- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Dual WAN on Cisco 881
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Dual WAN on Cisco 881
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2011 06:06 AM - edited 03-04-2019 11:51 AM
Hi,
I would like to configure my Cisco 881 enabling Dual Wan (load balancing and failover).
- First link: HTTP, FTP, SMTP,...
- Second link: DATA inter-site (VPN), VoIP,...
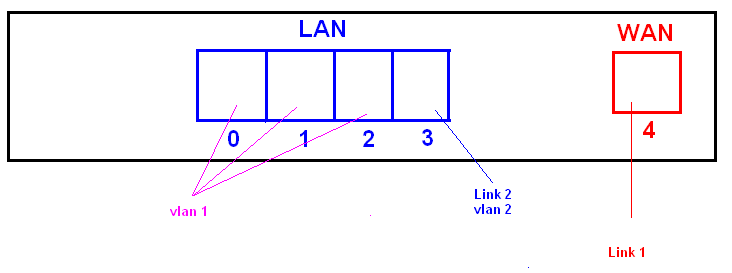
Configuration:
interface FastEthernet 4
ip address adress mask
interface FastEthernet 3
switchport mode access
switchport access vlan 2
interface vlan 2
ip address adress mask
route-map route1 permit 10
match ip address ACL1
match interface FastEthernet4
route-map route2 permit 10
match ip address ACL2
match interface VLAN2
ip nat inside source route-map route1 interface Fastethernet 4 overload
ip nat inside source route-map route2 interface VLAN2 overload
ip route 0.0.0.0 0.0.0.0 FastEthernet 4 track 1
ip route 0.0.0.0 0.0.0.0 VLAN 2 track 2
track 1 rtr1 reachability
delay down 1 up 1
track 2 rtr 2 reachability
delay down 1 up 1
-------------------------------------------------------------------
- Does the configuration seem OK?
- What does the command line "track 1 rtr 1 reachability delay down 1 up 1" mean?
- To send the different flow on one or the other port, do i have to configure it on the ACL1 and ACL2?
- Labels:
-
Other Routing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2011 08:27 AM
1. configuration seems ok. provided the following are also configured :
a) "ip nat outside" on the fa4 and int vlan 2
b)"ip nat inside" on the int vlan 1
c) The ACL's (ACL1 and ACL2) match correct traffic.
d) Also make sure that ACL2 and ACL2 are mutually exclusive (to remove any ambiguity) and exhaustive (covers all the traffic that needs to go out).
2. The delay waits for the specified time before removing/adding the route incase the track fails/comes-back-up.
"If you specify, for example, delay up 10 down 30, then if the object state changes from down to up, clients tracking that object are notified after 10 seconds. If the object state changes from up to down, then clients tracking that object are notified after 30 seconds."
from : http://www.cisco.com/en/US/docs/ios/12_2sb/feature/guide/sbaiptrk.html
3. Yes
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2011 07:06 AM
Thanks a lot for your answer.
I will try it!!!!
hace a nice day
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2011 11:06 AM
I attempted to copy this configuration on my Cisco 881 and was unsuccessful. I believe this feature, "RTR" only exists on older IOS releases as it is now part of IP SLAs.
To determine if your 881 image supports the RTR featureset, type "rtr ?" in config mode
---
#conf t
(config)#rtr ?
% Unrecognized command
---
This link may provide better information for those with a cisco881-k9 running the c880data-universalk9-mz.150-1.m4 image
http://esalonia.net/2010/08/10/dual-wan-link-failover-with-ip-slas/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2011 03:06 PM
Try something like this.
ip sla 1
icmp-echo XXX.XXX.XXX.XXX source-interface FastEthernet4
timeout 500
frequency 5
ip sla schedule 1 life forever start-time now
track 1 ip sla 1 reachability
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2014 03:47 PM
Can both External IPs be NAT'ed to with this config?
ip nat inside source static tcp Internal_IP1 3389 External_IP1 3389 route-map Route1 extendable
ip nat inside source static tcp Internal_IP2 3389 External_IP23389 route-map Route2 extendable
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2011 05:48 PM
The IP SLA config for different version of IOS is as follows :
For 12.3(8)T, 12.3(11)T, and 12.2(33)SRA
http://tools.cisco.com/squish/c1e9B
For 12.3(14)T, 12.4, 12.4(2)T, and 12.2(33)SXH
http://tools.cisco.com/squish/e2174
For 12.4(4)T and Later Releases
http://tools.cisco.com/squish/41C66
As you are running 15.0 code so for this consult the first link.
which is also explained in the last post by t_mcwilliams.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2011 09:37 AM
I am having the same problem but i make the same and if i plug the network cable on fe3 the internet go down.
any help will be apreciate.
hostname SIP-Firewall
!
boot-start-marker
boot-end-marker
!
logging message-counter syslog
!
no aaa new-model
!
!
ip source-route
!
ip dhcp pool LAN
network 10.10.0.0 255.255.255.0
default-router 10.10.0.1
dns-server 66.129.162.2 66.129.162.3
!
!
ip cef
!
!
track 1 ip sla 1 reachability
delay down 10 up 5
!
!
interface FastEthernet0
!
interface FastEthernet1
!
interface FastEthernet2
!
interface FastEthernet3
switchport access vlan 2
!
interface FastEthernet4
description ISP
ip address dhcp
ip nat outside
ip virtual-reassembly
duplex auto
speed auto
!
interface Vlan1
ip address 10.10.0.1 255.255.255.0
ip nat inside
ip virtual-reassembly
!
interface Vlan2
ip address 192.168.0.2 255.255.255.0
ip nat outside
ip virtual-reassembly
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 Vlan2 track 2
ip route 0.0.0.0 0.0.0.0 172.16.80.27
ip route 0.0.0.0 0.0.0.0 Vlan2
no ip http server
no ip http secure-server
!
ip nat inside source static tcp 10.10.0.5 80 interface FastEthernet4 80
ip nat inside source route-map isp1-primary interface FastEthernet4 overload
ip nat inside source route-map isp2-backup interface Vlan2 overload
!
ip sla 1
icmp-echo 4.2.2.2 source-interface FastEthernet4
frequency 5
ip sla schedule 1 life forever start-time now
access-list 100 permit ip any any
access-list 100 permit udp any any log
access-list 100 deny tcp any any eq 445 log
access-list 100 deny udp any any eq netbios-ns log
!
!
!
route-map isp1-primary permit 100
match ip address 100
match interface FastEthernet4
!
route-map isp2-backup permit 100
match ip address 101 100
match interface Vlan2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2011 04:48 PM
in your rout-map isp2 match only ACL 100 ACL 101 remove it
By the way you have permit any first line entry in ACL 100 which will not lead to block/ deny or exclude the las to deny lines you have to put the deny first then permit any any
Use the bellow link as an example
https://supportforums.cisco.com/docs/DOC-8313
Hope this help
If helpful rate
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-25-2011 02:27 AM
Hi,
I'm looking for almost the same solution, except:
- I have a 871 router
- pppoe dialere is used on both FE4 and VLAN2
- i only want backup functionality: if the PPPoE connection on FE4 fails, i want to use VLAN2's PPPoE connection (different ISPs).
Can I do this with a similar setup?
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-25-2011 02:44 AM
Hi,
yes but you'll have to give a higher AD in the static default route for backup, by default AD=1 and it is configured like this:
ip route 0.0.0.0 0.0.0.0 x.x.x.x 10
Regards.
Alain.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-06-2014 02:52 AM
Please any1 finally found a solution to this???
Kindly give working points.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-06-2014 07:16 AM
I believe this thread sufficiently covered the topic here. Either use the RTR feature (ios 12 or lower) or IP SLA feature in 15+ to accomplish this. Either way you're setting up a monitor for one connection and if that connection should fail it is disabled. the route with the next lowest metric becomes the default route.
In addition it is possible to use a route policy to distribute traffic across multiple interfaces for a sort of load balancing
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
