- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Point to point connection
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2023 12:14 PM
Hi,
I have 2 locations and they are connected to connected through VPN connection and it works fine but I am just adding a new point to point connection.
On both ends Fortinet Firewalls interface have been configured with ip address 172.16.30.1 and 172.16.30.2 respectively.
On both cisco SW we have int vlan 65 with ip address 172.16.0.5 on Cisco Sw site 1 and 172.16.30.6 on Cisco SW site 2.
Interface Connecting the 2 sites were configured as truck allowing vlan 65
Int GigabitEthernet1/0/22 and int GigabitEthernet 1/0/23 were configured as access allowing vlan 65.
Fortinet 1 cannot ping Fortinet 2
I tried putting an ip address on the interfaces connecting the 2 sites (
GigabitEthernet1/0/24 and Te2/1/1) and both sites can ping each other but still cannot get Fortinet 1 to ping Fortinet 2.
What will be the simplest setup to have Fortinet 1 ping Fortinet 2? i cannot change anything on Fortinet side
Thanks
Tazio
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2023 03:07 AM
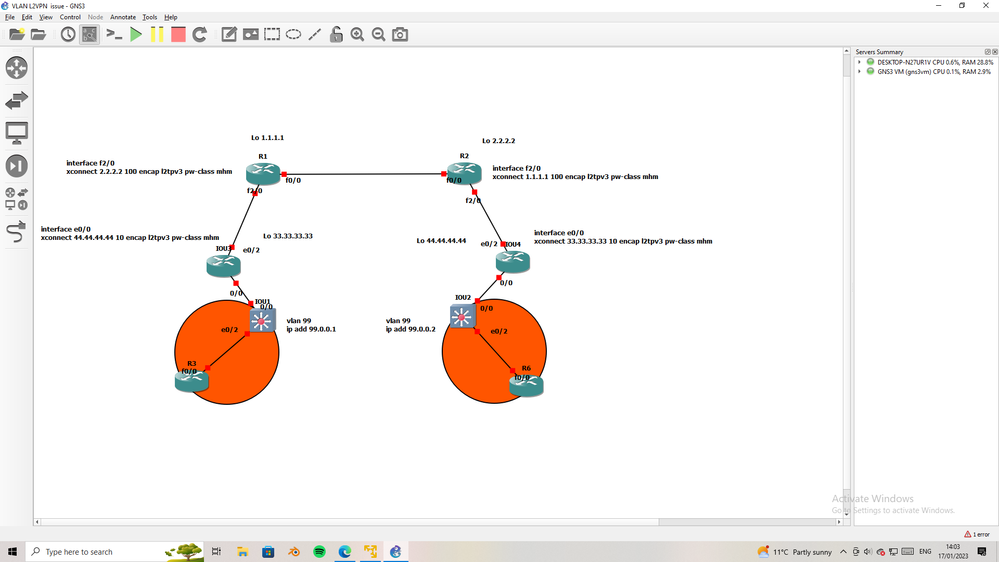
this is simple topology, I want to clear points here,
R1 & R2 is ISP router
IOU3 and IOU3 is your edge router,
IOU1 & IOU2 is L3SW
if we want to L2 between two SW, the two edge router must config with xconnect,
the issue is not solve in SW it solve in edge router that connect to ISP.
this solution will be L2 over ISP L2VPN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2023 12:23 PM
the SW port connect to Fortinet must assign to vlan 65.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2023 12:34 PM
Hi
Thanks for your reply
Interface GigabitEthernet1/0/22 and GigabitEthernet1/0/23 have these configuration
Switchport mode access
Switchport access vlan 65
Thanks
Tazio
GigabitEthernet1/0/22
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2023 12:53 PM
P2P VPN is it L2VPN or L3VPN ??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2023 07:45 AM
Hi ,
This is just a layer 2 Pt2Pt connection
Thanks
Tazio
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2023 07:47 AM - edited 01-12-2023 07:59 AM
then check the policy in both FW it can drop the icmp packet.
also check arp in both FW, are the ARP show IP-MAC in both FW??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2023 12:35 PM
Couple of question and clarification
1. have you created VLAN 65 on both switches?
2. you mentioned the IP address here, does this not match in the same network? or is this typo error?
ip address 172.16.0.5 on Cisco Sw site 1 and 172.16.30.6 on Cisco SW site 2.
3. if this this just Layer 2 extended on both the switches, that should work as expected.
4. Firewall what is the gateway they are pointing ?
5. I am sure p2p connection I take as Layer 2 connection (not layer3 connection)
6. On switch you using interface vlan 65 and IP address ?
7. From switch to switch are you able to ping ?
8 from Switch on site 1 to Firewall IP are you able to ping ? same case Site 2 ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2023 07:56 AM
Hi,
Thanks for your reply.
There is a little progress as I spoke with the Fortinet guy and he had GW missing so he added the GW and now Fortinet can ping directly connected Cisco SW but the 2 Cisco SWs are still not talking.
To answer to your question
1. Yes Vlan 65 are on both Sw
2. Yes it is a typo in fact the ip are 172.16.30.3 and 172.16.30.6 and these has been added as GW on Fortinet.
3. unfortunately still not working
4. Firewall GW were missing and now it has been added as 172.16.30.3 and 172.16.30.6
5 Yes this is a layer 2 pt2pt connection
6 Yes I am using int vlan 65 with ip address .Please see show run attached
7 SW to Sw cannot ping
8. SW to Firewall is now pingable after GW have been added.
Thanks
Tazio
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2023 09:46 AM
as per your diagram it was Gig 1/0/24
your config show as below : where is Gig 1/0/24 config
Cisco SW Site 1#sh run
!
interface GigabitEthernet1/0/22
switchport access vlan 65
switchport mode access
!
interface Vlan65
ip address 172.16.30.3 255.255.255.248
!
interface GigabitEthernet1/0/22
switchport trunk allowed vlan 65
switchport mode trunk
==========
can you also post show cdp neigh (from both the switches ?)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2023 10:15 AM
Sorry again typo when editing the file
Cisco SW Site 1#sh run
!
interface GigabitEthernet1/0/22
switchport access vlan 65
switchport mode access
!
interface Vlan65
ip address 172.16.30.3 255.255.255.248
!
interface GigabitEthernet1/0/24
switchport trunk allowed vlan 65
switchport mode trunk
Please see sh cdp nei attached. Can see neigh from one side only
Thanks
Tazio
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2023 11:18 AM
we do not see the switches forming CDP, Maybe it was not enabled not sure.
post below output from bot the switches :
show vlan
show IP interface brief
show span vlan 65
show interface gig 1/0/24 (from switch site1)
show interface ten 2/1/1 (from switch site2)
show run | in hostname
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2023 11:38 AM
Hi ,
Thanks for your prompt reply.
For ease of understanding I labelled the SW in site 1 as Cisco SW Site 1 but the hostname is BGP1
Same thing for site 2 I labelled it as Cisco SW Site 2 but the hostname is COLOSW_STACKED.
I am attaching 2 files for the output of the commands you requested.
Thanks
Tazio
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2023 11:58 AM - edited 01-12-2023 11:59 AM
here is my observation :
show vlan (COLOSW_STACKED)
I do not see your Ten 2/1/1 part of the VLAN. 65
65 PT-2-PT active Gi1/0/23, Gi2/0/22, Gi2/0/23
other part :
BGP1 Gi 1/0/24 is Ethernet port
COLOSW_STACKED - Ten 2/1/1 have SFP port ? (1000BaseLX SFP)
So that is not possible to connect Ethernet to SFP (until you have any media converters between)
So as per I know you have some Physical connection issue here -
If you look at the spantree output ( both switch for VLAN 65 acting as root )
BGP1#sh span vlan 65
VLAN0065
Spanning tree enabled protocol rstp
Root ID Priority 32833
Address 084f.f984.d200
This bridge is the root
COLOSW_STACKED#sh span vlan 65
VLAN0065
Spanning tree enabled protocol rstp
Root ID Priority 32833
Address 10b3.d62f.de80
This bridge is the root
Suggestions :
check Ten 2/1/1 config, make sure configured correctly trunk and with VLAN 65
check - show interface trunk
shutdown Ten 2/1/1 see what ports going down.
by the way what model switches is this ? what IOS code running ? ( I am sure some where I see Cat 9300 please clarify)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2023 12:38 PM
Hi ,
Thanks for your reply and trying your best to help me.
Int Te2/1/1 is a trunk port and hence will not show up in sh vlan .
Yes there is a media converter on the BGP1 site. The ISP hands over the circuit to be in a media converter on an Ethernet port and I take over from that port to my Cisco Sw.
Seems correct configuration on int Te2/1/1
COLOSW_STACKED#sh run int te2/1/1
Building configuration...
Current configuration : 98 bytes
!
interface TenGigabitEthernet2/1/1
switchport trunk allowed vlan 65
switchport mode trunk
end
I did shut down int Te2/1/1 and it goes admin down which means this is the correct port.
Both Sw are 9300 Sw and IOS is CAT9K_IOSXE
Thanks
Tazio
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2023 12:57 PM - edited 01-12-2023 01:02 PM
Yes there is a media converter on the BGP1 site. The ISP hands over the circuit to be in a media converter on an Ethernet port and I take over from that port to my Cisco Sw. - make sense I was expected this.
i mean when you shutdown Ten 2/1/1 (on BGP1 Gi 1/0/24 go down ?) - I think it will not go down due to media converter between.
can you post show IP route , show run | in routing , show IP arp (from both the switches)
Something looks not right in the connection I guess.
For testing - make it as access port - and vlan 65 - Ten 2/1/1
Connect Laptop on BGP1 side directly to laptop Ethernet and assisng IP address 172.16.30.3 and ping 172.16.30.6 (is this works ?)
So your connection will be like this :
Laptop (172.16.30.3)----Ethernet--Mediaconverter------ISP-------Te 2/1/1
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide