- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: How to manage routing & NAT for "secondary" ip address subnet
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to manage routing & NAT for "secondary" ip address subnet
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2019 07:26 PM
Hi !
The datacenter I'm hosted at delivered me two subnets of public IP address on the same interface on my CISCO2911 router. The secondary subnet is mainly going to be used for NAT static translations. I'm struggling to get things to work with the secondary subnet. I guess I can't figure out how to tell the router "If traffic comes from subnet A, use default route A and if it comes from subnet B, use default route B"
Routing
Here's what I got so far :
interface GigabitEthernet0/1 ip address 24.24.24.210 255.255.255.248 secondary ip address 68.68.68.50 255.255.255.240 ip nat outside --Internal network interface GigabitEthernet0/2.1 encapsulation dot1Q 1 native ip address 10.99.99.1 255.255.255.0 ip nat inside ip virtual-reassembly in ip nat inside source route-map RMAP_NAT interface GigabitEthernet0/1 overload ip route 0.0.0.0 0.0.0.0 68.68.68.49 route-map RMAP_NAT permit 100 match ip address ACL_NAT ip access-list extended ACL_NAT permit ip 10.99.99.0 0.0.0.255 any
Any help would be appreciated.
Thank you
-M
- Labels:
-
Other Routing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2019 09:48 PM
Hi,
Make a configuration like:
ip nat pool wan 24.24.24.210 24.24.24.210 netmask 255.255.255.248
!
ip nat inside source route-map RMAP_NAT pool wan overload
!
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2019 10:22 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2019 01:17 PM - edited 10-16-2019 09:25 AM
Hello
Your dc is aware of the secondary subnet so it will advertise and route for it - as for traffic being forwarded out of your network then traffic will always use the primary ip address however using static may will work for the primary or secondary addressing
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2019 10:01 PM - edited 10-16-2019 05:50 AM
Hi,
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2019 12:32 AM
Just to add to Paul's answer.
If the DC has given you a default gateway of 24.24.24.209 with the second subnet that suggests they are using secondary IPs.
Just ask them to route the entire subnet to 68.68.68.50, remove the secondary IP address (.210) from your router's interface and then as Paul says, just create static NATs and it will all work.
Make sure proxy arp is enabled on the router interface.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2019 06:46 AM
Hi,
Here, Enable the Proxy ARP and no need route for a secondary subnet.
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2019 01:39 AM
Hello
@martinlebel wrote:
Hi !
The datacenter I'm hosted at delivered me two subnets of public IP address on the same interface on my CISCO2911 router. The secondary subnet is mainly going to be used for NAT static translations. --
Nothing you need to do, just add the static nat statements as/when you need to
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2019 10:01 PM - edited 10-16-2019 05:49 AM
Hi,
Deleted as PBR is not a suitable option.
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2019 12:41 AM
Hello
@Deepak Kumar wrote:
Hi,
PBR will resolve your issue as:
access-list 100 permit ip 1 10.99.99.0 0.0.0.255 any
!
R1(config)#route-map Secondary_ISP
R1(config-route-map)#match ip address 100
R1(config-route-map)#set ip next-hop 24.24.24.209!
R1(config)#interface GigabitEthernet0/2.1
R1(config-subif)#ip policy route-map Secondary_ISP
and keep you all other configuration and add PBR as mentioned above. It will work for you.
This then will push all the lan traffic pertaining to that subnet via the secondary address even more so you will then have the same problem using the primary subnet as you would with the secondary.
My understanding 1-1 static network translation on the secondary addressing would be fine without any need to policy or re-route anything.
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2019 06:17 AM - edited 10-16-2019 07:04 AM
Hi,
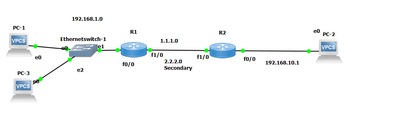
I am not sure that I am doing right or wrong but I did the same in my lab and here is the result:
R1 Configuration: (Where we need Secondary IP address (CE))
!
interface FastEthernet0/0
ip address 192.168.1.1 255.255.255.0
ip nat inside
ip virtual-reassembly in
duplex half
!
interface FastEthernet1/0
ip address 1.1.1.1 255.255.255.0
ip proxy-arp
ip nat outside
ip virtual-reassembly in
duplex auto
speed auto
!
!
ip nat pool wan 2.2.2.1 2.2.2.1 netmask 255.255.255.0
!
ip nat inside source list 100 pool wan overload
!
ip nat inside source static 192.168.1.12 1.1.1.1 extendable
ip nat inside source static 192.168.1.2 2.2.2.1 extendable
!
ip route 0.0.0.0 0.0.0.0 1.1.1.2
!
access-list 100 permit ip any any
!
=======================
R2 Configuration As ISP Router (PE):
!
interface FastEthernet0/0
ip address 192.168.10.1 255.255.255.0
duplex half
!
interface FastEthernet1/0
ip address 2.2.2.2 255.255.255.0 secondary
ip address 1.1.1.2 255.255.255.0
ip proxy-arp
duplex auto
speed auto
!
================
Here is the debug output:
(Ping From PC1 to R2 interface F0/0 IP)
R2#debug ip icmp
ICMP packet debugging is on
R2#
*Oct 16 13:00:13.015: ICMP: echo reply sent, src 192.168.10.1, dst 2.2.2.1, topology BASE, dscp 0 topoid 0
R2#
*Oct 16 13:00:14.051: ICMP: echo reply sent, src 192.168.10.1, dst 2.2.2.1, topology BASE, dscp 0 topoid 0
R2#
*Oct 16 13:00:15.091: ICMP: echo reply sent, src 192.168.10.1, dst 2.2.2.1, topology BASE, dscp 0 topoid 0
R2#
*Oct 16 13:00:16.119: ICMP: echo reply sent, src 192.168.10.1, dst 2.2.2.1, topology BASE, dscp 0 topoid 0
R2#
*Oct 16 13:00:17.139: ICMP: echo reply sent, src 192.168.10.1, dst 2.2.2.1, topology BASE, dscp 0 topoid 0
R2#
(PC2 to PC1(2.2.2.1) ping using Static NAT)
Oct 16 13:14:52.287: NAT*: s=192.168.10.2, d=2.2.2.1->192.168.1.2 [6102]
R1(config)#
*Oct 16 13:14:54.291: NAT*: s=192.168.10.2, d=2.2.2.1->192.168.1.2 [6103]
R1(config)#
*Oct 16 13:14:55.307: NAT*: s=192.168.1.2->2.2.2.1, d=192.168.10.2 [6102]
*Oct 16 13:14:55.307: NAT*: s=192.168.1.2->2.2.2.1, d=192.168.10.2 [6103]
*Oct 16 13:14:56.295: NAT*: s=192.168.10.2, d=2.2.2.1->192.168.1.2 [6104]
*Oct 16 13:14:56.303: NAT*: s=192.168.1.2->2.2.2.1, d=192.168.10.2 [6104]
R1(config)#
*Oct 16 13:14:57.311: NAT*: s=192.168.10.2, d=2.2.2.1->192.168.1.2 [6105]
*Oct 16 13:14:57.335: NAT*: s=192.168.1.2->2.2.2.1, d=192.168.10.2 [6105]
R1(config)#
*Oct 16 13:14:58.343: NAT*: s=192.168.10.2, d=2.2.2.1->192.168.1.2 [6106]
*Oct 16 13:14:58.367: NAT*: s=192.168.1.2->2.2.2.1, d=192.168.10.2 [6106]
R1(config)#
(PC2 to (1.1.1.1) PC3 ping using Static NAT)
*Oct 16 13:58:44.387: NAT*: s=192.168.10.2, d=1.1.1.1->192.168.1.12 [8734]
*Oct 16 13:58:44.431: NAT*: s=192.168.1.12->1.1.1.1, d=192.168.10.2 [8734]
R1(config)#
*Oct 16 13:58:45.467: NAT*: s=192.168.10.2, d=1.1.1.1->192.168.1.12 [8735]
*Oct 16 13:58:45.483: NAT*: s=192.168.1.12->1.1.1.1, d=192.168.10.2 [8735]
R1(config)#
*Oct 16 13:58:46.503: NAT*: s=192.168.10.2, d=1.1.1.1->192.168.1.12 [8736]
*Oct 16 13:58:46.519: NAT*: s=192.168.1.12->1.1.1.1, d=192.168.10.2 [8736]
R1(config)#
*Oct 16 13:58:47.511: NAT*: s=192.168.10.2, d=1.1.1.1->192.168.1.12 [8737]
*Oct 16 13:58:47.543: NAT*: s=192.168.1.12->1.1.1.1, d=192.168.10.2 [8737]
R1(config)#
*Oct 16 13:58:48.567: NAT*: s=192.168.10.2, d=1.1.1.1->192.168.1.12 [8738]
*Oct 16 13:58:48.571: NAT*: s=192.168.1.12->1.1.1.1, d=192.168.10.2 [8738]
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2019 07:14 AM - edited 10-16-2019 08:18 AM
@Deepak Kumar
In your lab you have the secondary addressing on the isp (PE) rtr interface towards the client (CE) rtr, This is incorrect the secondary addressing should be applied on the clients (CE) rtr wan facing interface!
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2019 08:47 AM
Hi @paul driver
If you look it closely, it is my gateway IP address for Secondary subnet and it does not require if I will add a static route.
As:
R2(config)#interface fastEthernet 1/0
R2(config-if)#no ip address 2.2.2.2 255.255.255.0 secondary
!
R2(config)#ip route 2.2.2.0 255.255.255.0 1.1.1.1
R2#sho ip route
Gateway of last resort is not set
1.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 1.1.1.0/24 is directly connected, FastEthernet1/0
L 1.1.1.2/32 is directly connected, FastEthernet1/0
2.0.0.0/24 is subnetted, 1 subnets
S 2.2.2.0 [1/0] via 1.1.1.1
192.168.10.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.10.0/24 is directly connected, FastEthernet0/0
L 192.168.10.1/32 is directly connected, FastEthernet0/0
R2#
(Ping from PC2 to PC1 (2.2.2.1)
PC-2> ping 2.2.2.1
84 bytes from 2.2.2.1 icmp_seq=1 ttl=62 time=122.753 ms
84 bytes from 2.2.2.1 icmp_seq=2 ttl=62 time=36.135 ms
84 bytes from 2.2.2.1 icmp_seq=3 ttl=62 time=31.625 ms
84 bytes from 2.2.2.1 icmp_seq=4 ttl=62 time=25.459 ms
84 bytes from 2.2.2.1 icmp_seq=5 ttl=62 time=36.348 ms
Router1 logs:
R1(config)#
*Oct 16 14:15:03.587: NAT*: s=192.168.10.2, d=2.2.2.1->192.168.1.2 [15036]
*Oct 16 14:15:03.647: NAT*: s=192.168.1.2->2.2.2.1, d=192.168.10.2 [15036]
R1(config)#
*Oct 16 14:15:04.707: NAT*: s=192.168.10.2, d=2.2.2.1->192.168.1.2 [15037]
*Oct 16 14:15:04.719: NAT*: s=192.168.1.2->2.2.2.1, d=192.168.10.2 [15037]
R1(config)#
*Oct 16 14:15:05.751: NAT*: s=192.168.10.2, d=2.2.2.1->192.168.1.2 [15038]
*Oct 16 14:15:05.755: NAT*: s=192.168.1.2->2.2.2.1, d=192.168.10.2 [15038]
R1(config)#
*Oct 16 14:15:06.771: NAT*: s=192.168.10.2, d=2.2.2.1->192.168.1.2 [15039]
*Oct 16 14:15:06.779: NAT*: s=192.168.1.2->2.2.2.1, d=192.168.10.2 [15039]
R1(config)#
*Oct 16 14:15:07.799: NAT*: s=192.168.10.2, d=2.2.2.1->192.168.1.2 [15040]
*Oct 16 14:15:07.815: NAT*: s=192.168.1.2->2.2.2.1, d=192.168.10.2 [15040]
R1(config)#
R1(config)#
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2019 04:04 AM
I've never been a fan of using secondary addresses on interfaces; it makes it complicated if you need to source traffic on the LAN that needs to go out through an IP other than the IP assigned to the outside interface. As Paul noted as long as your provider is routing both subnets to your outside interface it is just a matter of assigning the addresses to the outside interface to answer inbound or outbound request. You WAN IP and IP address assigned to your outside interface are fine. You will need to create NAT pools for each of your public addresses as Deepak notes but you don't need to do route maps.
When you you create the NAT pool for the public IP address that will bind the address to the outside Interface. You can then do port translations as you need to for that address. As long as your ISP is routing the subnet to you the router will answer for the address. I have a more detailed answer at the below link that will further clarify what you are trying to do:
Regards,
Sam
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2019 08:52 AM
Hello,
on a side note, if you want to use the secondary addresses just for static NAT, you could use a route map on the static NAT entry that specified the next hop as being the IP address of the other end, 24.24.24.209 in your case. Since static NAT takes precedence, your static entries would always go to the secondary IP.
That would look like this:
access-list 101 permit ip host 10.99.99.101 any
access-list 102 permit ip host 10.99.99.102 any
!
ip nat inside source static 10.99.99.101 24.24.24.210 route-map STATIC_1
ip nat inside source static 10.99.99.102 24.24.24.211 route-map STATIC_2
ip nat inside source list 1 interface GigabitEthernet0/1 overload
!
route-map STATIC_1 permit 10
match ip address 101
set ip next-hop 24.24.24.209
!
route-map STATIC_2 permit 10
match ip address 102
set ip next-hop 24.24.24.209
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide