200/24 GW: 10.99.97.254
Ping from 10.99.97.254 to 10.99.97.200 - Not reachable
and ping from 10.99.97.200 source 10.99.97.254 - not reachable
There are the debug ip packet 101 logs:
ak 533E088 consumed in input feature , packet consumed, MCI Check(63), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE pak 53341B8 consumed in input feature , packet consumed, MCI Check(63), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2017 04:57 AM
I am kind of confused. You were trying to ping with in the same subnet and it's not working.where is .200 and what device is .254 ( is it the gateway for subnet 97? And which location/site they are in?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2017 05:20 AM
Sorry!!
Firewall IP is 10.99.97.254 (Plant) - Default gateway
Client behind SW031 is 10.99.97.200 (Warehouse)
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2017 05:46 AM
Interesting, so you are going across the tunnel to reach the default gateway for subnet 97. May I ask what kind of kind of tunnel is it ? If it's an IPSec tunnel please make sure that 10.99.97.0/24 is included in the ACL that is used to trigger the tunnel. Can you also do a trace route from the client in warehouse to an address at plant? I am trying to think how would it work because you are traversing another network when you hit edge router at site plant before you hit the gateway for 10.99.97.0/24 let me know if I am missing anything
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2017 06:00 AM
And don't forget that client has to broadcast an arp request to get the layer 2 address of its gateway before it can reach anything outside of 10.99.97.0/24. Is there a reason your network is designed this way because it seems to a flawed design.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2017 06:21 AM
This is the first time I am trying this....
if needed I can also modify it to make it work for warehouse(which is 1-2 km away).
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2017 06:34 AM
I would change the subnet at warehouse to something else like 10.99.x.x/24 and create an svi on the sw31 that would be used as a default gateway for this new network and then route it towards 10.97.99.254 for Dmz traffic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2017 06:54 AM
Plant have 10.99.0.0/16
Warehouse:its already active
* 10.99.31.0/24 - LAN, DG: 10.99.31.254 (Active)
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide