(written by Matthew Robertson)
This blog extends information from Cognitive Threat Analytics (CTA): Release Notes
As the machine learning engine in Cognitive Analytics was designed to be deployed in real production networks it can be challenging to generate a detection in a home or customer lab environment and generating an "on-demand" detection of the Encrypted Traffic Analytics solution can be even more difficult. This page describes what we have found is the best way to test a Stealthwatch with Cognitive and ETA deployment and generate a detection in lab and on-demand environments.
Generating a Detection:
Classifiers for some of the same domains used to test Umbrella have been built into the Cognitive engine. Specifically classifiers for the following:
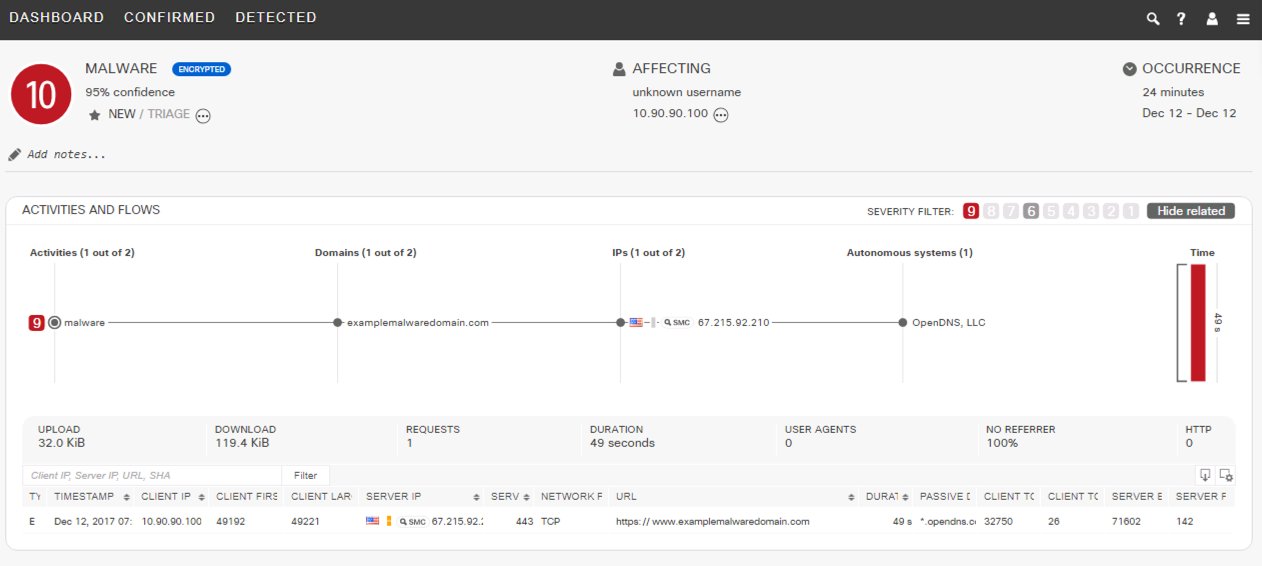
https://examplemalwaredomain.com (test site for malware)
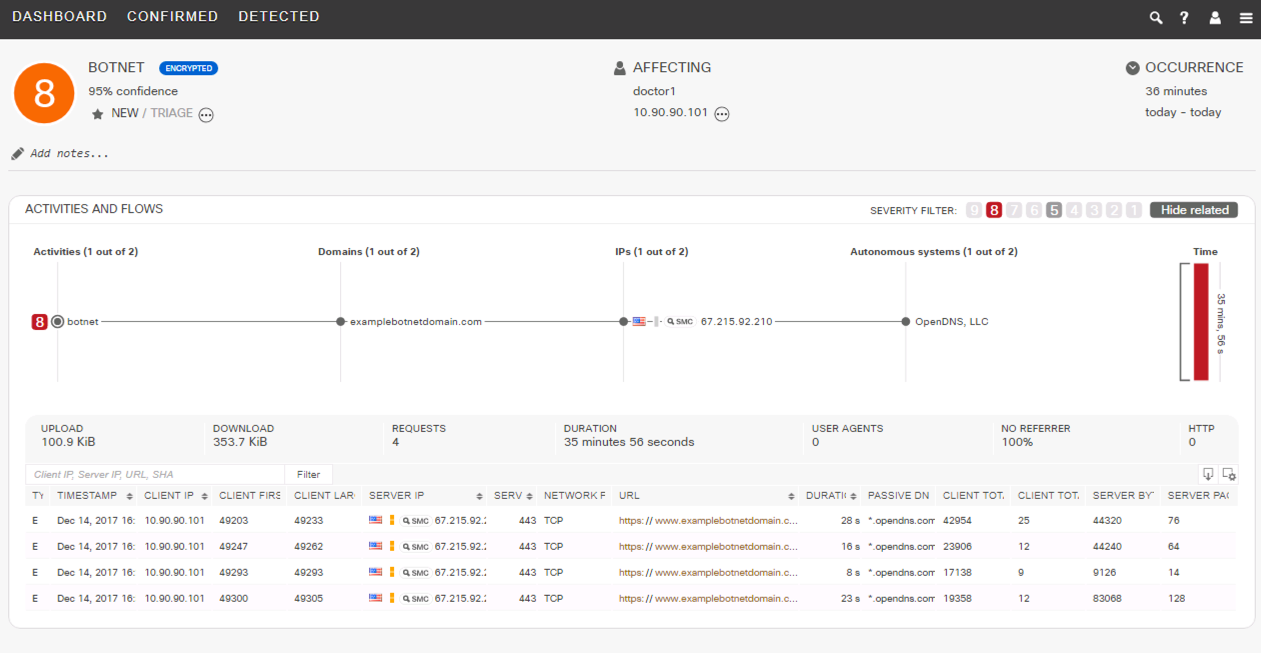
https://examplebotnetdomain.com (test site for botnet)
https://internetbadguys.com (test site for phishing)
Browsing to those URLs from a host, where the https session is passing through an enhanced NetFlow exporter will generate a detection in Cognitive which will display with the "Detected Using Encrypted Traffic Analytics" notifier.
Note: The detection may initially show up as with a risk rating of 5. The risk rating can increase with additional bad or repetitive behavior: such as going to multiple of the above URLs or repeatedly visiting the same URL.
Malware Detection in SMC Dashboard:
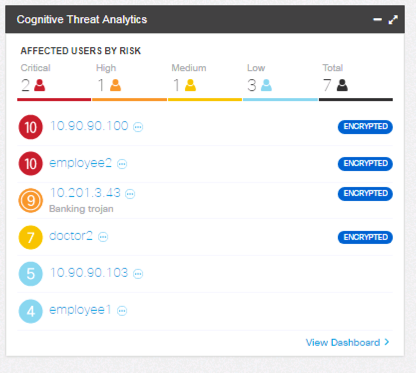
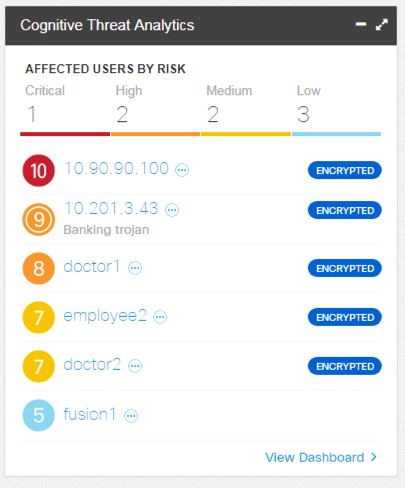
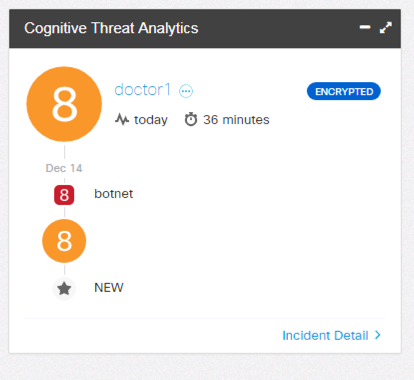
Malware detection in Cognitive Widget in the Host Report:
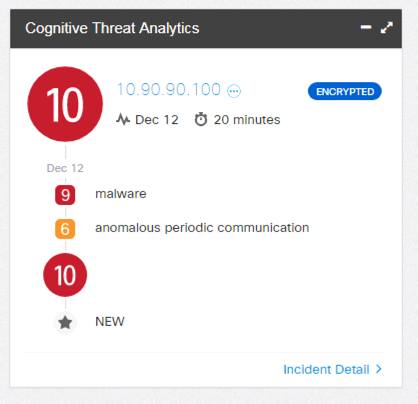
Malware Detection in the Cognitive Dashboard:
ETA TOR detections in SMC Dashboard Cognitive widget:
TOR detection in Cognitive Widget in the Host Report:
Potentially Unwanted Application in the Cognitive Dashboard:
Phishing Detection in SMC Dashboard:
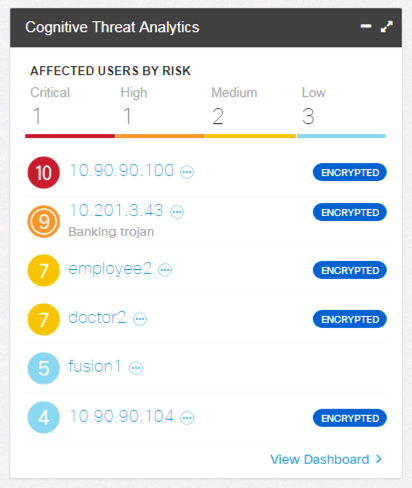
Phishing detection in Cognitive Widget in the Host Report:
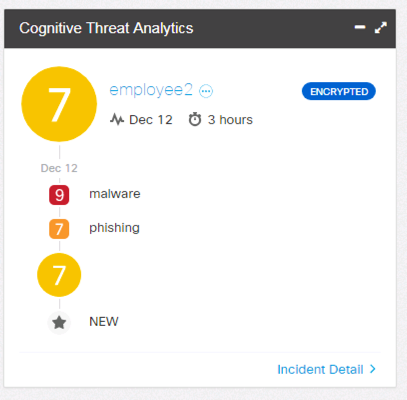
Phishing Detection in the Cognitive Dashboard:
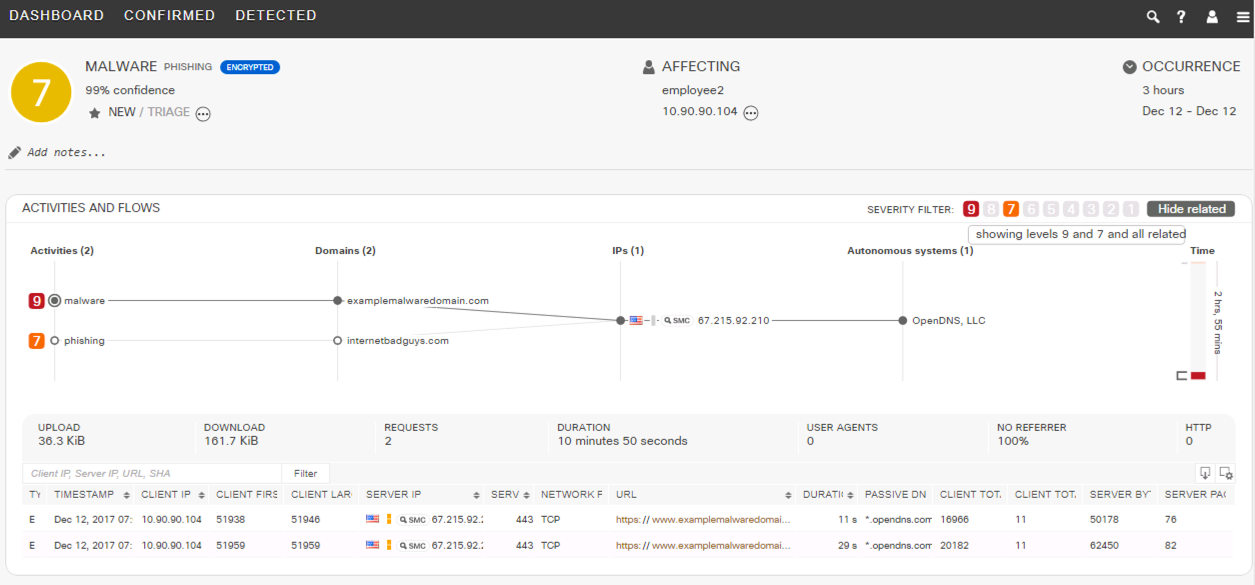
Generating a "Real" Detection
Cognitive is very effective at detecting the usage of TOR by a host and it is a significant value proposition for the technology.
A very simple way to demonstrate an active detection is to use the TOR browser on a host in the lab (a host behind the switch or router exporting the enhanced NetFlow).
First download and install the TOR browser: https://www.torproject.org/projects/torbrowser.html.en
After installing launch the TOR browser and do some internet browsing. A detection will appear in the Cognitive widget/dashboard shortly. The detection will display as a severity 4 possibly unwanted application with the “detected using encrypted traffic analytics” label.
ETA TOR detections in SMC Dashboard Cognitive widget:
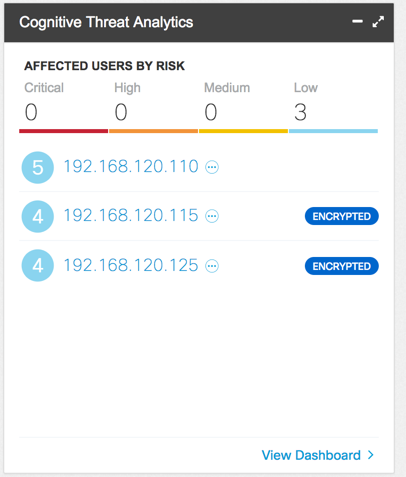
TOR detection in Cognitive Widget in the Host Report:
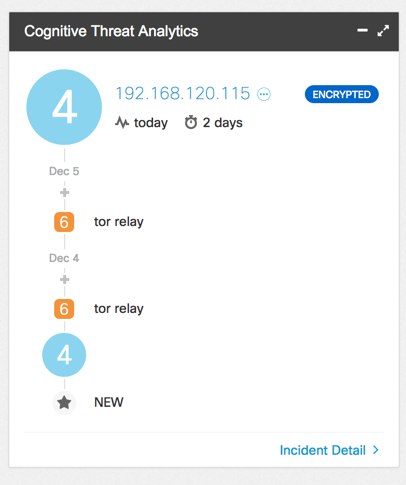
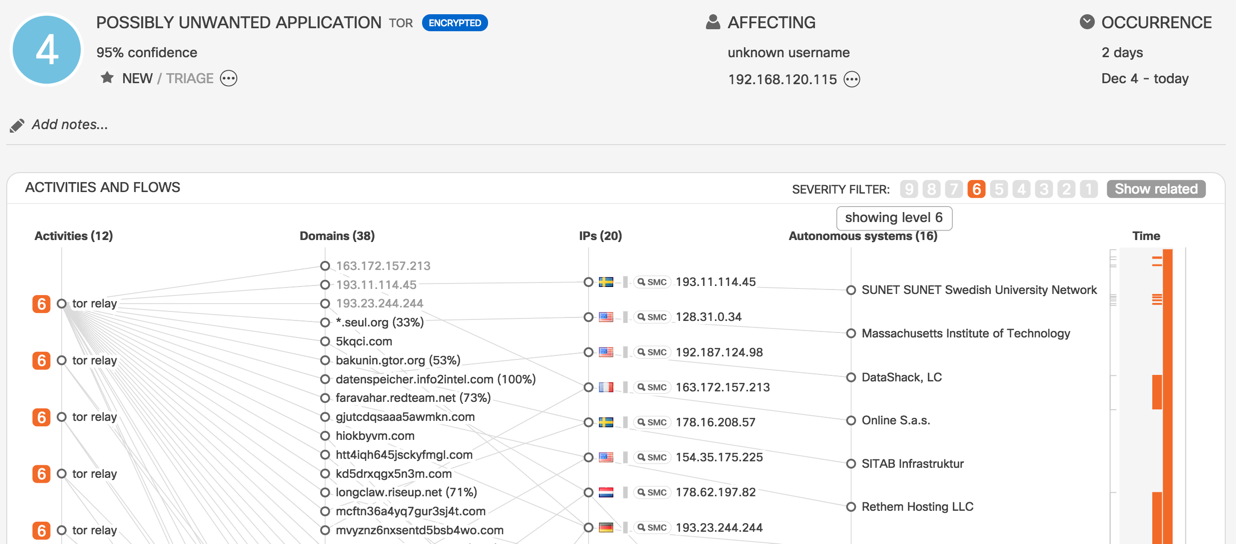
Potentially Unwanted Application in the Cognitive Dashboard:
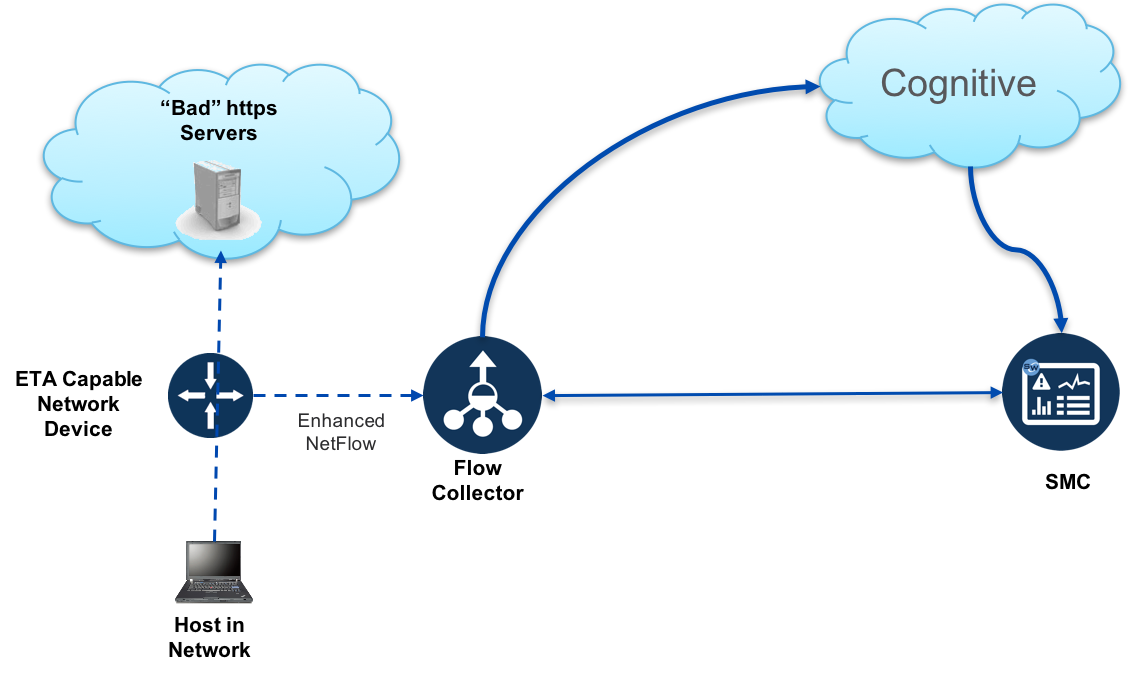
Basic Lab Overview:
In this scenario we have a host connected to a Catalyst 9300. The Catalyst 9300 is configured to send Enhanced NetFlow (including ETA) to Stealthwatch.