Cisco Secure Network Analytics
Cisco Secure Network Analytics (formerly known as Stealthwatch solution) was originally acquired from Lancope. It utilizes NetFlow information to provide telemetry and contextual information from network infrastructure devices. It is very helpful for network administrators, as well as cybersecurity professionals to utilize network telemetry data, to detect and mitigate cyber threats, such as network reconnaissance, malware proliferation, communication between the attacker and the compromised internal hosts, as well as data exfiltration.
Cisco Secure Network Analytics (formerly known as stealthwatch) aggregates and normalizes considerable amount of Netflow data to apply security analytics to detect malicious and suspicious activity. The Cisco Stealthwatch Management Console (SMC) provides a rich graphical user interface(GUI) with many visualizations and telemetry information.

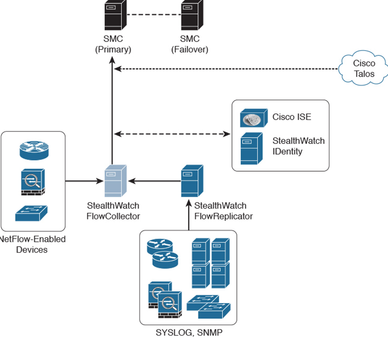
Secure Network Analytics Components:
The Secure Network Analytics (formerly known as Stealthwatch) enterprise solution is comprised of the following components.
The Flow Collector: which is a physical or virtual appliance that collects the NetFlow data that is sent to it from network infrastructure devices.
The Stealthwatch Management Console or SMC: the main management application that provides detailed dashboards and the ability to correlate network flow and events.
Optional Components: The following are the optional components of the Cisco Secure Network Analytics (formerly known as Stealthwatch):
Flow Sensor: A physical or Virtual appliance that can generate netflow data when legacy cisco network infrastructure components are not capable of providing line-rate, unsampled netflow data.
Flow Replicator: A physical appliance used to forward Netflow data as a single data steam to other devices. The flow replicator is also known as the udp director.

Cisco Secure Network Analytics and Logging, (formerly known as Stealthwatch Cloud) is a Software as a Service (SaaS) cloud solution. You can use Cisco Secure Network Analytics and Logging (Stealthwatch Cloud) to monitor many different public cloud environments, such as Amazon’s AWS, Google Cloud Platform, and Microsoft Azure.
All of these cloud providers support their own implementation of NetFlow:
- In Amazon AWS, the equivalent of NetFlow is called VPC Flow Logs.
- Google Cloud Platform also supports VPC Flow Logs (or Google-branded GPC Flow Logs).
- In Microsoft’s Azure, traffic flows are collected in Network Security Group (NSG) flow logs. NSG flow logs are a feature of Network Watcher.
You can also monitor on-premises networks in your organizations using Cisco Stealthwatch Cloud. In order to do so, you need to deploy at least one Cisco Stealthwatch Cloud Sensor appliance (virtual or physical appliance).
The Cisco Stealthwatch Cloud Sensor appliance can be deployed in two different modes (not mutually exclusive):
• Processing network metadata from a SPAN or a network TAP
• Processing metadata out of NetFlow or IPFIX flow records

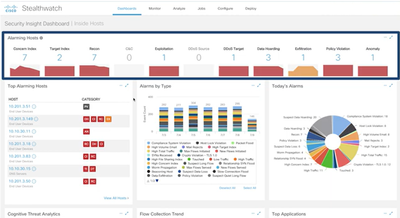
The Cisco Stealthwatch Security Insight Dashboard can be used to quickly see the events that have triggered alarms within your premises. Some of the graphics provide data for the past 7 days (such as the Alarms by Type), and some information concerns data for the last 24 hours (such as the Today’s Alarms statistics, the Flow Collection Trend, and the Top Applications visualization).
Threat Hunting with Cisco Stealthwatch: Threat hunting is the concept of “proactively” or “actively” searching for advanced threats that may evade your security products and capabilities.
Note: Cisco Stealthwatch Cloud can also be integrated withMeraki and Cisco Umbrella.
You can start using of Cisco Secure Analystics and Logging with 60-day trail, for more details, please go through the following link:
https://www.cisco.com/c/en/us/products/security/security-analytics-logging/index.html
To know more about Cisco Secure Analytics, please go through the following link:https://www.cisco.com/site/in/en/products/security/security-analytics/secure-network-analytics/index.html
Thank you very much..!!
