Security automation is a hot topic these days. Most organizations have many systems to patch and configure securely, with numerous versions of software and features enabled. Many security administrators are seeking ways to leverage standards and available tools to reduce the complexity and time necessary to respond to security advisories, assess their devices, and ensure compliance so they can allocate resources to focus on other areas of their network and security infrastructure.
Cisco is committed to protect customers by sharing critical security-related information in different formats.
Cisco’s Product Security Incident Response Team (PSIRT) is now including Open Vulnerability and Assessment Language (OVAL) definitions in Cisco IOS security advisories.
Also starting today, in addition to OVAL definitions, Cisco is publishing Common Vulnerability Reporting Framework (CVRF) content for all security advisories. CVRF allows vendors to publish security advisories in an XML format intended for the sharing of security-related information in a machine-readable format. CVRF has been designed by the Industry Consortium for Advancement of Security on the Internet (ICASI), of which Cisco is a member and took a major role in its development.
Note: Please refer to the blog posts titled “The Missing Manual: CVRF 1.1 Part 1 and Part 2 for detailed information about CVRF.
What is OVAL?
OVAL is an international community standard to promote open and publicly available security content, and to standardize the transfer of this information in security tools and services. OVAL is part of the Security Content Automation Protocol (SCAP) specifications. OVAL’s main purpose is to assist security administrators by accelerating the process of analyzing a system for the presence of a vulnerability or configuration best practices. MITRE’s OVAL website contains a detailed definition at the following link: http://oval.mitre.org/about/index.html
OVAL speeds up information exchange and processing of such security-related information. Using OVAL security administrators and other users can accelerate the process of detecting software vulnerabilities in Cisco IOS Software. OVAL content (often called “definitions”) can be downloaded directly from Cisco IOS security advisories. Each Cisco IOS security advisory includes a link to the corresponding OVAL definition(s).
The following figure (Figure 1) shows how customers can download OVAL and CVRF content directly from security advisories.
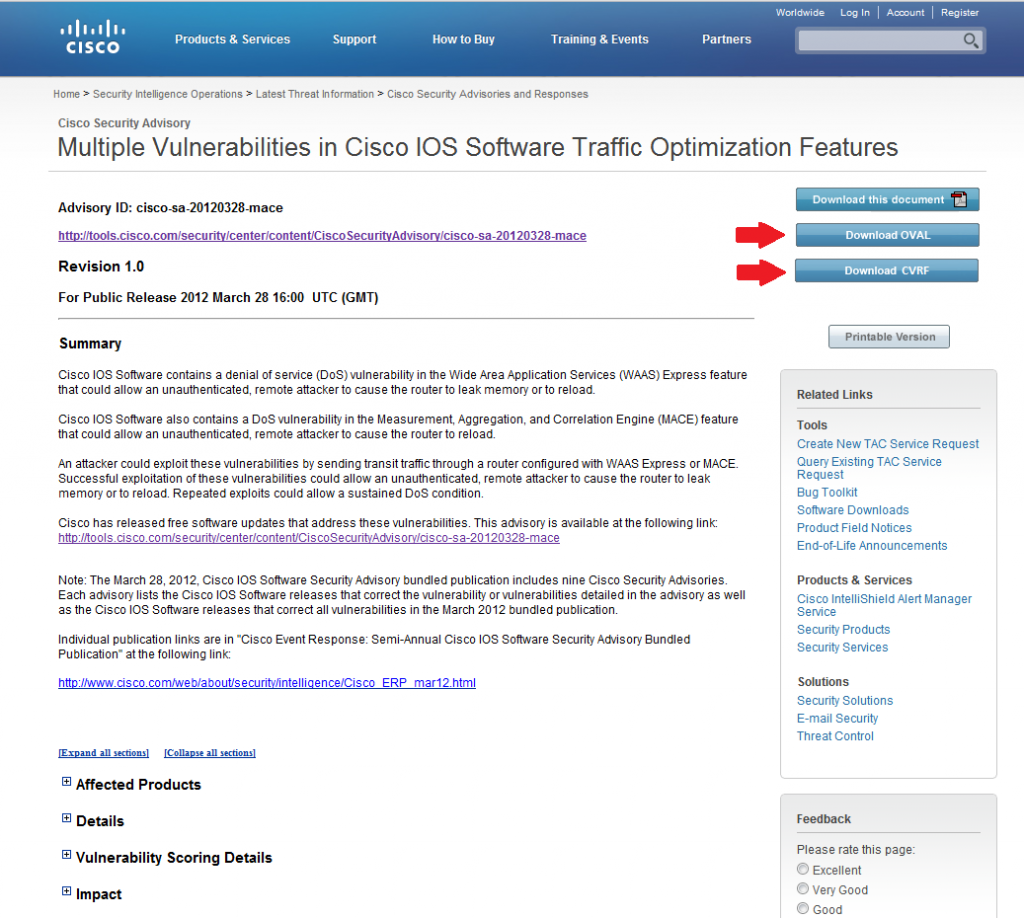
Figure 1 - OVAL and CVRF Content in Security Advisories
CVRF is available in all security advisories; however, OVAL is only supported in Cisco IOS advisories. Cisco is working with MITRE and the OVAL community to enhance and develop new schemata to enhanced Cisco IOS support and potentially other Cisco Products. Several changes have already been submitted and integrated in MITRE’s OVAL Language Sandbox.
OVAL Definitions are XML files that contain information about how to check a system for the presence of vulnerabilities, configuration issues, patches, installed applications, or other characteristics of such system. For vulnerability checks, definitions are written to check for a vulnerability, often identified by a specific Common Vulnerabilities and Exposures (CVE) identifier. OVAL definitions must comply with the OVAL Definition Schema, and should be written in accordance with the Authoring Style Guide defined by MITRE. MITRE’s “OVAL Definition Lifecycle” website has a detailed description of the OVAL definition process:
http://oval.mitre.org/repository/about/stages.html
OVAL enables interoperability between security and network management products from different vendors in different vertical markets allowing them to quickly and automatically perform vulnerability and compliance assessment of network infrastructure and networking devices. All organizations participating in the OVAL Adoption Program are listed in MITRE’s website at: http://oval.mitre.org/adoption/participants.html
Many vendors are working on integrating Cisco IOS schemata support into their products. An example of an open source tool that supports the Cisco IOS OVAL schema is jOVAL. For more information about jOVAL visit: http://joval.org
Figure 2 shows an example of an OVAL scan results from the jOVAL open source scanner:
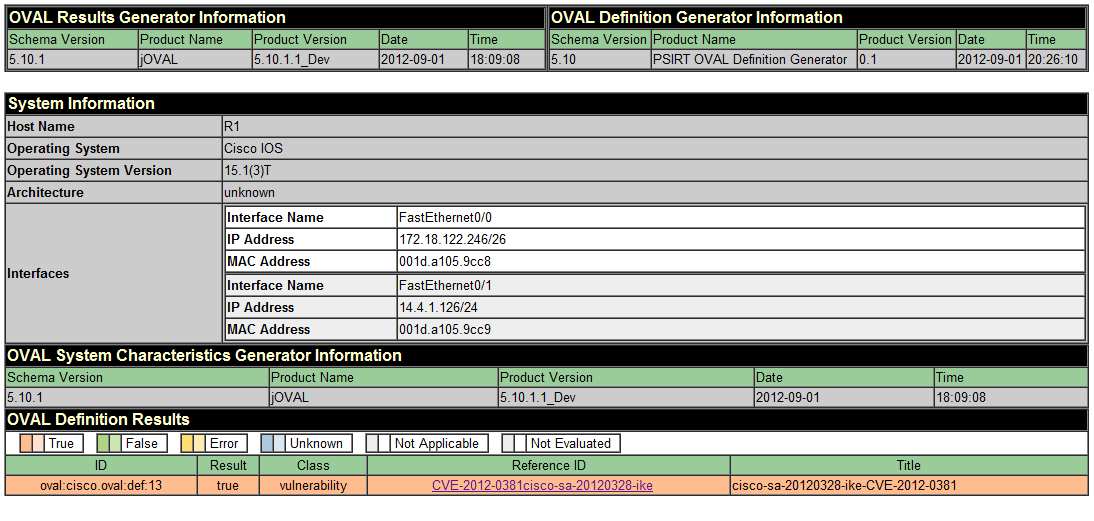
Figure 2 - OVAL Scan Results
The following whitepaper provides a detailed description of the SCAP components and other security automation specifications, as well as step-by-step instructions on how to use OVAL content with available open source tools:
http://www.cisco.com/web/about/security/intelligence/oval_scty_automation.html
A frequently asked questions (FAQ) document has been published at the following location to help answer some of the common questions related to Cisco’s OVAL adoption:
http://www.cisco.com/web/about/security/intelligence/oval_faq.html
