- Cisco Community
- Technology and Support
- Networking
- Routing
- Hi riksjit,
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Site to Site VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2017 02:18 AM - edited 03-05-2019 08:04 AM
Hi,
I have create site to site VPN tunnel and here it the configuration of both router, but when i verify tunnel status using command show crypto session it's show status down, even everything looks ok and both router has reachability to each other, i do not understand why it showing down.
EIGRP configure for routing networks,
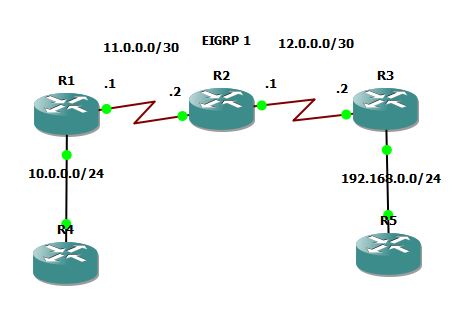
R1 configuration
crypto isakmp policy 1
encr aes
authentication pre-share
crypto isakmp key Cisco address 12.0.0.2
!
!
crypto ipsec transform-set Test esp-aes 192
!
crypto map Crypto_map 1 ipsec-isakmp
set peer 12.0.0.2
set transform-set Test
match address 100
access-list 100 permit ip 10.0.0.0 0.0.0.255 192.168.0.0 0.0.0.255
R3 configuration
crypto isakmp policy 1
encr aes
authentication pre-share
crypto isakmp key Cisco address 11.0.0.1
!
!
crypto ipsec transform-set Test esp-aes 192
!
crypto map Crypto_map 1 ipsec-isakmp
set peer 10.0.0.1
set transform-set Test
match address 100
access-list 100 permit ip 192.168.0.0 0.0.0.255 10.0.0.0 0.0.0.255
Thanks
Alpesh
- Labels:
-
Other Routing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2017 03:04 AM
"set peer 11.0.0.1"
Regards,
Rikshit
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2017 07:06 AM
Hi rikshit,
I have changed peer address bit still its showing down.
Thanks
Alpesh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2017 07:36 AM
ip route 0.0.0.0 0.0.0.0 11.0.0.2
ip route 0.0.0.0 0.0.0.0 12.0.0.1
Regards,
Riksht
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2017 09:03 AM
Hello,
post the full configs of R1 and R3...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2017 08:36 PM
Hi Georg,
here is full config of both router
R1#show running-config
Building configuration...
Current configuration : 1751 bytes
!
! Last configuration change at 09:56:37 UTC Tue Feb 21 2017
upgrade fpd auto
version 15.1
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R1
!
boot-start-marker
boot-end-marker
!
!
!
no aaa new-model
!
ip source-route
no ip icmp rate-limit unreachable
ip cef
!
!
!
!
!
no ip domain lookup
no ipv6 cef
!
multilink bundle-name authenticated
!
!
!
!
!
!
!
crypto pki token default removal timeout 0
!
!
!
redundancy
!
!
ip tcp synwait-time 5
!
!
crypto isakmp policy 1
encr aes
authentication pre-share
crypto isakmp key Cisco address 12.0.0.2
!
!
crypto ipsec transform-set IPSEC esp-aes esp-sha-hmac
!
crypto map CRYPTO 1 ipsec-isakmp
set peer 12.0.0.2
set transform-set IPSEC
match address 100
!
!
!
!
!
!
interface Loopback0
ip address 10.0.0.1 255.255.255.0
!
interface FastEthernet0/0
no ip address
shutdown
duplex half
!
interface Serial1/0
ip address 11.0.0.1 255.255.255.252
serial restart-delay 0
crypto map CRYPTO
!
interface Serial1/1
no ip address
shutdown
serial restart-delay 0
!
interface Serial1/2
no ip address
shutdown
serial restart-delay 0
!
interface Serial1/3
no ip address
shutdown
serial restart-delay 0
!
!
router eigrp 1
network 11.0.0.0 0.0.0.3
!
ip forward-protocol nd
no ip http server
no ip http secure-server
!
!
!
logging esm config
access-list 100 permit ip 10.0.0.0 0.0.0.255 192.168.0.0 0.0.0.255
no cdp log mismatch duplex
!
!
!
!
!
!
control-plane
!
!
!
mgcp profile default
!
!
!
gatekeeper
shutdown
!
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
stopbits 1
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
stopbits 1
line vty 0 4
login
transport input all
!
end
R3#show running-config
Building configuration...
Current configuration : 1754 bytes
!
! Last configuration change at 09:55:30 UTC Tue Feb 21 2017
upgrade fpd auto
version 15.1
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R3
!
boot-start-marker
boot-end-marker
!
!
!
no aaa new-model
!
ip source-route
no ip icmp rate-limit unreachable
ip cef
!
!
!
!
!
no ip domain lookup
no ipv6 cef
!
multilink bundle-name authenticated
!
!
!
!
!
!
!
crypto pki token default removal timeout 0
!
!
!
redundancy
!
!
ip tcp synwait-time 5
!
!
crypto isakmp policy 1
encr aes
authentication pre-share
crypto isakmp key Cisco address 11.0.0.1
!
!
crypto ipsec transform-set IPSEC esp-aes esp-sha-hmac
!
crypto map CRYPTO 1 ipsec-isakmp
set peer 11.0.0.1
set transform-set IPSEC
match address 100
!
!
!
!
!
!
interface Loopback0
ip address 192.168.0.1 255.255.255.0
!
interface FastEthernet0/0
no ip address
shutdown
duplex half
!
interface Serial1/0
ip address 12.0.0.2 255.255.255.252
serial restart-delay 0
crypto map CRYPTO
!
interface Serial1/1
no ip address
shutdown
serial restart-delay 0
!
interface Serial1/2
no ip address
shutdown
serial restart-delay 0
!
interface Serial1/3
no ip address
shutdown
serial restart-delay 0
!
!
router eigrp 1
network 12.0.0.0 0.0.0.3
!
ip forward-protocol nd
no ip http server
no ip http secure-server
!
!
!
logging esm config
access-list 100 permit ip 192.168.0.0 0.0.0.255 10.0.0.0 0.0.0.255
no cdp log mismatch duplex
!
!
!
!
!
!
control-plane
!
!
!
mgcp profile default
!
!
!
gatekeeper
shutdown
!
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
stopbits 1
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
stopbits 1
line vty 0 4
login
transport input all
!
end
R3#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2017 11:53 PM
Hello,
the config you posted is working, to test, try to ping with the loopback being the source:
R3#ping 10.0.0.1 source loopback 0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.0.1, timeout is 2 seconds:
Packet sent with a source address of 192.168.0.1
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 20/21/24 ms
R3#sh crypto session
Crypto session current status
Interface: Serial1/0
Session status: UP-ACTIVE
Peer: 11.0.0.1 port 500
IKEv1 SA: local 12.0.0.2/500 remote 11.0.0.1/500 Active
IPSEC FLOW: permit ip 192.168.0.0/255.255.255.0 10.0.0.0/255.255.255.0
Active SAs: 2, origin: crypto map
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2017 02:23 AM
Dear Georg,
Still i am not pinging to my remote site and crypto session is down.
here is the CLI snap of both router.
i am using Cisco IOS Software, 7200 Software (C7200-ADVENTERPRISEK9-M), Version 15.1(4)M, RELEASE SOFTWARE (fc1)

Thanks
Alpesh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2017 04:18 AM
Helllo Alpesh,
when you:
R3#ping 10.0.0.1 source loopback 0
and then issue the command 'show crypto session' it shows as down ? You need to have IPSec traffic, which in your case is traffic from 192.168.0.0 to 10.0.0.0.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2017 07:39 AM
Hi georg,
yes when i issue command ping 10.0.0.1 sou loo0 i don't received any reply form remote and also crypto session status show down(I did as u said).
Thanks
Alpesh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2017 07:45 AM
Hello Alpesh,
can you post the config of R2, the router in between R1 and R3 ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2017 08:30 AM
Hi Georg,
Here is R2 configuration.
R2#show running-config
Building configuration...
Current configuration : 1327 bytes
!
upgrade fpd auto
version 15.1
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R2
!
boot-start-marker
boot-end-marker
!
!
!
no aaa new-model
!
ip source-route
no ip icmp rate-limit unreachable
ip cef
!
!
!
!
!
no ip domain lookup
no ipv6 cef
!
multilink bundle-name authenticated
!
!
!
!
!
!
!
crypto pki token default removal timeout 0
!
!
!
redundancy
!
!
ip tcp synwait-time 5
!
!
!
!
!
!
!
!
interface FastEthernet0/0
no ip address
shutdown
duplex half
!
interface Serial1/0
ip address 11.0.0.2 255.255.255.252
serial restart-delay 0
!
interface Serial1/1
ip address 12.0.0.1 255.255.255.252
serial restart-delay 0
!
interface Serial1/2
no ip address
shutdown
serial restart-delay 0
!
interface Serial1/3
no ip address
shutdown
serial restart-delay 0
!
!
router eigrp 1
network 11.0.0.0 0.0.0.255
network 12.0.0.0 0.0.0.3
!
ip forward-protocol nd
no ip http server
no ip http secure-server
!
!
!
logging esm config
no cdp log mismatch duplex
!
!
!
!
!
!
control-plane
!
!
!
mgcp profile default
!
!
!
gatekeeper
shutdown
!
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
stopbits 1
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
stopbits 1
line vty 0 4
login
transport input all
!
end
R2#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2017 09:03 AM
Hello,
below is my working configuration. GNS can be buggy, which IOS image are you using ? I am using C7200-ADVIPSERVICESK9-M), Version 15.2(4)S5.
hostname R1
!
crypto isakmp policy 1
encr aes
authentication pre-share
crypto isakmp key Cisco address 12.0.0.2
!
crypto ipsec transform-set IPSEC esp-aes esp-sha-hmac
!
crypto map CRYPTO 1 ipsec-isakmp
set peer 12.0.0.2
set transform-set IPSEC
match address 100
!
interface Loopback0
ip address 10.0.0.1 255.255.255.0
!
interface Serial1/0
ip address 11.0.0.1 255.255.255.252
serial restart-delay 0
crypto map CRYPTO
!
router eigrp 1
network 11.0.0.0 0.0.0.3
!
access-list 100 permit ip 10.0.0.0 0.0.0.255 192.168.0.0 0.0.0.255
hostname R2
!
interface Serial1/0
ip address 11.0.0.2 255.255.255.252
serial restart-delay 0
!
interface Serial1/1
ip address 12.0.0.1 255.255.255.252
serial restart-delay 0
!
router eigrp 1
network 11.0.0.0 0.0.0.3
network 12.0.0.0 0.0.0.3
hostname R3
!
crypto isakmp policy 1
encr aes
authentication pre-share
crypto isakmp key Cisco address 11.0.0.1
!
crypto ipsec transform-set IPSEC esp-aes esp-sha-hmac
!
crypto map CRYPTO 1 ipsec-isakmp
set peer 11.0.0.1
set transform-set IPSEC
match address 100
!
interface Loopback0
ip address 192.168.0.1 255.255.255.0
!
interface Serial1/0
ip address 12.0.0.2 255.255.255.252
serial restart-delay 0
crypto map CRYPTO
!
router eigrp 1
network 12.0.0.0 0.0.0.3
!
access-list 100 permit ip 192.168.0.0 0.0.0.255 10.0.0.0 0.0.0.255
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2017 09:18 AM
Hi Georg,
Yes it possible that some bug BTW I will check using different version of IOS.
thanks for your effort and support.
Alpesh.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
