- Cisco Community
- Technology and Support
- Networking
- Routing
- VPN UP-ACTIVE but cannot ping across VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2013 10:07 AM - edited 03-04-2019 07:37 PM
I have a VPN setup that I am trying to get workling. When I issue the command sh crypto session on both routers I get the following:
OFFICE:
Interface: FastEthernet0/0
Session status: UP-ACTIVE
Peer: 70.193.192.131 port 14275
IKEv1 SA: local 40.197.68.9/4500 remote 70.193.192.131/14275 Active
IPSEC FLOW: permit ip 192.168.10.0/255.255.255.0 192.168.30.0/255.255.255.252
Active SAs: 2, origin: dynamic crypto map
HOME:
Interface: GigabitEthernet0/0
Session status: UP-ACTIVE
Peer: 40.197.68.9 port 4500
IKEv1 SA: local 192.168.30.1/4500 remote 40.197.68.9/4500 Active
IPSEC FLOW: permit ip 192.168.30.0/255.255.255.252 192.168.10.0/255.255.255.0
Active SAs: 2, origin: crypto map
But when I issue a ping 192.168.10.1 from the home router it returns .....
Here is my network topology:
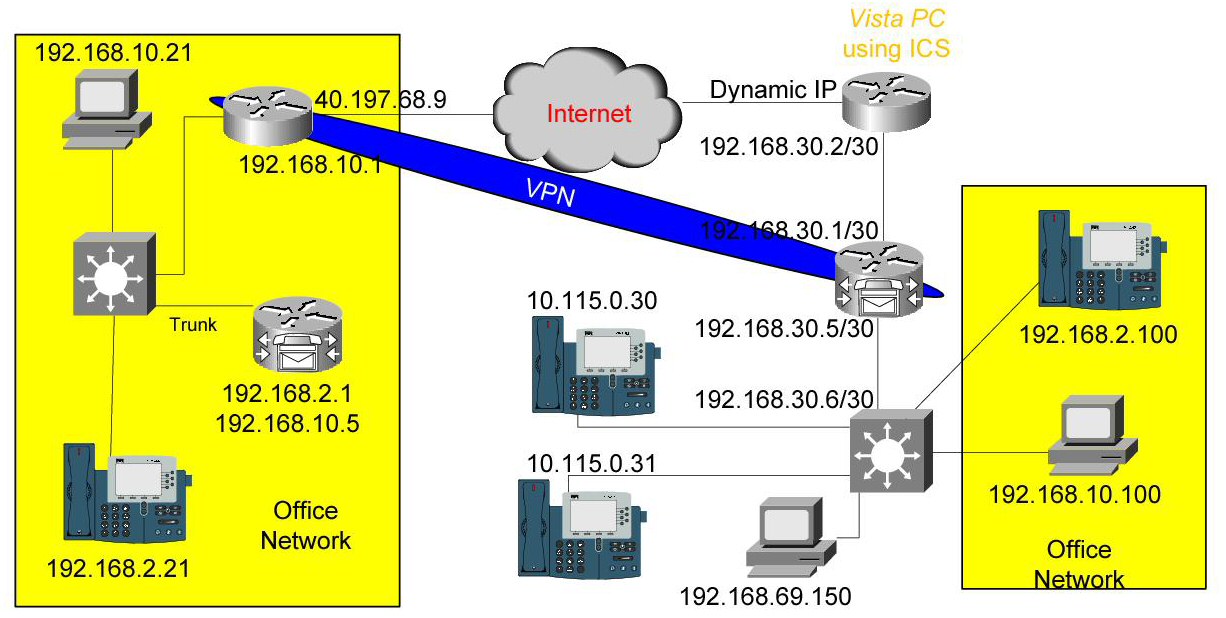
Attached are my config files.
First, I do not know what I need to do to get the home router to ping the office router. Secind, what do I do to get the 192.168.2.0 network (phone) to cross the VPN all the way to my phone.
Any help you can provide, I will be greatly thankful for!!!
Solved! Go to Solution.
- Labels:
-
Routing Protocols
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2013 06:16 PM
Ok,
Looking at your config, you're doing NAT per ACL 1, on your OFFICE router, for source of 192.168.10.0/24. You're NATing your OFFICE LAN to your public interface BEFORE it's being sent through tunnel:
http://www.techrepublic.com/article/understand-the-order-of-operations-for-cisco-ios/6055946 (NAT Order of Operations)
Change it to an extended and insert a line to that to deny NAT for your HOME network destinations across the tunnel:
ip access-list extended SDM_ACL
deny ip 192.168.10.0 0.0.0.255 192.168.30.0 0.0.0.3
permit ip 192.168.10.0 0.0.0.255 any
That will take care of connectivity to the /30 subnet, but if you're wanting access to the OFFICE from your 110 and 115 VLANs from your HOME, then you'll need to add those networks to the VPN1-FLA-TRAFFIC and VPN-TRAFFIC ACL's, respectively.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2013 12:11 PM
Without seeing some logs or debugs, etc...it would be hard to diagnose. However, perhaps you can manually set a lower interval DPD (Dead Peer Detection) keepalive and keep the tunnel up. Try:
crypto isakmp keepalive 30 5 periodic
http://www.cisco.com/en/US/docs/ios/security/command/reference/sec_c4.html#wp1057298
-Chris
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2013 03:00 PM
When you do your ping, are you sourcing it from the 192.168.30.0/255.255.255.252 interface of the router? It has to be from that, as that will match your 'interesting traffic' ACL for your IPSec tunnel:
e.g. 'ping ip
HTH!
-Chris
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2013 04:25 PM
Still nothing when issuing the command:
ping ip 192.168.10.1 source 192.168.30.1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2013 06:16 PM
Ok,
Looking at your config, you're doing NAT per ACL 1, on your OFFICE router, for source of 192.168.10.0/24. You're NATing your OFFICE LAN to your public interface BEFORE it's being sent through tunnel:
http://www.techrepublic.com/article/understand-the-order-of-operations-for-cisco-ios/6055946 (NAT Order of Operations)
Change it to an extended and insert a line to that to deny NAT for your HOME network destinations across the tunnel:
ip access-list extended SDM_ACL
deny ip 192.168.10.0 0.0.0.255 192.168.30.0 0.0.0.3
permit ip 192.168.10.0 0.0.0.255 any
That will take care of connectivity to the /30 subnet, but if you're wanting access to the OFFICE from your 110 and 115 VLANs from your HOME, then you'll need to add those networks to the VPN1-FLA-TRAFFIC and VPN-TRAFFIC ACL's, respectively.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2013 07:46 AM
Thnk you so much!!!
Can you tell me what I need to do on my switch so that I can get a PC on the 192.168.10.0 net please? I assume that the PC will need to be a static IP since we are blocking NAT over the VPN. Am I correct on this?
I do not want to share my 110 & 115 networks over the VPN. But, I do need access to the 192.168.2.0 office network so I can get my VoIP phone up. I assume that I would use the same settngs for the phone as the PC except I need to set it in Switchport Voice VLAN 2. Also, does the phone need to be static or can it use a dynamic IP from the office over the VPN?
Thanks so much!!!
UPDATE
I added the routes below:
OFFICE VPN ROUTER
ip route 192.168.30.0 255.255.255.0 FastEthernet0/0
OFFICE CME ROUTER
ip route 192.168.30.0 255.255.255.252 192.168.10.1
HOME ROUTER
ip route 192.168.10.0 255.255.255.0 GigabitEthernet0/0
I can now ping the 192.168.10.5 port on the CME router. But I cannot ping the 192.168.2.1 port of the CME router.
Then all of a suddon I can no onger ping anthing on the 192.168.10.x network fro mome. SH CRYPTO SESSION
Session status: UP-ACTIVE
Peer: 40.197.68.9 port 4500
IKEv1 SA: local 192.168.30.1/4500 remote 40.197.68.9/4500 Active
IPSEC FLOW: permit ip 192.168.30.0/255.255.255.252 192.168.2.0/255.255.255.0
Active SAs: 2, origin: crypto map
IPSEC FLOW: permit ip 192.168.30.0/255.255.255.252 192.168.10.0/255.255.255.0
Active SAs: 2, origin: crypto map
So now I am stuck again. Also, I do need this VPN to be up 7x24 so my VoIP phone will allways work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2013 08:27 AM
Your VPN1-FLA-TRAFFIC and VPN-TRAFFIC ACL's have to match (in reverse):
OFFICE:
ip access-list extended VPN1-FLA-TRAFFIC
permit ip 192.168.10.0 0.0.0.255 192.168.30.0 0.0.0.3
permit ip 192.168.2.0 0.0.0.255 192.168.30.0 0.0.0.3
HOME:
ip access-list extended VPN-TRAFFIC
permit ip 192.168.30.0 0.0.0.3 192.168.10.0 0.0.0.255
permit ip 192.168.30.0 0.0.0.3 192.168.2.0 0.0.0.255
But, of course, you'll either need the 192.168.2.0/24 network on your OFFICE router, or a route on your OFFICE router to point to that network (as it is not defined currently - from what I see in your config).
HTH!
-Chris
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2013 10:56 AM
I have changed both access list to allow the 192.168.2.0 network. I added an interface to the CME OFFICE router for the 192.168.10.0 network. I then added a static route to the 192.168.2.0 network from the OFFICE MAIN router. I can ping the CME (192.168.2.1) router from the office Main (192.168.10.1) router.
BUT, the VPN keeps stop sending data even though its status is UP-ACTIVE . It will send ping data for about 1 or 2 minutes and goes deas yet still UP-ACTIVE. It takes a while to drop the VPN and when I re-establish it, data works for a few mins.
So, what do I need to add/change to get a stable perminate VPN connection?
-Michael
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2013 12:11 PM
Without seeing some logs or debugs, etc...it would be hard to diagnose. However, perhaps you can manually set a lower interval DPD (Dead Peer Detection) keepalive and keep the tunnel up. Try:
crypto isakmp keepalive 30 5 periodic
http://www.cisco.com/en/US/docs/ios/security/command/reference/sec_c4.html#wp1057298
-Chris
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2013 12:57 PM
That seems to help a lot!!! Thanks so much.
Okay, now I have connectivity to my HOME router. What do I need to add to the HOME router and my Cisco 3550 switch so that I can get a phone connected? Also, will the phone get its IP from the OFFICE router or do I set a static one it in?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-19-2019 08:04 PM
Thank you so much for this! Once I re-ordered my NAT rules for the "interesting" traffic, things took right off! The ASDM made it easy for me to move 'em up the list prior to any other NAT taking place
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2019 04:43 PM
Hello.
I'm facing the same kind of issue. I'm able to connect to the VPN (Cisco-ASA-5505) but cannot ping internal network. Please advise/help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2019 04:44 PM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide