- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Latency issue with 4431
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2022 10:59 AM
Hello everyone, please need your help.
we had an old 2921 router, everything worked fine, we had 2 DMVPN tunnels via ipsec and isakmp.
we had to change the router 2921 to isr 4331, and keep the same configuration, after changing to 4431, the employees noticed a big latency problem, we tried to troubleshoot, we had the same configuration as 2921 the only difference was the isakmp key , on the new 4331 the key was encrypted, but in the other routers and the old one the key was not encrypted.
According to your experience, can a bad isakmp key cause latency?
thank you in advance .
Solved! Go to Solution.
- Labels:
-
ISR 4000 Series
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2023 09:30 AM
It sounds like there may be an issue with the configuration on the ISR 4331 router, specifically with the DMVPN tunnels or the IPsec and ISAKMP settings.
I would recommend checking the following:
- Ensure that the DMVPN configuration on the ISR 4331 is the same as the previous 2921 router, including the tunnel interfaces, crypto maps, and any other relevant settings.
- Verify that the ISAKMP key is configured correctly on the ISR 4331, including the correct encryption algorithm and key value.
- Check that the IPsec settings on the ISR 4331 are correct, including the correct encryption and authentication algorithms, and that the relevant access lists are configured correctly.
- Make sure that the MTU size is consistent across all the devices in the network, including the ISR 4331, the other routers, and any devices connected to the network.
- Verify that the routing protocols are configured correctly, and that the correct routes are being advertised and installed in the routing table.
- Check for any other misconfigurations or inconsistencies in the network, such as incorrect VLAN assignments or mismatched cable connections.
It is also possible that there is an issue with the physical connection or the network infrastructure. It's important to check the cabling, power, and other physical connectivity issues.
It's important to gather the debugs and logs to troubleshoot the issue and check if there is any errors or messages that could help identifying the issue.
It's also possible that working with the ISP and having them check their network could help identifying the issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2022 11:08 AM
no password not relate to latency
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2022 11:12 AM
Thanks, what could be causing the latency?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2022 12:02 PM
check this point
if you have 2911 HW encryption acceleration then it will be faster than new ISR4000
"""All Cisco 2900 Series Integrated Services Routers offer embedded hardware encryption acceleration"""
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2022 12:10 PM
No we don't have 2911 HW encryption acceleration
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2022 12:21 PM
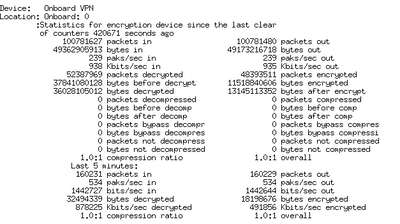
show crypto engine accelerator statistic <<-can you share this of old, if you can
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2022 12:32 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2022 11:49 AM
Hello,
are you using SVTIs on the 4331 routers ? Post the running configuration of one of the routers...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2022 12:07 PM
crypto isakmp policy 10
encryption 3des
authentication pre-share
group 2
crypto isakmp key 6 hdK1242!? address 0.0.0.0 no-xauth
crypto isakmp keepalive 10
crypto isakmp aggressive-mode disable
!
!
crypto ipsec transform-set CISCOSET esp-3des esp-sha-hmac
mode transport
!
crypto ipsec profile CISCO_PROF
set transform-set CISCOSET
!
!
!
!
!
!
!
!
!
!
interface Null0
no ip unreachables
!
interface Tunnel2
description BACKUP_DMVPN_TUNNEL
ip address 10.x.x.x 255.255.255.0
no ip redirects
ip mtu 1400
ip hello-interval eigrp 250 20
ip hold-time eigrp 250 60
ip nhrp authentication DmVPN2
ip nhrp map multicast X.X.X.
ip nhrp map 10.X.X.X X.X.X.X
ip nhrp network-id 254
ip nhrp holdtime 60
ip nhrp nhs 10.X.X.X
ip nhrp registration timeout 30
ip tcp adjust-mss 1360
tunnel source GigabitEthernet0/0/0
tunnel mode gre multipoint
tunnel key 254
tunnel protection ipsec profile BOT_PROF shared
!
interface Tunnel3
description PRIMARY_DMVPN_TUNNEL
ip address 10.Y.Y.Y 255.255.255.0
no ip redirects
ip mtu 1400
ip hello-interval eigrp 250 20
ip hold-time eigrp 250 60
ip nhrp authentication DmVPN3
ip nhrp map multicast 1Y.Y.Y.Y
ip nhrp map 10.Y.Y.Y Y.Y.Y.Y
ip nhrp network-id 255
ip nhrp holdtime 60
ip nhrp nhs 10.Y.Y.Y
ip nhrp registration timeout 30
ip tcp adjust-mss 1360
tunnel source GigabitEthernet0/0/0
tunnel mode gre multipoint
tunnel key 255
tunnel protection ipsec profile CISCO_PROF shared
!
interface GigabitEthernet0/0/0
bandwidth 20000
ip flow monitor Netflow-Monitor-In input
ip flow monitor Netflow-Monitor-Out output
ip address x.x.x.X 255.255.255.252
ip redirects
no ip proxy-arp
ip mtu 1400
ip tcp adjust-mss 1360
media-type rj45
speed 100
no negotiation auto
no cdp enable
no snmp trap link-status
service-policy output 20mbs-75_24
!
interface GigabitEthernet0/0/1
no ip address
no ip redirects
no ip proxy-arp
ip nbar protocol-discovery
negotiation auto
no cdp enable
!
interface GigabitEthernet0/0/1.18
description Central LAN
encapsulation dot1Q 18
ip flow monitor Netflow-Monitor-In input
ip flow monitor Netflow-Monitor-Out output
ip address Y.Y.Y.Y ....
no ip redirects
no ip unreachables
no ip proxy-arp
no cdp enable
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2022 12:27 PM - edited 10-17-2022 12:34 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2022 01:28 PM
Hello,
do you actually have the HSECK9 license purchased ? In any case, it is not enabled:
--> no license feature hseck9
According to Cisco, 'without the HSECK9 license, only 225 secure tunnels and 85 Mbps of crypto bandwidth would be available...'
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2022 01:46 PM
get it, perfect answer
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-19-2022 06:12 AM
Thank you All for your response
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2023 08:50 AM
Hello All , unfortunately we still have the issue in 8 locations now , it s not license issue . we took 1 router from an impacted location and use it in a location that s working fine and it worked fine . we have MPLS , we involved our isp , they didn't find anything in the circuit , mtu is configured correctly
thanks
thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2023 09:30 AM
It sounds like there may be an issue with the configuration on the ISR 4331 router, specifically with the DMVPN tunnels or the IPsec and ISAKMP settings.
I would recommend checking the following:
- Ensure that the DMVPN configuration on the ISR 4331 is the same as the previous 2921 router, including the tunnel interfaces, crypto maps, and any other relevant settings.
- Verify that the ISAKMP key is configured correctly on the ISR 4331, including the correct encryption algorithm and key value.
- Check that the IPsec settings on the ISR 4331 are correct, including the correct encryption and authentication algorithms, and that the relevant access lists are configured correctly.
- Make sure that the MTU size is consistent across all the devices in the network, including the ISR 4331, the other routers, and any devices connected to the network.
- Verify that the routing protocols are configured correctly, and that the correct routes are being advertised and installed in the routing table.
- Check for any other misconfigurations or inconsistencies in the network, such as incorrect VLAN assignments or mismatched cable connections.
It is also possible that there is an issue with the physical connection or the network infrastructure. It's important to check the cabling, power, and other physical connectivity issues.
It's important to gather the debugs and logs to troubleshoot the issue and check if there is any errors or messages that could help identifying the issue.
It's also possible that working with the ISP and having them check their network could help identifying the issue.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide