[toc:faq]
Disclaimer
Please note that while the below scenario should work for most setups, it is to be considered a hack/workaround/kludge.
There is an upcoming enhancement to IPsec code in ASA release codenamed Arsenal, which will be out later this year.
Background
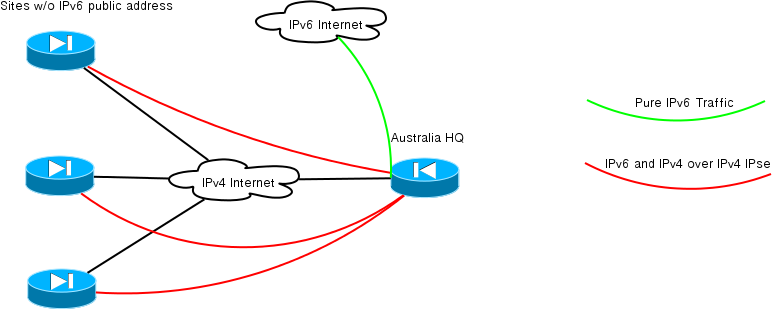
A few days ago Greg opened a case with TAC where he was looking for documentation on how to achieve parallel IPsec tunnels over IPv4 for both IPv4 and IPv6 traffic.
His actual topology were multiple devices all around the world connecting to a central hub location in Australia.
Not all the devices had IPv6 addressing so as an interim solution he wanted to tunnel IPv6 over IPv4 in a secure way.
The documentaion is quite scarce on this topic, so we had to go to the lab an test this out.
Topology diagram
Solution
The solution that worked for us was based on ASA 8.4.3 on all sites.
We run a parallel IKEv2 for IPv4 over IPv4 IPsec tunnel and IPv6 over IPv4 IKEv1 based tunnel.
Configuration
Basic configuration.
Site without IPv6 internet access
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 10.48.67.5 255.255.254.0
ipv6 enable
ipv6 nd suppress-ra
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
ipv6 address 2001:db8:11::1/64
crypto ipsec ikev1 transform-set TRA1 esp-aes esp-sha-hmac
crypto ipsec ikev2 ipsec-proposal TRA2
protocol esp encryption aes-192 aes
protocol esp integrity sha-1
crypto map MAP 10 match address V4
crypto map MAP 10 set peer 10.48.67.11
crypto map MAP 10 set ikev2 ipsec-proposal TRA2
crypto map MAP 20 match address V6
crypto map MAP 20 set peer 10.48.67.11
crypto map MAP 20 set ikev1 transform-set TRA1
crypto map MAP interface outside
crypto ikev2 policy 10
encryption aes-192 aes
integrity sha256 sha
group 2
prf sha
lifetime seconds 86400
crypto ikev2 enable outside
crypto ikev1 enable outside
crypto ikev1 policy 10
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
tunnel-group 10.48.67.11 type ipsec-l2l
tunnel-group 10.48.67.11 ipsec-attributes
ikev1 pre-shared-key *****
ikev2 remote-authentication pre-shared-key *****
ikev2 local-authentication pre-shared-key *****
access-list V4 extended permit ip 192.168.1.0 255.255.255.0 192.168.2.0 255.255.255.0
ipv6 route outside ::/0 fe80::1111
ipv6 access-list V6 permit ip 2001:db8:11::/64 2001:db8:22::/64
Site with IPv6 internet.
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 10.48.67.11 255.255.254.0
ipv6 address 2001:db8::2/64
ipv6 nd suppress-ra
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 192.168.2.1 255.255.255.0
ipv6 address 2001:db8:22::1/64
access-list V4 extended permit ip 192.168.2.0 255.255.255.0 192.168.1.0 255.255.255.0
ipv6 route outside ::/0 2001:db8::1
ipv6 access-list V6 permit ip 2001:db8:22::/64 2001:db8:11::/64
crypto ipsec ikev1 transform-set TRA1 esp-aes esp-sha-hmac
crypto ipsec ikev2 ipsec-proposal TRA2
protocol esp encryption aes-192 aes
protocol esp integrity sha-1
crypto map MAP 10 match address V4
crypto map MAP 10 set peer 10.48.67.5
crypto map MAP 10 set ikev2 ipsec-proposal TRA2
crypto map MAP 20 match address V6
crypto map MAP 20 set peer 10.48.67.5
crypto map MAP 20 set ikev1 transform-set TRA1
crypto map MAP interface outside
crypto ikev2 policy 10
encryption aes-192 aes
integrity sha256 sha
group 2
prf sha
lifetime seconds 86400
crypto ikev2 enable outside
crypto ikev1 enable outside
crypto ikev1 policy 10
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
tunnel-group 10.48.67.5 type ipsec-l2l
tunnel-group 10.48.67.5 ipsec-attributes
ikev1 pre-shared-key *****
ikev2 remote-authentication pre-shared-key *****
ikev2 local-authentication pre-shared-key *****
Result
After applying this configuration all remote sites were able to reach IPv6 internet.
Note that all IPv6 addresses need to be routable and typically assigned from same /48 or /56 pool as headquarters.
Verification
Let's check if both IKEv1 and IKEv2 are up.
bsns-asa5540-3# sh cry isa sa
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 10.48.67.5
Type : L2L Role : initiator
Rekey : no State : MM_ACTIVE
IKEv2 SAs:
Session-id:3, Status:UP-ACTIVE, IKE count:1, CHILD count:1
Tunnel-id Local Remote Status Role
1002325 10.48.67.11/500 10.48.67.5/500 READY INITIATOR
Encr: AES-CBC, keysize: 192, Hash: SHA256, DH Grp:2, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/17 sec
Child sa: local selector 192.168.2.0/0 - 192.168.2.255/65535
remote selector 192.168.1.0/0 - 192.168.1.255/65535
ESP spi in/out: 0x390ef9d2/0xcfee516
References
RFC 4306 - IKEv2
http://www.ietf.org/rfc/rfc4306.txt
RFC 2409 - IKEv1
http://www.ietf.org/rfc/rfc2409.txt
ASA product references:
http://www.cisco.com/en/US/products/ps6120/products_installation_and_configuration_guides_list.html
Comments? Feedback?
Leave a comment under this post.
