- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Networking Project Help
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Networking Project Help
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2019 02:14 AM - edited 12-02-2019 07:58 AM
Hi All,
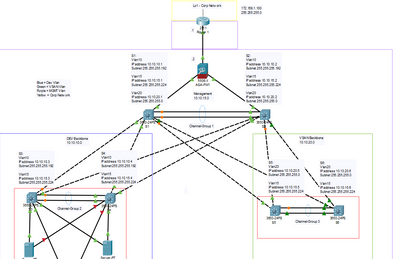
Below is a picture of my topology,
The file to the packet tracer is also attached. All password or logins are admin and cisco.
I would like DEV and Management network traffic to route through the firewall when access the corp network.
I have yet to configure the router and firewall as i'm not sure in what to do.
My other question is VLAN 10 and 20 can not cross communicate. This is the way i want it, but should i also put ACLS to reinforce this rule as best practice?
Kind Regards,
Daniel!
Daniel Growth
- Labels:
-
LAN Switching
-
Routing Protocols
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2019 07:24 AM
I am able to ping the interfaces on the firewall but am unable to ping 172.168.1.100.
When i ping the firewall it is super slow.
Switch#ping 10.10.15.20
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.10.15.20, timeout is 2 seconds:
!!!!!!
Success rate is 120 percent (6/5), round-trip min/avg/max = 216/354/492 ms
Switch#ping 10.10.15.20
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.10.15.20, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 183/256/299 ms
Switch#ping 10.10.15.20
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.10.15.20, timeout is 2 seconds:
....!
Success rate is 20 percent (1/5), round-trip min/avg/max = 255/255/255 ms
That is from switch 5.
It is a similar result to everything else to.
Daniel Growth
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2019 08:04 AM
Hello,
did you make all the changes on the firewall ? Post the running config of the firewall so I can doublecheck.
If I run the file on a 4Gig computer, it is indeed very slow. If I run it on a 16Gig computer, it is fast, so it might be the machine you are running it on. Either way, you would need to test in a real environment anyway, so I wouldn't worry too much about the performance of what in the end is just a simulator...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2019 08:25 AM
As long as you are confident the spanning tree etc is working fine then i'm happy :)
I have never configured an ASA firewall before.
Like I said im still unable to ping the Corp lan.
hostname ciscoasa
names
!
interface Port-channel1
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/1
nameif inside
security-level 0
ip address 192.168.1.1 255.255.255.0
!
interface GigabitEthernet1/2
description Link to S1
nameif inside1
security-level 100
ip address 10.10.15.20 255.255.255.224
!
interface GigabitEthernet1/3
description Link to S2
nameif inside2
security-level 100
ip address 10.10.15.21 255.255.255.224
!
interface GigabitEthernet1/4
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/5
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/6
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/7
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/8
no nameif
security-level 0
no ip address
channel-group 1 mode on
shutdown
!
interface Management1/1
management-only
no nameif
no security-level
no ip address
!
!
!
access-list INBOUND extended permit ip any any
!
!
!
!
!
!
class-map inspection_default
!
policy-map global_policy
class inspection_default
inspect icmp
!
!
telnet timeout 5
ssh timeout 5
!
!
!
!
!
router ospf 1
log-adjacency-changes
network 0.0.0.0 255.255.255.255 area 0
default-information originate
!
Daniel Growth
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2019 08:38 AM
Hello,
click on the ASA icon and go to the CLI tab. The prompt will be:
ciscoasa>
Type 'enable' and press ENTER (you don't need a password).
Then cut and paste the script below:
conf t
interface GigabitEthernet1/1
nameif outside
exit
route outside 0.0.0.0 0.0.0.0 192.168.1.2
access-group INBOUND in interface outside
end
wr mem
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2019 09:37 AM
I entered the config and it applied.
If i ping from anywhere to 192.168.1.1 or 2
It wont work.
I feel like the OSPF is not configured correctly possibly.
Daniel Growth
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2019 10:30 AM
Hello,
post the ASA config again with the changes you have implemented.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2019 12:53 PM
ASA Version 9.6(1)
!
hostname ciscoasa
names
!
interface Port-channel1
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/1
nameif inside
security-level 0
ip address 192.168.1.1 255.255.255.0
!
interface GigabitEthernet1/2
description Link to S1
nameif inside1
security-level 100
ip address 10.10.15.20 255.255.255.224
!
interface GigabitEthernet1/3
description Link to S2
nameif inside2
security-level 100
ip address 10.10.15.21 255.255.255.224
!
interface GigabitEthernet1/4
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/5
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/6
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/7
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/8
no nameif
security-level 0
no ip address
channel-group 1 mode on
shutdown
!
interface Management1/1
management-only
no nameif
no security-level
no ip address
!
!
!
access-list INBOUND extended permit ip any any
!
!
!
!
!
!
class-map inspection_default
!
policy-map global_policy
class inspection_default
inspect icmp
!
!
telnet timeout 5
ssh timeout 5
!
!
!
!
!
router ospf 1
log-adjacency-changes
network 0.0.0.0 0.0.0.0 area 0
default-information originate
!
I haven't made any changes to the OSPF. I think this is the issue. I tried changing it to the subnet rather than wildcard but it resets to the above.
Daniel Growth
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2019 01:23 PM
Hello,
that is still the old, non-working config. None of the changes have been applied, I don't know why that is to be honest. How do you actually access the ASA, and can you enter the changes manually ? Post the sequence of commands you enter from the ASA command line...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2019 01:11 AM
I reloaded you previous attachment:
ciscoasa>en
Password:
ciscoasa#conf t
ciscoasa(config)#interface GigabitEthernet1/1
ciscoasa(config-if)#nameif outside
ciscoasa(config-if)#exit
ciscoasa(config)#route outside 0.0.0.0 0.0.0.0 192.168.1.2
ciscoasa(config)#access-group INBOUND in interface outside
ciscoasa(config)#end
ciscoasa#wr mem
Building configuration...
Cryptochecksum: 6222183b 37822c26 521601ca 59323004
1341 bytes copied in 1.869 secs (717 bytes/sec)
[OK]
ciscoasa#show run
: Saved
:
ASA Version 9.6(1)
!
hostname ciscoasa
names
!
interface Port-channel1
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/1
nameif outside
security-level 0
ip address 192.168.1.1 255.255.255.0
!
interface GigabitEthernet1/2
description Link to S1
nameif inside1
security-level 100
ip address 10.10.15.20 255.255.255.224
!
interface GigabitEthernet1/3
description Link to S2
nameif inside2
security-level 100
ip address 10.10.15.21 255.255.255.224
!
interface GigabitEthernet1/4
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/5
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/6
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/7
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/8
no nameif
security-level 0
no ip address
channel-group 1 mode on
shutdown
!
interface Management1/1
management-only
no nameif
no security-level
no ip address
!
!
route outside 0.0.0.0 0.0.0.0 192.168.1.2 1
!
access-list INBOUND extended permit ip any any
!
!
access-group INBOUND in interface outside
!
!
!
!
class-map inspection_default
!
policy-map global_policy
class inspection_default
inspect icmp
!
!
telnet timeout 5
ssh timeout 5
!
!
!
!
!
router ospf 1
log-adjacency-changes
network 0.0.0.0 255.255.255.255 area 0
default-information originate
!
ciscoasa#
That is all the config from opening.
Daniel Growth
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2019 01:35 PM
To all concerned,
It is very clear this thread is school work.
Help the students learn: Post the links to documents and configuration guides.
Please refrain from handing out answers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2019 06:52 AM
In this case I would have to ask that you remove "It is very clear this thread is school work." as this is not true. Although I do appreciate you wanting people to be taught rather than given the answers.
Daniel Growth
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2019 04:44 AM
Hello,
I have revised the topology and made the links between both L3 switches and the firewall part of the Vlan 15.
Make sure the ASA has the config exactly as below. If it doesn't work, post the ASA configuration you have, so I can double check.
ASA Version 9.6(1)
!
hostname ciscoasa
names
!
interface Port-channel1
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/1
nameif outside
security-level 0
ip address 192.168.1.1 255.255.255.0
!
interface GigabitEthernet1/2
description Link to S1
nameif inside1
security-level 100
ip address 10.10.15.20 255.255.255.224
!
interface GigabitEthernet1/3
description Link to S2
nameif inside2
security-level 100
ip address 10.10.15.21 255.255.255.224
!
interface GigabitEthernet1/4
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/5
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/6
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/7
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/8
no nameif
security-level 0
no ip address
channel-group 1 mode on
shutdown
!
interface Management1/1
management-only
no nameif
no security-level
no ip address
!
route outside 0.0.0.0 0.0.0.0 192.168.1.2 1
!
access-list INBOUND extended permit ip any any
!
access-group INBOUND in interface outside
!
class-map inspection_default
!
policy-map global_policy
class inspection_default
inspect icmp
!
telnet timeout 5
ssh timeout 5
!
router ospf 1
log-adjacency-changes
network 0.0.0.0 0.0.0.0 area 0
default-information originate
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2019 07:56 AM
If i route ? it only gives the option of inside.
Daniel Growth
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2019 08:15 AM
Hello,
you need to name interface GigabitEthernet 'outside' first:
interface GigabitEthernet1/1
nameif outside
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2019 08:36 AM
This is the config so far:
ASA Version 9.6(1)
!
hostname ciscoasa
names
!
interface Port-channel1
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/1
nameif outside
security-level 0
ip address 192.168.1.1 255.255.255.0
!
interface GigabitEthernet1/2
description Link to S1
nameif inside1
security-level 100
ip address 10.10.15.20 255.255.255.224
!
interface GigabitEthernet1/3
description Link to S2
nameif inside2
security-level 100
ip address 10.10.15.21 255.255.255.224
!
interface GigabitEthernet1/4
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/5
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/6
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/7
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/8
no nameif
security-level 0
no ip address
channel-group 1 mode on
shutdown
!
interface Management1/1
management-only
no nameif
no security-level
no ip address
!
!
route outside 0.0.0.0 0.0.0.0 192.168.1.2 1
!
access-list INBOUND extended permit ip any any
!
!
access-group INBOUND in interface outside
!
!
!
!
class-map inspection_default
!
policy-map global_policy
class inspection_default
inspect icmp
!
!
telnet timeout 5
ssh timeout 5
!
!
!
!
!
router ospf 1
log-adjacency-changes
network 0.0.0.0 255.255.255.255 area 0
default-information originate
!
I am unable to ping from S1 to 192.... 1 but i am able to ping the two vlan 15 interfaces.
Daniel Growth
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide